Overview
In today's software development landscape, developers face significant challenges related to security and coding efficiency. The article presents four strategies to achieve success in secure coding automation, emphasizing the necessity of secure coding principles, the effective use of automation tools, and the importance of continuous monitoring. Kodezi addresses these challenges by providing features that streamline secure coding practices.
By implementing specific practices such as input validation, robust authentication, and regular security audits, developers can enhance application integrity and significantly reduce vulnerabilities. Furthermore, these strategies collectively contribute to a more secure software development lifecycle.
The benefits of utilizing Kodezi are clear: improved productivity and code quality. By leveraging automation tools, developers can focus on creating secure applications without compromising on efficiency. In addition, continuous monitoring ensures that security measures are always up to date, adapting to new threats as they arise.
Explore the tools available on the Kodezi platform to transform your secure coding practices. Are you ready to enhance your coding efficiency and security? Discover how Kodezi can help you achieve these goals today.
Introduction
In an age where digital security breaches are alarmingly common, have you considered the challenges developers face in ensuring secure code? Understanding and implementing secure coding practices is more critical than ever. Organizations are increasingly recognizing the importance of safeguarding their applications against vulnerabilities that could lead to catastrophic consequences.
Furthermore, Kodezi addresses these challenges with features designed to streamline security processes. From input validation and robust authentication to automated tools, the landscape of secure coding is evolving rapidly. By leveraging automation and effective tools, development teams can enhance their security posture and mitigate risks.
The benefits of using Kodezi are clear: improved productivity and higher code quality. As the stakes continue to rise, the call for a proactive approach to secure coding has never been more urgent. Are you ready to explore the tools available on the platform to elevate your coding practices?
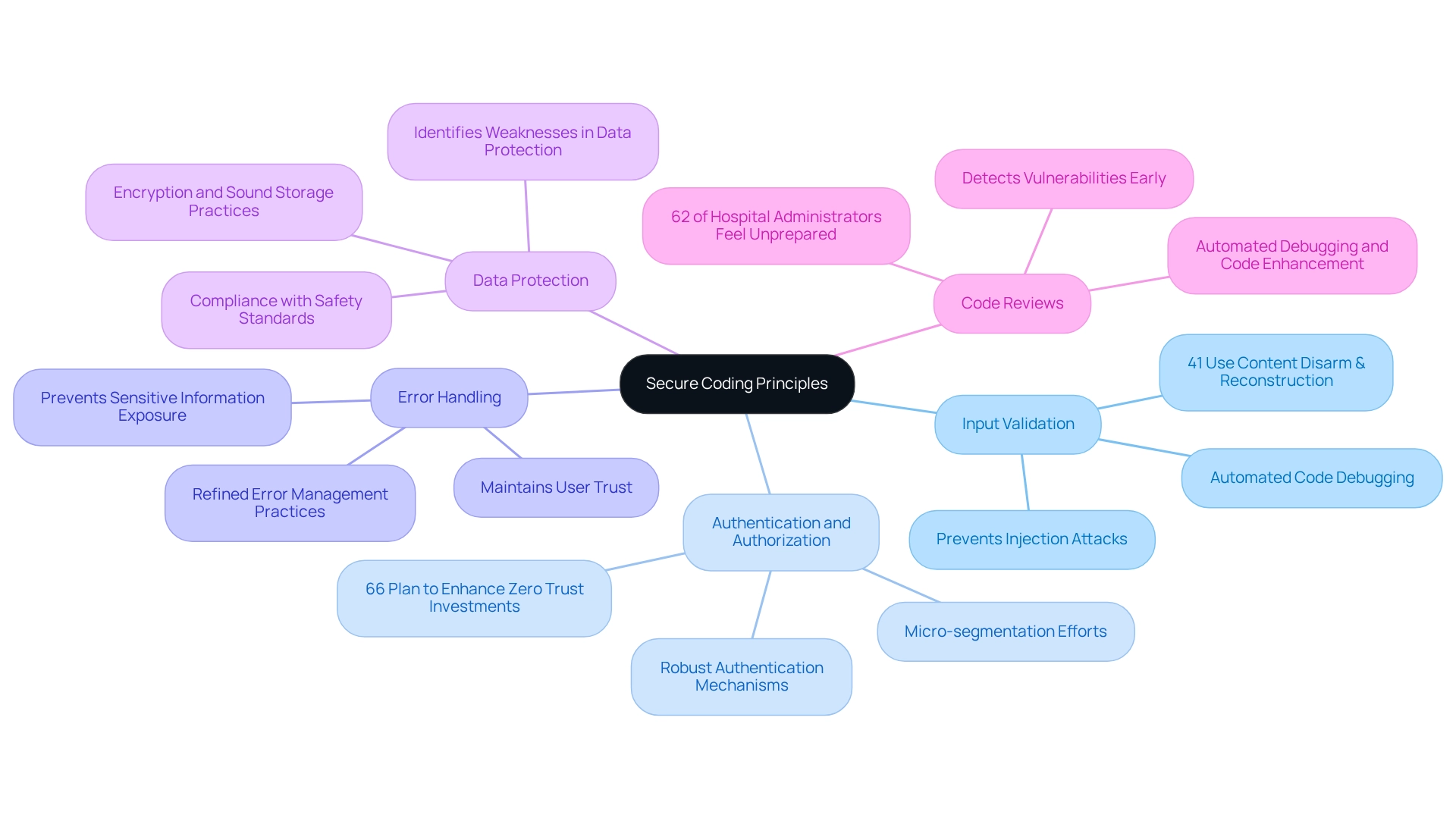
Understand Secure Coding Principles
Secure coding principles are essential methods designed to mitigate risks associated with software vulnerabilities. Developers often face significant challenges in this area, but Kodezi offers effective solutions to address them. By implementing these key principles, teams can enhance their coding practices and improve application integrity.
- Input Validation: Always validate user inputs to prevent injection attacks, such as SQL injection and cross-site scripting (XSS). Efficient input validation methods have shown a significant decrease in breach likelihood, with 41% of organizations employing content disarm and reconstruction techniques to protect users. Kodezi's automated code debugging helps identify and resolve input validation issues swiftly, ensuring adherence to best practices.
- Authentication and Authorization: Implement robust authentication mechanisms and ensure users have appropriate access levels. This is increasingly important, as 66% of organizations plan to enhance their Zero Trust investments, focusing on micro-segmentation efforts that bolster authentication protections. Kodezi supports these initiatives by enforcing coding standards that strengthen authentication security.
- Error Handling: Proper error handling is vital to prevent the exposure of sensitive information through error messages. This strategy not only protects data but also maintains user trust. Inadequate error handling can lead to serious security vulnerabilities, highlighting the need for careful implementation. Kodezi's features enable developers to refine error management practices, ensuring sensitive information remains secure.
- Data Protection: Safeguard sensitive data through encryption and sound storage practices. As cyber threats evolve, the necessity of protecting data becomes increasingly critical. Kodezi aids in identifying potential weaknesses in data protection strategies, ensuring compliance with the latest safety standards and enhancing overall data security.
- Code Reviews: Conduct regular code evaluations to detect potential vulnerabilities early in the development process. This proactive approach is crucial, especially since 62% of hospital administrators feel unprepared to handle cybersecurity breaches. Regular code reviews can alleviate this concern by identifying and mitigating risks before they escalate. Kodezi's automated debugging and code enhancement capabilities streamline the code review process, making it easier to uphold high safety standards.
By adhering to these principles and leveraging Kodezi's resources, development teams can utilize secure coding automation to significantly reduce the likelihood of breaches and enhance the overall integrity of their applications. The rise of remote work has further underscored the need for secure coding automation, as evidenced by case studies demonstrating the effectiveness of secure code training in protecting digital assets across decentralized teams. As Ganga Sumanth, a Security Engineer Developer, emphasizes, "If you're not investing in secure coding training now, you might be putting your organization at risk.
Leverage Automation for Enhanced Security
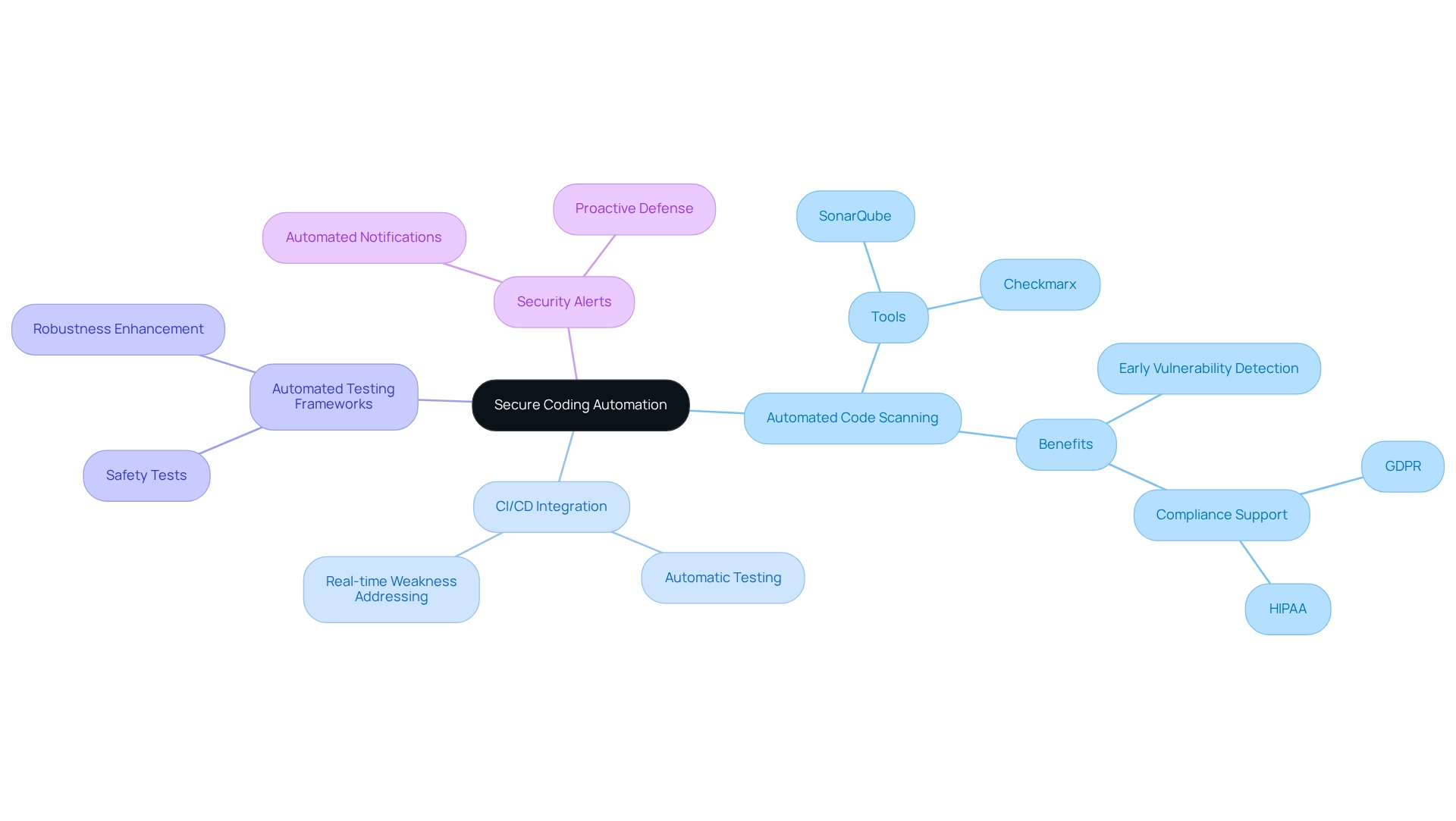
Automation plays a pivotal role in secure coding automation to bolster security within coding practices through several key strategies. Have you ever faced challenges in ensuring the security of your code? Automation can be a game-changer in addressing these issues.
- Automated Code Scanning is essential. By utilizing secure coding automation tools that automatically scan code for vulnerabilities throughout the development lifecycle, such as SonarQube and Checkmarx, developers can detect vulnerabilities early, preventing them from reaching production. This proactive strategy is crucial, particularly given that more than 20% of organizations reported encountering an incident within their pipelines in the past year. Furthermore, secure coding automation through static analysis tools supports compliance with regulatory standards like GDPR and HIPAA, minimizing risks associated with software development.
- In addition, the integration of Continuous Integration/Continuous Deployment (CI/CD) with secure coding automation ensures that every code change undergoes automatic testing for weaknesses. This not only simplifies the development process but also significantly reduces the chance of breaches, as weaknesses are addressed in real-time.
- Moreover, implementing automated testing frameworks that incorporate secure coding automation and safety tests guarantees that safety considerations are embedded within the testing process. This approach enhances the overall robustness of the software, making it more resilient against potential threats.
- Have you considered the importance of Security Alerts? Setting up automated notifications for any identified weaknesses allows teams to react quickly to emerging threats. This prompt feedback loop is vital for maintaining a proactive defense stance and reducing the likelihood of vulnerabilities going unnoticed.
By utilizing secure coding automation, development teams can effectively reduce risks and improve the safety of their applications, ensuring compliance with regulatory standards such as GDPR and HIPAA. The efficiency of automated code scanning solutions is further underscored by case studies that demonstrate how secure coding automation plays a role in upholding legal and safety requirements, ultimately mitigating risks related to software development. As highlighted by Techstrong Research, "The journey ahead is challenging, but with informed strategies and collaborative efforts, we can significantly minimize the weaknesses of the software we provide as part of our digital infrastructures." Furthermore, resources like Codacy exemplify versatile static analysis solutions that support major coding languages and standards, illustrating the practical application of secure coding automation in enhancing security.
Utilize Effective Tools for Secure Coding Automation
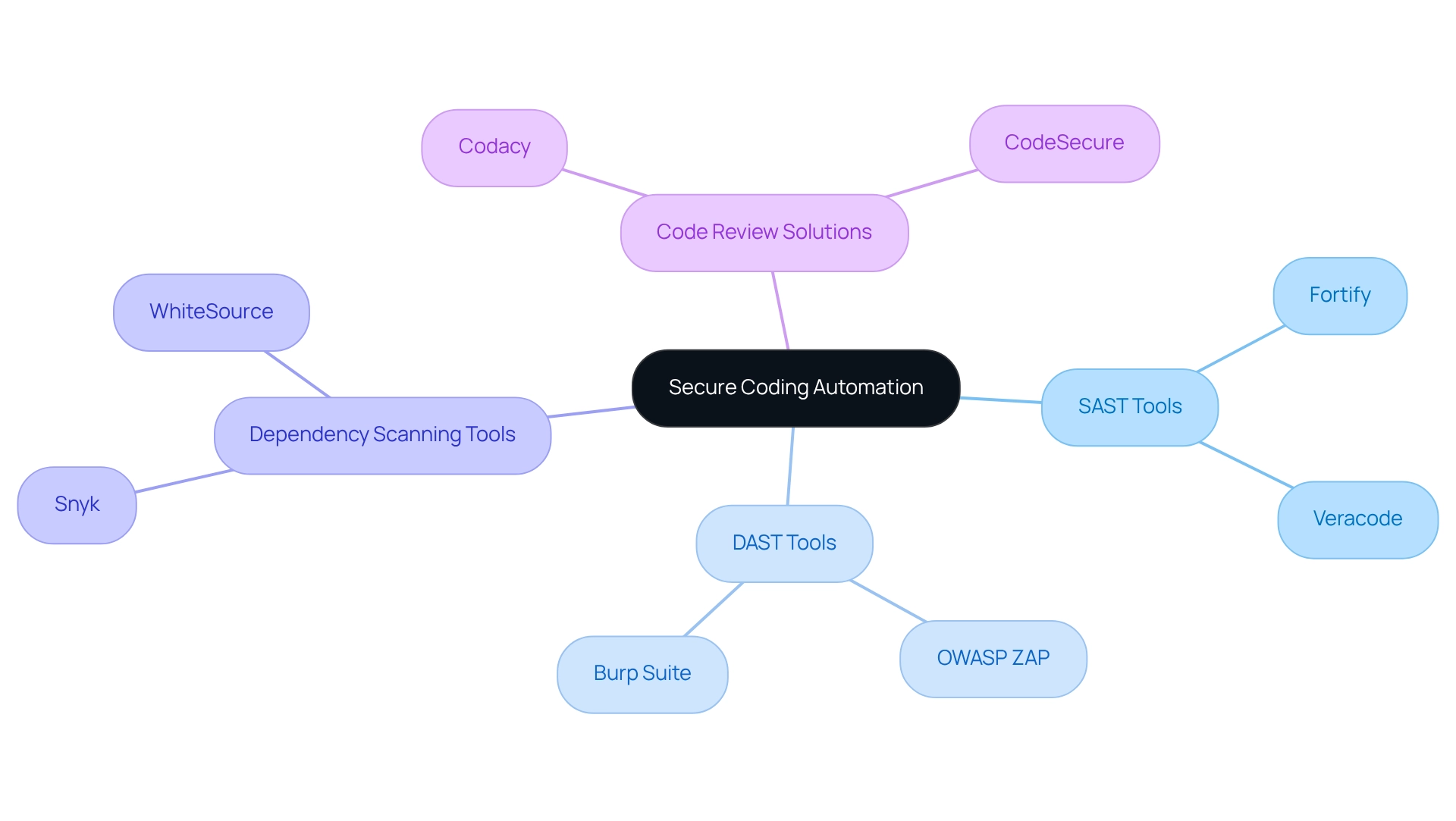
In the realm of software development, secure coding practices are paramount, yet many developers face significant challenges in maintaining these standards. To address these issues, secure coding automation tools can play a crucial role in enhancing security measures during the coding process.
Static Application Security Testing (SAST) Tools such as Fortify and Veracode are essential for analyzing source code for vulnerabilities without executing the program. This early detection capability is vital, as research indicates that weaknesses should be prioritized according to their severity and exploitability. By focusing on the most urgent concerns first, teams can effectively mitigate risks before they escalate.
Dynamic Application Security Testing (DAST) Tools like OWASP ZAP and Burp Suite examine active applications for weaknesses. These tools provide insights into potential vulnerabilities during execution, assisting organizations in recognizing and addressing risks that may not be apparent in static code reviews. Interestingly, only 10% of developers currently examine their code for weaknesses after utilizing AI coding tools, highlighting a significant opportunity for improvement in protective practices.
Dependency Scanning Tools such as Snyk and WhiteSource automatically scan for vulnerabilities in third-party libraries and dependencies. As organizations increasingly rely on external components, ensuring that all parts of the application remain secure and compliant with safety standards is becoming more critical.
Code Review Solutions like Codacy and CodeSecure can automate code assessments, ensuring that best practices for safety are consistently followed. These tools not only enhance the overall security posture but also streamline the evaluation process, allowing teams to focus on development rather than manual inspections.
By employing these tools, teams can greatly simplify the process of secure coding automation, facilitating adherence to high protection standards and reducing the likelihood of vulnerabilities in their applications. Are you ready to explore how these tools can transform your coding practices?
Implement Continuous Monitoring and Maintenance Strategies
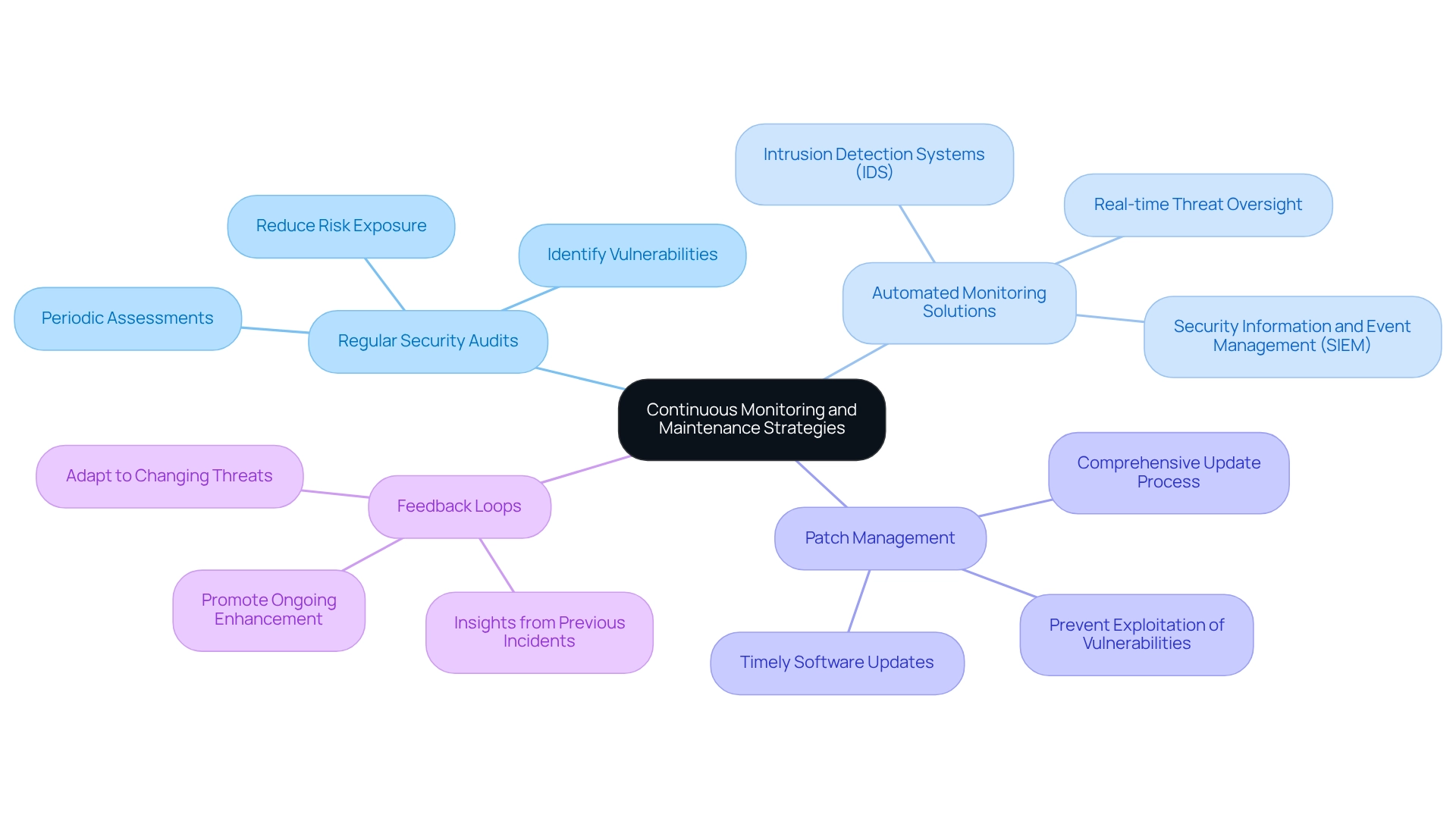
In the ever-evolving landscape of software development, implementing secure coding automation is a paramount challenge for developers to ensure long-term security in coding practices. How can teams effectively safeguard their applications against emerging threats? By implementing secure coding automation along with continuous monitoring and maintenance strategies, organizations can enhance their security posture significantly.
- Regular Security Audits: Conducting periodic security audits is essential for assessing the effectiveness of current security measures. These audits help identify vulnerabilities and areas for improvement, and studies indicate that organizations implementing secure coding automation and performing regular audits can significantly reduce their risk exposure. For instance, healthcare companies documented 145 data breaches in Q1 2023, underscoring the urgent necessity for proactive steps in ensuring protection.
- Automated Monitoring Solutions: Furthermore, utilizing resources that offer real-time oversight of applications for potential threats is crucial. Solutions like intrusion detection systems (IDS) and information and event management (SIEM) systems are vital for identifying anomalies and reacting to possible breaches promptly. The latest tools for secure coding automation are designed to adapt to new threats, ensuring that protective measures remain robust.
- Patch Management: In addition, establishing a comprehensive patch management process is vital for keeping all software components updated. Frequent updates reduce identified vulnerabilities, especially considering that 62% of organizations are postponing new application launches due to safety issues. A proactive approach to secure coding automation can prevent the exploitation of outdated software, reinforcing the need for timely updates.
- Feedback Loops: Similarly, establishing feedback loops allows developers to gain insights from previous incidents, promoting a culture of ongoing enhancement in coding methods. This strategy not only improves protection but also utilizes secure coding automation to enable teams to adjust effectively to changing threats.
As Altay Ataman, an industry analyst, observes, 'Best practices involve performing regular audits, staying informed about the latest trends and threats, implementing a secure development lifecycle, educating developers in safe coding methods, and utilizing secure coding automation tools for testing.' By implementing these strategies, teams can maintain a strong security posture and remain agile in the face of changing cybersecurity landscapes. Are you ready to explore the tools available on the Kodezi platform to enhance your coding practices?
Conclusion
In today's digital landscape, developers face significant challenges due to the prevalence of security breaches. Secure coding practices are essential to mitigate these risks. By adhering to fundamental principles such as input validation, strong authentication, and proper error handling, development teams can effectively reduce vulnerabilities. Tools like Kodezi play a vital role in this process by enabling quick identification and resolution of security issues, thereby enhancing code integrity.
Furthermore, automation is a crucial element of secure coding. The implementation of automated code scanning, continuous integration, and testing ensures that security is woven throughout the development lifecycle. This approach allows for early detection of vulnerabilities and prompt responses to potential threats.
In addition, utilizing effective tools such as Static and Dynamic Application Security Testing, dependency scanning, and security code review solutions is essential for managing risks associated with third-party components. As reliance on these components grows in application development, addressing their security becomes increasingly important.
Finally, continuous monitoring and maintenance strategies, including regular security audits and real-time monitoring, empower organizations to stay ahead of emerging threats. By fostering a culture of continuous improvement and learning from past incidents, development teams can adapt to the ever-evolving cybersecurity landscape.
In summary, prioritizing secure coding practices, leveraging automation, employing effective tools, and maintaining ongoing monitoring are critical steps for protecting digital assets. As security challenges escalate, organizations must take these measures to safeguard their applications and uphold user trust.
Frequently Asked Questions
What are secure coding principles?
Secure coding principles are essential methods aimed at mitigating risks associated with software vulnerabilities, helping developers enhance their coding practices and improve application integrity.
Why is input validation important in secure coding?
Input validation is crucial to prevent injection attacks, such as SQL injection and cross-site scripting (XSS). Proper validation methods significantly decrease the likelihood of breaches.
How can Kodezi assist with input validation?
Kodezi offers automated code debugging that helps identify and resolve input validation issues quickly, ensuring adherence to best practices.
What role does authentication and authorization play in secure coding?
Robust authentication mechanisms and appropriate user access levels are vital to security. Many organizations are focusing on enhancing their Zero Trust investments to strengthen authentication protections.
How does Kodezi support authentication and authorization efforts?
Kodezi enforces coding standards that bolster authentication security, helping organizations implement robust authentication mechanisms.
Why is proper error handling necessary in secure coding?
Proper error handling prevents the exposure of sensitive information through error messages, protecting data and maintaining user trust.
How can Kodezi improve error handling practices?
Kodezi provides features that enable developers to refine their error management practices, ensuring that sensitive information remains secure.
What measures should be taken to protect sensitive data?
Sensitive data should be safeguarded through encryption and sound storage practices, which are increasingly critical as cyber threats evolve.
How does Kodezi assist with data protection?
Kodezi helps identify potential weaknesses in data protection strategies, ensuring compliance with the latest safety standards and enhancing overall data security.
What is the significance of regular code reviews in secure coding?
Regular code evaluations help detect potential vulnerabilities early in the development process, allowing teams to identify and mitigate risks before they escalate.
How does Kodezi facilitate the code review process?
Kodezi's automated debugging and code enhancement capabilities streamline the code review process, making it easier to uphold high safety standards.
What impact has remote work had on secure coding practices?
The rise of remote work has highlighted the need for secure coding automation, with case studies showing the effectiveness of secure code training in protecting digital assets across decentralized teams.
What is the consequence of not investing in secure coding training?
Not investing in secure coding training can put organizations at risk, as emphasized by security professionals in the field.




