Overview
In the realm of software development, developers often face significant challenges, including security vulnerabilities that can hinder progress. How can these issues be effectively addressed? Automated vulnerability scanning emerges as a powerful solution, enhancing efficiency and security in the development process. This article explores the numerous benefits of automated vulnerability scanning, such as:
- Improved security posture
- Reduced human error
- Substantial time savings
Organizations leveraging these tools experience faster identification of issues, leading to enhanced compliance and a more robust development process. Furthermore, the data supports these claims, showcasing that teams utilizing automated scanning tools can streamline their workflows and focus on delivering quality software.
Why should developers consider integrating automated vulnerability scanning into their practices? The advantages are compelling: not only does it minimize the risk of human error, but it also accelerates the overall development timeline. In addition, the enhanced security measures contribute to a more resilient software product, ultimately benefiting both developers and end-users alike.
For those looking to improve productivity and code quality, exploring the tools available for automated vulnerability scanning is a crucial step. By adopting these technologies, developers can transform their approach to security, ensuring a more efficient and effective development lifecycle.
Introduction
In an era where cyber threats are increasingly sophisticated, developers face significant challenges in maintaining security. Automated vulnerability scanning emerges as a game-changer, providing a streamlined approach to identifying and mitigating risks before they escalate. This article explores the myriad benefits of automated vulnerability scanning, revealing how it not only enhances security but also boosts efficiency in development processes. What if the key to a more secure and productive coding environment lies in embracing automation? By leveraging automated tools, developers can focus on writing quality code while ensuring robust protection against vulnerabilities.
Kodezi | Professional OpenAPI Specification Generator - AI Dev-Tool: Enhance Security and Compliance
Developers often encounter significant challenges when it comes to coding, particularly in ensuring the security and compliance of their APIs. The operating system automates the creation of OpenAPI specifications, which are crucial for defining APIs in a secure and compliant way. By ensuring that APIs comply with industry standards, automated vulnerability scanning assists groups in avoiding vulnerabilities that could emerge from poorly defined interfaces.
Furthermore, automated vulnerability scanning not only saves time but also enhances the overall protection stance of applications. It ensures that all endpoints are documented and compliant with regulations, which is essential for maintaining security. In addition, the CLI enhances engineering groups by integrating quality, safety, and efficiency through automated code evaluations. This alignment of API documentation with code modifications further reinforces the integrity of the codebase, making it a powerful tool for developers.
Have you considered how much more productive your team could be with such tools? By leveraging these features, teams can significantly improve their coding practices and overall project outcomes. Explore the tools available on the platform to see how they can transform your development process.
Proactive Vulnerability Identification: Stay Ahead of Threats
In the fast-paced world of software development, identifying potential coding challenges is crucial. Automated vulnerability scanning empowers teams to pinpoint possible risks before they can be exploited. By consistently tracking the codebase, the Kodezi CLI detects weaknesses in real-time, allowing teams to address issues proactively. This autonomous solution not only mitigates risks but also fosters a culture of security awareness within development teams, ensuring that security remains a priority throughout the development lifecycle.
Organizations utilizing Kodezi CLI's automated vulnerability scanning experience a remarkable 30-50% faster identification of issues, significantly reducing the average exposure time from discovery to resolution. As cybersecurity specialists emphasize, maintaining extensive detection coverage and swiftly addressing vulnerabilities can greatly diminish the risk of exploitation and data breaches. In fact, in 2025, it was noted that 68-75% of high-severity issues are resolved within service-level agreements, underscoring the continuous need for efficient automated solutions.
By integrating automated vulnerability scanning into the CLI, teams can enhance their protective measures and compliance, leading to a more robust development environment. Are you ready to elevate your coding practices and ensure your team's security? Explore the tools available on the Kodezi platform and experience the benefits of improved productivity and code quality.
Time and Resource Efficiency: Streamline Security Processes
Developers often encounter significant challenges in managing coding and security processes. Automated vulnerability scanning effectively addresses these issues, enhancing the efficiency of risk evaluations while significantly reducing time and resource costs. By automating routine checks, the command-line interface (CLI) allows developers to concentrate on coding and feature implementation, alleviating the burden of manual processes. This transformation not only accelerates development timelines but also guarantees that security protocols are consistently upheld without the need for extensive manual oversight.
Furthermore, the AI-driven features of automated vulnerability scanning tools enable independent assessment and resolution of issues before they reach production. This proactive approach not only improves code quality but also boosts overall efficiency. Organizations that have adopted automated vulnerability scanning tools report substantial resource savings and a marked reduction in human errors, which leads to more reliable evaluations. This shift empowers cybersecurity teams to tackle more complex challenges effectively.
In addition, firms implementing automated vulnerability scanning, especially with tools like Kodezi, simplify their protective measures and enhance their operational effectiveness. They are better equipped to respond swiftly to emerging threats. To optimize automated flaw detection, organizations should evaluate their current protective measures and consider integrating a command-line interface, thereby improving resource distribution and operational efficiency.
Continuous Monitoring: Real-Time Threat Detection
Ongoing surveillance serves as a vital element in effective risk management. Have you ever considered the coding challenges developers face today? Kodezi OS stands out with its real-time threat detection, enabling teams to swiftly tackle emerging vulnerabilities. This proactive method ensures that protective measures evolve alongside the codebase, maintaining a secure environment.
Organizations that implement automated vulnerability scanning along with continuous monitoring have seen significant improvements in their security posture. In fact, AI-driven systems can identify threats up to five times faster than traditional methods. For example, companies utilizing this operating system can contain breaches in an average of 214 days, compared to 322 days for those dependent on legacy systems.
Cybersecurity professionals stress the importance of real-time detection; 70% believe AI is highly effective at spotting threats that might otherwise go unnoticed. Furthermore, by integrating ongoing monitoring with Kodezi's automated vulnerability scanning features, teams can quickly identify and resolve codebase issues, enhancing performance and ensuring compliance with the latest safety best practices.
Setting a benchmark for typical user behavior is essential for detecting unusual changes that may indicate potential threats. To maximize the benefits of ongoing monitoring, teams should regularly evaluate and update their security measures, utilizing automated vulnerability scanning to ensure they adapt to new vulnerabilities as their codebases grow.
Compliance Assurance: Meet Industry Standards and Regulations
For organizations aiming to comply with industry standards and regulatory requirements, automated vulnerability scanning is crucial. The operating system plays a vital role by continuously monitoring adherence to security protocols, which streamlines the compliance process for teams. This proactive strategy not only protects organizations from potential fines but also significantly boosts their reputation in the marketplace.
Furthermore, the CLI serves as a versatile tool for B2B engineering teams, autonomously enhancing codebases and resolving bugs before they reach production. This ensures that compliance is maintained without sacrificing productivity.
Why not experience these advantages firsthand? Sign up for a free trial or demo today!
Seamless Integration: Enhance Existing Development Workflows
In the fast-paced world of software development, developers often face significant challenges in maintaining code quality while utilizing automated vulnerability scanning to ensure security. Kodezi OS addresses these issues head-on, seamlessly integrating with current development workflows to enhance protective measures without disrupting the development process. By partnering with platforms such as GitHub and CI/CD pipelines, Kodezi OS incorporates safety checks directly into the development lifecycle.
This proactive approach allows teams to maintain productivity while prioritizing safety, a crucial aspect of modern development, especially through automated vulnerability scanning. Organizations that implement these integrated solutions have reported not only improved protective measures but also enhanced developer efficiency with the use of automated vulnerability scanning. This demonstrates that automated vulnerability scanning in protection can indeed coexist with agile development practices.
As industry leaders emphasize, the future of development hinges on the ability to balance safety and productivity. Kodezi enables teams to innovate confidently, ensuring that protection is never compromised. Are you ready to explore how Kodezi can transform your development experience? Discover the tools available on the platform and take the first step towards a more secure and efficient coding environment.
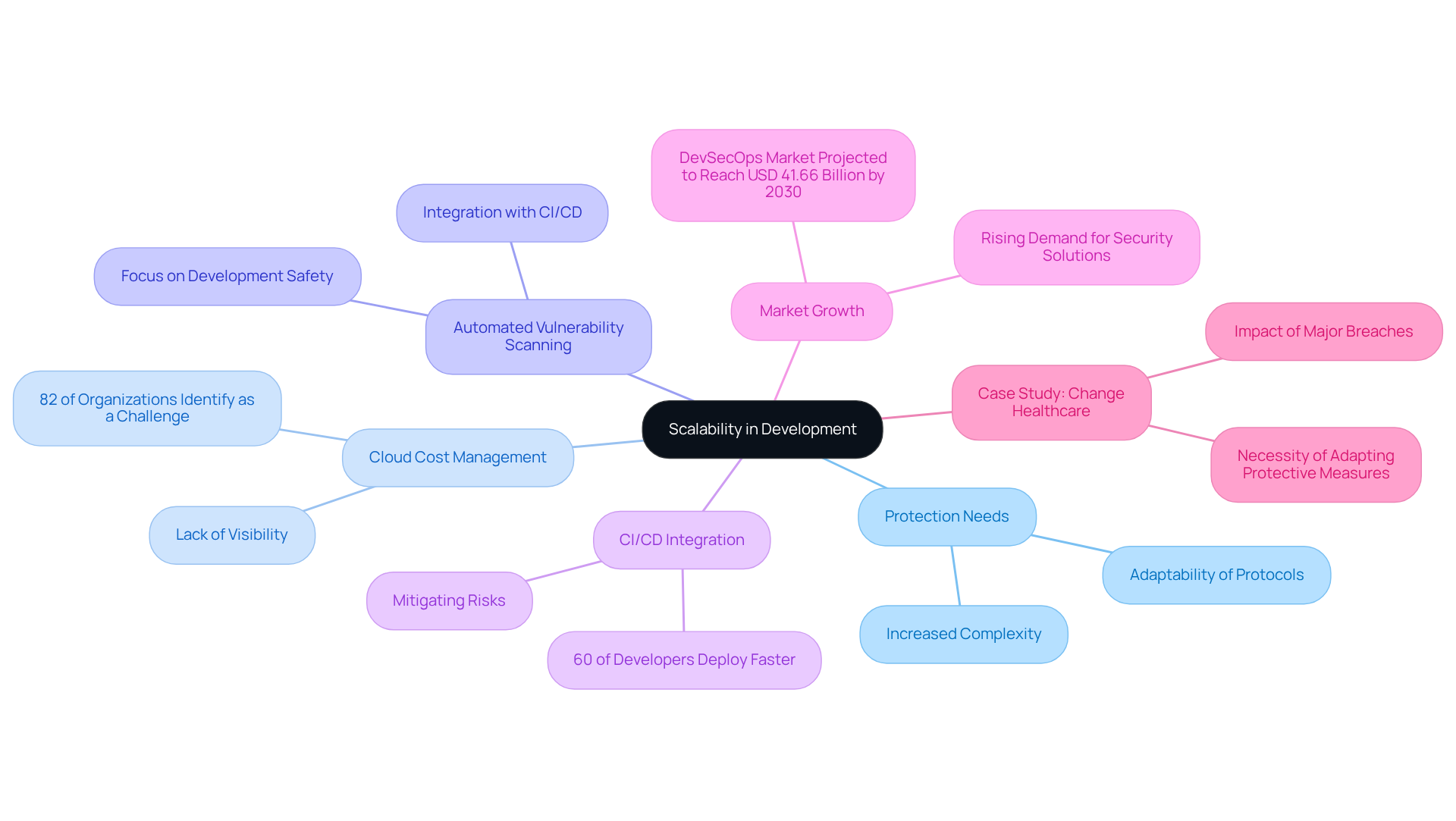
Scalability: Adapt to Growing Development Needs
As development teams expand, the complexities of their protection needs intensify. Have you ever considered how these challenges can impact your coding practices? The CLI tool is designed to scale seamlessly with your organization, adeptly managing the growing intricacies and volume of code. This adaptability ensures that protective protocols remain robust and effective, regardless of the codebase size or the number of developers involved.
With 82% of organizations identifying cloud cost management as a significant challenge in safeguarding, this tool helps tackle the issue through automated vulnerability scanning of protective processes. This automation allows teams to focus on development without compromising safety. Furthermore, as 60% of developers report deploying code at an accelerated pace, the CLI tool integrates safeguards into the CI/CD pipeline, mitigating risks associated with rapid development.
Organizations like Change Healthcare underscore the necessity of adapting protective measures to cope with increased code complexity, especially in the wake of major breaches caused by misconfigurations. By leveraging the CLI, teams can ensure that their protective measures not only keep up with growth but also enhance overall code integrity and compliance.
As the DevSecOps market is projected to reach USD 41.66 billion by 2030, the significance of automated vulnerability scanning solutions that evolve with development practices cannot be overstated. Are you ready to explore the tools available on our platform to elevate your coding practices and safeguard your projects?
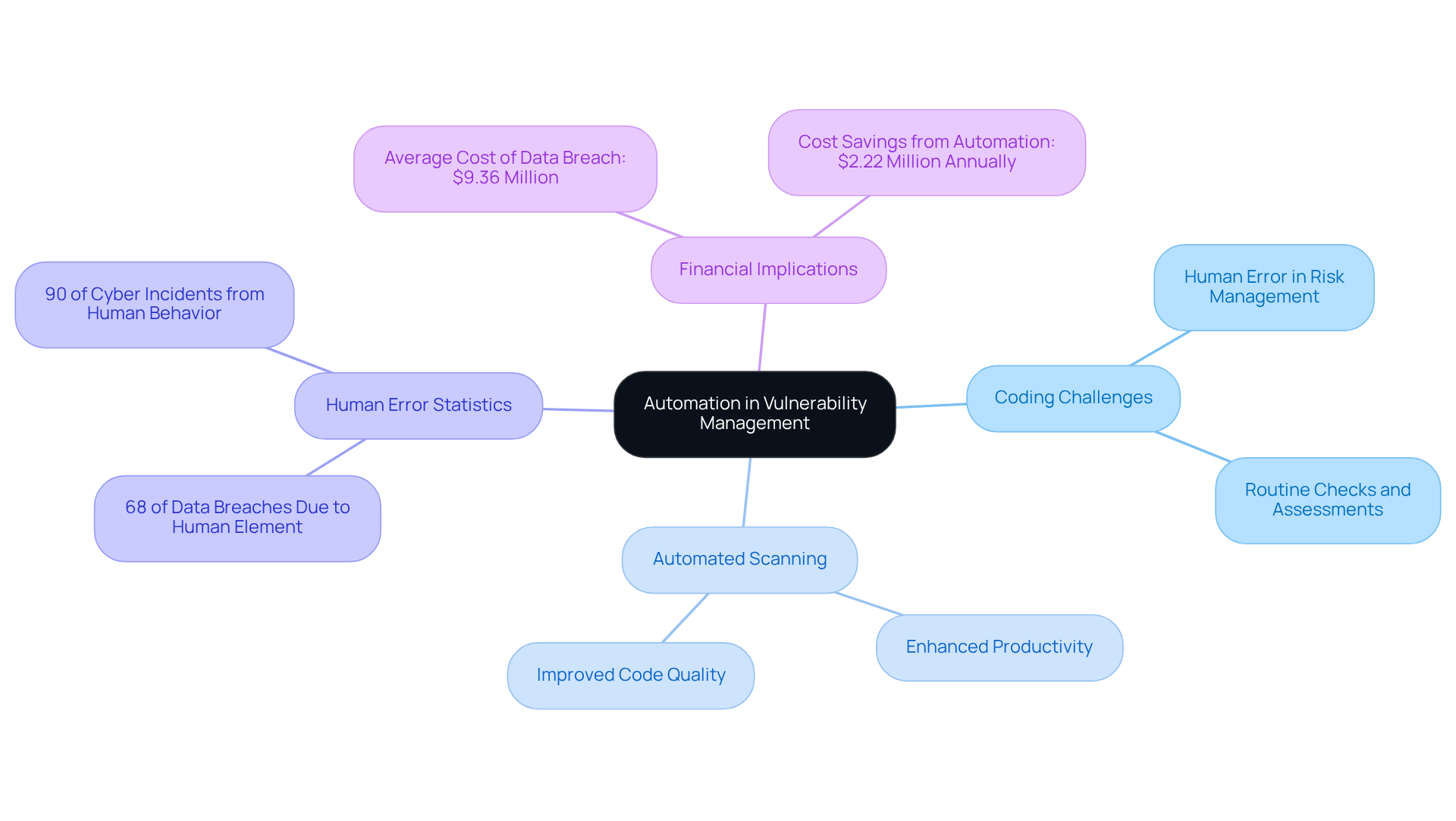
Reduced Human Error: Enhance Accuracy in Vulnerability Management
Coding challenges are a common hurdle for developers, often leading to human error in risk management. The role of automated vulnerability scanning is crucial in mitigating these issues. Kodezi CLI addresses these challenges by automating routine checks and assessments, significantly enhancing programming productivity and improving code quality. By autonomously fixing bugs before they reach production, Kodezi not only reinforces protective measures but also instills greater confidence among development teams.
As organizations progressively embrace automation, they can anticipate improved accuracy in inspections, which results in stronger protections against cyber threats. Furthermore, according to the Verizon report, the human element is the root cause of 68% of data breaches, underscoring the critical need for automation. In addition, the average cost of a data breach in the U.S. is $9.36 million, highlighting the financial implications of human error. Companies utilizing automated vulnerability scanning have reported reductions in incident response times and decreases in successful attacks, illustrating the transformative impact of technology in this critical area.
Imagine the efficiency gains when your team can focus on innovation rather than fixing bugs. Explore Kodezi's tools to experience these benefits firsthand. With Kodezi, you can not only improve your code quality but also enhance your overall development process.
Detailed Reporting: Informed Decision-Making for Security
Organizations today face significant challenges in managing vulnerabilities and assessments. Kodezi OS addresses these challenges by providing extensive reporting that enables informed decision-making regarding protective strategies. These reports deliver essential insights into potential risks and the effectiveness of current measures. Consequently, teams can prioritize their efforts and allocate resources efficiently.
Furthermore, this data-focused approach not only enhances overall safety but also aligns with industry trends. Notably, 70% of compliance and risk management leaders anticipate that AI will significantly influence their roles in the coming years. By adopting Kodezi OS, organizations can proactively manage risks, ensuring their protective measures evolve alongside emerging threats.
In addition, the benefits of utilizing Kodezi extend beyond mere compliance. The platform empowers teams to improve productivity and code quality, making it a valuable asset in today’s fast-paced environment. Are you ready to enhance your risk management strategies? Explore the tools available on Kodezi and take the first step towards a more secure future.
Improved Security Posture: Strengthen Defense Against Threats
For organizations aiming to enhance their security posture, implementing automated vulnerability scanning is crucial. Developers often face significant coding challenges, and the CLI tool, known as the B2B Swiss Army Knife for Engineering Teams, plays a vital role in addressing these issues. By autonomously improving code quality and resolving problems before they reach production, this tool ensures that vulnerabilities are addressed proactively. It continuously monitors for weaknesses, guarantees compliance, and provides comprehensive insights that facilitate informed decision-making.
By integrating Kodezi CLI into their workflows, development teams can cultivate a culture of safety awareness while boosting coding efficiency. For a quick start, teams can take advantage of a 5-minute quickstart guide and view a demo to better understand its capabilities. Have you considered how much human error contributes to cyber incidents? Statistics reveal that 90% of such incidents stem from mistakes, underscoring the necessity for robust protective measures. Organizations employing proactive strategies, such as automated vulnerability scanning through CLI tools, can significantly mitigate risks associated with vulnerabilities. For example, companies that adopt automated vulnerability scanning along with patch management report an average annual savings of $2.22 million compared to those that do not.
Furthermore, organizations such as Google have showcased the effectiveness of proactive cybersecurity measures, successfully thwarting large-scale attacks through continuous monitoring and rapid response tactics. By utilizing tools like Kodezi CLI, companies can not only fortify their defenses against software threats but also ensure that their protective practices evolve alongside the increasing complexity of cyber threats. This commitment to proactive security is essential in today’s landscape, where the frequency of cyberattacks has doubled since the COVID-19 pandemic. The urgent need for organizations to remain vigilant and prepared has never been clearer.
Conclusion
Automated vulnerability scanning stands as a pivotal solution to the coding challenges developers encounter, significantly enhancing the efficiency and security of software development practices. By integrating these advanced tools into the development lifecycle, organizations can proactively identify and mitigate vulnerabilities, streamline compliance processes, and ultimately foster a culture of security awareness among teams.
The article underscores several key benefits of automated vulnerability scanning, such as:
- Improved identification of threats
- Time and resource efficiency
- Continuous monitoring
- Enhanced compliance assurance
These tools not only alleviate the burden of manual oversight but also empower teams to focus on innovation while maintaining robust security measures. Furthermore, the seamless integration of these solutions into existing workflows ensures uninterrupted productivity while safeguarding projects.
As the cybersecurity landscape evolves, the adoption of automated vulnerability scanning becomes increasingly crucial. Organizations are encouraged to embrace these technologies to fortify their defenses against escalating cyber threats. By prioritizing proactive security measures and leveraging the capabilities of tools like Kodezi, teams can enhance their overall coding practices, improve operational efficiency, and protect their projects from potential vulnerabilities.
Frequently Asked Questions
What is Kodezi and how does it help developers?
Kodezi is a professional OpenAPI specification generator that automates the creation of OpenAPI specifications, crucial for defining APIs securely and in compliance with industry standards. It enhances security by ensuring that APIs are well-defined, which helps avoid vulnerabilities.
How does automated vulnerability scanning benefit software development?
Automated vulnerability scanning helps teams identify potential coding risks proactively, allowing them to address issues before they can be exploited. It also improves the speed of issue identification by 30-50%, reducing the average exposure time from discovery to resolution.
What impact does Kodezi’s CLI have on coding practices?
The Kodezi CLI integrates quality, safety, and efficiency through automated code evaluations, aligning API documentation with code modifications. This enhances the integrity of the codebase and improves overall coding practices and project outcomes.
How does automated vulnerability scanning streamline security processes?
Automated vulnerability scanning enhances the efficiency of risk evaluations, reduces time and resource costs, and allows developers to focus on coding rather than manual security checks. This approach ensures security protocols are consistently upheld without extensive manual oversight.
What are the advantages of using Kodezi's automated vulnerability scanning tools?
Organizations using Kodezi's automated tools report substantial resource savings, a reduction in human errors, and improved code quality. These tools enable independent assessment and resolution of issues before they reach production, enhancing overall efficiency.
How can teams improve their protective measures with Kodezi?
By integrating automated vulnerability scanning into their processes, teams can enhance their protective measures and compliance, leading to a more robust development environment and better preparedness against emerging threats.
What should organizations consider when implementing automated vulnerability scanning?
Organizations should evaluate their current protective measures and consider integrating a command-line interface to optimize automated flaw detection, improve resource distribution, and enhance operational efficiency.




