Introduction
Static code analysis tools have become indispensable in modern software development, aiding in the quest for security, reliability, and code excellence. These tools employ advanced techniques to analyze codebases, identifying vulnerabilities, inefficiencies, and deviations from industry standards.
In this article, we will explore a range of static code analysis tools, including PVS Studio, Parasoft, Coverity, SonarQube, Clang-Tidy, Polyspace, CppCheck, ASAN/TSAN, Codium.ai, and HelloBar. Each of these tools offers unique features and benefits that can significantly enhance code security and productivity. Let's dive into the world of static code analysis and discover how these tools can revolutionize your development process.
The deployment of Static Code Analysis (SCA) tools is a significant advance in the development of secure software, diving deep into the codebase without execution to unearth issues that might compromise system quality, including buffer overflows, memory leaks, and code injections. Such analysis is integral to fostering a culture of quality keeping your software reliable and trustworthy.
Christophe Limpalair, who founded Cybr after recognizing the challenges organizations face in software security, emphasizes this integration of SCA in his teachings about Infrastructure as Code (IAC) scanning and adopting Policy as Code principles. The process of adopting SCA tools is not without its considerations.
There's an imperative to comprehend the broader context of system quality, evaluating metrics such as resilience and trustworthiness. This understanding positions the analysis tools to function optimally within your existing environment, addressing the 'what' and 'why' of SCA at every phase of the software lifecycle.
For example, the software's security and privacy requirements must be clear from the onset, involving threat models and data flow diagrams to align with regulatory standards and anticipate evolving threats. Looking beyond mere bug detection, SCA should be seen as part of a broader trend analysis, scrutinizing patterns over time and generalizing remedies for the industry. This aligns with insights from studies suggesting that a strategic selection of SCA tools is vital for enhancing software reliability and the development process. By examining these patterns, we gain insight into the progress of software quality initiatives corporate-wide, and can discern whether a quality improvement program might be necessary, thus elevating software security from dire to robust.
Harnessing the potential of PVS Studio's static code analysis can transform your C/C++/C# projects, elevating security to remarkable new heights. This tool excels in uncovering a multitude of problematic code patterns — ranging from the perilous null pointer dereferences to the subtle, yet critical, uninitialized variables.
Add to this its prowess in mitigating incorrect arithmetic expressions and curtailing buffer overflows, and you have a formidable ally in the quest for code security. Detailed reports generated by PVS Studio facilitate a swift response to complications, allowing developers to pinpoint vulnerabilities with precision.
The tool's intuitive interface further simplifies navigation through the complex landscape of code security, ensuring a smooth remediation process. Reflecting on real-world applications, such as the examination of the iconic Quake World's codebase, we learn the significance of learning from code — both our own and that of others.
In spite of challenges, analyzing such a project can unearth practical insights that are beneficial to the wider programming community. As recent discussions in the tech space underscore the crucial role of programming language safety — accentuated by the pressing need for secure cyberinfrastructure — tools like PVS Studio become central to the discourse. They echo the sentiment in the industry, aligning with guidance from authoritative resources like NISTIR 8397 on software security, underscoring the importance of reliable coding standards across various programming languages. Moreover, the growing conversations about memory-safe languages and their impact on software safety prompt a reflection on the essential practices for developing code that is not only secure but also safe, further highlighting the essential role that tools like PVS Studio play in modern software development.
Parasoft stands out as a distinguished static code analysis tool that accommodates a variety of programming languages including C/C++, Java, and .NET. What sets Parasoft apart is not just its broad language support, but its extensive suite of security rules and robust guidelines designed to uphold both code quality and security integrity. Leveraging sophisticated analysis mechanisms, this tool has a proven capability to pinpoint an array of issues such as vulnerabilities, memory leaks, and deviations from coding standards.
Under the guidance of experts like Prashant KV, with over 15 years in information security, Parasoft equips developers with precise, actionable advice. Balancing in-depth experience with application security and a developer's perspective, the insights provided help developers tackle issues efficiently and bolster the security posture of their codebases. This dedication to enhancing cybersecurity skills at all levels mirrors the spirit of Prashant's conferences, where training days cater to various expertise levels – from novice programmers to enterprise security professionals – all with a focus on hands-on, transformative education.
Utilizing the state-of-the-art static analysis tool Coverity, developers can significantly improve the security and reliability of complex software projects. Coverity excels in probing the intricate components of software written in diverse languages including C/C++, Java, and C#.
It meticulously scrutinizes the code to unearth a plethora of defects such as memory corruption, resource leaks, and race conditions, as well as multiple security vulnerabilities. The power of Coverity lies not only in its capacity to identify defects but also in its ability to track trends over time.
By analyzing the ebb and flow of software quality, companies can ascertain whether their software developments are evolving towards greater excellence or if there's an urgent need for a remedial quality program. Additionally, the importance of embedding software security early in the development process—often termed as ‘shift left’—cannot be overstated. In domains where embedded software commands vital systems, such as automotive and aerospace industries, an overlooked flaw can result in grave outcomes, including system failures or unauthorized access. Coverity serves as a vigilant guard, providing comprehensive reports and integrating seamlessly with mainstream development tools, ensuring that such systems are built on a foundation of security and safety from the outset.
SonarQube excels as a versatile static code analysis tool that not only supports a myriad of programming languages but also stands as the embodiment of what it means to instill clean code practices. It thrusts forward an extensive set of rules focused on unearthing security vulnerabilities, code smells, and the bane of developers - technical debt.
It pushes the agenda of 'Clean Code', insisting that code should not only function flawlessly but also be crafted in such a way that it stands as a clear, maintainable beacon for any future voyagers in the codebase. Emphasizing quality code that shines with readability and simplicity, SonarQube becomes the vigilant overseer that provides developers with immediate insights on code health.
Complex constructs are avoided and a clear convention throughout the codebase is promoted. By embedding itself within CI/CD pipelines, SonarQube ensures that the code's clarity and security are not afterthoughts but integral parts of the continuous integration process. It serves as the lighthouse guiding ships safely into the harbor, ensuring that each iteration maintains the gold standard for code excellence. Integration with development workflows turns SonarQube not just into a tool, but a vital companion for any team striving to elevate their code to its highest potential.
Dive into the realm of code security with Clang-Tidy, a powerhouse static analysis tool essential for C and C++ developers. As part of the Clang compiler suite, the tool offers an arsenal of checks designed to unveil and resolve potential security vulnerabilities. But that's just the beginning.
With a core focus on enhancing code quality, Clang-Tidy also identifies performance bottlenecks and coding style discrepancies. Follow a structured pathway to mastering this tool, starting with acquiring the open-source Clang project and progressing to constructing your static analysis tool using Clang's front-end libraries to dissect the C++ source AST (Abstract Syntax Tree). Embrace the task of crafting a tool that can, for instance, verify the capitalization of class names in your source and header files—a testament to the potent customizability and automated refactoring skills of Clang-Tidy.
Before embarking on this journey, a primer on compilers and a grasp of C++ fundamentals set the stage for a productive learning experience. Grasp the significance of programming language safety, its vital role in fabricating secure and reliable software systems, and understand how enhancements in language safety, particularly in memory safety, can shield our increasingly digital world from catastrophic cyber incidents. With a commitment to fostering excellence in software development and offering recommendations to pinpoint the most effective static analysis tools, Clang-Tidy stands as a beacon of security in an age where robust coding practices are not just an asset but a necessity for developers, practitioners, and researchers alike.
Polyspace, as a cutting-edge static code analysis (SCA) tool, has established its prowess beyond simple bug-tracking. It digs into the very fabric of software, performing rigorous mathematical modeling to pinpoint security vulnerabilities and potential run-time errors.
For critical software where failure is not an option—think spacecraft, lifesaving medical devices, and modern vehicles—Polyspace provides peace of mind. It works by dissecting codebases at the granular level of units such as functions or classes to ensure each segment's integrity contributes to a dependable whole.
Taking to heart lessons from the field, Polyspace emerges as a sentinel against the looming shadows of code deficiency. In a world where software complexities balloon and reliance on multitudes of obscure libraries is rampant, its capability to meticulously comb through lines of code and flag obscurities is indispensable.
It underscores the dire need for quality—a synergy of trust, dependability, and resilience in software systems. Aligning with stringent industry standards, such as ISO 26262 for automotive safety, Polyspace's analysis establishes an assurance case, becoming instrumental in compliance and certification processes. Studies recommend SCA tools like Polyspace as a criteria for selecting software for high-stakes environments, where one oversight can be catastrophic. Moreover, the tool houses the prescient ability to evolve with emerging paradigms in technology, from AI-based systems to autonomous vehicles, safeguarding against the errors of today and the unknown threats of tomorrow.
CppCheck serves the critical function of enhancing code security and vulnerability management in C and C++ codebases. Leveraging the power of Static Code Analysis (SCA), it meticulously scans source code, sans execution, employing Data Flow Analysis among other techniques.
This analysis is crucial for mapping out potential variables' values across the code, laying bare vulnerabilities like null pointer dereferences and buffer overflows, as well as errors such as uninitialized variables and memory leaks. While CppCheck adeptly pinpoints a breadth of potential issues, practitioners must navigate the challenge of false positives—a common SCA plight where non-exploitable bugs masquerade as genuine threats due to the tool's occasional inability to accurately track data integrity through the application.
Despite this, CppCheck's capacity for seamless IDE integration and its free, open-source nature solidify its status as an invaluable asset in the developer's toolkit. Moreover, adhering to the guidelines set forth in the NISTIR 8397 offers a framework for reliable and secure software construction. To extract the utmost benefit from such tools in modern, agile development environments, incorporating a security requirements questionnaire into feature development from the onset can effectively tailor the Software Development Life Cycle to mitigate pertinent risks. As emphasized by experts, threat modeling and a discerning approach to development can substantially reduce noise and focus on genuine security enhancements.
Compiler-based tools such as ASAN (AddressSanitizer) and TSAN (ThreadSanitizer) represent pivotal strides in code security, tracing their conceptual heritage to the early days of computing as described in the Universal Turing Machine paper, which influenced the "stored-program computer" model integral to the Von Neumann architecture. Recognizing the critical need for simplified memory management outlined by Von Neumann's design, ASAN provides a robust line of defense against memory corruption bugs like buffer overflows and use-after-free errors—predominant culprits in security breaches that impose substantial costs on users.
Similarly, TSAN stands guard against the peril of data races and concurrent programming pitfalls, which can be as destructive as memory errors if left unchecked. Paired with other sanitizers, including UBSAN for undefined behaviors, they furnish developers with a comprehensive arsenal for early detection and mitigation of vulnerabilities, aligning with research recommendations that underscore the priority of enhancing software reliability through improved static analysis tools.
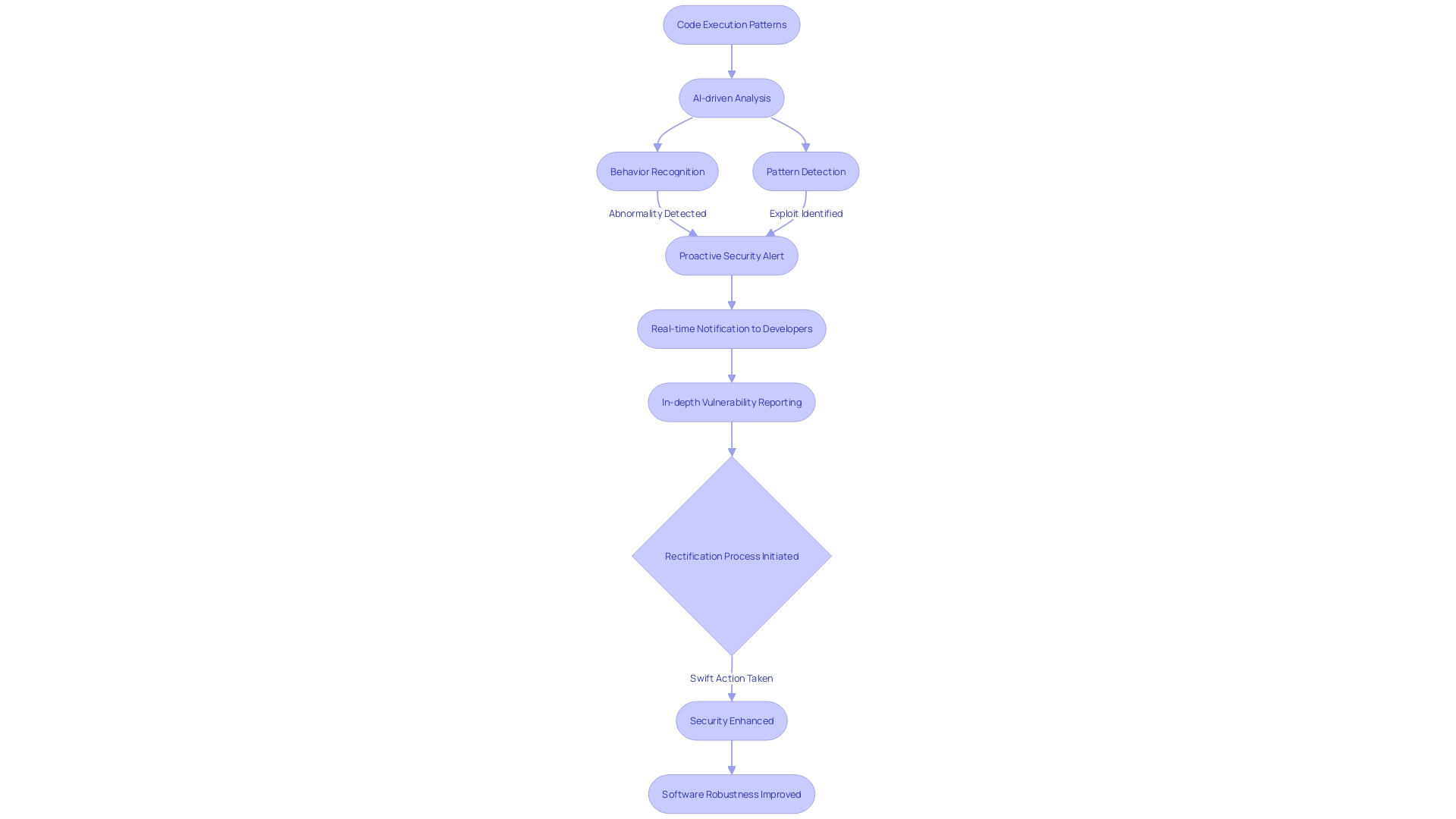
Revolutionizing the world of code security, Codium.ai stands at the forefront with its advanced dynamic analysis capabilities. This sophisticated tool employs AI-driven algorithms to scrutinize code execution patterns and behaviors as the code operates, offering a proactive stance against possible security breaches. What sets Codium.ai apart is its agility in pinpointing abnormalities and potential security exploits the moment they transpire.
For developers tasked with upholding the sanctity of their codebase, the real-time notifications and in-depth reporting features become indispensable tools. They allow swift rectification of discovered vulnerabilities, thereby bolstering both the security posture and robustness of their software solutions. Reflecting on research that underscores the necessity for adept static analysis tools, Codium.ai presents itself as more than just an option; it is a companion in the pursuit of excellence in software development and a harbinger for elevated quality and reliability in software systems.
HelloBar serves as a static code analysis tool that goes beyond just probing code quality. It is tailored to pinpoint security loopholes and ensure maintainability, thus fostering resilient codebases. This resource is essential in preemptively addressing software susceptibilities by providing a thorough suite of analysis features that not only detect but also recommend solutions to bolster code security.
With its user-centric design, HelloBar seamlessly fuses with prevalent coding environments, streamlining the process of integrating secure coding protocols into developers' daily regime. Delivered through an intuitive dashboard, it generates elaborate reports, affording developers the insight to rectify issues swiftly and decisively. Furthermore, its actionable tips are instrumental in preserving exceptional code quality, thereby mitigating potential security predicaments.
An illustrative case underscores the indispensability of such analytic rigor: upon encountering a new codebase, perhaps one derived from an options-based market protocol, a holistic assessment is imperative. Developers must discern whether they are dealing with novel or forked code and, if the latter, gauge the extent of modifications. Focusing on the principal functions invoked by users unveils a clearer outlook on security and functionality.
Supporting this, recent research advocates for a standardized recommendation framework that facilitates software developers in selecting the optimal static analysis tools. This initiative also triggers further inquiry into refining said tools, driving enhancements in software system quality and development practices. As analysis trends materialize over time, they unveil patterns - a first step that should be complemented by examining how these patterns evolve, thereby revealing which software firms are advancing and which ought to adopt a quality enhancement plan.
In conclusion, static code analysis tools are indispensable for enhancing software security and reliability. These tools, such as PVS Studio, Parasoft, Coverity, SonarQube, Clang-Tidy, Polyspace, CppCheck, ASAN/TSAN, Codium.ai, and HelloBar, offer unique features and benefits that revolutionize the development process. From precise vulnerability identification to extensive language support and actionable advice, these tools empower developers to address issues efficiently and improve the overall security posture of their software.
They enable trend tracking, clean code practices, performance analysis, and mathematical modeling for robustness. Despite occasional false positives and false negatives, these tools provide invaluable insights into vulnerabilities, coding errors, and best practices. By adopting static code analysis tools, developers can proactively enhance code quality, identify and mitigate potential security vulnerabilities, and ensure the reliability of their software.
These tools offer real-time detection, seamless integration with development workflows, and comprehensive reporting, allowing for swift remediation and improved productivity. In a rapidly evolving digital landscape, these tools play a vital role in building trust, dependability, and resilience in software systems. By leveraging the power of static code analysis, developers can deliver secure and reliable software solutions, mitigate risks, enhance user confidence, and elevate overall development practices.
Incorporating static code analysis into the software development lifecycle is essential for creating high-quality software. With their unique capabilities, these tools enable developers to stay proactive, improve code security, and achieve excellence in software development. By embracing these tools, developers can unlock the full potential of their code and deliver exceptional software that meets the highest standards of security and reliability.
Upgrade your code quality and security today with Kodezi!
Why Use Static Code Analysis Tools
The deployment of Static Code Analysis (SCA) tools is a significant advance in the development of secure software, diving deep into the codebase without execution to unearth issues that might compromise system quality, including buffer overflows, memory leaks, and code injections. Such analysis is integral to fostering a culture of quality keeping your software reliable and trustworthy.
Christophe Limpalair, who founded Cybr after recognizing the challenges organizations face in software security, emphasizes this integration of SCA in his teachings about Infrastructure as Code (IAC) scanning and adopting Policy as Code principles. The process of adopting SCA tools is not without its considerations.
There's an imperative to comprehend the broader context of system quality, evaluating metrics such as resilience and trustworthiness. This understanding positions the analysis tools to function optimally within your existing environment, addressing the 'what' and 'why' of SCA at every phase of the software lifecycle.
For example, the software's security and privacy requirements must be clear from the onset, involving threat models and data flow diagrams to align with regulatory standards and anticipate evolving threats. Looking beyond mere bug detection, SCA should be seen as part of a broader trend analysis, scrutinizing patterns over time and generalizing remedies for the industry. This aligns with insights from studies suggesting that a strategic selection of SCA tools is vital for enhancing software reliability and the development process. By examining these patterns, we gain insight into the progress of software quality initiatives corporate-wide, and can discern whether a quality improvement program might be necessary, thus elevating software security from dire to robust.
Harnessing the potential of PVS Studio's static code analysis can transform your C/C++/C# projects, elevating security to remarkable new heights. This tool excels in uncovering a multitude of problematic code patterns — ranging from the perilous null pointer dereferences to the subtle, yet critical, uninitialized variables.
Add to this its prowess in mitigating incorrect arithmetic expressions and curtailing buffer overflows, and you have a formidable ally in the quest for code security. Detailed reports generated by PVS Studio facilitate a swift response to complications, allowing developers to pinpoint vulnerabilities with precision.
The tool's intuitive interface further simplifies navigation through the complex landscape of code security, ensuring a smooth remediation process. Reflecting on real-world applications, such as the examination of the iconic Quake World's codebase, we learn the significance of learning from code — both our own and that of others.
In spite of challenges, analyzing such a project can unearth practical insights that are beneficial to the wider programming community. As recent discussions in the tech space underscore the crucial role of programming language safety — accentuated by the pressing need for secure cyberinfrastructure — tools like PVS Studio become central to the discourse. They echo the sentiment in the industry, aligning with guidance from authoritative resources like NISTIR 8397 on software security, underscoring the importance of reliable coding standards across various programming languages. Moreover, the growing conversations about memory-safe languages and their impact on software safety prompt a reflection on the essential practices for developing code that is not only secure but also safe, further highlighting the essential role that tools like PVS Studio play in modern software development.
Parasoft stands out as a distinguished static code analysis tool that accommodates a variety of programming languages including C/C++, Java, and .NET. What sets Parasoft apart is not just its broad language support, but its extensive suite of security rules and robust guidelines designed to uphold both code quality and security integrity. Leveraging sophisticated analysis mechanisms, this tool has a proven capability to pinpoint an array of issues such as vulnerabilities, memory leaks, and deviations from coding standards.
Under the guidance of experts like Prashant KV, with over 15 years in information security, Parasoft equips developers with precise, actionable advice. Balancing in-depth experience with application security and a developer's perspective, the insights provided help developers tackle issues efficiently and bolster the security posture of their codebases. This dedication to enhancing cybersecurity skills at all levels mirrors the spirit of Prashant's conferences, where training days cater to various expertise levels – from novice programmers to enterprise security professionals – all with a focus on hands-on, transformative education.
Utilizing the state-of-the-art static analysis tool Coverity, developers can significantly improve the security and reliability of complex software projects. Coverity excels in probing the intricate components of software written in diverse languages including C/C++, Java, and C#.
It meticulously scrutinizes the code to unearth a plethora of defects such as memory corruption, resource leaks, and race conditions, as well as multiple security vulnerabilities. The power of Coverity lies not only in its capacity to identify defects but also in its ability to track trends over time.
By analyzing the ebb and flow of software quality, companies can ascertain whether their software developments are evolving towards greater excellence or if there's an urgent need for a remedial quality program. Additionally, the importance of embedding software security early in the development process—often termed as ‘shift left’—cannot be overstated. In domains where embedded software commands vital systems, such as automotive and aerospace industries, an overlooked flaw can result in grave outcomes, including system failures or unauthorized access. Coverity serves as a vigilant guard, providing comprehensive reports and integrating seamlessly with mainstream development tools, ensuring that such systems are built on a foundation of security and safety from the outset.
SonarQube excels as a versatile static code analysis tool that not only supports a myriad of programming languages but also stands as the embodiment of what it means to instill clean code practices. It thrusts forward an extensive set of rules focused on unearthing security vulnerabilities, code smells, and the bane of developers - technical debt.
It pushes the agenda of 'Clean Code', insisting that code should not only function flawlessly but also be crafted in such a way that it stands as a clear, maintainable beacon for any future voyagers in the codebase. Emphasizing quality code that shines with readability and simplicity, SonarQube becomes the vigilant overseer that provides developers with immediate insights on code health.
Complex constructs are avoided and a clear convention throughout the codebase is promoted. By embedding itself within CI/CD pipelines, SonarQube ensures that the code's clarity and security are not afterthoughts but integral parts of the continuous integration process. It serves as the lighthouse guiding ships safely into the harbor, ensuring that each iteration maintains the gold standard for code excellence. Integration with development workflows turns SonarQube not just into a tool, but a vital companion for any team striving to elevate their code to its highest potential.
Dive into the realm of code security with Clang-Tidy, a powerhouse static analysis tool essential for C and C++ developers. As part of the Clang compiler suite, the tool offers an arsenal of checks designed to unveil and resolve potential security vulnerabilities. But that's just the beginning.
With a core focus on enhancing code quality, Clang-Tidy also identifies performance bottlenecks and coding style discrepancies. Follow a structured pathway to mastering this tool, starting with acquiring the open-source Clang project and progressing to constructing your static analysis tool using Clang's front-end libraries to dissect the C++ source AST (Abstract Syntax Tree). Embrace the task of crafting a tool that can, for instance, verify the capitalization of class names in your source and header files—a testament to the potent customizability and automated refactoring skills of Clang-Tidy.
Before embarking on this journey, a primer on compilers and a grasp of C++ fundamentals set the stage for a productive learning experience. Grasp the significance of programming language safety, its vital role in fabricating secure and reliable software systems, and understand how enhancements in language safety, particularly in memory safety, can shield our increasingly digital world from catastrophic cyber incidents. With a commitment to fostering excellence in software development and offering recommendations to pinpoint the most effective static analysis tools, Clang-Tidy stands as a beacon of security in an age where robust coding practices are not just an asset but a necessity for developers, practitioners, and researchers alike.
Polyspace, as a cutting-edge static code analysis (SCA) tool, has established its prowess beyond simple bug-tracking. It digs into the very fabric of software, performing rigorous mathematical modeling to pinpoint security vulnerabilities and potential run-time errors.
For critical software where failure is not an option—think spacecraft, lifesaving medical devices, and modern vehicles—Polyspace provides peace of mind. It works by dissecting codebases at the granular level of units such as functions or classes to ensure each segment's integrity contributes to a dependable whole.
Taking to heart lessons from the field, Polyspace emerges as a sentinel against the looming shadows of code deficiency. In a world where software complexities balloon and reliance on multitudes of obscure libraries is rampant, its capability to meticulously comb through lines of code and flag obscurities is indispensable.
It underscores the dire need for quality—a synergy of trust, dependability, and resilience in software systems. Aligning with stringent industry standards, such as ISO 26262 for automotive safety, Polyspace's analysis establishes an assurance case, becoming instrumental in compliance and certification processes. Studies recommend SCA tools like Polyspace as a criteria for selecting software for high-stakes environments, where one oversight can be catastrophic. Moreover, the tool houses the prescient ability to evolve with emerging paradigms in technology, from AI-based systems to autonomous vehicles, safeguarding against the errors of today and the unknown threats of tomorrow.
CppCheck serves the critical function of enhancing code security and vulnerability management in C and C++ codebases. Leveraging the power of Static Code Analysis (SCA), it meticulously scans source code, sans execution, employing Data Flow Analysis among other techniques.
This analysis is crucial for mapping out potential variables' values across the code, laying bare vulnerabilities like null pointer dereferences and buffer overflows, as well as errors such as uninitialized variables and memory leaks. While CppCheck adeptly pinpoints a breadth of potential issues, practitioners must navigate the challenge of false positives—a common SCA plight where non-exploitable bugs masquerade as genuine threats due to the tool's occasional inability to accurately track data integrity through the application.
Despite this, CppCheck's capacity for seamless IDE integration and its free, open-source nature solidify its status as an invaluable asset in the developer's toolkit. Moreover, adhering to the guidelines set forth in the NISTIR 8397 offers a framework for reliable and secure software construction. To extract the utmost benefit from such tools in modern, agile development environments, incorporating a security requirements questionnaire into feature development from the onset can effectively tailor the Software Development Life Cycle to mitigate pertinent risks. As emphasized by experts, threat modeling and a discerning approach to development can substantially reduce noise and focus on genuine security enhancements.
Compiler-based tools such as ASAN (AddressSanitizer) and TSAN (ThreadSanitizer) represent pivotal strides in code security, tracing their conceptual heritage to the early days of computing as described in the Universal Turing Machine paper, which influenced the "stored-program computer" model integral to the Von Neumann architecture. Recognizing the critical need for simplified memory management outlined by Von Neumann's design, ASAN provides a robust line of defense against memory corruption bugs like buffer overflows and use-after-free errors—predominant culprits in security breaches that impose substantial costs on users.
Similarly, TSAN stands guard against the peril of data races and concurrent programming pitfalls, which can be as destructive as memory errors if left unchecked. Paired with other sanitizers, including UBSAN for undefined behaviors, they furnish developers with a comprehensive arsenal for early detection and mitigation of vulnerabilities, aligning with research recommendations that underscore the priority of enhancing software reliability through improved static analysis tools.
Revolutionizing the world of code security, Codium.ai stands at the forefront with its advanced dynamic analysis capabilities. This sophisticated tool employs AI-driven algorithms to scrutinize code execution patterns and behaviors as the code operates, offering a proactive stance against possible security breaches. What sets Codium.ai apart is its agility in pinpointing abnormalities and potential security exploits the moment they transpire.
For developers tasked with upholding the sanctity of their codebase, the real-time notifications and in-depth reporting features become indispensable tools. They allow swift rectification of discovered vulnerabilities, thereby bolstering both the security posture and robustness of their software solutions. Reflecting on research that underscores the necessity for adept static analysis tools, Codium.ai presents itself as more than just an option; it is a companion in the pursuit of excellence in software development and a harbinger for elevated quality and reliability in software systems.

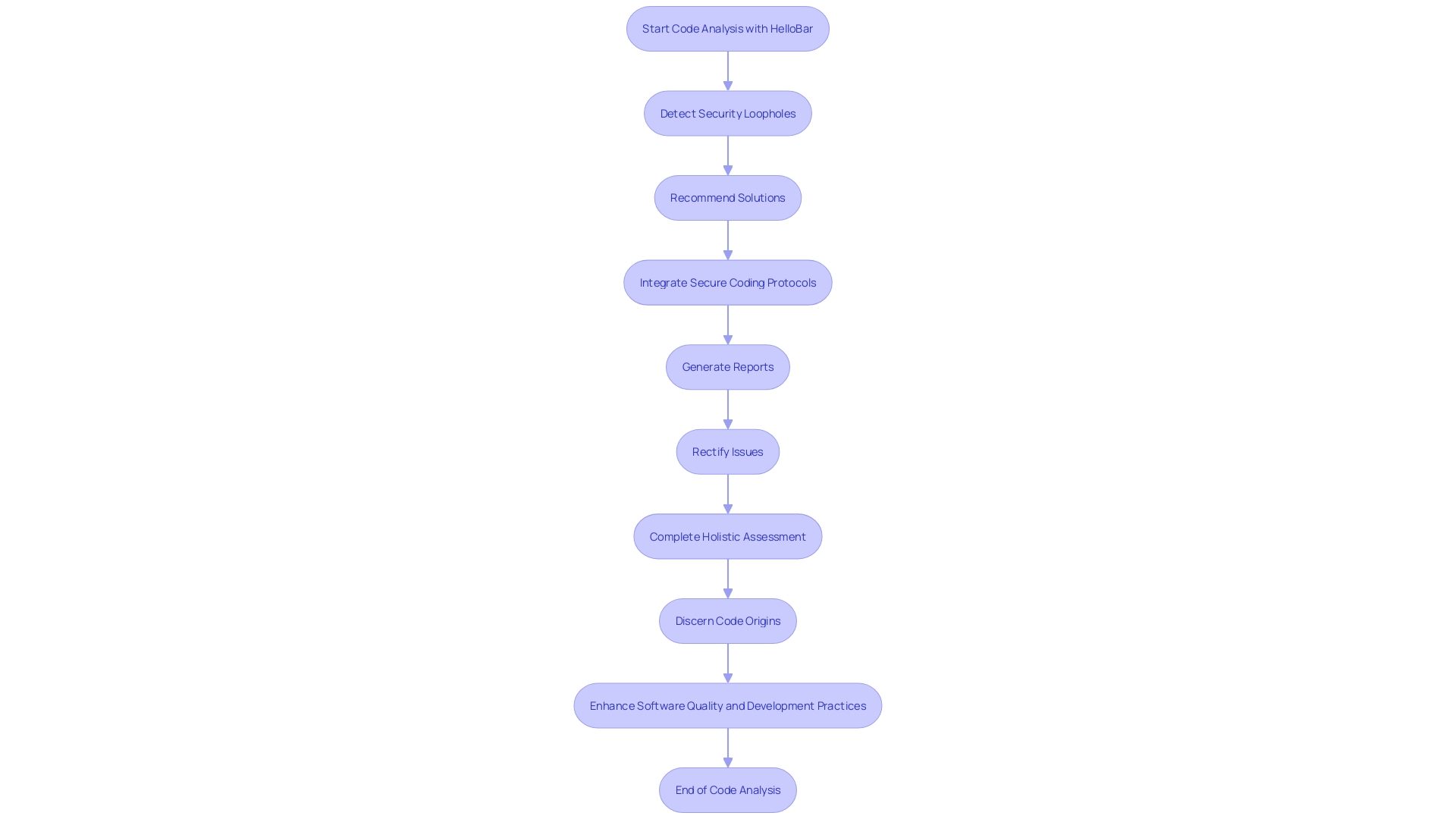
HelloBar serves as a static code analysis tool that goes beyond just probing code quality. It is tailored to pinpoint security loopholes and ensure maintainability, thus fostering resilient codebases. This resource is essential in preemptively addressing software susceptibilities by providing a thorough suite of analysis features that not only detect but also recommend solutions to bolster code security.
With its user-centric design, HelloBar seamlessly fuses with prevalent coding environments, streamlining the process of integrating secure coding protocols into developers' daily regime. Delivered through an intuitive dashboard, it generates elaborate reports, affording developers the insight to rectify issues swiftly and decisively. Furthermore, its actionable tips are instrumental in preserving exceptional code quality, thereby mitigating potential security predicaments.
An illustrative case underscores the indispensability of such analytic rigor: upon encountering a new codebase, perhaps one derived from an options-based market protocol, a holistic assessment is imperative. Developers must discern whether they are dealing with novel or forked code and, if the latter, gauge the extent of modifications. Focusing on the principal functions invoked by users unveils a clearer outlook on security and functionality.
Supporting this, recent research advocates for a standardized recommendation framework that facilitates software developers in selecting the optimal static analysis tools. This initiative also triggers further inquiry into refining said tools, driving enhancements in software system quality and development practices. As analysis trends materialize over time, they unveil patterns - a first step that should be complemented by examining how these patterns evolve, thereby revealing which software firms are advancing and which ought to adopt a quality enhancement plan.

In conclusion, static code analysis tools are indispensable for enhancing software security and reliability. These tools, such as PVS Studio, Parasoft, Coverity, SonarQube, Clang-Tidy, Polyspace, CppCheck, ASAN/TSAN, Codium.ai, and HelloBar, offer unique features and benefits that revolutionize the development process. From precise vulnerability identification to extensive language support and actionable advice, these tools empower developers to address issues efficiently and improve the overall security posture of their software.
They enable trend tracking, clean code practices, performance analysis, and mathematical modeling for robustness. Despite occasional false positives and false negatives, these tools provide invaluable insights into vulnerabilities, coding errors, and best practices. By adopting static code analysis tools, developers can proactively enhance code quality, identify and mitigate potential security vulnerabilities, and ensure the reliability of their software.
These tools offer real-time detection, seamless integration with development workflows, and comprehensive reporting, allowing for swift remediation and improved productivity. In a rapidly evolving digital landscape, these tools play a vital role in building trust, dependability, and resilience in software systems. By leveraging the power of static code analysis, developers can deliver secure and reliable software solutions, mitigate risks, enhance user confidence, and elevate overall development practices.
Incorporating static code analysis into the software development lifecycle is essential for creating high-quality software. With their unique capabilities, these tools enable developers to stay proactive, improve code security, and achieve excellence in software development. By embracing these tools, developers can unlock the full potential of their code and deliver exceptional software that meets the highest standards of security and reliability.
Upgrade your code quality and security today with Kodezi!
PVS Studio
Harnessing the potential of PVS Studio's static code analysis can transform your C/C++/C# projects, elevating security to remarkable new heights. This tool excels in uncovering a multitude of problematic code patterns — ranging from the perilous null pointer dereferences to the subtle, yet critical, uninitialized variables.
Add to this its prowess in mitigating incorrect arithmetic expressions and curtailing buffer overflows, and you have a formidable ally in the quest for code security. Detailed reports generated by PVS Studio facilitate a swift response to complications, allowing developers to pinpoint vulnerabilities with precision.
The tool's intuitive interface further simplifies navigation through the complex landscape of code security, ensuring a smooth remediation process. Reflecting on real-world applications, such as the examination of the iconic Quake World's codebase, we learn the significance of learning from code — both our own and that of others.
In spite of challenges, analyzing such a project can unearth practical insights that are beneficial to the wider programming community. As recent discussions in the tech space underscore the crucial role of programming language safety — accentuated by the pressing need for secure cyberinfrastructure — tools like PVS Studio become central to the discourse. They echo the sentiment in the industry, aligning with guidance from authoritative resources like NISTIR 8397 on software security, underscoring the importance of reliable coding standards across various programming languages. Moreover, the growing conversations about memory-safe languages and their impact on software safety prompt a reflection on the essential practices for developing code that is not only secure but also safe, further highlighting the essential role that tools like PVS Studio play in modern software development.
Parasoft stands out as a distinguished static code analysis tool that accommodates a variety of programming languages including C/C++, Java, and .NET. What sets Parasoft apart is not just its broad language support, but its extensive suite of security rules and robust guidelines designed to uphold both code quality and security integrity. Leveraging sophisticated analysis mechanisms, this tool has a proven capability to pinpoint an array of issues such as vulnerabilities, memory leaks, and deviations from coding standards.
Under the guidance of experts like Prashant KV, with over 15 years in information security, Parasoft equips developers with precise, actionable advice. Balancing in-depth experience with application security and a developer's perspective, the insights provided help developers tackle issues efficiently and bolster the security posture of their codebases. This dedication to enhancing cybersecurity skills at all levels mirrors the spirit of Prashant's conferences, where training days cater to various expertise levels – from novice programmers to enterprise security professionals – all with a focus on hands-on, transformative education.
Utilizing the state-of-the-art static analysis tool Coverity, developers can significantly improve the security and reliability of complex software projects. Coverity excels in probing the intricate components of software written in diverse languages including C/C++, Java, and C#.
It meticulously scrutinizes the code to unearth a plethora of defects such as memory corruption, resource leaks, and race conditions, as well as multiple security vulnerabilities. The power of Coverity lies not only in its capacity to identify defects but also in its ability to track trends over time.
By analyzing the ebb and flow of software quality, companies can ascertain whether their software developments are evolving towards greater excellence or if there's an urgent need for a remedial quality program. Additionally, the importance of embedding software security early in the development process—often termed as ‘shift left’—cannot be overstated. In domains where embedded software commands vital systems, such as automotive and aerospace industries, an overlooked flaw can result in grave outcomes, including system failures or unauthorized access. Coverity serves as a vigilant guard, providing comprehensive reports and integrating seamlessly with mainstream development tools, ensuring that such systems are built on a foundation of security and safety from the outset.
SonarQube excels as a versatile static code analysis tool that not only supports a myriad of programming languages but also stands as the embodiment of what it means to instill clean code practices. It thrusts forward an extensive set of rules focused on unearthing security vulnerabilities, code smells, and the bane of developers - technical debt.
It pushes the agenda of 'Clean Code', insisting that code should not only function flawlessly but also be crafted in such a way that it stands as a clear, maintainable beacon for any future voyagers in the codebase. Emphasizing quality code that shines with readability and simplicity, SonarQube becomes the vigilant overseer that provides developers with immediate insights on code health.
Complex constructs are avoided and a clear convention throughout the codebase is promoted. By embedding itself within CI/CD pipelines, SonarQube ensures that the code's clarity and security are not afterthoughts but integral parts of the continuous integration process. It serves as the lighthouse guiding ships safely into the harbor, ensuring that each iteration maintains the gold standard for code excellence. Integration with development workflows turns SonarQube not just into a tool, but a vital companion for any team striving to elevate their code to its highest potential.
Dive into the realm of code security with Clang-Tidy, a powerhouse static analysis tool essential for C and C++ developers. As part of the Clang compiler suite, the tool offers an arsenal of checks designed to unveil and resolve potential security vulnerabilities. But that's just the beginning.
With a core focus on enhancing code quality, Clang-Tidy also identifies performance bottlenecks and coding style discrepancies. Follow a structured pathway to mastering this tool, starting with acquiring the open-source Clang project and progressing to constructing your static analysis tool using Clang's front-end libraries to dissect the C++ source AST (Abstract Syntax Tree). Embrace the task of crafting a tool that can, for instance, verify the capitalization of class names in your source and header files—a testament to the potent customizability and automated refactoring skills of Clang-Tidy.
Before embarking on this journey, a primer on compilers and a grasp of C++ fundamentals set the stage for a productive learning experience. Grasp the significance of programming language safety, its vital role in fabricating secure and reliable software systems, and understand how enhancements in language safety, particularly in memory safety, can shield our increasingly digital world from catastrophic cyber incidents. With a commitment to fostering excellence in software development and offering recommendations to pinpoint the most effective static analysis tools, Clang-Tidy stands as a beacon of security in an age where robust coding practices are not just an asset but a necessity for developers, practitioners, and researchers alike.
Polyspace, as a cutting-edge static code analysis (SCA) tool, has established its prowess beyond simple bug-tracking. It digs into the very fabric of software, performing rigorous mathematical modeling to pinpoint security vulnerabilities and potential run-time errors.
For critical software where failure is not an option—think spacecraft, lifesaving medical devices, and modern vehicles—Polyspace provides peace of mind. It works by dissecting codebases at the granular level of units such as functions or classes to ensure each segment's integrity contributes to a dependable whole.
Taking to heart lessons from the field, Polyspace emerges as a sentinel against the looming shadows of code deficiency. In a world where software complexities balloon and reliance on multitudes of obscure libraries is rampant, its capability to meticulously comb through lines of code and flag obscurities is indispensable.
It underscores the dire need for quality—a synergy of trust, dependability, and resilience in software systems. Aligning with stringent industry standards, such as ISO 26262 for automotive safety, Polyspace's analysis establishes an assurance case, becoming instrumental in compliance and certification processes. Studies recommend SCA tools like Polyspace as a criteria for selecting software for high-stakes environments, where one oversight can be catastrophic. Moreover, the tool houses the prescient ability to evolve with emerging paradigms in technology, from AI-based systems to autonomous vehicles, safeguarding against the errors of today and the unknown threats of tomorrow.
CppCheck serves the critical function of enhancing code security and vulnerability management in C and C++ codebases. Leveraging the power of Static Code Analysis (SCA), it meticulously scans source code, sans execution, employing Data Flow Analysis among other techniques.
This analysis is crucial for mapping out potential variables' values across the code, laying bare vulnerabilities like null pointer dereferences and buffer overflows, as well as errors such as uninitialized variables and memory leaks. While CppCheck adeptly pinpoints a breadth of potential issues, practitioners must navigate the challenge of false positives—a common SCA plight where non-exploitable bugs masquerade as genuine threats due to the tool's occasional inability to accurately track data integrity through the application.
Despite this, CppCheck's capacity for seamless IDE integration and its free, open-source nature solidify its status as an invaluable asset in the developer's toolkit. Moreover, adhering to the guidelines set forth in the NISTIR 8397 offers a framework for reliable and secure software construction. To extract the utmost benefit from such tools in modern, agile development environments, incorporating a security requirements questionnaire into feature development from the onset can effectively tailor the Software Development Life Cycle to mitigate pertinent risks. As emphasized by experts, threat modeling and a discerning approach to development can substantially reduce noise and focus on genuine security enhancements.
Compiler-based tools such as ASAN (AddressSanitizer) and TSAN (ThreadSanitizer) represent pivotal strides in code security, tracing their conceptual heritage to the early days of computing as described in the Universal Turing Machine paper, which influenced the "stored-program computer" model integral to the Von Neumann architecture. Recognizing the critical need for simplified memory management outlined by Von Neumann's design, ASAN provides a robust line of defense against memory corruption bugs like buffer overflows and use-after-free errors—predominant culprits in security breaches that impose substantial costs on users.
Similarly, TSAN stands guard against the peril of data races and concurrent programming pitfalls, which can be as destructive as memory errors if left unchecked. Paired with other sanitizers, including UBSAN for undefined behaviors, they furnish developers with a comprehensive arsenal for early detection and mitigation of vulnerabilities, aligning with research recommendations that underscore the priority of enhancing software reliability through improved static analysis tools.
Revolutionizing the world of code security, Codium.ai stands at the forefront with its advanced dynamic analysis capabilities. This sophisticated tool employs AI-driven algorithms to scrutinize code execution patterns and behaviors as the code operates, offering a proactive stance against possible security breaches. What sets Codium.ai apart is its agility in pinpointing abnormalities and potential security exploits the moment they transpire.
For developers tasked with upholding the sanctity of their codebase, the real-time notifications and in-depth reporting features become indispensable tools. They allow swift rectification of discovered vulnerabilities, thereby bolstering both the security posture and robustness of their software solutions. Reflecting on research that underscores the necessity for adept static analysis tools, Codium.ai presents itself as more than just an option; it is a companion in the pursuit of excellence in software development and a harbinger for elevated quality and reliability in software systems.

HelloBar serves as a static code analysis tool that goes beyond just probing code quality. It is tailored to pinpoint security loopholes and ensure maintainability, thus fostering resilient codebases. This resource is essential in preemptively addressing software susceptibilities by providing a thorough suite of analysis features that not only detect but also recommend solutions to bolster code security.
With its user-centric design, HelloBar seamlessly fuses with prevalent coding environments, streamlining the process of integrating secure coding protocols into developers' daily regime. Delivered through an intuitive dashboard, it generates elaborate reports, affording developers the insight to rectify issues swiftly and decisively. Furthermore, its actionable tips are instrumental in preserving exceptional code quality, thereby mitigating potential security predicaments.
An illustrative case underscores the indispensability of such analytic rigor: upon encountering a new codebase, perhaps one derived from an options-based market protocol, a holistic assessment is imperative. Developers must discern whether they are dealing with novel or forked code and, if the latter, gauge the extent of modifications. Focusing on the principal functions invoked by users unveils a clearer outlook on security and functionality.
Supporting this, recent research advocates for a standardized recommendation framework that facilitates software developers in selecting the optimal static analysis tools. This initiative also triggers further inquiry into refining said tools, driving enhancements in software system quality and development practices. As analysis trends materialize over time, they unveil patterns - a first step that should be complemented by examining how these patterns evolve, thereby revealing which software firms are advancing and which ought to adopt a quality enhancement plan.

In conclusion, static code analysis tools are indispensable for enhancing software security and reliability. These tools, such as PVS Studio, Parasoft, Coverity, SonarQube, Clang-Tidy, Polyspace, CppCheck, ASAN/TSAN, Codium.ai, and HelloBar, offer unique features and benefits that revolutionize the development process. From precise vulnerability identification to extensive language support and actionable advice, these tools empower developers to address issues efficiently and improve the overall security posture of their software.
They enable trend tracking, clean code practices, performance analysis, and mathematical modeling for robustness. Despite occasional false positives and false negatives, these tools provide invaluable insights into vulnerabilities, coding errors, and best practices. By adopting static code analysis tools, developers can proactively enhance code quality, identify and mitigate potential security vulnerabilities, and ensure the reliability of their software.
These tools offer real-time detection, seamless integration with development workflows, and comprehensive reporting, allowing for swift remediation and improved productivity. In a rapidly evolving digital landscape, these tools play a vital role in building trust, dependability, and resilience in software systems. By leveraging the power of static code analysis, developers can deliver secure and reliable software solutions, mitigate risks, enhance user confidence, and elevate overall development practices.
Incorporating static code analysis into the software development lifecycle is essential for creating high-quality software. With their unique capabilities, these tools enable developers to stay proactive, improve code security, and achieve excellence in software development. By embracing these tools, developers can unlock the full potential of their code and deliver exceptional software that meets the highest standards of security and reliability.
Upgrade your code quality and security today with Kodezi!
Parasoft
Parasoft stands out as a distinguished static code analysis tool that accommodates a variety of programming languages including C/C++, Java, and .NET. What sets Parasoft apart is not just its broad language support, but its extensive suite of security rules and robust guidelines designed to uphold both code quality and security integrity. Leveraging sophisticated analysis mechanisms, this tool has a proven capability to pinpoint an array of issues such as vulnerabilities, memory leaks, and deviations from coding standards.
Under the guidance of experts like Prashant KV, with over 15 years in information security, Parasoft equips developers with precise, actionable advice. Balancing in-depth experience with application security and a developer's perspective, the insights provided help developers tackle issues efficiently and bolster the security posture of their codebases. This dedication to enhancing cybersecurity skills at all levels mirrors the spirit of Prashant's conferences, where training days cater to various expertise levels – from novice programmers to enterprise security professionals – all with a focus on hands-on, transformative education.
Utilizing the state-of-the-art static analysis tool Coverity, developers can significantly improve the security and reliability of complex software projects. Coverity excels in probing the intricate components of software written in diverse languages including C/C++, Java, and C#.
It meticulously scrutinizes the code to unearth a plethora of defects such as memory corruption, resource leaks, and race conditions, as well as multiple security vulnerabilities. The power of Coverity lies not only in its capacity to identify defects but also in its ability to track trends over time.
By analyzing the ebb and flow of software quality, companies can ascertain whether their software developments are evolving towards greater excellence or if there's an urgent need for a remedial quality program. Additionally, the importance of embedding software security early in the development process—often termed as ‘shift left’—cannot be overstated. In domains where embedded software commands vital systems, such as automotive and aerospace industries, an overlooked flaw can result in grave outcomes, including system failures or unauthorized access. Coverity serves as a vigilant guard, providing comprehensive reports and integrating seamlessly with mainstream development tools, ensuring that such systems are built on a foundation of security and safety from the outset.
SonarQube excels as a versatile static code analysis tool that not only supports a myriad of programming languages but also stands as the embodiment of what it means to instill clean code practices. It thrusts forward an extensive set of rules focused on unearthing security vulnerabilities, code smells, and the bane of developers - technical debt.
It pushes the agenda of 'Clean Code', insisting that code should not only function flawlessly but also be crafted in such a way that it stands as a clear, maintainable beacon for any future voyagers in the codebase. Emphasizing quality code that shines with readability and simplicity, SonarQube becomes the vigilant overseer that provides developers with immediate insights on code health.
Complex constructs are avoided and a clear convention throughout the codebase is promoted. By embedding itself within CI/CD pipelines, SonarQube ensures that the code's clarity and security are not afterthoughts but integral parts of the continuous integration process. It serves as the lighthouse guiding ships safely into the harbor, ensuring that each iteration maintains the gold standard for code excellence. Integration with development workflows turns SonarQube not just into a tool, but a vital companion for any team striving to elevate their code to its highest potential.
Dive into the realm of code security with Clang-Tidy, a powerhouse static analysis tool essential for C and C++ developers. As part of the Clang compiler suite, the tool offers an arsenal of checks designed to unveil and resolve potential security vulnerabilities. But that's just the beginning.
With a core focus on enhancing code quality, Clang-Tidy also identifies performance bottlenecks and coding style discrepancies. Follow a structured pathway to mastering this tool, starting with acquiring the open-source Clang project and progressing to constructing your static analysis tool using Clang's front-end libraries to dissect the C++ source AST (Abstract Syntax Tree). Embrace the task of crafting a tool that can, for instance, verify the capitalization of class names in your source and header files—a testament to the potent customizability and automated refactoring skills of Clang-Tidy.
Before embarking on this journey, a primer on compilers and a grasp of C++ fundamentals set the stage for a productive learning experience. Grasp the significance of programming language safety, its vital role in fabricating secure and reliable software systems, and understand how enhancements in language safety, particularly in memory safety, can shield our increasingly digital world from catastrophic cyber incidents. With a commitment to fostering excellence in software development and offering recommendations to pinpoint the most effective static analysis tools, Clang-Tidy stands as a beacon of security in an age where robust coding practices are not just an asset but a necessity for developers, practitioners, and researchers alike.
Polyspace, as a cutting-edge static code analysis (SCA) tool, has established its prowess beyond simple bug-tracking. It digs into the very fabric of software, performing rigorous mathematical modeling to pinpoint security vulnerabilities and potential run-time errors.
For critical software where failure is not an option—think spacecraft, lifesaving medical devices, and modern vehicles—Polyspace provides peace of mind. It works by dissecting codebases at the granular level of units such as functions or classes to ensure each segment's integrity contributes to a dependable whole.
Taking to heart lessons from the field, Polyspace emerges as a sentinel against the looming shadows of code deficiency. In a world where software complexities balloon and reliance on multitudes of obscure libraries is rampant, its capability to meticulously comb through lines of code and flag obscurities is indispensable.
It underscores the dire need for quality—a synergy of trust, dependability, and resilience in software systems. Aligning with stringent industry standards, such as ISO 26262 for automotive safety, Polyspace's analysis establishes an assurance case, becoming instrumental in compliance and certification processes. Studies recommend SCA tools like Polyspace as a criteria for selecting software for high-stakes environments, where one oversight can be catastrophic. Moreover, the tool houses the prescient ability to evolve with emerging paradigms in technology, from AI-based systems to autonomous vehicles, safeguarding against the errors of today and the unknown threats of tomorrow.
CppCheck serves the critical function of enhancing code security and vulnerability management in C and C++ codebases. Leveraging the power of Static Code Analysis (SCA), it meticulously scans source code, sans execution, employing Data Flow Analysis among other techniques.
This analysis is crucial for mapping out potential variables' values across the code, laying bare vulnerabilities like null pointer dereferences and buffer overflows, as well as errors such as uninitialized variables and memory leaks. While CppCheck adeptly pinpoints a breadth of potential issues, practitioners must navigate the challenge of false positives—a common SCA plight where non-exploitable bugs masquerade as genuine threats due to the tool's occasional inability to accurately track data integrity through the application.
Despite this, CppCheck's capacity for seamless IDE integration and its free, open-source nature solidify its status as an invaluable asset in the developer's toolkit. Moreover, adhering to the guidelines set forth in the NISTIR 8397 offers a framework for reliable and secure software construction. To extract the utmost benefit from such tools in modern, agile development environments, incorporating a security requirements questionnaire into feature development from the onset can effectively tailor the Software Development Life Cycle to mitigate pertinent risks. As emphasized by experts, threat modeling and a discerning approach to development can substantially reduce noise and focus on genuine security enhancements.
Compiler-based tools such as ASAN (AddressSanitizer) and TSAN (ThreadSanitizer) represent pivotal strides in code security, tracing their conceptual heritage to the early days of computing as described in the Universal Turing Machine paper, which influenced the "stored-program computer" model integral to the Von Neumann architecture. Recognizing the critical need for simplified memory management outlined by Von Neumann's design, ASAN provides a robust line of defense against memory corruption bugs like buffer overflows and use-after-free errors—predominant culprits in security breaches that impose substantial costs on users.
Similarly, TSAN stands guard against the peril of data races and concurrent programming pitfalls, which can be as destructive as memory errors if left unchecked. Paired with other sanitizers, including UBSAN for undefined behaviors, they furnish developers with a comprehensive arsenal for early detection and mitigation of vulnerabilities, aligning with research recommendations that underscore the priority of enhancing software reliability through improved static analysis tools.
Revolutionizing the world of code security, Codium.ai stands at the forefront with its advanced dynamic analysis capabilities. This sophisticated tool employs AI-driven algorithms to scrutinize code execution patterns and behaviors as the code operates, offering a proactive stance against possible security breaches. What sets Codium.ai apart is its agility in pinpointing abnormalities and potential security exploits the moment they transpire.
For developers tasked with upholding the sanctity of their codebase, the real-time notifications and in-depth reporting features become indispensable tools. They allow swift rectification of discovered vulnerabilities, thereby bolstering both the security posture and robustness of their software solutions. Reflecting on research that underscores the necessity for adept static analysis tools, Codium.ai presents itself as more than just an option; it is a companion in the pursuit of excellence in software development and a harbinger for elevated quality and reliability in software systems.

HelloBar serves as a static code analysis tool that goes beyond just probing code quality. It is tailored to pinpoint security loopholes and ensure maintainability, thus fostering resilient codebases. This resource is essential in preemptively addressing software susceptibilities by providing a thorough suite of analysis features that not only detect but also recommend solutions to bolster code security.
With its user-centric design, HelloBar seamlessly fuses with prevalent coding environments, streamlining the process of integrating secure coding protocols into developers' daily regime. Delivered through an intuitive dashboard, it generates elaborate reports, affording developers the insight to rectify issues swiftly and decisively. Furthermore, its actionable tips are instrumental in preserving exceptional code quality, thereby mitigating potential security predicaments.
An illustrative case underscores the indispensability of such analytic rigor: upon encountering a new codebase, perhaps one derived from an options-based market protocol, a holistic assessment is imperative. Developers must discern whether they are dealing with novel or forked code and, if the latter, gauge the extent of modifications. Focusing on the principal functions invoked by users unveils a clearer outlook on security and functionality.
Supporting this, recent research advocates for a standardized recommendation framework that facilitates software developers in selecting the optimal static analysis tools. This initiative also triggers further inquiry into refining said tools, driving enhancements in software system quality and development practices. As analysis trends materialize over time, they unveil patterns - a first step that should be complemented by examining how these patterns evolve, thereby revealing which software firms are advancing and which ought to adopt a quality enhancement plan.

In conclusion, static code analysis tools are indispensable for enhancing software security and reliability. These tools, such as PVS Studio, Parasoft, Coverity, SonarQube, Clang-Tidy, Polyspace, CppCheck, ASAN/TSAN, Codium.ai, and HelloBar, offer unique features and benefits that revolutionize the development process. From precise vulnerability identification to extensive language support and actionable advice, these tools empower developers to address issues efficiently and improve the overall security posture of their software.
They enable trend tracking, clean code practices, performance analysis, and mathematical modeling for robustness. Despite occasional false positives and false negatives, these tools provide invaluable insights into vulnerabilities, coding errors, and best practices. By adopting static code analysis tools, developers can proactively enhance code quality, identify and mitigate potential security vulnerabilities, and ensure the reliability of their software.
These tools offer real-time detection, seamless integration with development workflows, and comprehensive reporting, allowing for swift remediation and improved productivity. In a rapidly evolving digital landscape, these tools play a vital role in building trust, dependability, and resilience in software systems. By leveraging the power of static code analysis, developers can deliver secure and reliable software solutions, mitigate risks, enhance user confidence, and elevate overall development practices.
Incorporating static code analysis into the software development lifecycle is essential for creating high-quality software. With their unique capabilities, these tools enable developers to stay proactive, improve code security, and achieve excellence in software development. By embracing these tools, developers can unlock the full potential of their code and deliver exceptional software that meets the highest standards of security and reliability.
Upgrade your code quality and security today with Kodezi!
Coverity
Utilizing the state-of-the-art static analysis tool Coverity, developers can significantly improve the security and reliability of complex software projects. Coverity excels in probing the intricate components of software written in diverse languages including C/C++, Java, and C#.
It meticulously scrutinizes the code to unearth a plethora of defects such as memory corruption, resource leaks, and race conditions, as well as multiple security vulnerabilities. The power of Coverity lies not only in its capacity to identify defects but also in its ability to track trends over time.
By analyzing the ebb and flow of software quality, companies can ascertain whether their software developments are evolving towards greater excellence or if there's an urgent need for a remedial quality program. Additionally, the importance of embedding software security early in the development process—often termed as ‘shift left’—cannot be overstated. In domains where embedded software commands vital systems, such as automotive and aerospace industries, an overlooked flaw can result in grave outcomes, including system failures or unauthorized access. Coverity serves as a vigilant guard, providing comprehensive reports and integrating seamlessly with mainstream development tools, ensuring that such systems are built on a foundation of security and safety from the outset.
SonarQube excels as a versatile static code analysis tool that not only supports a myriad of programming languages but also stands as the embodiment of what it means to instill clean code practices. It thrusts forward an extensive set of rules focused on unearthing security vulnerabilities, code smells, and the bane of developers - technical debt.
It pushes the agenda of 'Clean Code', insisting that code should not only function flawlessly but also be crafted in such a way that it stands as a clear, maintainable beacon for any future voyagers in the codebase. Emphasizing quality code that shines with readability and simplicity, SonarQube becomes the vigilant overseer that provides developers with immediate insights on code health.
Complex constructs are avoided and a clear convention throughout the codebase is promoted. By embedding itself within CI/CD pipelines, SonarQube ensures that the code's clarity and security are not afterthoughts but integral parts of the continuous integration process. It serves as the lighthouse guiding ships safely into the harbor, ensuring that each iteration maintains the gold standard for code excellence. Integration with development workflows turns SonarQube not just into a tool, but a vital companion for any team striving to elevate their code to its highest potential.
Dive into the realm of code security with Clang-Tidy, a powerhouse static analysis tool essential for C and C++ developers. As part of the Clang compiler suite, the tool offers an arsenal of checks designed to unveil and resolve potential security vulnerabilities. But that's just the beginning.
With a core focus on enhancing code quality, Clang-Tidy also identifies performance bottlenecks and coding style discrepancies. Follow a structured pathway to mastering this tool, starting with acquiring the open-source Clang project and progressing to constructing your static analysis tool using Clang's front-end libraries to dissect the C++ source AST (Abstract Syntax Tree). Embrace the task of crafting a tool that can, for instance, verify the capitalization of class names in your source and header files—a testament to the potent customizability and automated refactoring skills of Clang-Tidy.
Before embarking on this journey, a primer on compilers and a grasp of C++ fundamentals set the stage for a productive learning experience. Grasp the significance of programming language safety, its vital role in fabricating secure and reliable software systems, and understand how enhancements in language safety, particularly in memory safety, can shield our increasingly digital world from catastrophic cyber incidents. With a commitment to fostering excellence in software development and offering recommendations to pinpoint the most effective static analysis tools, Clang-Tidy stands as a beacon of security in an age where robust coding practices are not just an asset but a necessity for developers, practitioners, and researchers alike.
Polyspace, as a cutting-edge static code analysis (SCA) tool, has established its prowess beyond simple bug-tracking. It digs into the very fabric of software, performing rigorous mathematical modeling to pinpoint security vulnerabilities and potential run-time errors.
For critical software where failure is not an option—think spacecraft, lifesaving medical devices, and modern vehicles—Polyspace provides peace of mind. It works by dissecting codebases at the granular level of units such as functions or classes to ensure each segment's integrity contributes to a dependable whole.
Taking to heart lessons from the field, Polyspace emerges as a sentinel against the looming shadows of code deficiency. In a world where software complexities balloon and reliance on multitudes of obscure libraries is rampant, its capability to meticulously comb through lines of code and flag obscurities is indispensable.
It underscores the dire need for quality—a synergy of trust, dependability, and resilience in software systems. Aligning with stringent industry standards, such as ISO 26262 for automotive safety, Polyspace's analysis establishes an assurance case, becoming instrumental in compliance and certification processes. Studies recommend SCA tools like Polyspace as a criteria for selecting software for high-stakes environments, where one oversight can be catastrophic. Moreover, the tool houses the prescient ability to evolve with emerging paradigms in technology, from AI-based systems to autonomous vehicles, safeguarding against the errors of today and the unknown threats of tomorrow.
CppCheck serves the critical function of enhancing code security and vulnerability management in C and C++ codebases. Leveraging the power of Static Code Analysis (SCA), it meticulously scans source code, sans execution, employing Data Flow Analysis among other techniques.
This analysis is crucial for mapping out potential variables' values across the code, laying bare vulnerabilities like null pointer dereferences and buffer overflows, as well as errors such as uninitialized variables and memory leaks. While CppCheck adeptly pinpoints a breadth of potential issues, practitioners must navigate the challenge of false positives—a common SCA plight where non-exploitable bugs masquerade as genuine threats due to the tool's occasional inability to accurately track data integrity through the application.
Despite this, CppCheck's capacity for seamless IDE integration and its free, open-source nature solidify its status as an invaluable asset in the developer's toolkit. Moreover, adhering to the guidelines set forth in the NISTIR 8397 offers a framework for reliable and secure software construction. To extract the utmost benefit from such tools in modern, agile development environments, incorporating a security requirements questionnaire into feature development from the onset can effectively tailor the Software Development Life Cycle to mitigate pertinent risks. As emphasized by experts, threat modeling and a discerning approach to development can substantially reduce noise and focus on genuine security enhancements.
Compiler-based tools such as ASAN (AddressSanitizer) and TSAN (ThreadSanitizer) represent pivotal strides in code security, tracing their conceptual heritage to the early days of computing as described in the Universal Turing Machine paper, which influenced the "stored-program computer" model integral to the Von Neumann architecture. Recognizing the critical need for simplified memory management outlined by Von Neumann's design, ASAN provides a robust line of defense against memory corruption bugs like buffer overflows and use-after-free errors—predominant culprits in security breaches that impose substantial costs on users.
Similarly, TSAN stands guard against the peril of data races and concurrent programming pitfalls, which can be as destructive as memory errors if left unchecked. Paired with other sanitizers, including UBSAN for undefined behaviors, they furnish developers with a comprehensive arsenal for early detection and mitigation of vulnerabilities, aligning with research recommendations that underscore the priority of enhancing software reliability through improved static analysis tools.
Revolutionizing the world of code security, Codium.ai stands at the forefront with its advanced dynamic analysis capabilities. This sophisticated tool employs AI-driven algorithms to scrutinize code execution patterns and behaviors as the code operates, offering a proactive stance against possible security breaches. What sets Codium.ai apart is its agility in pinpointing abnormalities and potential security exploits the moment they transpire.
For developers tasked with upholding the sanctity of their codebase, the real-time notifications and in-depth reporting features become indispensable tools. They allow swift rectification of discovered vulnerabilities, thereby bolstering both the security posture and robustness of their software solutions. Reflecting on research that underscores the necessity for adept static analysis tools, Codium.ai presents itself as more than just an option; it is a companion in the pursuit of excellence in software development and a harbinger for elevated quality and reliability in software systems.

HelloBar serves as a static code analysis tool that goes beyond just probing code quality. It is tailored to pinpoint security loopholes and ensure maintainability, thus fostering resilient codebases. This resource is essential in preemptively addressing software susceptibilities by providing a thorough suite of analysis features that not only detect but also recommend solutions to bolster code security.
With its user-centric design, HelloBar seamlessly fuses with prevalent coding environments, streamlining the process of integrating secure coding protocols into developers' daily regime. Delivered through an intuitive dashboard, it generates elaborate reports, affording developers the insight to rectify issues swiftly and decisively. Furthermore, its actionable tips are instrumental in preserving exceptional code quality, thereby mitigating potential security predicaments.
An illustrative case underscores the indispensability of such analytic rigor: upon encountering a new codebase, perhaps one derived from an options-based market protocol, a holistic assessment is imperative. Developers must discern whether they are dealing with novel or forked code and, if the latter, gauge the extent of modifications. Focusing on the principal functions invoked by users unveils a clearer outlook on security and functionality.
Supporting this, recent research advocates for a standardized recommendation framework that facilitates software developers in selecting the optimal static analysis tools. This initiative also triggers further inquiry into refining said tools, driving enhancements in software system quality and development practices. As analysis trends materialize over time, they unveil patterns - a first step that should be complemented by examining how these patterns evolve, thereby revealing which software firms are advancing and which ought to adopt a quality enhancement plan.

In conclusion, static code analysis tools are indispensable for enhancing software security and reliability. These tools, such as PVS Studio, Parasoft, Coverity, SonarQube, Clang-Tidy, Polyspace, CppCheck, ASAN/TSAN, Codium.ai, and HelloBar, offer unique features and benefits that revolutionize the development process. From precise vulnerability identification to extensive language support and actionable advice, these tools empower developers to address issues efficiently and improve the overall security posture of their software.
They enable trend tracking, clean code practices, performance analysis, and mathematical modeling for robustness. Despite occasional false positives and false negatives, these tools provide invaluable insights into vulnerabilities, coding errors, and best practices. By adopting static code analysis tools, developers can proactively enhance code quality, identify and mitigate potential security vulnerabilities, and ensure the reliability of their software.
These tools offer real-time detection, seamless integration with development workflows, and comprehensive reporting, allowing for swift remediation and improved productivity. In a rapidly evolving digital landscape, these tools play a vital role in building trust, dependability, and resilience in software systems. By leveraging the power of static code analysis, developers can deliver secure and reliable software solutions, mitigate risks, enhance user confidence, and elevate overall development practices.
Incorporating static code analysis into the software development lifecycle is essential for creating high-quality software. With their unique capabilities, these tools enable developers to stay proactive, improve code security, and achieve excellence in software development. By embracing these tools, developers can unlock the full potential of their code and deliver exceptional software that meets the highest standards of security and reliability.
Upgrade your code quality and security today with Kodezi!
SonarQube
SonarQube excels as a versatile static code analysis tool that not only supports a myriad of programming languages but also stands as the embodiment of what it means to instill clean code practices. It thrusts forward an extensive set of rules focused on unearthing security vulnerabilities, code smells, and the bane of developers - technical debt.
It pushes the agenda of 'Clean Code', insisting that code should not only function flawlessly but also be crafted in such a way that it stands as a clear, maintainable beacon for any future voyagers in the codebase. Emphasizing quality code that shines with readability and simplicity, SonarQube becomes the vigilant overseer that provides developers with immediate insights on code health.
Complex constructs are avoided and a clear convention throughout the codebase is promoted. By embedding itself within CI/CD pipelines, SonarQube ensures that the code's clarity and security are not afterthoughts but integral parts of the continuous integration process. It serves as the lighthouse guiding ships safely into the harbor, ensuring that each iteration maintains the gold standard for code excellence. Integration with development workflows turns SonarQube not just into a tool, but a vital companion for any team striving to elevate their code to its highest potential.
Dive into the realm of code security with Clang-Tidy, a powerhouse static analysis tool essential for C and C++ developers. As part of the Clang compiler suite, the tool offers an arsenal of checks designed to unveil and resolve potential security vulnerabilities. But that's just the beginning.
With a core focus on enhancing code quality, Clang-Tidy also identifies performance bottlenecks and coding style discrepancies. Follow a structured pathway to mastering this tool, starting with acquiring the open-source Clang project and progressing to constructing your static analysis tool using Clang's front-end libraries to dissect the C++ source AST (Abstract Syntax Tree). Embrace the task of crafting a tool that can, for instance, verify the capitalization of class names in your source and header files—a testament to the potent customizability and automated refactoring skills of Clang-Tidy.
Before embarking on this journey, a primer on compilers and a grasp of C++ fundamentals set the stage for a productive learning experience. Grasp the significance of programming language safety, its vital role in fabricating secure and reliable software systems, and understand how enhancements in language safety, particularly in memory safety, can shield our increasingly digital world from catastrophic cyber incidents. With a commitment to fostering excellence in software development and offering recommendations to pinpoint the most effective static analysis tools, Clang-Tidy stands as a beacon of security in an age where robust coding practices are not just an asset but a necessity for developers, practitioners, and researchers alike.
Polyspace, as a cutting-edge static code analysis (SCA) tool, has established its prowess beyond simple bug-tracking. It digs into the very fabric of software, performing rigorous mathematical modeling to pinpoint security vulnerabilities and potential run-time errors.
For critical software where failure is not an option—think spacecraft, lifesaving medical devices, and modern vehicles—Polyspace provides peace of mind. It works by dissecting codebases at the granular level of units such as functions or classes to ensure each segment's integrity contributes to a dependable whole.
Taking to heart lessons from the field, Polyspace emerges as a sentinel against the looming shadows of code deficiency. In a world where software complexities balloon and reliance on multitudes of obscure libraries is rampant, its capability to meticulously comb through lines of code and flag obscurities is indispensable.
It underscores the dire need for quality—a synergy of trust, dependability, and resilience in software systems. Aligning with stringent industry standards, such as ISO 26262 for automotive safety, Polyspace's analysis establishes an assurance case, becoming instrumental in compliance and certification processes. Studies recommend SCA tools like Polyspace as a criteria for selecting software for high-stakes environments, where one oversight can be catastrophic. Moreover, the tool houses the prescient ability to evolve with emerging paradigms in technology, from AI-based systems to autonomous vehicles, safeguarding against the errors of today and the unknown threats of tomorrow.
CppCheck serves the critical function of enhancing code security and vulnerability management in C and C++ codebases. Leveraging the power of Static Code Analysis (SCA), it meticulously scans source code, sans execution, employing Data Flow Analysis among other techniques.
This analysis is crucial for mapping out potential variables' values across the code, laying bare vulnerabilities like null pointer dereferences and buffer overflows, as well as errors such as uninitialized variables and memory leaks. While CppCheck adeptly pinpoints a breadth of potential issues, practitioners must navigate the challenge of false positives—a common SCA plight where non-exploitable bugs masquerade as genuine threats due to the tool's occasional inability to accurately track data integrity through the application.
Despite this, CppCheck's capacity for seamless IDE integration and its free, open-source nature solidify its status as an invaluable asset in the developer's toolkit. Moreover, adhering to the guidelines set forth in the NISTIR 8397 offers a framework for reliable and secure software construction. To extract the utmost benefit from such tools in modern, agile development environments, incorporating a security requirements questionnaire into feature development from the onset can effectively tailor the Software Development Life Cycle to mitigate pertinent risks. As emphasized by experts, threat modeling and a discerning approach to development can substantially reduce noise and focus on genuine security enhancements.
Compiler-based tools such as ASAN (AddressSanitizer) and TSAN (ThreadSanitizer) represent pivotal strides in code security, tracing their conceptual heritage to the early days of computing as described in the Universal Turing Machine paper, which influenced the "stored-program computer" model integral to the Von Neumann architecture. Recognizing the critical need for simplified memory management outlined by Von Neumann's design, ASAN provides a robust line of defense against memory corruption bugs like buffer overflows and use-after-free errors—predominant culprits in security breaches that impose substantial costs on users.
Similarly, TSAN stands guard against the peril of data races and concurrent programming pitfalls, which can be as destructive as memory errors if left unchecked. Paired with other sanitizers, including UBSAN for undefined behaviors, they furnish developers with a comprehensive arsenal for early detection and mitigation of vulnerabilities, aligning with research recommendations that underscore the priority of enhancing software reliability through improved static analysis tools.
Revolutionizing the world of code security, Codium.ai stands at the forefront with its advanced dynamic analysis capabilities. This sophisticated tool employs AI-driven algorithms to scrutinize code execution patterns and behaviors as the code operates, offering a proactive stance against possible security breaches. What sets Codium.ai apart is its agility in pinpointing abnormalities and potential security exploits the moment they transpire.
For developers tasked with upholding the sanctity of their codebase, the real-time notifications and in-depth reporting features become indispensable tools. They allow swift rectification of discovered vulnerabilities, thereby bolstering both the security posture and robustness of their software solutions. Reflecting on research that underscores the necessity for adept static analysis tools, Codium.ai presents itself as more than just an option; it is a companion in the pursuit of excellence in software development and a harbinger for elevated quality and reliability in software systems.

HelloBar serves as a static code analysis tool that goes beyond just probing code quality. It is tailored to pinpoint security loopholes and ensure maintainability, thus fostering resilient codebases. This resource is essential in preemptively addressing software susceptibilities by providing a thorough suite of analysis features that not only detect but also recommend solutions to bolster code security.
With its user-centric design, HelloBar seamlessly fuses with prevalent coding environments, streamlining the process of integrating secure coding protocols into developers' daily regime. Delivered through an intuitive dashboard, it generates elaborate reports, affording developers the insight to rectify issues swiftly and decisively. Furthermore, its actionable tips are instrumental in preserving exceptional code quality, thereby mitigating potential security predicaments.
An illustrative case underscores the indispensability of such analytic rigor: upon encountering a new codebase, perhaps one derived from an options-based market protocol, a holistic assessment is imperative. Developers must discern whether they are dealing with novel or forked code and, if the latter, gauge the extent of modifications. Focusing on the principal functions invoked by users unveils a clearer outlook on security and functionality.
Supporting this, recent research advocates for a standardized recommendation framework that facilitates software developers in selecting the optimal static analysis tools. This initiative also triggers further inquiry into refining said tools, driving enhancements in software system quality and development practices. As analysis trends materialize over time, they unveil patterns - a first step that should be complemented by examining how these patterns evolve, thereby revealing which software firms are advancing and which ought to adopt a quality enhancement plan.

In conclusion, static code analysis tools are indispensable for enhancing software security and reliability. These tools, such as PVS Studio, Parasoft, Coverity, SonarQube, Clang-Tidy, Polyspace, CppCheck, ASAN/TSAN, Codium.ai, and HelloBar, offer unique features and benefits that revolutionize the development process. From precise vulnerability identification to extensive language support and actionable advice, these tools empower developers to address issues efficiently and improve the overall security posture of their software.
They enable trend tracking, clean code practices, performance analysis, and mathematical modeling for robustness. Despite occasional false positives and false negatives, these tools provide invaluable insights into vulnerabilities, coding errors, and best practices. By adopting static code analysis tools, developers can proactively enhance code quality, identify and mitigate potential security vulnerabilities, and ensure the reliability of their software.
These tools offer real-time detection, seamless integration with development workflows, and comprehensive reporting, allowing for swift remediation and improved productivity. In a rapidly evolving digital landscape, these tools play a vital role in building trust, dependability, and resilience in software systems. By leveraging the power of static code analysis, developers can deliver secure and reliable software solutions, mitigate risks, enhance user confidence, and elevate overall development practices.
Incorporating static code analysis into the software development lifecycle is essential for creating high-quality software. With their unique capabilities, these tools enable developers to stay proactive, improve code security, and achieve excellence in software development. By embracing these tools, developers can unlock the full potential of their code and deliver exceptional software that meets the highest standards of security and reliability.
Upgrade your code quality and security today with Kodezi!
Clang-Tidy
Dive into the realm of code security with Clang-Tidy, a powerhouse static analysis tool essential for C and C++ developers. As part of the Clang compiler suite, the tool offers an arsenal of checks designed to unveil and resolve potential security vulnerabilities. But that's just the beginning.
With a core focus on enhancing code quality, Clang-Tidy also identifies performance bottlenecks and coding style discrepancies. Follow a structured pathway to mastering this tool, starting with acquiring the open-source Clang project and progressing to constructing your static analysis tool using Clang's front-end libraries to dissect the C++ source AST (Abstract Syntax Tree). Embrace the task of crafting a tool that can, for instance, verify the capitalization of class names in your source and header files—a testament to the potent customizability and automated refactoring skills of Clang-Tidy.
Before embarking on this journey, a primer on compilers and a grasp of C++ fundamentals set the stage for a productive learning experience. Grasp the significance of programming language safety, its vital role in fabricating secure and reliable software systems, and understand how enhancements in language safety, particularly in memory safety, can shield our increasingly digital world from catastrophic cyber incidents. With a commitment to fostering excellence in software development and offering recommendations to pinpoint the most effective static analysis tools, Clang-Tidy stands as a beacon of security in an age where robust coding practices are not just an asset but a necessity for developers, practitioners, and researchers alike.
Polyspace, as a cutting-edge static code analysis (SCA) tool, has established its prowess beyond simple bug-tracking. It digs into the very fabric of software, performing rigorous mathematical modeling to pinpoint security vulnerabilities and potential run-time errors.
For critical software where failure is not an option—think spacecraft, lifesaving medical devices, and modern vehicles—Polyspace provides peace of mind. It works by dissecting codebases at the granular level of units such as functions or classes to ensure each segment's integrity contributes to a dependable whole.
Taking to heart lessons from the field, Polyspace emerges as a sentinel against the looming shadows of code deficiency. In a world where software complexities balloon and reliance on multitudes of obscure libraries is rampant, its capability to meticulously comb through lines of code and flag obscurities is indispensable.
It underscores the dire need for quality—a synergy of trust, dependability, and resilience in software systems. Aligning with stringent industry standards, such as ISO 26262 for automotive safety, Polyspace's analysis establishes an assurance case, becoming instrumental in compliance and certification processes. Studies recommend SCA tools like Polyspace as a criteria for selecting software for high-stakes environments, where one oversight can be catastrophic. Moreover, the tool houses the prescient ability to evolve with emerging paradigms in technology, from AI-based systems to autonomous vehicles, safeguarding against the errors of today and the unknown threats of tomorrow.
CppCheck serves the critical function of enhancing code security and vulnerability management in C and C++ codebases. Leveraging the power of Static Code Analysis (SCA), it meticulously scans source code, sans execution, employing Data Flow Analysis among other techniques.
This analysis is crucial for mapping out potential variables' values across the code, laying bare vulnerabilities like null pointer dereferences and buffer overflows, as well as errors such as uninitialized variables and memory leaks. While CppCheck adeptly pinpoints a breadth of potential issues, practitioners must navigate the challenge of false positives—a common SCA plight where non-exploitable bugs masquerade as genuine threats due to the tool's occasional inability to accurately track data integrity through the application.
Despite this, CppCheck's capacity for seamless IDE integration and its free, open-source nature solidify its status as an invaluable asset in the developer's toolkit. Moreover, adhering to the guidelines set forth in the NISTIR 8397 offers a framework for reliable and secure software construction. To extract the utmost benefit from such tools in modern, agile development environments, incorporating a security requirements questionnaire into feature development from the onset can effectively tailor the Software Development Life Cycle to mitigate pertinent risks. As emphasized by experts, threat modeling and a discerning approach to development can substantially reduce noise and focus on genuine security enhancements.
Compiler-based tools such as ASAN (AddressSanitizer) and TSAN (ThreadSanitizer) represent pivotal strides in code security, tracing their conceptual heritage to the early days of computing as described in the Universal Turing Machine paper, which influenced the "stored-program computer" model integral to the Von Neumann architecture. Recognizing the critical need for simplified memory management outlined by Von Neumann's design, ASAN provides a robust line of defense against memory corruption bugs like buffer overflows and use-after-free errors—predominant culprits in security breaches that impose substantial costs on users.
Similarly, TSAN stands guard against the peril of data races and concurrent programming pitfalls, which can be as destructive as memory errors if left unchecked. Paired with other sanitizers, including UBSAN for undefined behaviors, they furnish developers with a comprehensive arsenal for early detection and mitigation of vulnerabilities, aligning with research recommendations that underscore the priority of enhancing software reliability through improved static analysis tools.
Revolutionizing the world of code security, Codium.ai stands at the forefront with its advanced dynamic analysis capabilities. This sophisticated tool employs AI-driven algorithms to scrutinize code execution patterns and behaviors as the code operates, offering a proactive stance against possible security breaches. What sets Codium.ai apart is its agility in pinpointing abnormalities and potential security exploits the moment they transpire.
For developers tasked with upholding the sanctity of their codebase, the real-time notifications and in-depth reporting features become indispensable tools. They allow swift rectification of discovered vulnerabilities, thereby bolstering both the security posture and robustness of their software solutions. Reflecting on research that underscores the necessity for adept static analysis tools, Codium.ai presents itself as more than just an option; it is a companion in the pursuit of excellence in software development and a harbinger for elevated quality and reliability in software systems.

HelloBar serves as a static code analysis tool that goes beyond just probing code quality. It is tailored to pinpoint security loopholes and ensure maintainability, thus fostering resilient codebases. This resource is essential in preemptively addressing software susceptibilities by providing a thorough suite of analysis features that not only detect but also recommend solutions to bolster code security.
With its user-centric design, HelloBar seamlessly fuses with prevalent coding environments, streamlining the process of integrating secure coding protocols into developers' daily regime. Delivered through an intuitive dashboard, it generates elaborate reports, affording developers the insight to rectify issues swiftly and decisively. Furthermore, its actionable tips are instrumental in preserving exceptional code quality, thereby mitigating potential security predicaments.
An illustrative case underscores the indispensability of such analytic rigor: upon encountering a new codebase, perhaps one derived from an options-based market protocol, a holistic assessment is imperative. Developers must discern whether they are dealing with novel or forked code and, if the latter, gauge the extent of modifications. Focusing on the principal functions invoked by users unveils a clearer outlook on security and functionality.
Supporting this, recent research advocates for a standardized recommendation framework that facilitates software developers in selecting the optimal static analysis tools. This initiative also triggers further inquiry into refining said tools, driving enhancements in software system quality and development practices. As analysis trends materialize over time, they unveil patterns - a first step that should be complemented by examining how these patterns evolve, thereby revealing which software firms are advancing and which ought to adopt a quality enhancement plan.

In conclusion, static code analysis tools are indispensable for enhancing software security and reliability. These tools, such as PVS Studio, Parasoft, Coverity, SonarQube, Clang-Tidy, Polyspace, CppCheck, ASAN/TSAN, Codium.ai, and HelloBar, offer unique features and benefits that revolutionize the development process. From precise vulnerability identification to extensive language support and actionable advice, these tools empower developers to address issues efficiently and improve the overall security posture of their software.
They enable trend tracking, clean code practices, performance analysis, and mathematical modeling for robustness. Despite occasional false positives and false negatives, these tools provide invaluable insights into vulnerabilities, coding errors, and best practices. By adopting static code analysis tools, developers can proactively enhance code quality, identify and mitigate potential security vulnerabilities, and ensure the reliability of their software.
These tools offer real-time detection, seamless integration with development workflows, and comprehensive reporting, allowing for swift remediation and improved productivity. In a rapidly evolving digital landscape, these tools play a vital role in building trust, dependability, and resilience in software systems. By leveraging the power of static code analysis, developers can deliver secure and reliable software solutions, mitigate risks, enhance user confidence, and elevate overall development practices.
Incorporating static code analysis into the software development lifecycle is essential for creating high-quality software. With their unique capabilities, these tools enable developers to stay proactive, improve code security, and achieve excellence in software development. By embracing these tools, developers can unlock the full potential of their code and deliver exceptional software that meets the highest standards of security and reliability.
Upgrade your code quality and security today with Kodezi!
Polyspace
Polyspace, as a cutting-edge static code analysis (SCA) tool, has established its prowess beyond simple bug-tracking. It digs into the very fabric of software, performing rigorous mathematical modeling to pinpoint security vulnerabilities and potential run-time errors.
For critical software where failure is not an option—think spacecraft, lifesaving medical devices, and modern vehicles—Polyspace provides peace of mind. It works by dissecting codebases at the granular level of units such as functions or classes to ensure each segment's integrity contributes to a dependable whole.
Taking to heart lessons from the field, Polyspace emerges as a sentinel against the looming shadows of code deficiency. In a world where software complexities balloon and reliance on multitudes of obscure libraries is rampant, its capability to meticulously comb through lines of code and flag obscurities is indispensable.
It underscores the dire need for quality—a synergy of trust, dependability, and resilience in software systems. Aligning with stringent industry standards, such as ISO 26262 for automotive safety, Polyspace's analysis establishes an assurance case, becoming instrumental in compliance and certification processes. Studies recommend SCA tools like Polyspace as a criteria for selecting software for high-stakes environments, where one oversight can be catastrophic. Moreover, the tool houses the prescient ability to evolve with emerging paradigms in technology, from AI-based systems to autonomous vehicles, safeguarding against the errors of today and the unknown threats of tomorrow.
CppCheck serves the critical function of enhancing code security and vulnerability management in C and C++ codebases. Leveraging the power of Static Code Analysis (SCA), it meticulously scans source code, sans execution, employing Data Flow Analysis among other techniques.
This analysis is crucial for mapping out potential variables' values across the code, laying bare vulnerabilities like null pointer dereferences and buffer overflows, as well as errors such as uninitialized variables and memory leaks. While CppCheck adeptly pinpoints a breadth of potential issues, practitioners must navigate the challenge of false positives—a common SCA plight where non-exploitable bugs masquerade as genuine threats due to the tool's occasional inability to accurately track data integrity through the application.
Despite this, CppCheck's capacity for seamless IDE integration and its free, open-source nature solidify its status as an invaluable asset in the developer's toolkit. Moreover, adhering to the guidelines set forth in the NISTIR 8397 offers a framework for reliable and secure software construction. To extract the utmost benefit from such tools in modern, agile development environments, incorporating a security requirements questionnaire into feature development from the onset can effectively tailor the Software Development Life Cycle to mitigate pertinent risks. As emphasized by experts, threat modeling and a discerning approach to development can substantially reduce noise and focus on genuine security enhancements.
Compiler-based tools such as ASAN (AddressSanitizer) and TSAN (ThreadSanitizer) represent pivotal strides in code security, tracing their conceptual heritage to the early days of computing as described in the Universal Turing Machine paper, which influenced the "stored-program computer" model integral to the Von Neumann architecture. Recognizing the critical need for simplified memory management outlined by Von Neumann's design, ASAN provides a robust line of defense against memory corruption bugs like buffer overflows and use-after-free errors—predominant culprits in security breaches that impose substantial costs on users.
Similarly, TSAN stands guard against the peril of data races and concurrent programming pitfalls, which can be as destructive as memory errors if left unchecked. Paired with other sanitizers, including UBSAN for undefined behaviors, they furnish developers with a comprehensive arsenal for early detection and mitigation of vulnerabilities, aligning with research recommendations that underscore the priority of enhancing software reliability through improved static analysis tools.
Revolutionizing the world of code security, Codium.ai stands at the forefront with its advanced dynamic analysis capabilities. This sophisticated tool employs AI-driven algorithms to scrutinize code execution patterns and behaviors as the code operates, offering a proactive stance against possible security breaches. What sets Codium.ai apart is its agility in pinpointing abnormalities and potential security exploits the moment they transpire.
For developers tasked with upholding the sanctity of their codebase, the real-time notifications and in-depth reporting features become indispensable tools. They allow swift rectification of discovered vulnerabilities, thereby bolstering both the security posture and robustness of their software solutions. Reflecting on research that underscores the necessity for adept static analysis tools, Codium.ai presents itself as more than just an option; it is a companion in the pursuit of excellence in software development and a harbinger for elevated quality and reliability in software systems.

HelloBar serves as a static code analysis tool that goes beyond just probing code quality. It is tailored to pinpoint security loopholes and ensure maintainability, thus fostering resilient codebases. This resource is essential in preemptively addressing software susceptibilities by providing a thorough suite of analysis features that not only detect but also recommend solutions to bolster code security.
With its user-centric design, HelloBar seamlessly fuses with prevalent coding environments, streamlining the process of integrating secure coding protocols into developers' daily regime. Delivered through an intuitive dashboard, it generates elaborate reports, affording developers the insight to rectify issues swiftly and decisively. Furthermore, its actionable tips are instrumental in preserving exceptional code quality, thereby mitigating potential security predicaments.
An illustrative case underscores the indispensability of such analytic rigor: upon encountering a new codebase, perhaps one derived from an options-based market protocol, a holistic assessment is imperative. Developers must discern whether they are dealing with novel or forked code and, if the latter, gauge the extent of modifications. Focusing on the principal functions invoked by users unveils a clearer outlook on security and functionality.
Supporting this, recent research advocates for a standardized recommendation framework that facilitates software developers in selecting the optimal static analysis tools. This initiative also triggers further inquiry into refining said tools, driving enhancements in software system quality and development practices. As analysis trends materialize over time, they unveil patterns - a first step that should be complemented by examining how these patterns evolve, thereby revealing which software firms are advancing and which ought to adopt a quality enhancement plan.

In conclusion, static code analysis tools are indispensable for enhancing software security and reliability. These tools, such as PVS Studio, Parasoft, Coverity, SonarQube, Clang-Tidy, Polyspace, CppCheck, ASAN/TSAN, Codium.ai, and HelloBar, offer unique features and benefits that revolutionize the development process. From precise vulnerability identification to extensive language support and actionable advice, these tools empower developers to address issues efficiently and improve the overall security posture of their software.
They enable trend tracking, clean code practices, performance analysis, and mathematical modeling for robustness. Despite occasional false positives and false negatives, these tools provide invaluable insights into vulnerabilities, coding errors, and best practices. By adopting static code analysis tools, developers can proactively enhance code quality, identify and mitigate potential security vulnerabilities, and ensure the reliability of their software.
These tools offer real-time detection, seamless integration with development workflows, and comprehensive reporting, allowing for swift remediation and improved productivity. In a rapidly evolving digital landscape, these tools play a vital role in building trust, dependability, and resilience in software systems. By leveraging the power of static code analysis, developers can deliver secure and reliable software solutions, mitigate risks, enhance user confidence, and elevate overall development practices.
Incorporating static code analysis into the software development lifecycle is essential for creating high-quality software. With their unique capabilities, these tools enable developers to stay proactive, improve code security, and achieve excellence in software development. By embracing these tools, developers can unlock the full potential of their code and deliver exceptional software that meets the highest standards of security and reliability.
Upgrade your code quality and security today with Kodezi!
CppCheck
CppCheck serves the critical function of enhancing code security and vulnerability management in C and C++ codebases. Leveraging the power of Static Code Analysis (SCA), it meticulously scans source code, sans execution, employing Data Flow Analysis among other techniques.
This analysis is crucial for mapping out potential variables' values across the code, laying bare vulnerabilities like null pointer dereferences and buffer overflows, as well as errors such as uninitialized variables and memory leaks. While CppCheck adeptly pinpoints a breadth of potential issues, practitioners must navigate the challenge of false positives—a common SCA plight where non-exploitable bugs masquerade as genuine threats due to the tool's occasional inability to accurately track data integrity through the application.
Despite this, CppCheck's capacity for seamless IDE integration and its free, open-source nature solidify its status as an invaluable asset in the developer's toolkit. Moreover, adhering to the guidelines set forth in the NISTIR 8397 offers a framework for reliable and secure software construction. To extract the utmost benefit from such tools in modern, agile development environments, incorporating a security requirements questionnaire into feature development from the onset can effectively tailor the Software Development Life Cycle to mitigate pertinent risks. As emphasized by experts, threat modeling and a discerning approach to development can substantially reduce noise and focus on genuine security enhancements.
Compiler-based tools such as ASAN (AddressSanitizer) and TSAN (ThreadSanitizer) represent pivotal strides in code security, tracing their conceptual heritage to the early days of computing as described in the Universal Turing Machine paper, which influenced the "stored-program computer" model integral to the Von Neumann architecture. Recognizing the critical need for simplified memory management outlined by Von Neumann's design, ASAN provides a robust line of defense against memory corruption bugs like buffer overflows and use-after-free errors—predominant culprits in security breaches that impose substantial costs on users.
Similarly, TSAN stands guard against the peril of data races and concurrent programming pitfalls, which can be as destructive as memory errors if left unchecked. Paired with other sanitizers, including UBSAN for undefined behaviors, they furnish developers with a comprehensive arsenal for early detection and mitigation of vulnerabilities, aligning with research recommendations that underscore the priority of enhancing software reliability through improved static analysis tools.
Revolutionizing the world of code security, Codium.ai stands at the forefront with its advanced dynamic analysis capabilities. This sophisticated tool employs AI-driven algorithms to scrutinize code execution patterns and behaviors as the code operates, offering a proactive stance against possible security breaches. What sets Codium.ai apart is its agility in pinpointing abnormalities and potential security exploits the moment they transpire.
For developers tasked with upholding the sanctity of their codebase, the real-time notifications and in-depth reporting features become indispensable tools. They allow swift rectification of discovered vulnerabilities, thereby bolstering both the security posture and robustness of their software solutions. Reflecting on research that underscores the necessity for adept static analysis tools, Codium.ai presents itself as more than just an option; it is a companion in the pursuit of excellence in software development and a harbinger for elevated quality and reliability in software systems.

HelloBar serves as a static code analysis tool that goes beyond just probing code quality. It is tailored to pinpoint security loopholes and ensure maintainability, thus fostering resilient codebases. This resource is essential in preemptively addressing software susceptibilities by providing a thorough suite of analysis features that not only detect but also recommend solutions to bolster code security.
With its user-centric design, HelloBar seamlessly fuses with prevalent coding environments, streamlining the process of integrating secure coding protocols into developers' daily regime. Delivered through an intuitive dashboard, it generates elaborate reports, affording developers the insight to rectify issues swiftly and decisively. Furthermore, its actionable tips are instrumental in preserving exceptional code quality, thereby mitigating potential security predicaments.
An illustrative case underscores the indispensability of such analytic rigor: upon encountering a new codebase, perhaps one derived from an options-based market protocol, a holistic assessment is imperative. Developers must discern whether they are dealing with novel or forked code and, if the latter, gauge the extent of modifications. Focusing on the principal functions invoked by users unveils a clearer outlook on security and functionality.
Supporting this, recent research advocates for a standardized recommendation framework that facilitates software developers in selecting the optimal static analysis tools. This initiative also triggers further inquiry into refining said tools, driving enhancements in software system quality and development practices. As analysis trends materialize over time, they unveil patterns - a first step that should be complemented by examining how these patterns evolve, thereby revealing which software firms are advancing and which ought to adopt a quality enhancement plan.

In conclusion, static code analysis tools are indispensable for enhancing software security and reliability. These tools, such as PVS Studio, Parasoft, Coverity, SonarQube, Clang-Tidy, Polyspace, CppCheck, ASAN/TSAN, Codium.ai, and HelloBar, offer unique features and benefits that revolutionize the development process. From precise vulnerability identification to extensive language support and actionable advice, these tools empower developers to address issues efficiently and improve the overall security posture of their software.
They enable trend tracking, clean code practices, performance analysis, and mathematical modeling for robustness. Despite occasional false positives and false negatives, these tools provide invaluable insights into vulnerabilities, coding errors, and best practices. By adopting static code analysis tools, developers can proactively enhance code quality, identify and mitigate potential security vulnerabilities, and ensure the reliability of their software.
These tools offer real-time detection, seamless integration with development workflows, and comprehensive reporting, allowing for swift remediation and improved productivity. In a rapidly evolving digital landscape, these tools play a vital role in building trust, dependability, and resilience in software systems. By leveraging the power of static code analysis, developers can deliver secure and reliable software solutions, mitigate risks, enhance user confidence, and elevate overall development practices.
Incorporating static code analysis into the software development lifecycle is essential for creating high-quality software. With their unique capabilities, these tools enable developers to stay proactive, improve code security, and achieve excellence in software development. By embracing these tools, developers can unlock the full potential of their code and deliver exceptional software that meets the highest standards of security and reliability.
Upgrade your code quality and security today with Kodezi!
ASAN/TSAN
Compiler-based tools such as ASAN (AddressSanitizer) and TSAN (ThreadSanitizer) represent pivotal strides in code security, tracing their conceptual heritage to the early days of computing as described in the Universal Turing Machine paper, which influenced the "stored-program computer" model integral to the Von Neumann architecture. Recognizing the critical need for simplified memory management outlined by Von Neumann's design, ASAN provides a robust line of defense against memory corruption bugs like buffer overflows and use-after-free errors—predominant culprits in security breaches that impose substantial costs on users.
Similarly, TSAN stands guard against the peril of data races and concurrent programming pitfalls, which can be as destructive as memory errors if left unchecked. Paired with other sanitizers, including UBSAN for undefined behaviors, they furnish developers with a comprehensive arsenal for early detection and mitigation of vulnerabilities, aligning with research recommendations that underscore the priority of enhancing software reliability through improved static analysis tools.
Revolutionizing the world of code security, Codium.ai stands at the forefront with its advanced dynamic analysis capabilities. This sophisticated tool employs AI-driven algorithms to scrutinize code execution patterns and behaviors as the code operates, offering a proactive stance against possible security breaches. What sets Codium.ai apart is its agility in pinpointing abnormalities and potential security exploits the moment they transpire.
For developers tasked with upholding the sanctity of their codebase, the real-time notifications and in-depth reporting features become indispensable tools. They allow swift rectification of discovered vulnerabilities, thereby bolstering both the security posture and robustness of their software solutions. Reflecting on research that underscores the necessity for adept static analysis tools, Codium.ai presents itself as more than just an option; it is a companion in the pursuit of excellence in software development and a harbinger for elevated quality and reliability in software systems.

HelloBar serves as a static code analysis tool that goes beyond just probing code quality. It is tailored to pinpoint security loopholes and ensure maintainability, thus fostering resilient codebases. This resource is essential in preemptively addressing software susceptibilities by providing a thorough suite of analysis features that not only detect but also recommend solutions to bolster code security.
With its user-centric design, HelloBar seamlessly fuses with prevalent coding environments, streamlining the process of integrating secure coding protocols into developers' daily regime. Delivered through an intuitive dashboard, it generates elaborate reports, affording developers the insight to rectify issues swiftly and decisively. Furthermore, its actionable tips are instrumental in preserving exceptional code quality, thereby mitigating potential security predicaments.
An illustrative case underscores the indispensability of such analytic rigor: upon encountering a new codebase, perhaps one derived from an options-based market protocol, a holistic assessment is imperative. Developers must discern whether they are dealing with novel or forked code and, if the latter, gauge the extent of modifications. Focusing on the principal functions invoked by users unveils a clearer outlook on security and functionality.
Supporting this, recent research advocates for a standardized recommendation framework that facilitates software developers in selecting the optimal static analysis tools. This initiative also triggers further inquiry into refining said tools, driving enhancements in software system quality and development practices. As analysis trends materialize over time, they unveil patterns - a first step that should be complemented by examining how these patterns evolve, thereby revealing which software firms are advancing and which ought to adopt a quality enhancement plan.

In conclusion, static code analysis tools are indispensable for enhancing software security and reliability. These tools, such as PVS Studio, Parasoft, Coverity, SonarQube, Clang-Tidy, Polyspace, CppCheck, ASAN/TSAN, Codium.ai, and HelloBar, offer unique features and benefits that revolutionize the development process. From precise vulnerability identification to extensive language support and actionable advice, these tools empower developers to address issues efficiently and improve the overall security posture of their software.
They enable trend tracking, clean code practices, performance analysis, and mathematical modeling for robustness. Despite occasional false positives and false negatives, these tools provide invaluable insights into vulnerabilities, coding errors, and best practices. By adopting static code analysis tools, developers can proactively enhance code quality, identify and mitigate potential security vulnerabilities, and ensure the reliability of their software.
These tools offer real-time detection, seamless integration with development workflows, and comprehensive reporting, allowing for swift remediation and improved productivity. In a rapidly evolving digital landscape, these tools play a vital role in building trust, dependability, and resilience in software systems. By leveraging the power of static code analysis, developers can deliver secure and reliable software solutions, mitigate risks, enhance user confidence, and elevate overall development practices.
Incorporating static code analysis into the software development lifecycle is essential for creating high-quality software. With their unique capabilities, these tools enable developers to stay proactive, improve code security, and achieve excellence in software development. By embracing these tools, developers can unlock the full potential of their code and deliver exceptional software that meets the highest standards of security and reliability.
Upgrade your code quality and security today with Kodezi!
Codium.ai
Revolutionizing the world of code security, Codium.ai stands at the forefront with its advanced dynamic analysis capabilities. This sophisticated tool employs AI-driven algorithms to scrutinize code execution patterns and behaviors as the code operates, offering a proactive stance against possible security breaches. What sets Codium.ai apart is its agility in pinpointing abnormalities and potential security exploits the moment they transpire.
For developers tasked with upholding the sanctity of their codebase, the real-time notifications and in-depth reporting features become indispensable tools. They allow swift rectification of discovered vulnerabilities, thereby bolstering both the security posture and robustness of their software solutions. Reflecting on research that underscores the necessity for adept static analysis tools, Codium.ai presents itself as more than just an option; it is a companion in the pursuit of excellence in software development and a harbinger for elevated quality and reliability in software systems.

HelloBar serves as a static code analysis tool that goes beyond just probing code quality. It is tailored to pinpoint security loopholes and ensure maintainability, thus fostering resilient codebases. This resource is essential in preemptively addressing software susceptibilities by providing a thorough suite of analysis features that not only detect but also recommend solutions to bolster code security.
With its user-centric design, HelloBar seamlessly fuses with prevalent coding environments, streamlining the process of integrating secure coding protocols into developers' daily regime. Delivered through an intuitive dashboard, it generates elaborate reports, affording developers the insight to rectify issues swiftly and decisively. Furthermore, its actionable tips are instrumental in preserving exceptional code quality, thereby mitigating potential security predicaments.
An illustrative case underscores the indispensability of such analytic rigor: upon encountering a new codebase, perhaps one derived from an options-based market protocol, a holistic assessment is imperative. Developers must discern whether they are dealing with novel or forked code and, if the latter, gauge the extent of modifications. Focusing on the principal functions invoked by users unveils a clearer outlook on security and functionality.
Supporting this, recent research advocates for a standardized recommendation framework that facilitates software developers in selecting the optimal static analysis tools. This initiative also triggers further inquiry into refining said tools, driving enhancements in software system quality and development practices. As analysis trends materialize over time, they unveil patterns - a first step that should be complemented by examining how these patterns evolve, thereby revealing which software firms are advancing and which ought to adopt a quality enhancement plan.

In conclusion, static code analysis tools are indispensable for enhancing software security and reliability. These tools, such as PVS Studio, Parasoft, Coverity, SonarQube, Clang-Tidy, Polyspace, CppCheck, ASAN/TSAN, Codium.ai, and HelloBar, offer unique features and benefits that revolutionize the development process. From precise vulnerability identification to extensive language support and actionable advice, these tools empower developers to address issues efficiently and improve the overall security posture of their software.
They enable trend tracking, clean code practices, performance analysis, and mathematical modeling for robustness. Despite occasional false positives and false negatives, these tools provide invaluable insights into vulnerabilities, coding errors, and best practices. By adopting static code analysis tools, developers can proactively enhance code quality, identify and mitigate potential security vulnerabilities, and ensure the reliability of their software.
These tools offer real-time detection, seamless integration with development workflows, and comprehensive reporting, allowing for swift remediation and improved productivity. In a rapidly evolving digital landscape, these tools play a vital role in building trust, dependability, and resilience in software systems. By leveraging the power of static code analysis, developers can deliver secure and reliable software solutions, mitigate risks, enhance user confidence, and elevate overall development practices.
Incorporating static code analysis into the software development lifecycle is essential for creating high-quality software. With their unique capabilities, these tools enable developers to stay proactive, improve code security, and achieve excellence in software development. By embracing these tools, developers can unlock the full potential of their code and deliver exceptional software that meets the highest standards of security and reliability.
Upgrade your code quality and security today with Kodezi!
HelloBar
HelloBar serves as a static code analysis tool that goes beyond just probing code quality. It is tailored to pinpoint security loopholes and ensure maintainability, thus fostering resilient codebases. This resource is essential in preemptively addressing software susceptibilities by providing a thorough suite of analysis features that not only detect but also recommend solutions to bolster code security.
With its user-centric design, HelloBar seamlessly fuses with prevalent coding environments, streamlining the process of integrating secure coding protocols into developers' daily regime. Delivered through an intuitive dashboard, it generates elaborate reports, affording developers the insight to rectify issues swiftly and decisively. Furthermore, its actionable tips are instrumental in preserving exceptional code quality, thereby mitigating potential security predicaments.
An illustrative case underscores the indispensability of such analytic rigor: upon encountering a new codebase, perhaps one derived from an options-based market protocol, a holistic assessment is imperative. Developers must discern whether they are dealing with novel or forked code and, if the latter, gauge the extent of modifications. Focusing on the principal functions invoked by users unveils a clearer outlook on security and functionality.
Supporting this, recent research advocates for a standardized recommendation framework that facilitates software developers in selecting the optimal static analysis tools. This initiative also triggers further inquiry into refining said tools, driving enhancements in software system quality and development practices. As analysis trends materialize over time, they unveil patterns - a first step that should be complemented by examining how these patterns evolve, thereby revealing which software firms are advancing and which ought to adopt a quality enhancement plan.

In conclusion, static code analysis tools are indispensable for enhancing software security and reliability. These tools, such as PVS Studio, Parasoft, Coverity, SonarQube, Clang-Tidy, Polyspace, CppCheck, ASAN/TSAN, Codium.ai, and HelloBar, offer unique features and benefits that revolutionize the development process. From precise vulnerability identification to extensive language support and actionable advice, these tools empower developers to address issues efficiently and improve the overall security posture of their software.
They enable trend tracking, clean code practices, performance analysis, and mathematical modeling for robustness. Despite occasional false positives and false negatives, these tools provide invaluable insights into vulnerabilities, coding errors, and best practices. By adopting static code analysis tools, developers can proactively enhance code quality, identify and mitigate potential security vulnerabilities, and ensure the reliability of their software.
These tools offer real-time detection, seamless integration with development workflows, and comprehensive reporting, allowing for swift remediation and improved productivity. In a rapidly evolving digital landscape, these tools play a vital role in building trust, dependability, and resilience in software systems. By leveraging the power of static code analysis, developers can deliver secure and reliable software solutions, mitigate risks, enhance user confidence, and elevate overall development practices.
Incorporating static code analysis into the software development lifecycle is essential for creating high-quality software. With their unique capabilities, these tools enable developers to stay proactive, improve code security, and achieve excellence in software development. By embracing these tools, developers can unlock the full potential of their code and deliver exceptional software that meets the highest standards of security and reliability.
Upgrade your code quality and security today with Kodezi!
Conclusion
In conclusion, static code analysis tools are indispensable for enhancing software security and reliability. These tools, such as PVS Studio, Parasoft, Coverity, SonarQube, Clang-Tidy, Polyspace, CppCheck, ASAN/TSAN, Codium.ai, and HelloBar, offer unique features and benefits that revolutionize the development process. From precise vulnerability identification to extensive language support and actionable advice, these tools empower developers to address issues efficiently and improve the overall security posture of their software.
They enable trend tracking, clean code practices, performance analysis, and mathematical modeling for robustness. Despite occasional false positives and false negatives, these tools provide invaluable insights into vulnerabilities, coding errors, and best practices. By adopting static code analysis tools, developers can proactively enhance code quality, identify and mitigate potential security vulnerabilities, and ensure the reliability of their software.
These tools offer real-time detection, seamless integration with development workflows, and comprehensive reporting, allowing for swift remediation and improved productivity. In a rapidly evolving digital landscape, these tools play a vital role in building trust, dependability, and resilience in software systems. By leveraging the power of static code analysis, developers can deliver secure and reliable software solutions, mitigate risks, enhance user confidence, and elevate overall development practices.
Incorporating static code analysis into the software development lifecycle is essential for creating high-quality software. With their unique capabilities, these tools enable developers to stay proactive, improve code security, and achieve excellence in software development. By embracing these tools, developers can unlock the full potential of their code and deliver exceptional software that meets the highest standards of security and reliability.




