Overview
In the realm of software development, developers face numerous coding challenges that can hinder efficiency and security. One solution to these challenges is Kodezi, which offers innovative features designed to streamline the development process. With automated scanning, contextual prioritization, and real-time threat detection, Kodezi not only enhances security management but also boosts operational productivity.
By integrating AI into vulnerability management, Kodezi empowers developers to address vulnerabilities proactively. This leads to improved security posture and allows teams to focus on delivering high-quality code. Imagine the impact of having a tool that not only identifies risks but also prioritizes them based on context—this is where Kodezi shines.
Furthermore, the benefits of utilizing Kodezi extend beyond mere efficiency. Developers can experience significant gains in productivity and code quality, making it an essential tool in the modern development landscape. Are you ready to elevate your coding practices and enhance your team's output?
Explore the various tools available on the Kodezi platform and discover how they can transform your approach to software development and security management. Embrace the future of coding with Kodezi and experience the difference that AI-driven solutions can make.
Introduction
In a digital landscape fraught with security threats, the necessity for effective vulnerability management tools has never been more critical. This article explores ten cutting-edge AI vulnerability scanning tools that promise to enhance efficiency and strengthen security postures for organizations of all sizes. But with numerous options available, how can teams discern which tools truly deliver on their promises? By examining these innovative solutions, readers will uncover their unique features and the transformative potential they hold for proactive risk management in an increasingly complex cyber environment.
Kodezi | Professional OpenAPI Specification Generator - AI Dev-Tool: Automate Vulnerability Scanning and Code Maintenance
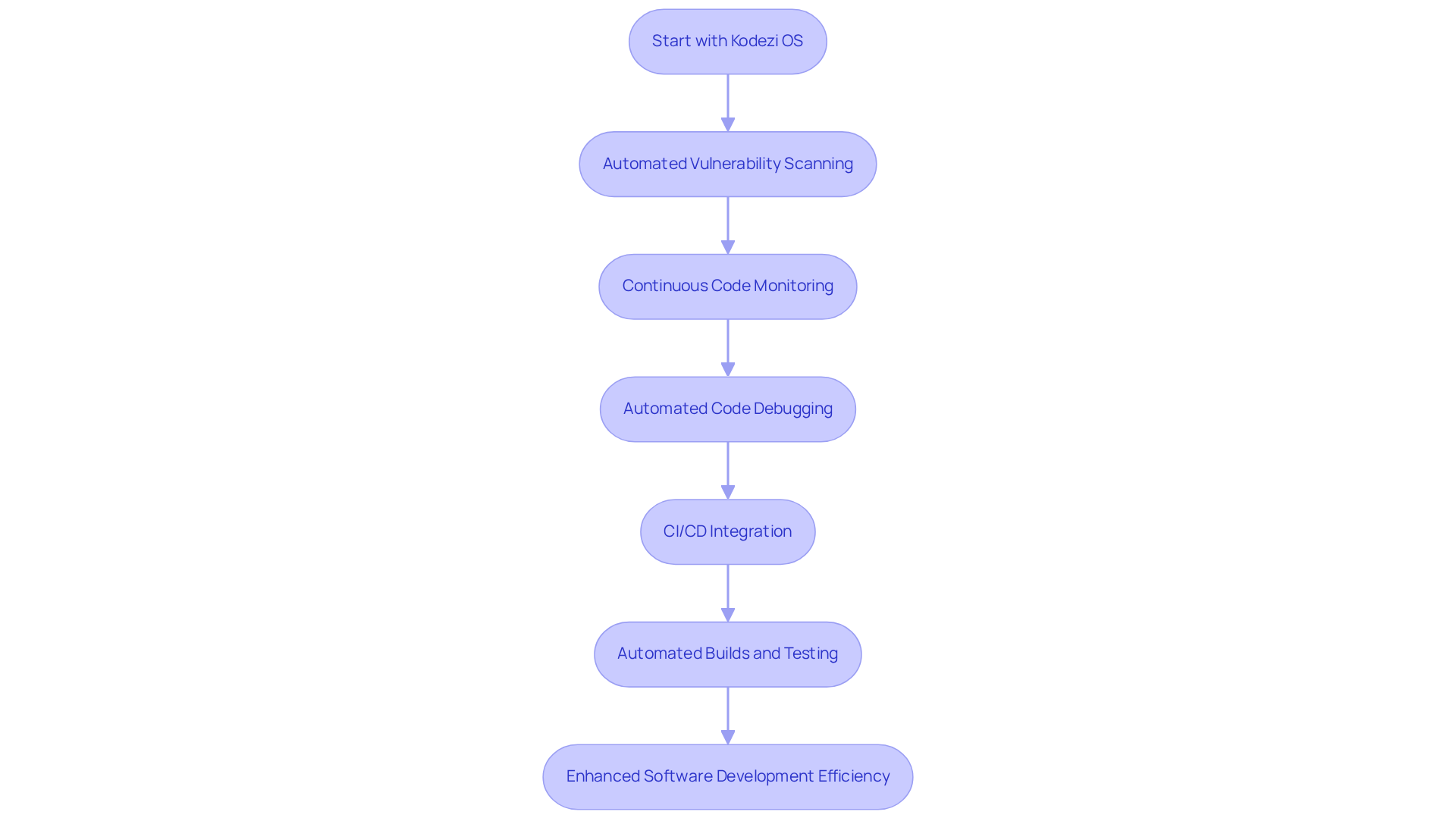
In the fast-paced world of software development, coding challenges can often hinder progress. How can developers ensure their code is not only functional but also secure and efficient? Kodezi OS emerges as a premier OpenAPI specification generator that transforms flaw scanning and code upkeep through automation. By continuously monitoring codebases, ai vulnerability scanning autonomously identifies and rectifies vulnerabilities, ensuring that your code remains both clean and compliant.
This proactive approach enhances security by implementing ai vulnerability scanning, while significantly boosting software development efficiency. With Kodezi OS's automated code debugging features, teams can promptly detect and address codebase problems, gaining comprehensive insights into what occurred and how it was rectified. Furthermore, the seamless integration into CI/CD pipelines allows for timely updates and fixes, making Kodezi OS an essential resource for engineering groups committed to maintaining high-quality code standards.
In addition to these features, Kodezi OS enhances the software development lifecycle through automated builds and testing. This ensures that bugs are caught before they multiply, driving productivity and reducing technical debt. As industry leaders emphasize the necessity of autonomous codebase management, Kodezi OS stands out as a critical tool in the modern developer's toolkit. Are you ready to elevate your coding practices? Explore the tools available on the Kodezi platform and discover how you can drive productivity and reduce technical debt.
DeepSurface Security: Fast and Accurate Vulnerability Detection
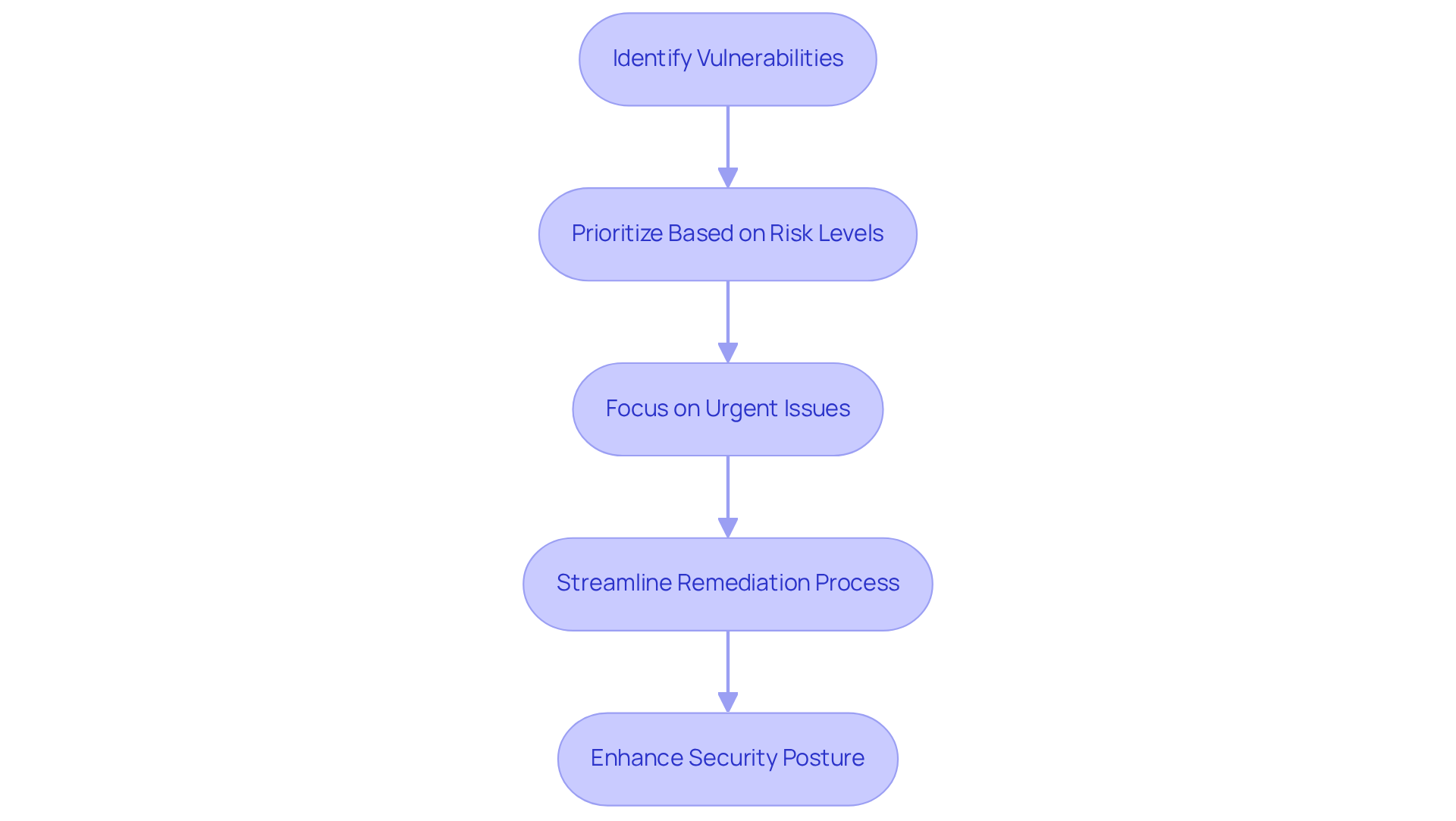
In today's fast-paced digital landscape, organizations face significant security challenges that demand immediate attention. DeepSurface Security stands out by providing rapid and precise flaw detection through sophisticated algorithms that continuously monitor for potential threats in real-time. By prioritizing weaknesses based on their related risk levels, teams can focus on the most urgent issues first. This targeted approach streamlines the remediation process and significantly enhances overall security posture. Organizations utilizing DeepSurface Security have reported substantial time savings, allowing them to address vulnerabilities more quickly than conventional methods.
As Jason Firch, Founder and President of PurpleSec, emphasizes, organizations need to shift their focus from traditional monthly patching routines to addressing weaknesses within days or even hours. This urgency is underscored by the alarming statistic that the average time to identify a weakness currently stands at seven months, highlighting the critical need for tools like DeepSurface Security. Furthermore, with vulnerabilities often exploited within a day of detection, the ability to prioritize efficiently is essential, especially in software development, where swift responses can mitigate risks before they escalate.
The latest trends in real-time risk detection tools highlight the importance of integrating AI vulnerability scanning solutions into current workflows. By doing so, organizations can ensure their security measures keep pace with emerging threats, ultimately fostering a more resilient security environment.
Qualys VMDR: Contextual Prioritization for Effective Risk Management
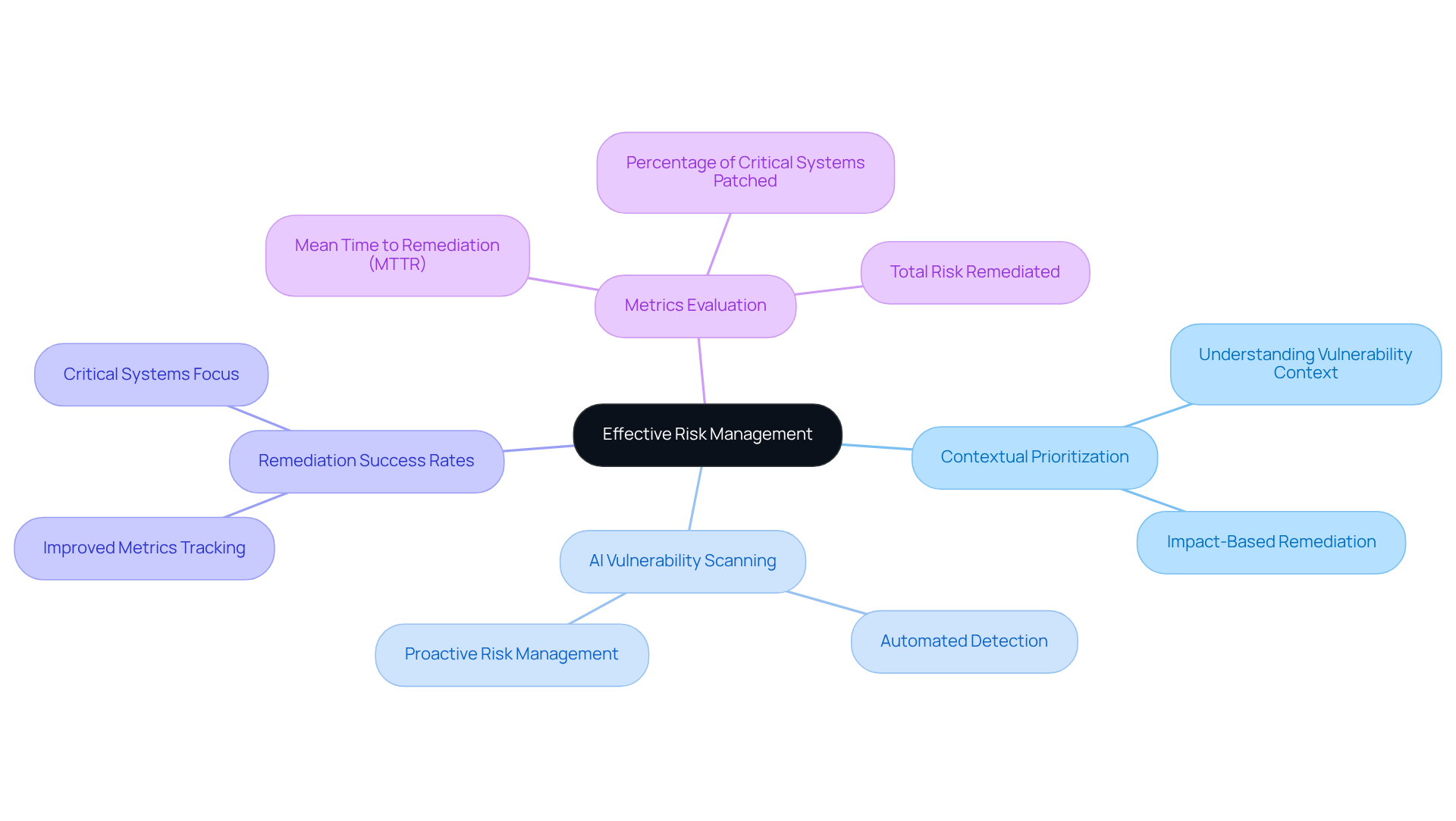
Qualys VMDR stands out for its ability to prioritize vulnerabilities contextually, thereby facilitating AI vulnerability scanning to help organizations manage weaknesses with greater efficacy. By assessing the specific circumstances surrounding these vulnerabilities, it guides teams in prioritizing their remediation efforts based on potential impact. This ensures that resources are allocated efficiently, significantly reducing risks.
Organizations that frequently perform contextual evaluations often report improved remediation success rates, as they can address the most critical weaknesses first. As Vinugayathri Chinnasamy insightfully stated, "Vulnerability management is not just about spotting weaknesses; it is about fixing them effectively and staying ahead of attackers." This perspective underscores the importance of understanding the context in which vulnerabilities arise for effective remediation.
Qualys VMDR embodies this approach by offering insights that assist teams in navigating their complex environments. By integrating contextual information, organizations can enhance their risk remediation processes with AI vulnerability scanning, ensuring they not only identify but also effectively mitigate threats associated with vulnerabilities. This proactive strategy is essential in today's rapidly evolving threat landscape, where timely and informed decision-making is crucial for safeguarding vital assets.
To further bolster their risk management initiatives, organizations should routinely evaluate their metrics, such as the percentage of critical systems updated and mean time to remediation (MTTR), to confirm they are addressing the most pressing vulnerabilities effectively.
Tenable.io: Adaptive Learning for Continuous Improvement in Vulnerability Management
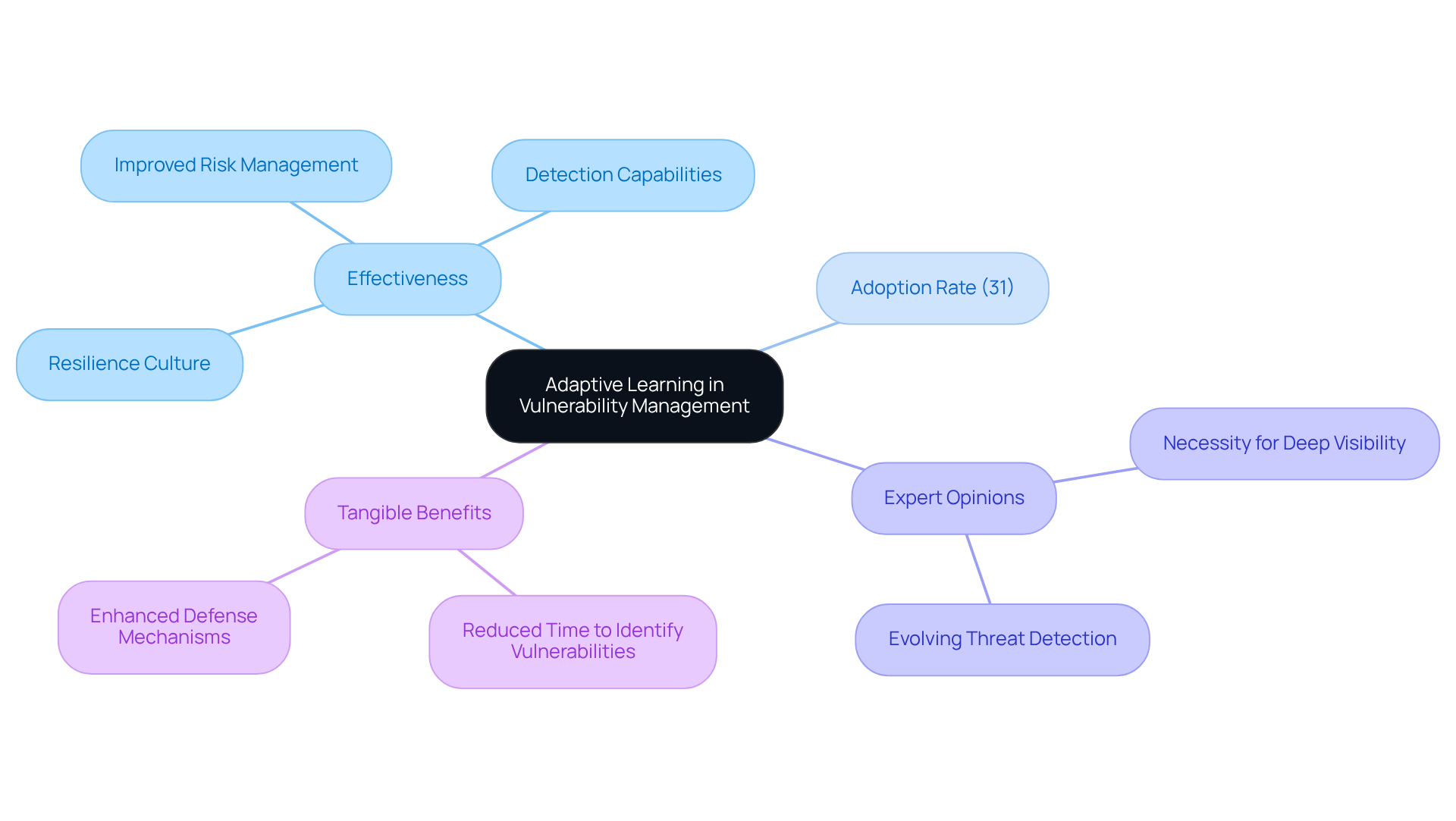
Tenable.io illustrates the effectiveness of adaptive learning in improving risk management processes. By systematically examining historical vulnerabilities and remediation efforts, it enhances its detection capabilities, ensuring that security teams are always ready to address emerging risks. In 2025, 31% of organizations are anticipated to implement adaptive learning methods for risk detection, reflecting a growing acknowledgment of its effectiveness. Cybersecurity experts emphasize that evolving threat detection capabilities are crucial in an era where traditional methods often fall short. For instance, Chaim Mazal cautions that adversarial AI is surpassing existing protective measures, highlighting the necessity for organizations to attain deep visibility into network traffic.
Furthermore, organizations that have implemented continuous improvement strategies have reported a marked decrease in the time taken to identify and remediate vulnerabilities, showcasing the tangible benefits of adaptive learning. This proactive strategy not only enhances defenses but also nurtures a culture of resilience within security teams. Consequently, they are better equipped to stay ahead of increasingly sophisticated cyber challenges. Have you considered how adaptive learning could transform your organization's risk management approach?
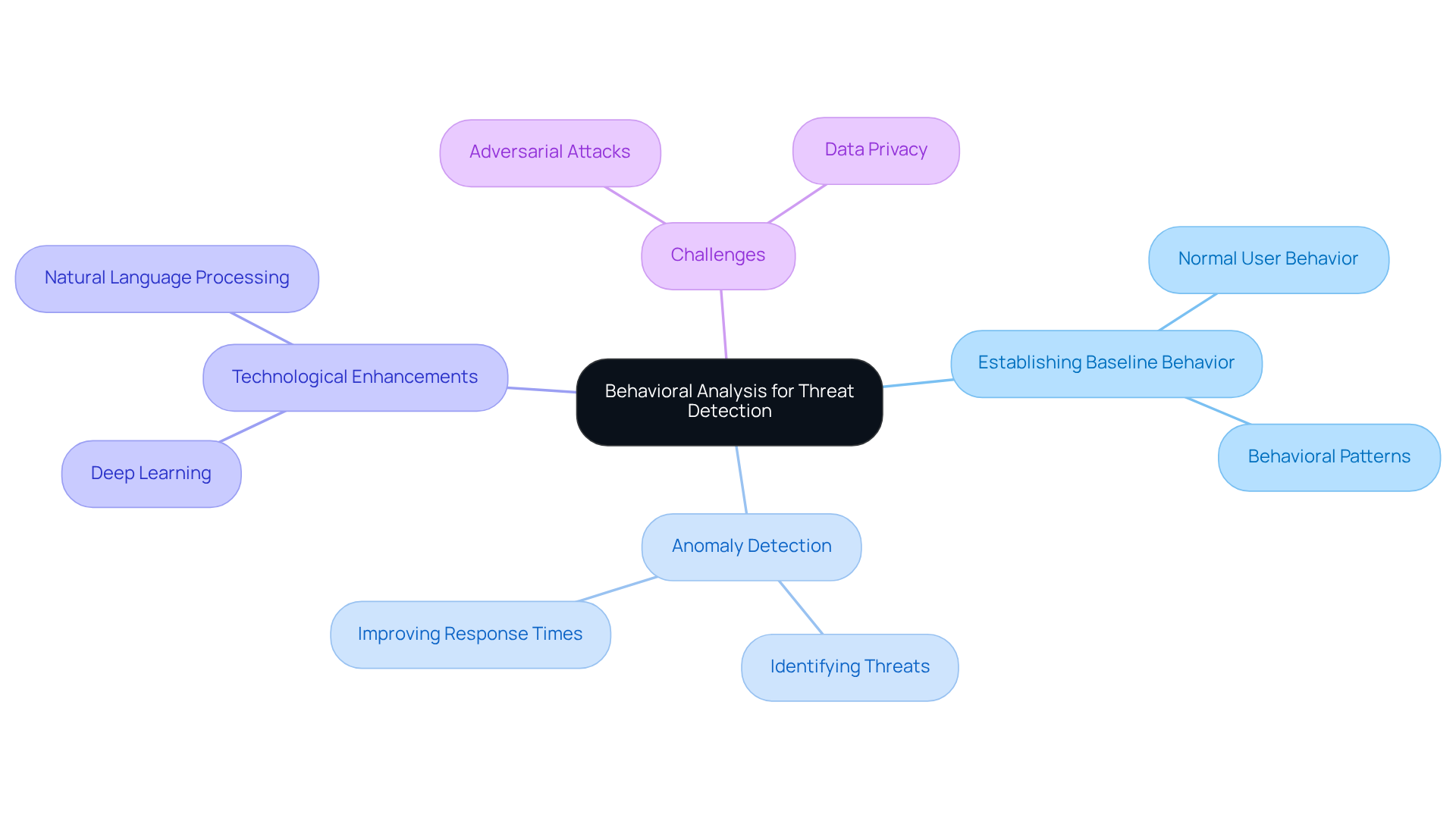
Darktrace PREVENT: Behavioral Analysis for Enhanced Threat Detection
Darktrace PREVENT significantly enhances danger detection capabilities through advanced behavioral analysis. By establishing a baseline of normal user behavior, it effectively identifies anomalies that may signal potential threats. This proactive approach not only improves the speed and precision of threat detection but also equips teams with practical insights to address risks before they escalate.
Organizations employing behavioral analysis have reported notable improvements in their ability to identify and respond to incidents. Professionals in the field stress that a thorough understanding of user behavior is crucial for boosting vulnerability detection rates, ultimately leading to a more robust cybersecurity posture.
Furthermore, incorporating technologies such as Deep Learning (DL) and Natural Language Processing (NLP) can further enhance automated cyber risk detection. However, it is vital to remain vigilant regarding challenges posed by AI, including adversarial attacks and ethical concerns surrounding data privacy.
Notably, case studies, such as the impact of the WannaCry ransomware, illustrate the practical implications of behavioral analysis in cybersecurity.
Microsoft Defender Threat Intelligence: Seamless Integration with Development Workflows
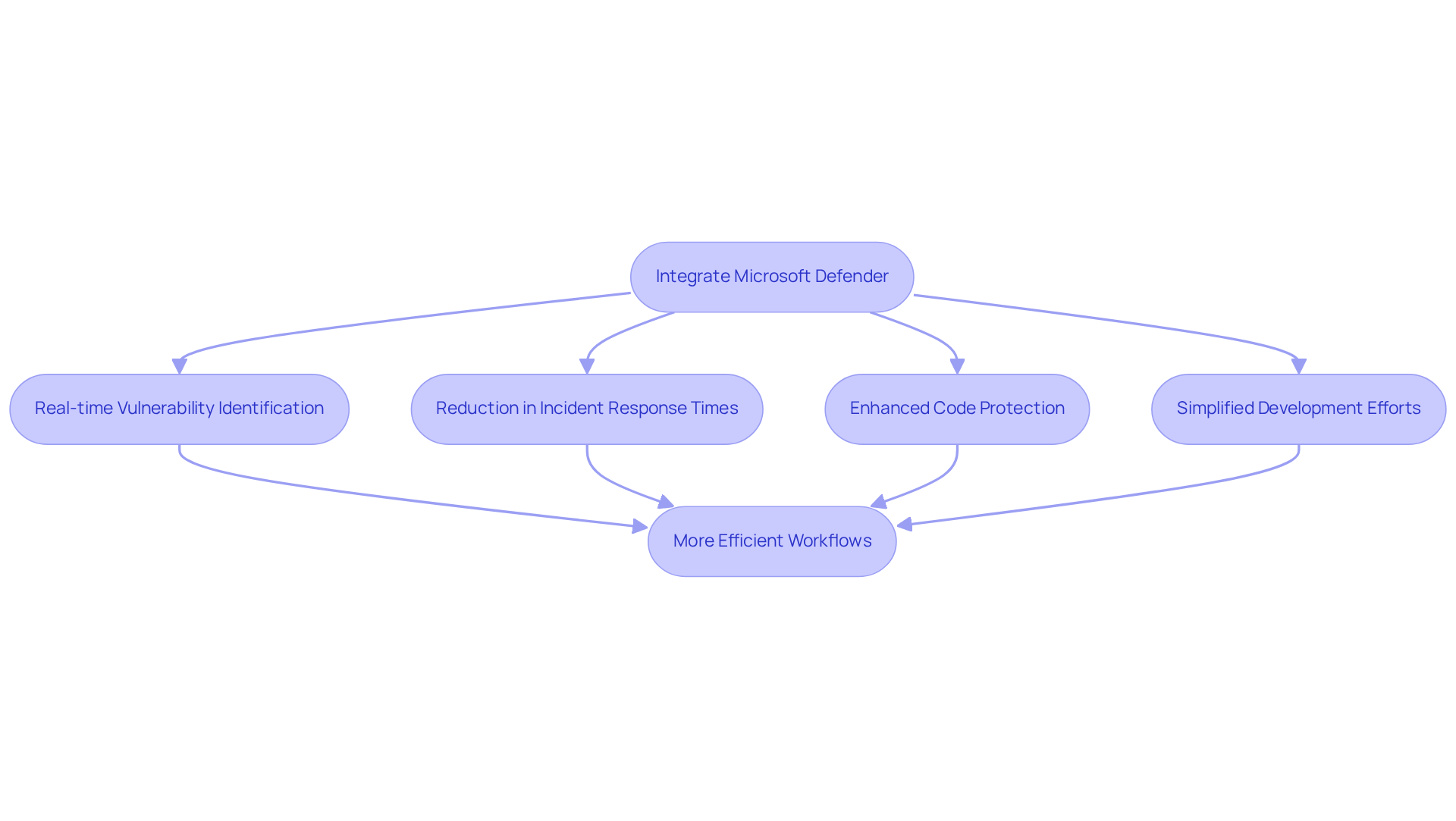
In today's development landscape, security challenges, particularly those addressed by AI vulnerability scanning, are a significant concern for teams striving to maintain productivity. Microsoft Defender Threat Intelligence integrates seamlessly with development workflows, allowing teams to embed essential security measures without disrupting their processes. This integration facilitates real-time identification of weaknesses using AI vulnerability scanning, ensuring that potential threats are swiftly detected and mitigated. Organizations utilizing Microsoft Defender for AI vulnerability scanning have reported a notable reduction in incident response times, which enables them to address vulnerabilities proactively rather than reactively.
Furthermore, industry leaders emphasize that this integration not only enhances code protection but also simplifies development efforts, ultimately resulting in more efficient workflows. By leveraging extensive risk intelligence, teams can focus on innovation while maintaining robust security through AI vulnerability scanning. This demonstrates how contemporary security solutions can bolster productivity without compromising safety. Have you considered how integrating such solutions could transform your development practices? Explore the tools available on the Microsoft Defender platform to enhance your security measures and streamline your workflows.
Rapid7 InsightVM: Comprehensive Coverage for Vulnerability Management
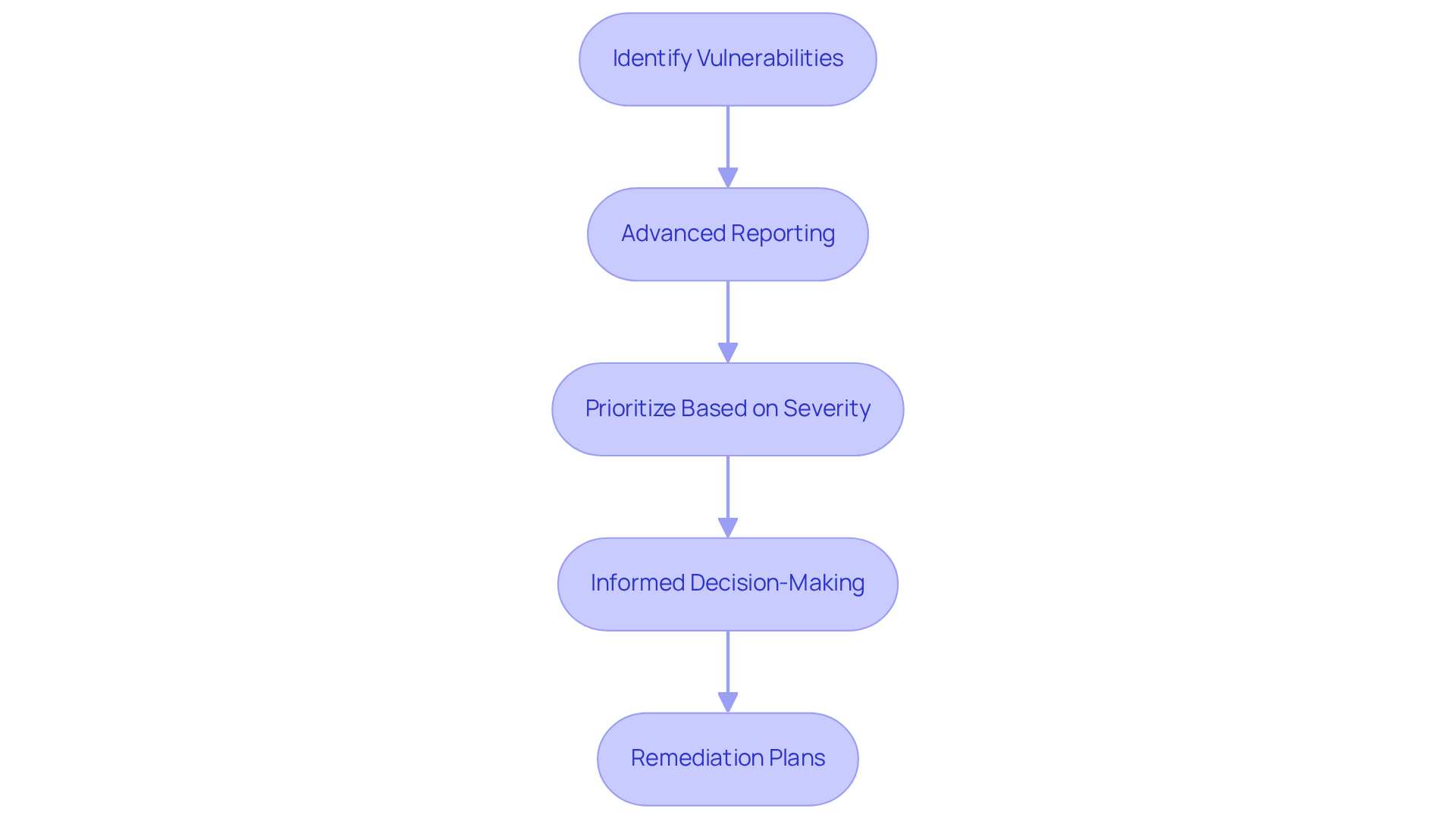
In the ever-evolving landscape of cybersecurity, risk management tools like Rapid7 InsightVM play a pivotal role. They provide extensive coverage that meticulously examines every facet of a codebase for potential threats. This robust tool empowers teams with critical insights through advanced reporting capabilities, enabling them to prioritize vulnerabilities based on severity and context. In 2025, the average reporting capabilities of risk management tools have significantly improved, with many now offering real-time analytics and customizable dashboards that enhance visibility into protective postures.
Furthermore, cybersecurity experts emphasize that effective reporting is essential for addressing weaknesses. It not only aids in detecting flaws but also fosters informed decision-making for remediation plans. As Scott Charney aptly states, "Cybersecurity is not a sprint; it’s a marathon," highlighting the continuous nature of security efforts. Practical applications of comprehensive reporting demonstrate that organizations can substantially reduce their risk exposure by swiftly addressing weaknesses identified through these advanced reporting features.
In addition, as the cybersecurity landscape continues to evolve, tools like Rapid7 InsightVM are indispensable for maintaining a proactive stance against emerging threats. This aligns with the understanding that cybersecurity is not a one-time event; it’s an ongoing process that requires continuous vigilance and adaptation.
Intruder: Cost-Effective AI Vulnerability Scanning Solutions
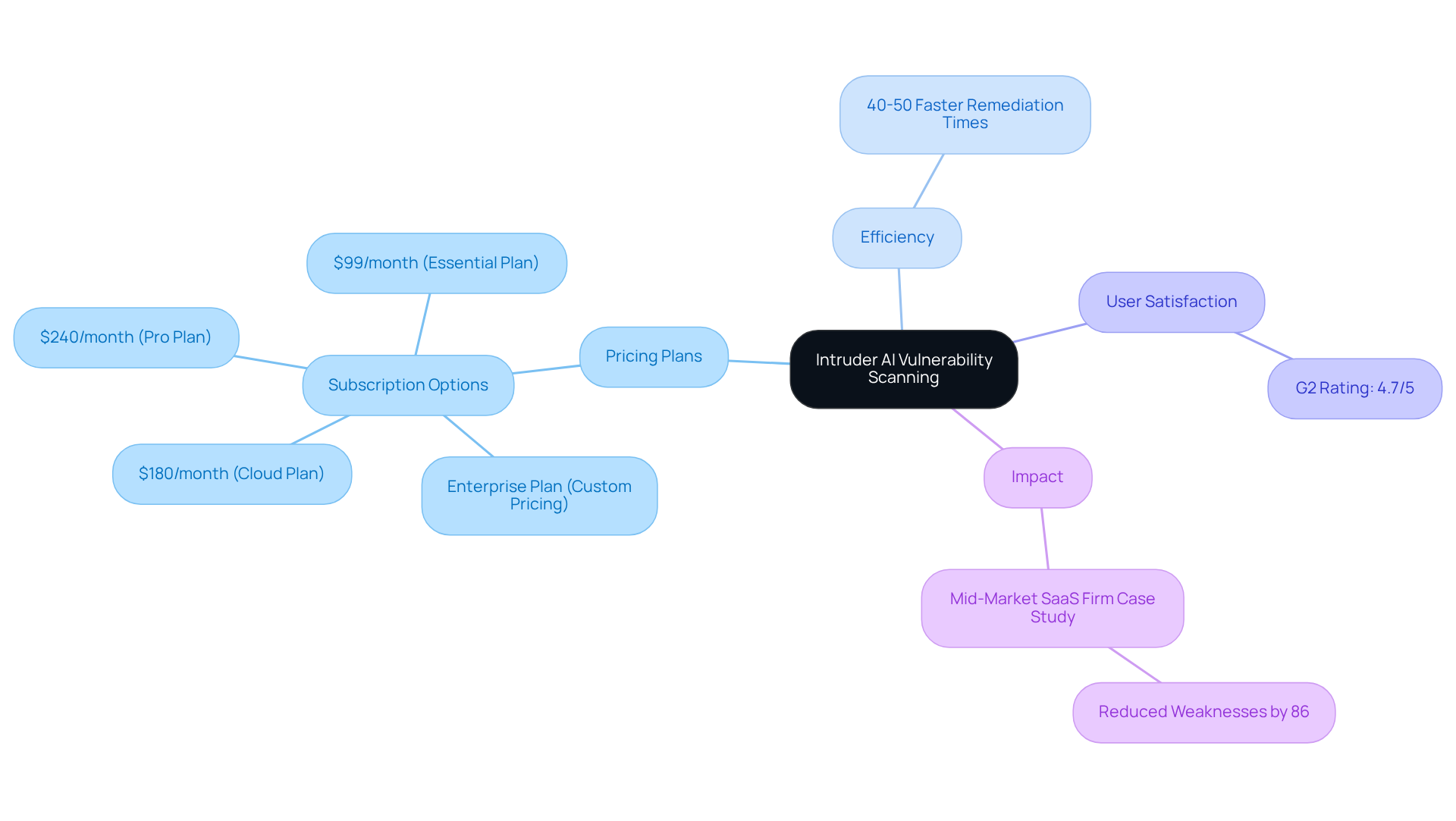
Intruder stands out as an economical solution for AI vulnerability scanning, appealing to organizations with limited budgets. With subscription options starting at just $99 monthly, along with the Cloud Plan at $180/month, Pro Plan at $240/month, and an Enterprise Plan offering personalized pricing, it features an intuitive interface that streamlines the threat detection process. This efficiency allows teams to quickly identify and address vulnerabilities using AI vulnerability scanning without incurring significant expenses, making protective measures more accessible.
Organizations utilizing Intruder report notable cost savings, with many experiencing remediation times that are 40-50% faster, thanks to its automated scanning capabilities. Industry leaders emphasize that affordable security tools like Intruder are essential for democratizing access to robust cybersecurity measures, such as AI vulnerability scanning, ensuring that even smaller teams can effectively manage their risk landscape.
For instance, a mid-market SaaS firm that conducted a thorough evaluation reduced significant weaknesses by 86% within six months, showcasing the potential impact of employing such tools. Furthermore, Intruder boasts a G2 rating of 4.7/5, further enhancing its credibility among users.
Vectra AI Cognito: The Future of AI in Vulnerability Management
Vectra AI Cognito stands out in AI vulnerability scanning, leveraging advanced machine learning algorithms to significantly enhance risk detection capabilities. By continuously analyzing network behavior and identifying anomalies, Cognito empowers teams to proactively address emerging risks before they escalate.
Did you know that 71% of safety stakeholders believe AI-driven solutions excel at risk prevention? Moreover, organizations that utilize AI vulnerability scanning have reported a remarkable 60% improvement in risk detection. This innovative strategy not only streamlines incident response but also shortens the time required to identify and mitigate risks, making it an indispensable asset for organizations striving to strengthen their cybersecurity posture.
As Sohrob Kazerounian from Vectra AI notes, "The incorporation of AI in operational procedures is rising, resulting in decreased breach expenses and enhanced risk detection abilities."
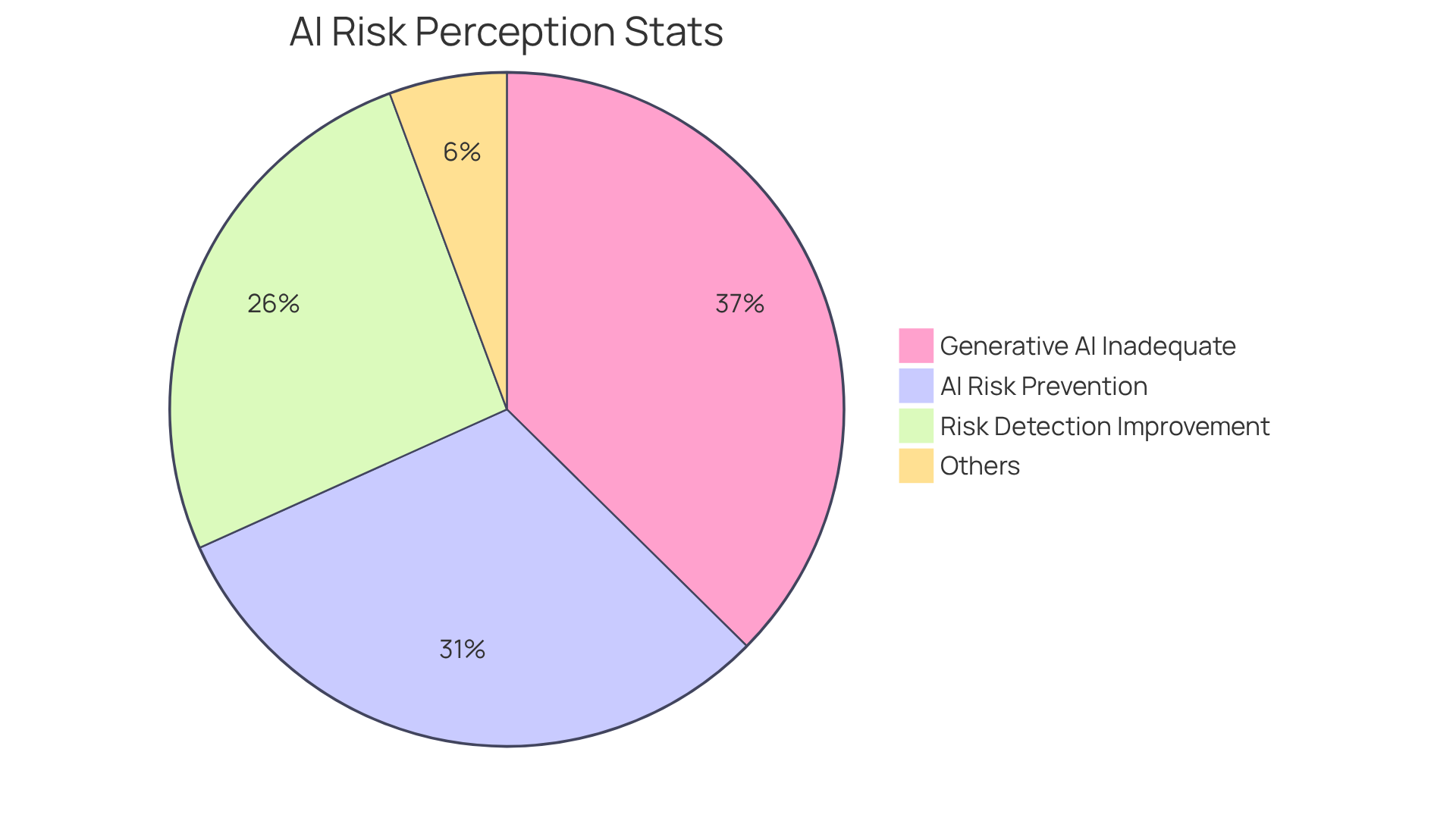
As AI technology continues to evolve, tools like Vectra AI Cognito are crucial for proactive defense measures, such as AI vulnerability scanning, enabling teams to stay ahead of cyber threats. However, it is essential to acknowledge that 86% of security professionals believe that generative AI alone is inadequate to tackle emerging threats, underscoring the necessity for a comprehensive cybersecurity strategy.
Arcanna.ai: Compliance and Governance in AI Vulnerability Management
Arcanna.ai plays a crucial role in AI risk management by prioritizing compliance and governance, essential for organizations navigating complex regulatory environments. How does this impact your organization? By ensuring adherence to industry standards, Arcanna.ai effectively mitigates risks associated with AI deployment. Its robust reporting features streamline vulnerability management and enhance compliance adherence rates through AI vulnerability scanning. This makes it an indispensable tool for organizations in regulated sectors.
As industry leaders emphasize, maintaining rigorous standards in security is essential for safeguarding sensitive data and ensuring operational integrity. Furthermore, the latest trends in compliance tools underscore the necessity for organizations to adopt comprehensive solutions that integrate seamlessly with existing workflows. This fosters a culture of accountability and proactive risk management, ultimately benefiting the entire organization.
Conclusion
The exploration of AI vulnerability scanning tools underscores their vital role in bolstering software security and operational efficiency. In a landscape where cyber threats are increasingly sophisticated, how can organizations effectively safeguard their systems? By leveraging advanced technologies, these tools not only identify and mitigate vulnerabilities but also streamline the development process. This allows teams to focus on innovation without compromising safety.
Throughout the article, key tools such as Kodezi, DeepSurface Security, Qualys VMDR, and others have been discussed. Each offers unique features tailored to meet the diverse needs of organizations. From automated debugging and contextual prioritization to adaptive learning and behavioral analysis, these solutions collectively empower teams to stay ahead of emerging threats. Are you ready to reduce risk exposure significantly?
Adopting these AI-driven tools is not just advantageous but essential. Organizations must prioritize integrating effective vulnerability scanning solutions into their workflows to foster a robust security posture. By doing so, they can navigate the complexities of cybersecurity with confidence, ensuring compliance and governance while enhancing overall productivity. The future of secure software development lies in these innovative technologies—embracing them is a crucial step towards a safer digital environment. Explore the tools available and take action to enhance your security measures today.
Frequently Asked Questions
What is Kodezi OS and what does it do?
Kodezi OS is a professional OpenAPI specification generator that automates vulnerability scanning and code maintenance, ensuring that code remains functional, secure, and efficient.
How does Kodezi OS enhance security in software development?
Kodezi OS enhances security by continuously monitoring codebases and autonomously identifying and rectifying vulnerabilities through AI vulnerability scanning.
What are the benefits of Kodezi OS's automated code debugging features?
The automated code debugging features of Kodezi OS allow teams to promptly detect and address codebase problems, providing comprehensive insights into issues and their resolutions.
How does Kodezi OS integrate into existing workflows?
Kodezi OS seamlessly integrates into CI/CD pipelines, allowing for timely updates and fixes, which is essential for maintaining high-quality code standards.
What additional features does Kodezi OS offer to improve the software development lifecycle?
Kodezi OS offers automated builds and testing, which help catch bugs early, driving productivity and reducing technical debt.
What is DeepSurface Security and what are its key features?
DeepSurface Security provides fast and accurate vulnerability detection using sophisticated algorithms that continuously monitor for potential threats in real-time, prioritizing weaknesses based on their risk levels.
Why is rapid vulnerability detection important for organizations?
Rapid vulnerability detection is crucial because vulnerabilities can be exploited shortly after detection, and organizations need to address weaknesses quickly to mitigate risks.
How does DeepSurface Security change traditional vulnerability management practices?
DeepSurface Security encourages organizations to move away from traditional monthly patching routines to addressing vulnerabilities within days or hours, enhancing their overall security posture.
What is Qualys VMDR and how does it assist in risk management?
Qualys VMDR is a tool that prioritizes vulnerabilities contextually, helping organizations manage weaknesses more effectively by assessing the specific circumstances surrounding those vulnerabilities.
What advantages do organizations gain from contextual evaluations in vulnerability management?
Organizations that perform contextual evaluations often see improved remediation success rates by addressing the most critical weaknesses first, leading to more efficient resource allocation.
How can organizations enhance their risk management initiatives with Qualys VMDR?
Organizations can enhance their risk management initiatives by routinely evaluating metrics such as the percentage of critical systems updated and mean time to remediation (MTTR) to ensure effective vulnerability addressing.




