Overview
The article titled "10 SAST Vulnerabilities Every Developer Should Address" sheds light on the critical security weaknesses that developers must recognize and tackle in software development. It identifies various vulnerabilities, including:
- SQL Injection
- Cross-Site Scripting (XSS)
- Sensitive data exposure
By emphasizing the importance of utilizing Static Application Security Testing (SAST) tools, the article encourages developers to proactively identify and mitigate these risks. This approach not only enhances overall application security but also boosts developer productivity, making it essential reading for those looking to improve their coding practices.
Introduction
In the ever-evolving landscape of software development, security challenges are increasingly pressing as organizations strive to protect their applications from a myriad of vulnerabilities. How can developers effectively address these challenges?
Static Application Security Testing (SAST) tools have emerged as essential allies in this battle, enabling developers to identify and rectify potential security flaws before they can be exploited. With alarming statistics revealing the prevalence of vulnerabilities such as:
- SQL Injection
- Cross-Site Scripting (XSS)
- Sensitive data exposure
the urgency for robust security measures is undeniable. This article delves into the critical role of SAST tools, highlighting their effectiveness in detecting common vulnerabilities. Furthermore, developers can adopt proactive strategies to enhance application security. As the digital landscape grows increasingly complex, understanding and leveraging these tools is vital for safeguarding sensitive information and maintaining user trust.
Kodezi | Professional OpenAPI Specification Generator - AI Dev-Tool: Automate Detection of SAST Vulnerabilities
Developers often face significant challenges when it comes to ensuring the security of their code. Kodezi's Professional OpenAPI Specification Generator harnesses advanced AI to automate the detection of SAST vulnerabilities, addressing these challenges head-on. In 2025, a notable 37% of organizations intend to adopt Software Composition Analysis (SCA) during development, emphasizing an increasing awareness of the necessity for strong protective measures against vulnerable open-source components. By effortlessly merging into the development workflow, Kodezi enables developers to detect potential vulnerabilities early in the coding process.
This proactive approach not only enhances code protection but also simplifies the development cycle. With Kodezi, teams can focus on building robust applications without the ongoing worry of missed vulnerabilities. Kodezi CLI serves as a versatile tool for B2B engineering teams, autonomously improving codebases and fixing bugs before they reach production. As Daniel J. Galin states, "Testing is not responsible for creating quality; only for assessing it," which underscores the necessity of proactive protective measures in development.
Furthermore, the automation of SAST vulnerabilities detection via Kodezi ensures that developers can maintain high standards of code quality and safety with minimal effort. This ultimately boosts productivity and confidence in the integrity of their codebases. As Harold Abelson suggests, programs should be written for human readability, reinforcing the importance of writing secure and understandable code. With Kodezi's AI-driven automated builds and testing, teams can significantly enhance their programming productivity and code quality in software development.
Are you ready to improve your coding practices? To get started, check out our 5-minute quickstart and see a demo to experience Kodezi's capabilities firsthand.
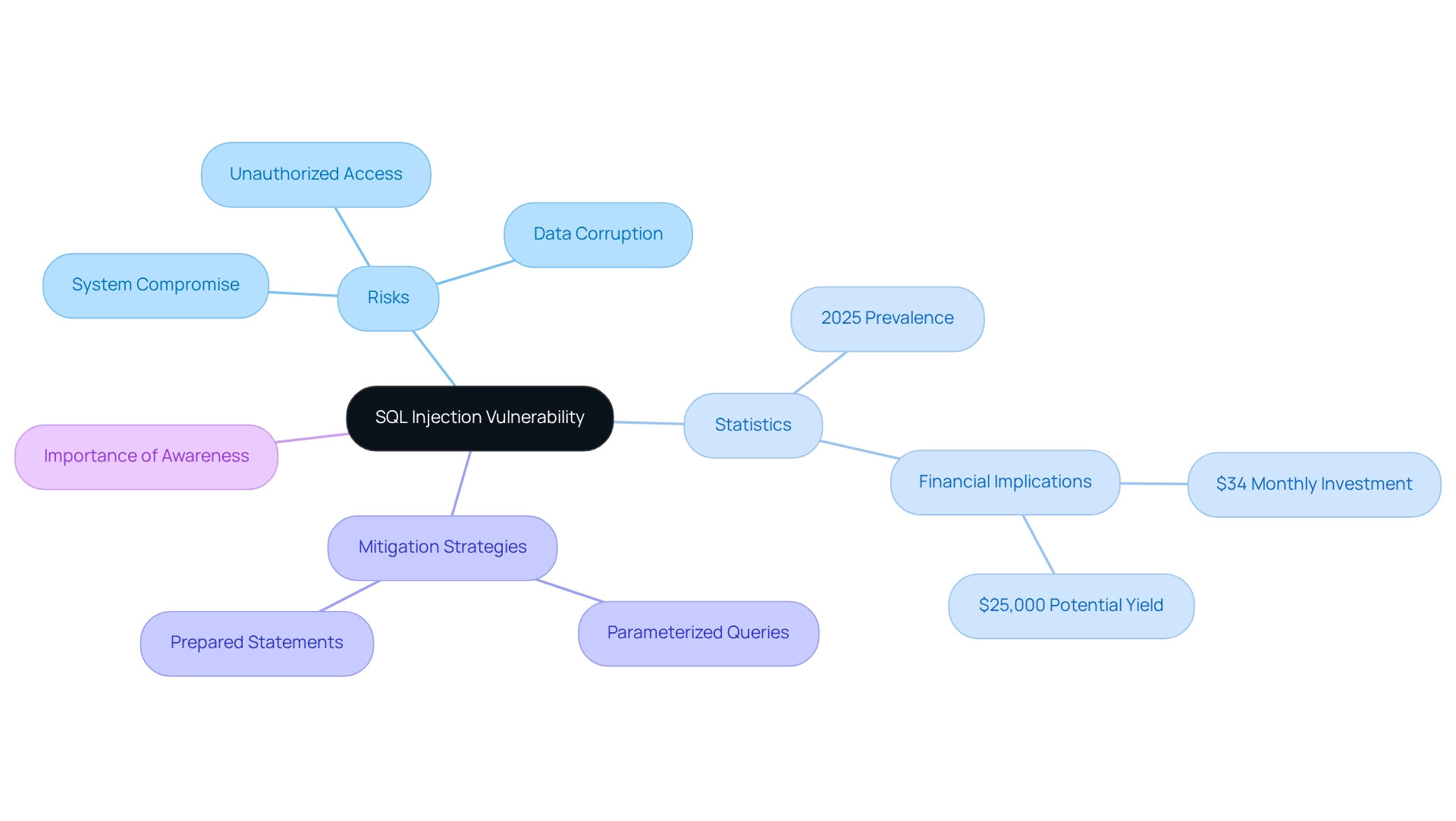
SQL Injection: A Critical Vulnerability Detected by SAST Tools
SQL Injection represents a significant risk faced by developers, particularly when applications permit untrusted data to manipulate SQL queries. This vulnerability can lead to unauthorized access to sensitive information, data corruption, or even complete system compromise.
In 2025, statistics indicate that SQL Injection weaknesses remain prevalent in web applications, with a notable increase in attacks. A mere $34 monthly investment could potentially yield a criminal $25,000 a month, underscoring the urgent need for robust protective measures, as SAST vulnerabilities can be identified through Static Application Security Testing resources that scrutinize source code for exploitable patterns.
Cybersecurity experts emphasize that the 'OR 1 = 1' clause always evaluates to true, demonstrating the ease with which SQL Injection can be executed. By implementing parameterized queries and prepared statements, developers can effectively mitigate these risks, ensuring that user inputs are sanitized before processing by the database.
The application of these strategies is vital for maintaining application integrity and security, and recent case studies, such as Panasonic's management of substantial data volumes, illustrate successful reductions in SQL Injection risks by addressing SAST vulnerabilities. This highlights their effectiveness in enhancing overall application protection.
As the cyber threat landscape evolves, it is essential for developers to stay informed about the latest trends and adopt proactive measures to safeguard their applications. Are you prepared to take action against SQL Injection vulnerabilities?
Improper Input Validation: Key SAST Vulnerability to Address
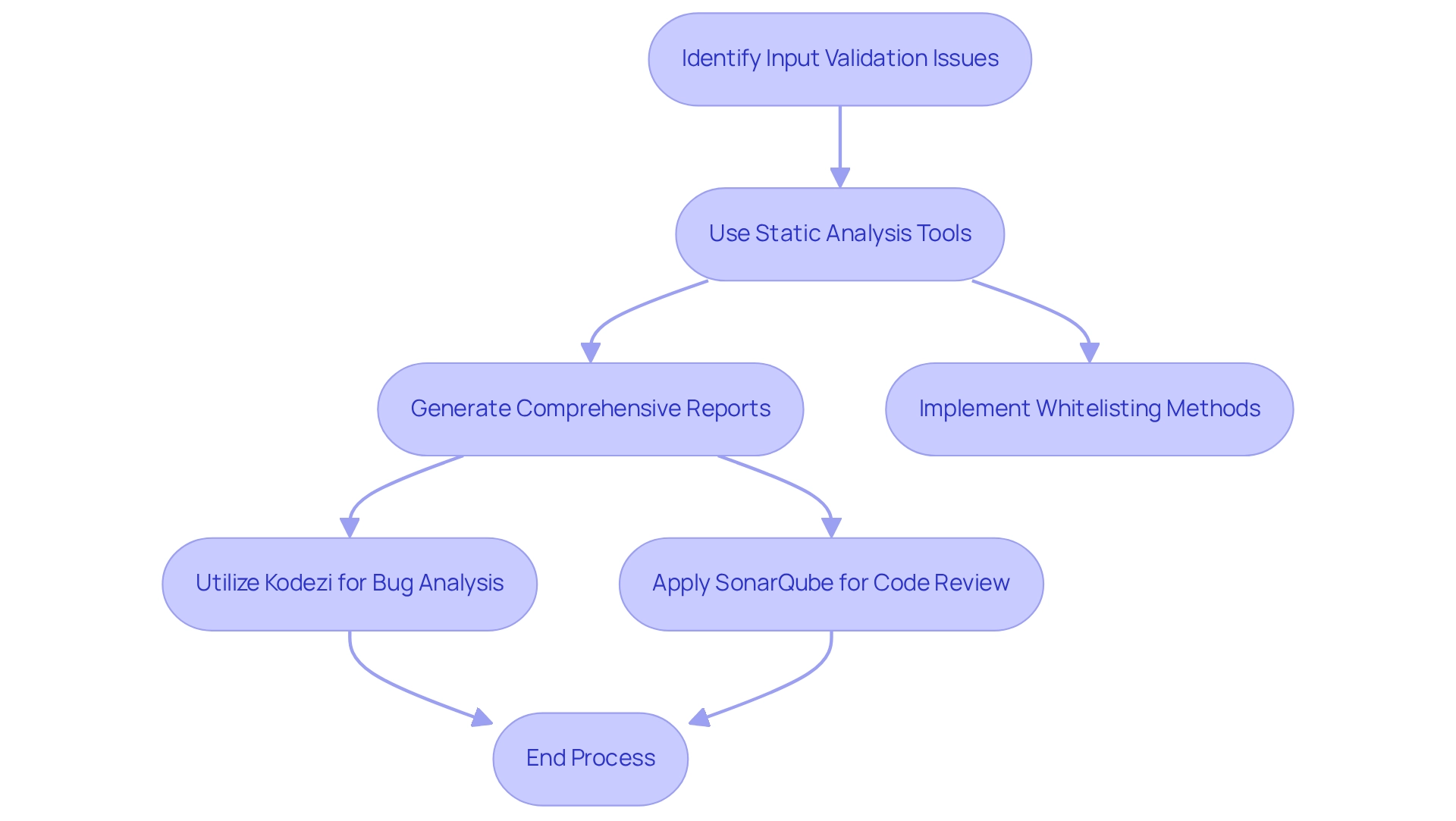
Inadequate input validation is a significant challenge that developers face, occurring when applications do not sufficiently verify or clean user inputs. This oversight can lead to serious risks, such as SQL Injection and Cross-Site Scripting (XSS). Statistics from 2025 reveal that improper input validation is a leading cause of security breaches and is considered one of the SAST vulnerabilities, highlighting the urgent need for robust validation mechanisms.
Static analysis tools are essential in detecting weaknesses by examining the code pathways that handle user inputs. For instance, static application security testing can generate comprehensive reports that summarize findings, list identified weaknesses, provide descriptions, severity ratings, and corrective recommendations. These resources empower developers to address issues efficiently.
Furthermore, tools like Kodezi enhance this process by automatically analyzing bugs and offering explanations. This functionality allows developers to optimize their code and implement strict validation rules effectively. By ensuring that all inputs conform to expected formats and types, developers can significantly reduce risks.
In addition, utilizing whitelisting methods improves protection by permitting only specified inputs, thereby minimizing the potential for exploitation by malicious actors. A case study on reducing risks with static application testing demonstrates that proactive identification and correction of SAST vulnerabilities not only safeguard organizational reputation but also sustain consumer trust, directly correlating with statistics on improper input validation weaknesses.
Similarly, resources such as SonarQube facilitate automated code review and static code analysis, assisting developers in applying appropriate input validation methods. As the landscape of application protection evolves, emphasizing input validation through static analysis resources, including innovative options like Kodezi, is crucial for defending applications against escalating threats.
Are you ready to explore the tools available on the Kodezi platform to enhance your coding practices?
Insecure Function Usage: A Common Pitfall in Application Security
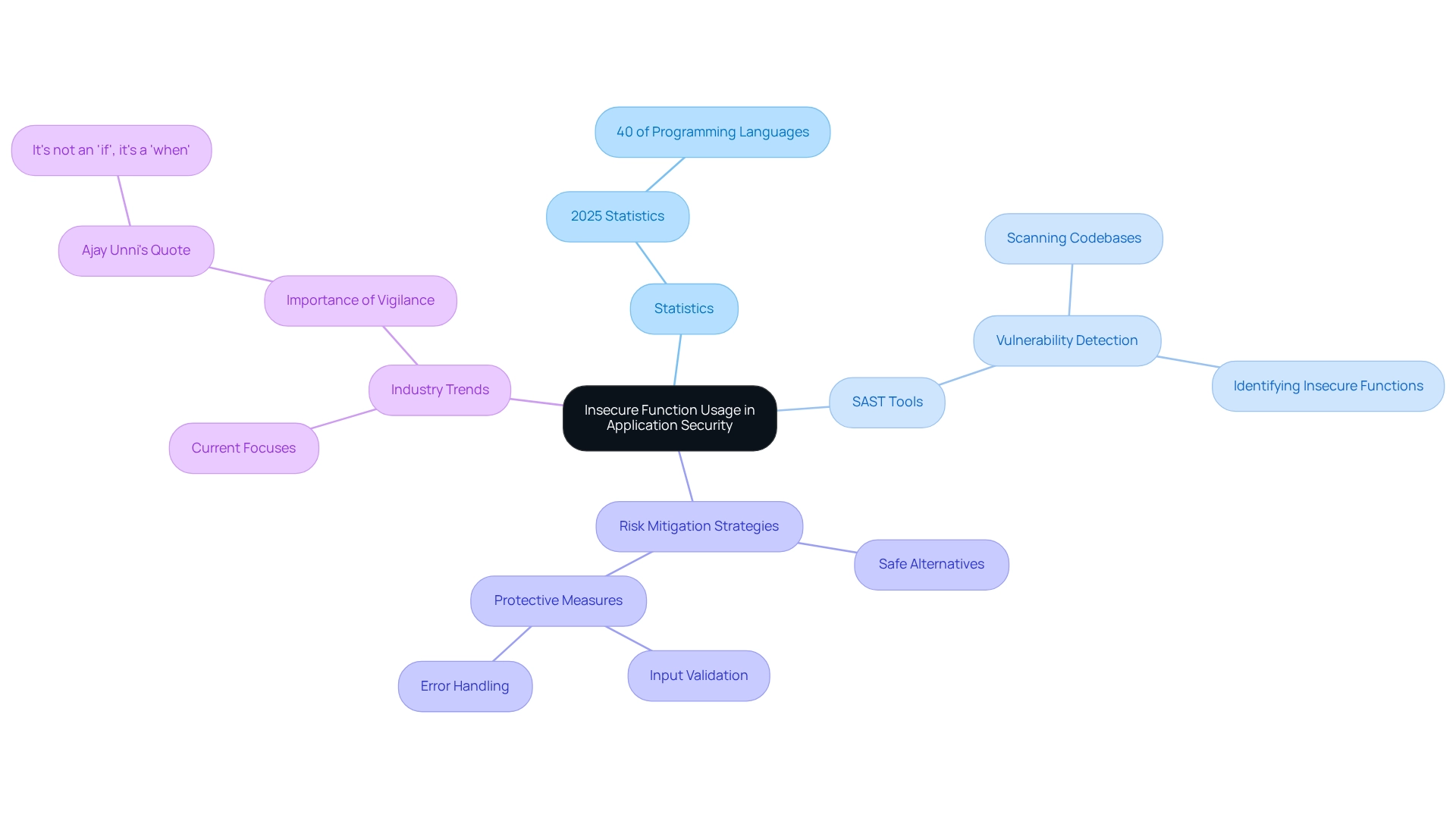
Insecure function usage presents significant challenges for developers, as it involves employing functions that are either inherently vulnerable or lack sufficient safeguards against misuse. Functions that execute system commands or manipulate memory without rigorous checks can expose applications to considerable security risks. In 2025, statistics from Myror Security reveal that approximately 40% of programming languages still utilize insecure functions, underscoring the urgency for developers to confront this issue.
SAST vulnerabilities are crucial to detect, and SAST tools help in scanning codebases for known insecure functions. Furthermore, a recent case study titled "Risk Assessment in Vulnerability Scanners" highlights that prioritizing detected vulnerabilities based on their potential impact enables organizations to allocate resources effectively, focusing on the most critical issues first.
To mitigate risks, developers are encouraged to substitute insecure functions with safe alternatives and implement strong protective measures, including input validation and thorough error handling. Industry specialists emphasize the importance of this proactive approach, noting that transitioning from vulnerable to secure functions is vital for enhancing application protection. As Ajay Unni, founder of StickmanCyber, aptly stated, "It’s not an ‘if,’ it’s a ‘when’" regarding potential cyberattacks, emphasizing the need for vigilance in coding practices.
Current trends in application protection indicate a growing emphasis on identifying and addressing insecure function usage, particularly in the first quarter of 2025. This period serves as a critical juncture for enterprises and vendors to invest in agile, intelligence-led defense mechanisms. By utilizing SAST tools, developers can not only identify SAST vulnerabilities but also stay ahead of emerging threats, ensuring their applications remain secure in an increasingly complex digital environment.
Code Injection: A Major Threat Identified by SAST
Code injection represents a significant threat to application security, allowing attackers to insert malicious code that can be executed by the system. This vulnerability can lead to unauthorized access, data breaches, and serious system compromises. As we look ahead to 2025, the prevalence of code injection flaws remains alarming, with a notable increase in reported incidents. Statistics reveal that 58% of businesses now recognize data exfiltration as their primary concern in API security, underscoring the urgency of addressing these weaknesses to protect sensitive information.
Static Application Security Testing (SAST) vulnerabilities are crucial in detecting code injection issues by thoroughly examining code for patterns that could facilitate such attacks. To effectively mitigate these risks, developers should adopt best practices, including:
- Implementing strict input validation to ensure that only expected data is processed.
- Utilizing secure coding techniques that minimize the potential for weaknesses.
- Conducting regular code reviews to identify and rectify potential injection points.
Case studies illustrate that organizations employing SAST tools have successfully identified and addressed SAST vulnerabilities related to code injection before exploitation could occur. For instance, a recent study indicated that companies integrating AI into their cybersecurity strategies could save as much as $3.81 million per breach, particularly in preventing code injection attacks. This emphasizes the financial advantages of proactive risk management.
Expert insights highlight the importance of prioritizing vulnerabilities, as not all present the same level of threat. Eoin Keary, CEO & Founder, notes, "This report aids in prioritizing what is important across sectors, as not all weaknesses pose the same level of threat." Regular audits and developer training in secure coding are essential components of a robust application security strategy. As the landscape of cyber threats evolves, staying informed about the latest trends and implementing effective prevention measures is vital for safeguarding applications against code injection attacks.
Cross-Site Scripting (XSS): A Vulnerability Every Developer Must Know
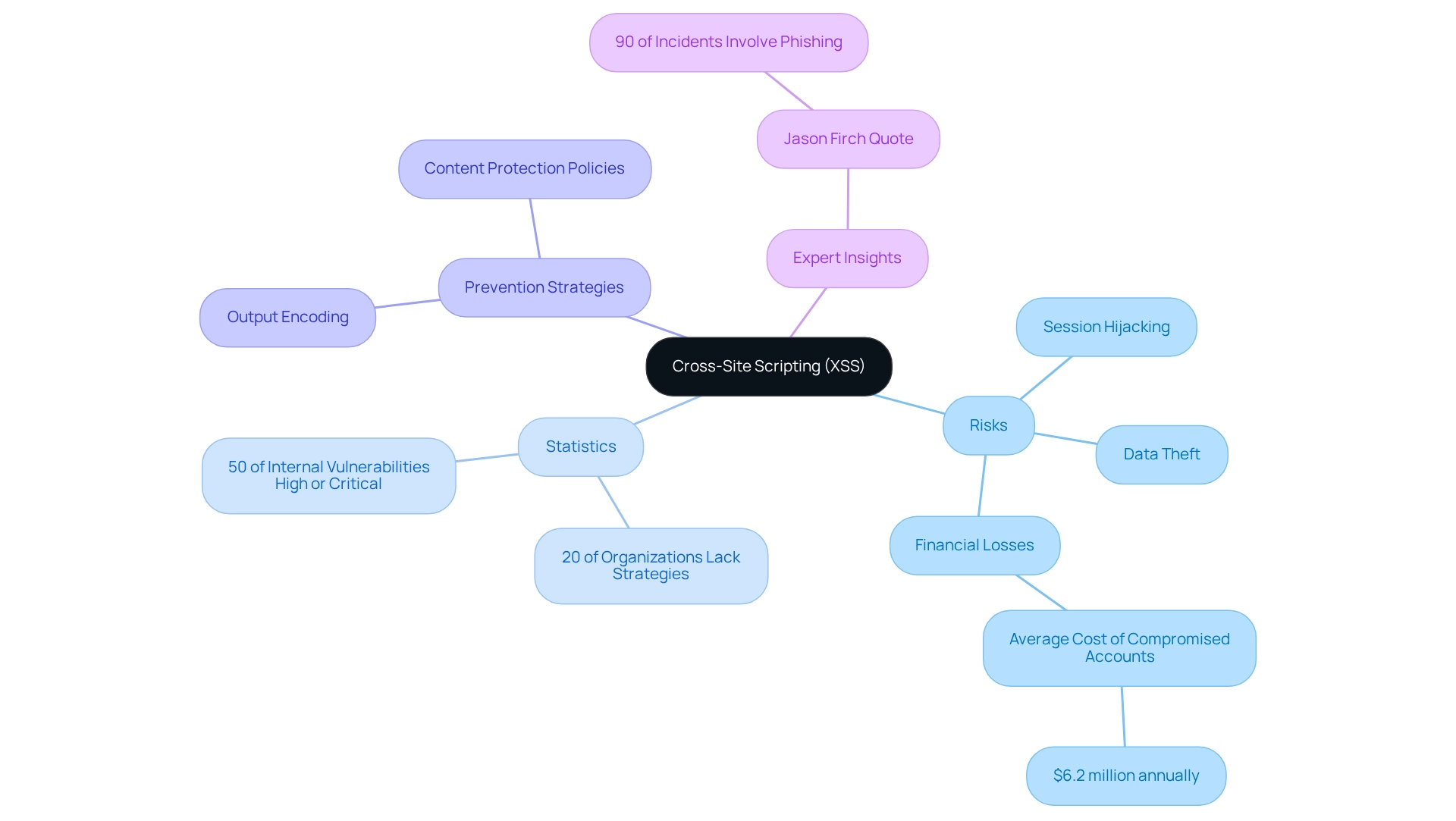
Cross-Site Scripting (XSS) flaws pose significant risks, allowing attackers to inject malicious scripts into web pages. This vulnerability can lead to session hijacking, data theft, and other harmful activities. In 2025, statistics suggest that XSS weaknesses remain a prevalent issue, with a considerable percentage of web applications still exposed to such attacks. Alarmingly, 20% of organizations do not employ any strategies to safeguard remote users accessing the internet, highlighting the commonality of issues like XSS in environments lacking protective measures.
SAST (Static Application Security Testing) tools are essential for identifying SAST vulnerabilities by examining code for unsanitized user inputs that may be displayed in the browser. To effectively reduce XSS risks, developers should prioritize output encoding and implement robust content protection policies. These practices ensure that user inputs are sanitized before display, significantly lowering the likelihood of successful attacks. Expert insights emphasize that output encoding is vital in preventing XSS, as it transforms potentially harmful input into a safe format that browsers can display without executing malicious scripts.
Recent case studies underscore the impact of XSS attacks on user data protection. Compromised web applications can lead to severe financial and reputational harm. For instance, organizations have reported significant losses due to data breaches associated with XSS weaknesses, underscoring the need for proactive protective measures. Compromised cloud accounts cost organizations an average of $6.2 million annually, illustrating the financial consequences of these vulnerabilities.
As the landscape of web protection evolves, staying informed about the latest advancements in XSS vulnerabilities is essential for developers. By utilizing tools to identify SAST vulnerabilities and adhering to best practices for prevention, developers can enhance the safety of their applications and protect user data from potential threats. Furthermore, with 50% of internal application weaknesses classified as high or critical risks, addressing XSS issues should be a top priority. As Jason Firch pointed out, due to the rise in phishing attacks, it is estimated that 90% of incidents and breaches involved a phishing component in 2019, further highlighting the interconnected nature of these threats.
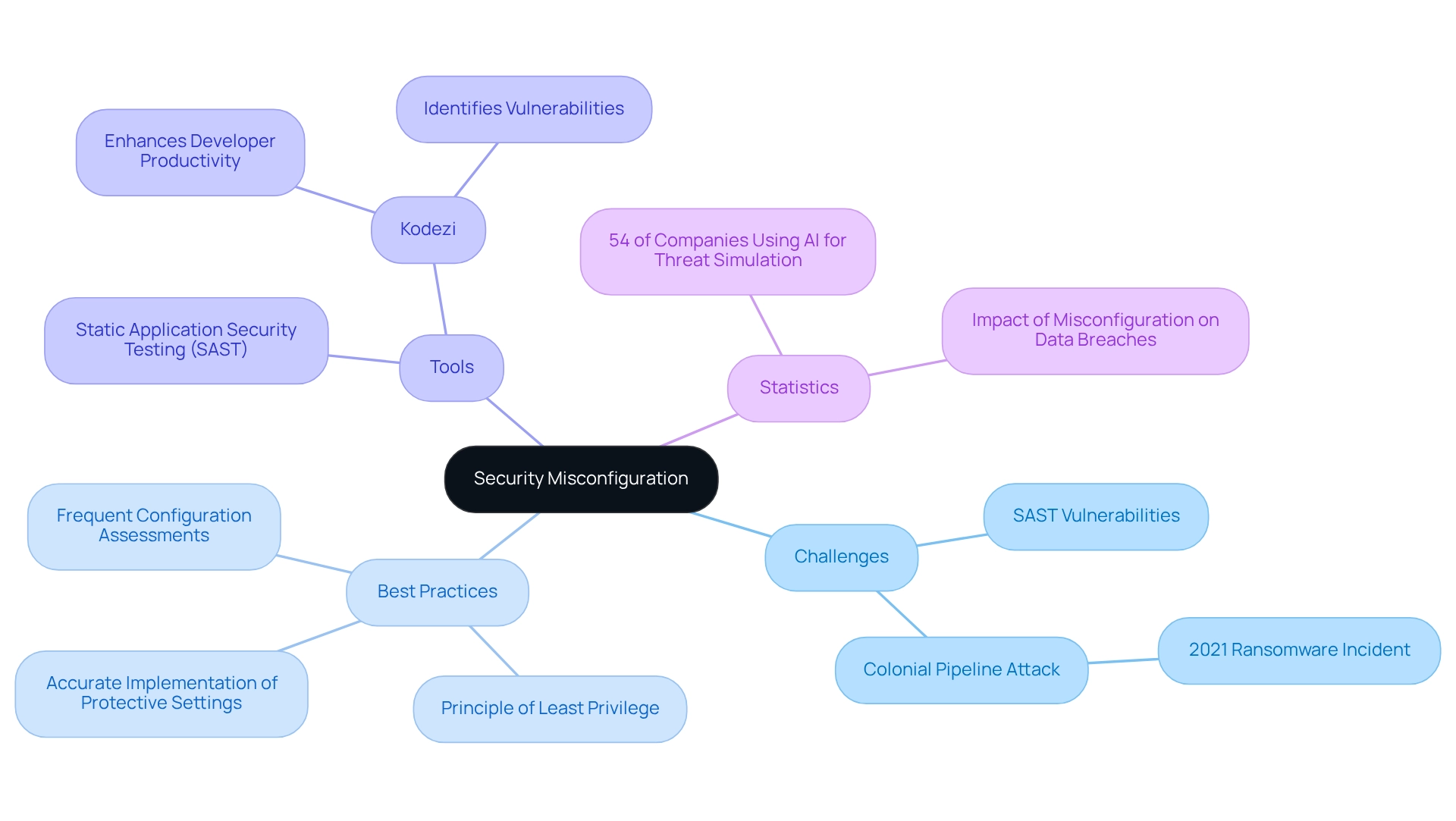
Security Misconfiguration: A Vulnerability to Monitor with SAST
Misconfiguration poses significant challenges for developers, as it leads to SAST vulnerabilities when protective settings are poorly defined, implemented, or maintained, creating exploitable weaknesses for attackers. In 2025, statistics reveal that security misconfiguration continues to be a primary reason for data breaches, underscoring the essential requirement for vigilance in application security. A notable example is the 2021 ransomware attack on the Colonial Pipeline, which illustrated the severe consequences of such vulnerabilities. Static Application Security Testing (SAST) tools play a vital role in identifying SAST vulnerabilities by thoroughly analyzing code and configuration files for insecure settings.
To mitigate the risks associated with misconfiguration, developers should adopt best practices like:
- Frequently assessing their configurations
- Applying the principle of least privilege
- Ensuring that all protective settings are accurately implemented
Experts emphasize the importance of maintaining a continuous and comprehensive perspective of configurations in today’s complex threat landscape. As William Jepma aptly notes, "As we enjoy the convenience of digital services, we must also recognize the growing attack surface and evolving threat landscape."
Organizations are increasingly aware of the impact of misconfiguration on data breaches, making proactive measures essential. A recent case study highlights that 54% of companies are leveraging AI to simulate threats, showcasing a shift toward incorporating advanced technologies in risk management. This trend emphasizes the significance of static analysis resources, such as those offered by Kodezi, which not only aid in detecting and correcting misconfigurations but also enhance overall efficiency for developers in managing SAST vulnerabilities.
User testimonials reveal that Kodezi has transformed the debugging experience for over 1,000,000 programmers. One user from the Massachusetts Institute of Technology remarked, "Kodezi has helped me find and fix bugs faster and easier than trying to manually. It is a lifesaver when it comes to correcting issues and bugs." Another user, a software engineer, expressed, "I love what Kodezi is doing with debugging; it feels like I just unlocked a new superpower!" These insights underscore how Kodezi assists in identifying vulnerabilities in configurations while significantly boosting developer productivity. By leveraging SAST vulnerabilities, developers can effectively enhance the overall security posture of their applications.
Sensitive Data Exposure: A Key Concern for Developers Using SAST
Sensitive data exposure arises when applications fail to adequately safeguard sensitive information, including personal and financial data. This weakness can lead to significant data breaches, eroding user trust and harming business reputations. In 2025, the landscape of sensitive data exposure vulnerabilities continues to evolve, with a notable increase in incidents reported. Statistics show that there have been 9,044 public data breaches since 2005, highlighting the essential need for strong protective measures. Furthermore, the alarming rise in cyber scams, which increased by 400 percent in March 2020, underscores the ongoing security threats developers face today.
SAST vulnerabilities play a vital role in identifying code areas where sensitive data is mishandled or exposed. By incorporating static application security testing into the development process, developers can actively identify weaknesses before they result in breaches. Effective strategies include:
- Implementing strong encryption
- Enforcing strict access controls
- Utilizing data masking techniques to protect sensitive information while ensuring compliance with data protection regulations
Historical case studies reveal that data breaches have been a persistent issue since the 1980s, with a marked increase in frequency and public awareness in the early 2000s. This context emphasizes the continual need for vigilance and enhancement in data protection practices. As Ajay Unni, founder of StickmanCyber, aptly states, "It’s not an ‘if,’ it’s a ‘when’"—emphasizing the inevitability of potential breaches.
The impact of sensitive data exposure on user trust and business reputation cannot be overstated. A single breach can lead to a loss of customer confidence and significant financial repercussions. To protect sensitive information efficiently, developers need to remain aware of new trends in weaknesses and utilize analysis software to improve their applications' defense stance. By doing so, they not only protect user data but also maintain trust and uphold their business's reputation in an increasingly security-conscious environment. Developers are encouraged to regularly review and update their protective practices to address SAST vulnerabilities, ensuring that SAST tools are effectively integrated into their workflows to mitigate risks.
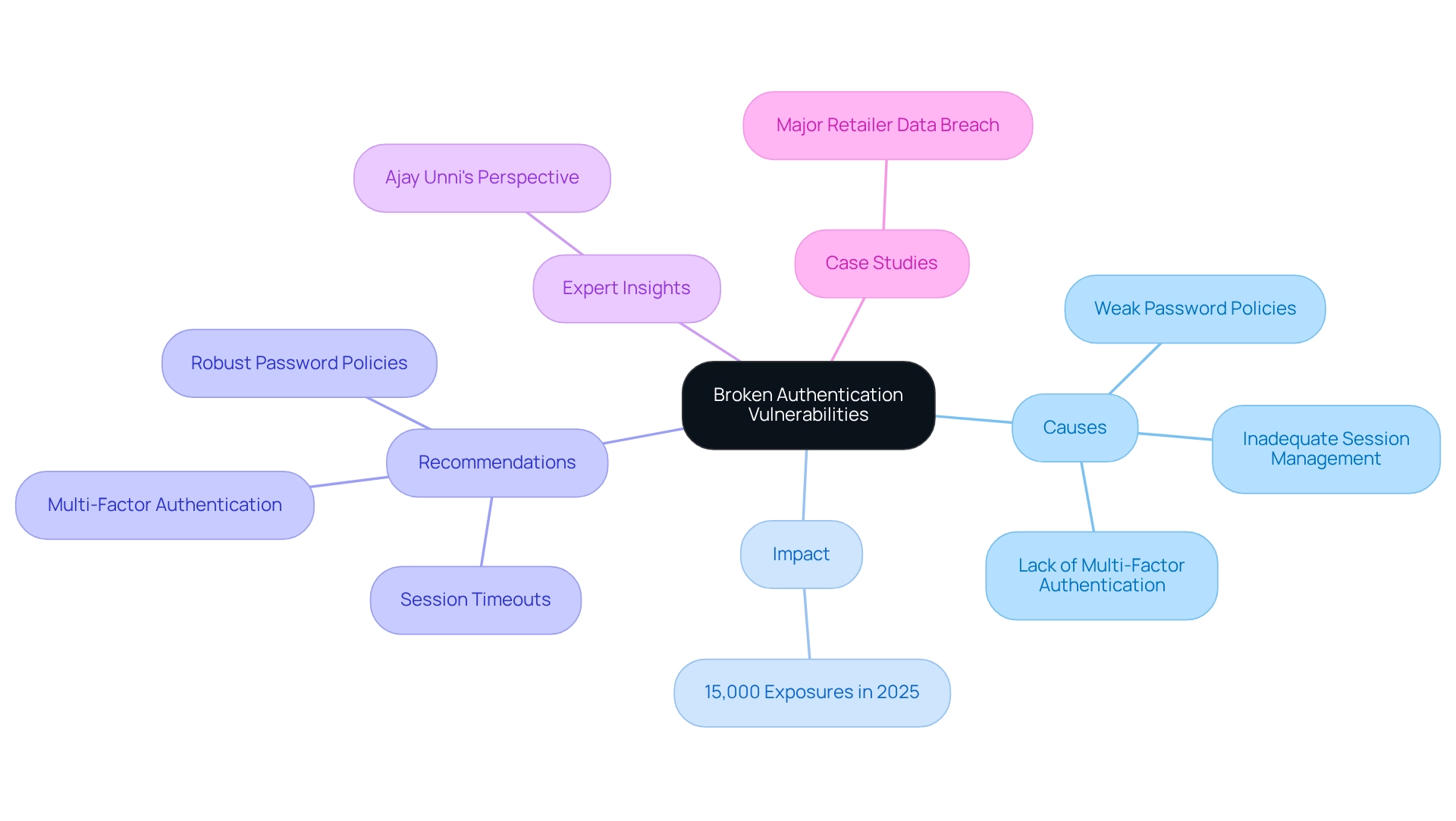
Broken Authentication: A Vulnerability Highlighted by SAST Tools
Broken authentication represents significant vulnerabilities that enable attackers to compromise user accounts or gain unauthorized access to systems. Common causes include weak password policies, inadequate session management, and the lack of multi-factor authentication. In 2025, the impact of compromised authentication on user account security remains considerable, with organizations facing an estimated 15,000 exposures specifically linked to these weaknesses across their environments. This reality underscores the urgent need for effective risk management.
Static Application Security Testing (SAST) vulnerabilities are essential in identifying issues related to broken authentication by examining code for insecure practices. These tools can effectively pinpoint weaknesses, empowering developers to take proactive measures. To enhance authentication security, developers should:
- Enforce robust password policies
- Implement session timeouts
- [Adopt multi-factor authentication
Expert insights](https://purplesec.us/resources/cybersecurity-statistics) highlight the critical necessity of addressing these vulnerabilities. As Ajay Unni, founder of StickmanCyber, states, "It’s not an ‘if,’ it’s a ‘when’—you could be the next in line, you never know." This perspective emphasizes the pressing need for organizations to embrace a comprehensive approach to exposure management, especially during Cybersecurity Awareness Month, which stresses the importance of safeguarding critical assets.
Case studies reveal that organizations often overlook issues related to broken authentication, leading to significant breaches. For example, a recent case study indicated that a major retailer experienced a data breach due to inadequate session management, resulting in the exposure of thousands of user accounts. By leveraging static analysis software, developers can identify and rectify SAST vulnerabilities, which ultimately enhances user account protection and improves overall application safety. Furthermore, employing automated systems for assessment is vital in this process, as they facilitate the detection of weaknesses and ensure a stronger defense against potential attacks.
Utilizing SAST Tools: Essential for Identifying Common Vulnerabilities
Incorporating Static Application Security Testing resources is essential for developers facing the challenge of detecting and addressing SAST vulnerabilities in their code before deployment. These instruments thoroughly examine source code for vulnerabilities, providing practical insights that greatly improve both code quality and protection. By integrating static application analysis resources into the development process, teams can identify weaknesses early, which not only lowers remediation expenses but also enhances the overall resilience of their applications.
Have you considered how frequent use of static application testing resources can foster a culture of awareness among developers? This ensures that protective measures are prioritized throughout the development process. Organizations that have adopted developer-focused practices for addressing SAST vulnerabilities report a marked improvement in their ability to maintain secure codebases. Statistics indicate that automated tools effectively enforce coding standards, leading to consistent and secure codebases.
Furthermore, creating significant metrics associated with protection is crucial for evaluating the efficiency of DevSecOps practices. By monitoring key performance indicators, organizations can identify areas for enhancement and ensure their protective measures remain strong. As industry leader Jit notes, "Effective reporting allows organizations to identify security gaps, mitigate them, and measure progress over time," highlighting the importance of integrating reporting into security practices.
In 2025, the trend of incorporating security analysis solutions into development processes continues to gain momentum, showcasing the increasing acknowledgment of their significance in contemporary software development. Case studies show that organizations utilizing static analysis resources have effectively detected weaknesses that may otherwise have remained hidden. For instance, those that have adopted static analysis instruments have reported substantial enhancements in their weakness detection rates, underscoring the practical advantages of these integrations.
To further enhance your development process, consider trying Kodezi CLI, a versatile resource designed to auto-heal codebases and boost programming productivity. Kodezi CLI not only streamlines your workflow but also addresses SAST vulnerabilities identified by tools, ensuring your code remains secure and efficient. Don't miss out on the opportunity to elevate your coding practices—sign up for a free trial today!
Conclusion
The integration of Static Application Security Testing (SAST) tools is essential for developers who seek to identify and mitigate vulnerabilities throughout the software development lifecycle. By automating the detection of security flaws, these tools enable teams to tackle issues such as:
- SQL Injection
- Cross-Site Scripting
- Sensitive data exposure
before they can be exploited. Furthermore, the proactive use of SAST not only enhances code quality but also fosters a culture of security awareness among developers, ensuring that security remains a top priority in application development.
As the landscape of cyber threats continues to evolve, it becomes increasingly clear that relying solely on traditional testing methods is insufficient. Organizations that adopt SAST tools report significant improvements in vulnerability detection rates and overall application security. Case studies highlighted throughout the article underscore the importance of these tools, demonstrating their effectiveness in safeguarding sensitive information and maintaining user trust.
In conclusion, leveraging SAST tools is not merely a best practice; it is an essential strategy for modern developers. By embedding security into the development process, teams can significantly reduce remediation costs, enhance productivity, and ultimately create more resilient applications. As the digital environment grows more complex, the need for robust security measures becomes even more critical. Embracing SAST tools like Kodezi represents a proactive step towards ensuring the integrity and security of applications in an increasingly security-conscious world.
Frequently Asked Questions
What challenges do developers face regarding code security?
Developers often struggle to ensure the security of their code, particularly in detecting vulnerabilities such as those identified through Static Application Security Testing (SAST).
How does Kodezi help with code security?
Kodezi's Professional OpenAPI Specification Generator uses advanced AI to automate the detection of SAST vulnerabilities, allowing developers to identify potential issues early in the coding process and integrate security measures seamlessly into their workflow.
What is the significance of Software Composition Analysis (SCA) in 2025?
In 2025, 37% of organizations plan to adopt Software Composition Analysis (SCA) during development, highlighting a growing awareness of the need for strong protective measures against vulnerable open-source components.
What benefits does Kodezi provide to development teams?
Kodezi enhances code protection, simplifies the development cycle, and allows teams to focus on building robust applications without the constant worry of missed vulnerabilities. It also autonomously improves codebases and fixes bugs before they reach production.
What is the importance of input validation in application security?
Inadequate input validation can lead to serious vulnerabilities, such as SQL Injection and Cross-Site Scripting (XSS). Proper validation mechanisms are essential to safeguard applications against these risks.
How can developers mitigate SQL Injection vulnerabilities?
Developers can mitigate SQL Injection risks by implementing parameterized queries and prepared statements, which ensure that user inputs are sanitized before being processed by the database.
What role do static analysis tools play in ensuring code quality?
Static analysis tools help detect weaknesses by examining code pathways that handle user inputs. They generate comprehensive reports that summarize findings, list identified weaknesses, and provide corrective recommendations.
How does Kodezi assist with input validation?
Kodezi enhances the input validation process by automatically analyzing bugs and offering explanations, allowing developers to optimize their code and implement strict validation rules effectively.
What strategies can developers use to improve input validation?
Developers can use whitelisting methods to permit only specified inputs, thereby reducing the potential for exploitation. Tools like SonarQube can also assist with automated code review and static code analysis.
What should developers do to stay informed about security threats?
Developers should stay updated on the latest trends in cybersecurity and adopt proactive measures to safeguard their applications against evolving threats, such as SQL Injection and improper input validation.




