Introduction
An API Gateway is a crucial component in safeguarding the integrity of your APIs by filtering incoming requests and granting access only to authenticated users or systems. In today's digital landscape, where sensitive data is increasingly at risk, the security measures provided by an API Gateway are more important than ever. It acts as a centralized and secure conduit for service management, complete with monitoring, traffic control, and reliability.
However, not all API gateways are created equal. In the realm of microservices, access management strategies vary, with some services independently managing access while others rely on an API Gateway's centralized authority. The latter approach offers a streamlined and unified access point, simplifying developers' tasks by offloading the burden of infrastructure management to cloud providers.
But no solution is without trade-offs. Cloud-based API gateways may impose limits on request rates, potentially hindering scalability. Despite this, an API Gateway serves as a sophisticated mediator, ensuring that only authenticated entities are allowed entry.
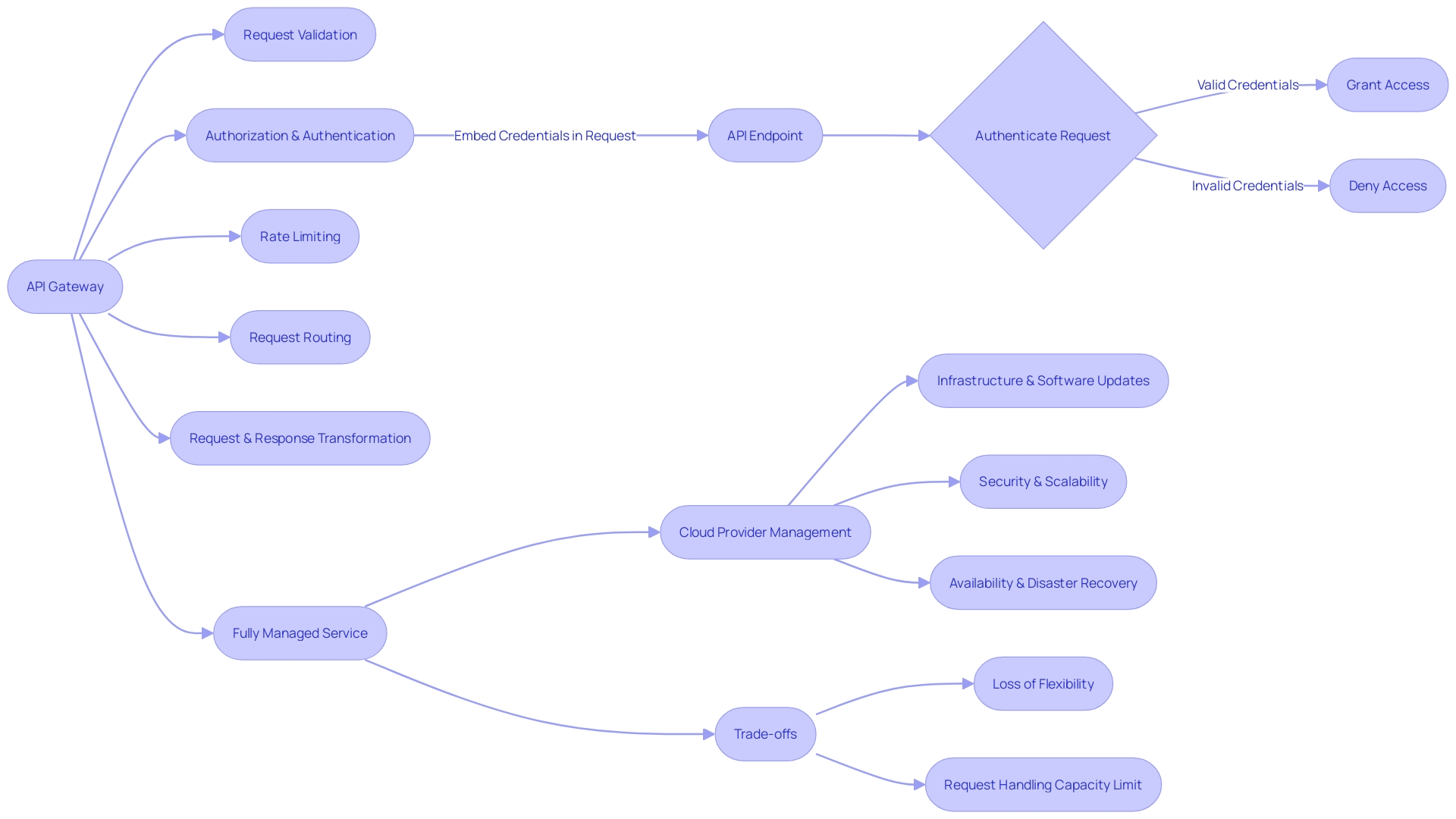
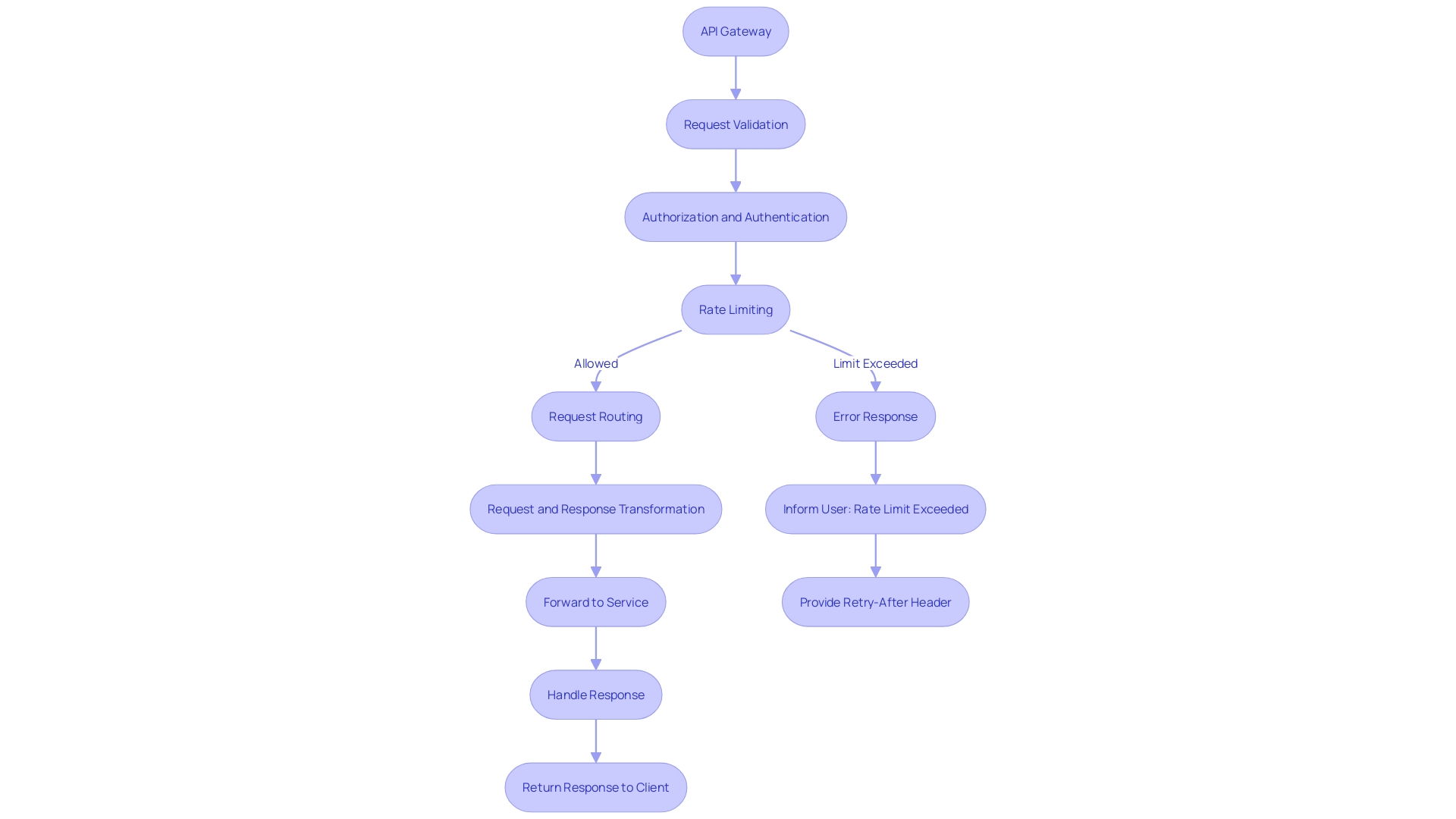
Its role involves request validation, authorization, rate limiting, and routing, all of which contribute to a secure and efficient API ecosystem.
In this article, we will explore the different types of API Gateway authorizers, such as Cognito User Pool Authorizer, Lambda Authorizer, and OAuth2 Authorizer. We will also discuss the process of creating an API Gateway Authorizer and best practices for using them. By implementing the right API Gateway Authorizer, you can enhance the security, efficiency, and reliability of your API ecosystem.
Why Use API Gateway Authorizers
An API Gateway is the linchpin in safeguarding the integrity of your APIs, acting as a robust barrier that meticulously filters incoming requests. Much like a vigilant gatekeeper, it grants access only to authenticated users or systems, ensuring each request is legitimate before allowing interaction with the API endpoints. This security measure is paramount in today's digital ecosystem, where sensitive data is increasingly at risk from unauthorized access.
In a world where information systems are ever-expanding, and staff turnover is on the rise, flexible yet secure management of both internal and external resources is not just desirable, it's imperative. Incorporating LDAP Single Sign-On (SSO) functionality, API Gateways have become indispensable in enterprises, offering a centralized and secure conduit for service management, complete with monitoring, traffic control, and heightened reliability.
The necessity of robust API gateways is underscored by alarming statistics: within the last year, 78% of cybersecurity teams have encountered an API-related security incident. Despite 72% of organizations maintaining a comprehensive API inventory, only 40% possess insight into APIs that handle sensitive data. This reality has propelled API security to a higher priority for 81% of respondents compared to a year ago.
In the realm of microservices, access management strategies vary, with some services independently managing access—each acting as its own bouncer—while others rely on an API Gateway's centralized authority. The latter approach offers a streamlined, unified access point, simplifying developers' tasks by offloading the burden of infrastructure management to cloud providers. However, it's crucial to recognize that no solution is without trade-offs; for example, cloud-based API gateways often impose limits on request rates, which could hinder scalability.
Ultimately, an API Gateway functions as a sophisticated mediator, akin to a restaurant's maître d', ensuring that only guests with a reservation—authenticated entities—are allowed entry. It's a complex role involving request validation, authorization, rate limiting, and routing, all of which contribute to a secure and efficient API ecosystem.
Types of API Gateway Authorizers
Selecting the right API Gateway Authorizer is pivotal for the security and efficiency of your enterprise's information systems. API gateways act as gatekeepers, akin to air traffic controllers for network requests, ensuring only authorized requests access your backend services. They are crucial in managing the increasing demands of modern enterprises and frequent personnel changes, offering flexibility and security for internal and external resource management.
API gateways not only simplify developers' tasks by providing a unified access point for easier service management but also enhance the system's reliability with features like security protocols, monitoring, and traffic control. In the microservices architecture, some opt for individual service-level access management, likened to having a unique bouncer for each club room. In contrast, others prefer a centralized approach, using the API Gateway as the sole authority for access control.
A fully managed API gateway service relieves developers from the burdens of infrastructure maintenance, allowing them to focus on creating and improving services. However, this convenience comes at the cost of reduced flexibility, as cloud providers typically impose limits on the number of requests per second (RPS) that can be handled.
Recent developments in Kubernetes, such as the Gateway API, showcase the collaborative efforts of the community to enhance the accessibility and management of these services without necessitating an upgrade to the latest Kubernetes version. The Gateway API, proposed 4 years ago and developed by a robust community, demonstrates the ongoing evolution and importance of API gateways.
In light of these advancements, it's clear that API gateways are more than a trend—they're an indispensable component of modern IT infrastructure. According to a 2021 survey by Vanson Bourne, 93% of organizations recognize APIs as essential to their operations, and 86% agree that without APIs, organizational silos would prevail. These statistics underscore the critical role of API gateways in fostering integration, visibility of data assets, and overall organizational efficiency.
Cognito User Pool Authorizer
Integrating Amazon Cognito with applications starts by setting up an identity provider through services like Auth0. You initiate this process by creating a new application within the Auth0 dashboard, selecting the appropriate application type—such as a Single Page Application for our scenario. Critical information like the Application Domain and Client ID is generated, which is essential for future steps in authentication.
Once the application is established, you can leverage the Cognito User Pool Authorizer to authenticate users. This system verifies user credentials and issues access tokens, empowering authenticated users to access secured endpoints. It's a seamless way to manage user access, ensuring that only authorized individuals can interact with your application's protected resources.
The practical application of this setup is evident in scenarios like using Amazon Rekognition Custom Labels to train machine learning models for specific tasks, such as animal breed identification from images. This process involves developing a custom ML model, a complex task that can take months and require a vast dataset of labeled images. Access to such sensitive operations would necessitate robust user authentication, for which a Cognito User Pool Authorizer, configured with an Auth0 application, is a well-suited solution.
For developers looking to implement this, full code examples are available, along with templates for quickly establishing a Cognito user pool complete with groups and app clients. Once deployed, you're equipped to create users, assign them to groups, and facilitate secure access to your application's functionalities. This integrated approach to user authentication and authorization is a cornerstone of building secure, efficient applications that cater to specific business needs.
Lambda Authorizer
Leveraging a Lambda Authorizer is a strategic approach to securing serverless applications. It empowers developers to define custom authentication and authorization procedures tailored to their application's unique requirements. For instance, in a multi tenant file management system, distinct roles such as a CEO, who needs access to all files within their organization, and a user, who should only see their own files, demand nuanced access controls.
The Lambda Authorizer allows for the creation of sophisticated authorization logic that goes beyond basic permission sets. It can integrate with various identity providers and enforce permissions dynamically, ensuring that each user interacts with the system within their designated boundaries. This method effectively addresses the challenges of serverless architectures by decoupling authorization from business logic, thereby enhancing security and maintainability.
It's a solution that not only protects against unauthorized access but also scales seamlessly with the application, demonstrating its value in building robust, enterprise-level serverless applications.
OAuth2 Authorizer
As software applications become increasingly intertwined, APIs serve as vital conduits for data exchange, with authentication and authorization at the forefront of securing these essential pathways. The OAuth2 Authorizer epitomizes this security measure by facilitating the integration of your API with an OAuth2 provider. It meticulously validates OAuth2 tokens, ensuring that only authorized entities can gain access to protected resources according to the permissions assigned within the token.
The essence of authentication lies in its ability to verify the identity of a user or system, a principle that forms the bedrock of a Kubernetes API gateway's security. Traditional methods of authentication are now facing challenges in safeguarding against the ever-evolving threats in sophisticated environments like Kubernetes. Against this backdrop, OAuth2 emerges as a robust solution, providing an authentication framework that is both secure and flexible, crucial in a landscape where 78% of cybersecurity teams report API-related security incidents within a year.
In the realm of enterprise information systems, the integration of API gateways with LDAP Single Sign-On (SSO) has emerged as a pivotal strategy. This combination not only enhances security and reliability by mitigating risks like password leakage but also streamlines system management. It simplifies the developer experience by providing a unified entry point to internal and external services, complete with enhanced functions like monitoring and traffic control.
These features collectively fortify the system's integrity and reduce operational costs.
Reflecting on the words of industry experts, authentication and authorization are not mere technical terms but are the sentinels guarding the sanctity of software systems. Authentication asks, "Who are you?" and requires users to prove their identity through various means, such as credentials or biometric data, while authorization determines the scope of access granted to the authenticated entity.
It is imperative for organizations to adopt comprehensive API security measures, as inadequate security can leave APIs vulnerable to sophisticated attacks that target their inherent weaknesses. Such breaches can have far-reaching consequences, affecting businesses and consumers alike. Therefore, as reliance on APIs grows, so does the prioritization of their security, with 81% of respondents recognizing it as a more pressing concern than just 12 months prior.
In conclusion, the OAuth2 Authorizer represents a key tool in the arsenal for enhancing API security, addressing the need for both robust authentication and precise authorization to protect the digital assets of enterprises and individuals. By integrating such advanced mechanisms, organizations can better manage access to their services, optimize user experience, and maintain the highest levels of security and efficiency.
Creating an API Gateway Authorizer
Implementing an API Gateway Authorizer is central to managing access in a microservices architecture. By serving as the security checkpoint, the API Gateway ensures that only authorized users can interact with your services. Here's how to harness its power:
-
Understand the Significance: Recognize that an API Gateway acts as a unified entry point, crucial for secure and efficient resource management in modern enterprise systems. It's like a club with strict bouncers at each door, checking IDs to protect your services from unauthorized access.
-
Review Authentication: Authentication is a core function of an API Gateway, verifying user identities to safeguard your application from unauthorized entry. Traditional authentication might fall short in complex environments, so ensure your Gateway's authentication mechanisms are robust and up-to-date.
-
Fully Managed Service: Leverage the benefits of a fully managed API Gateway service provided by cloud vendors. This means all maintenance, from infrastructure to security, is handled by the provider, freeing developers to focus on building services rather than managing them.
-
Rate Limiting and Request Routing: Incorporate rate limiting to control the traffic flow and prevent system overloads. Request routing is equally important to direct users to the correct services efficiently.
-
Real-World Application: Reflect on the broader community's experiences. For instance, Kubernetes Gateway API doesn't require you to upgrade to the latest version of Kubernetes to benefit from updates, providing flexibility and ease of maintenance.
-
Bringing it Together: Integrate all these elements to construct a secure, efficient, and manageable API Gateway that stands as a testament to the balance between ease of use for developers and stringent security protocols.
By following these steps, you not only enhance the security and reliability of your enterprise but also improve the user experience and system management, ultimately driving down operational costs.
Step 1: Configure the Authorizer
Effective API documentation is akin to a well-designed user manual; it guides developers and users through the intricacies of API integration and usage with clarity and precision. Just as a user manual details the operation of a laptop, API documentation must articulate the structure and behavior of the API, ensuring that the intended audience can utilize it effectively.
To illustrate the importance of this documentation, consider the user manual that accompanies a new laptop, which explains how to navigate its functions. Similarly, API documentation serves as a guide for developers to understand and implement the API successfully. It's a critical tool that functions as a definitive reference for both internal teams and external consumers.
Authorization, a key component of API usage, establishes who has permission to do what. For instance, if you're invited to collaborate on a document, you may be granted 'comment' access without the ability to modify the original content. This principle of defining specific permissions is crucial for API security and functionality.
As described in a recent announcement by Databricks, jobs can now run as a service principal, which ensures stable permissions regardless of changes in user roles within an organization.
In the world of APIs, the equivalent of setting permissions is configuring the authorizer settings. This includes determining the type of authorizer that will dictate who can access the API, the identity source which serves as the credential repository, and authorization caching to optimize performance.
When considering the structure of a JWT (JSON Web Token), think of it like a tamper-evident seal on medication, signaling any unauthorized access attempts and carrying an expiration date. JWTs have become a standard for secure authentication and authorization on the web, representing a step forward in ensuring secure and restricted API access.
Remember, the goal is not merely to authenticate users but to authorize them appropriately, granting precise access levels to API functions. For example, policy creation forms in IAM systems may include 'Effect' statements that determine whether access is allowed or denied, reinforcing the notion that meticulous authorization is as essential as authentication in API security.
In conclusion, the deliberate crafting of API documentation and the meticulous configuration of authorization settings are indispensable. They ensure that APIs are not only accessible but also secure, reliable, and used appropriately, much like a carefully authored user manual enables the optimal use of a new laptop.
Step 2: Implement the Authorization Logic
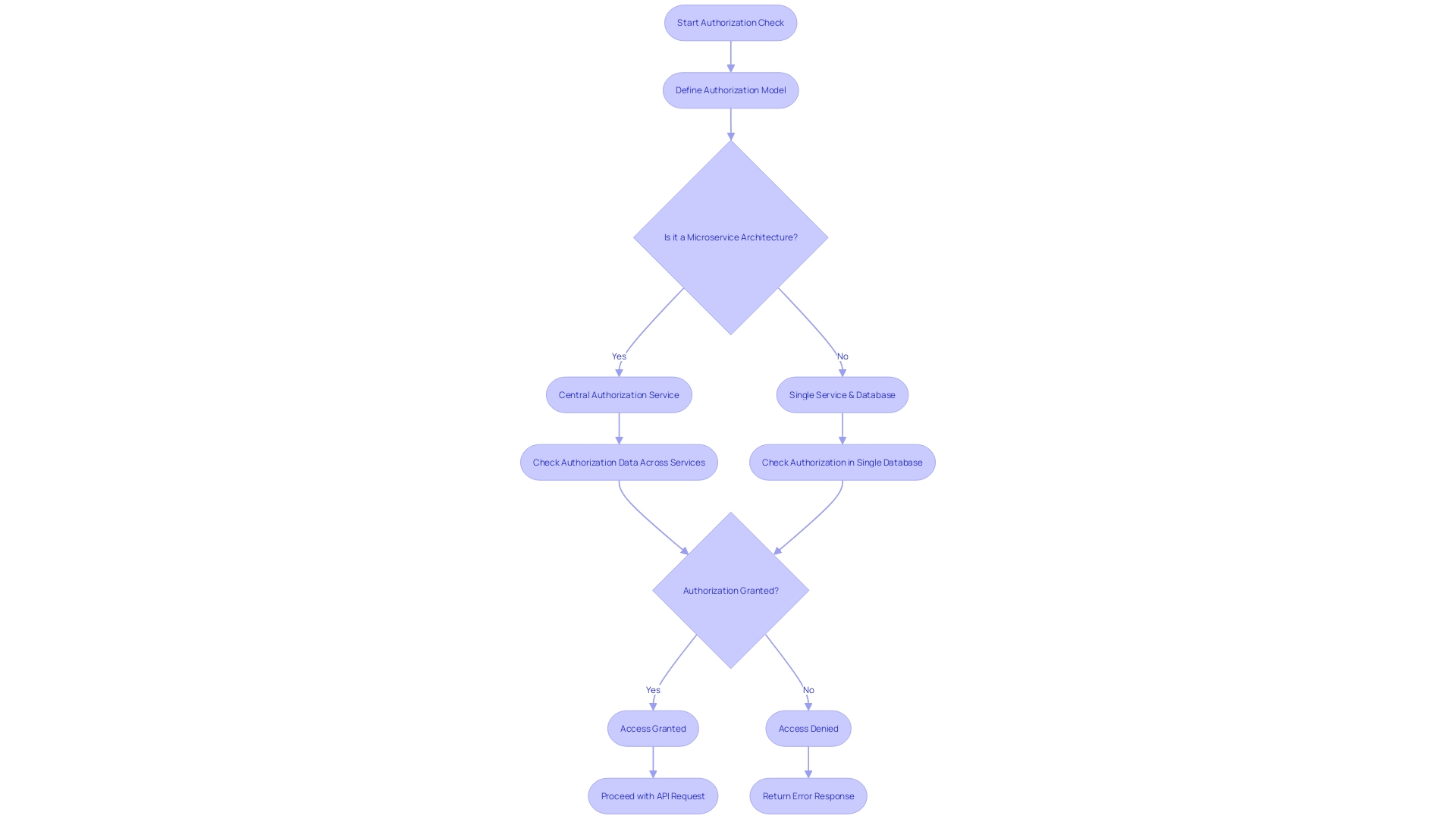
When structuring the authorization logic for your API, it's crucial to recognize that it might necessitate interactions with various services and databases, especially in a microservices architecture where data is distributed. This complexity is exemplified by the need for a central authorization service, as highlighted in the case of Reddit's advertising platform. They underscored the importance of low-latency checks to maintain a smooth user experience, emphasizing that even a brief outage could be detrimental to their operations.
Also, consider Ad Tech's intricate systems, which demand not only robust security but also the agility to meet diverse user expectations and account structures.
It's advisable to begin by categorizing your API documentation into clear sections that address distinct facets of the API. Utilize subheadings and concise descriptions to direct users through the necessary information, and employ lists for clarity and brevity. This organizational strategy ensures that users can effortlessly navigate the documentation and access the information pertinent to their needs without wading through dense text.
A solid documentation foundation comprises five essential elements, starting with an overview that quickly informs new users about the API's offerings. Prospective users should be able to understand how to engage with the API and benefit from its features promptly. Addressing users as distinct cohorts or personas can facilitate a personalized onboarding experience and help them realize the API's advantages swiftly.
Remember, the data required for authorization decisions often intersects with application data. This overlap can expand over time, making it imperative to consider both application-specific and authorization-centric data. Questions such as what tooling is supported for defining authorization patterns and what documentation is provided for this purpose are critical for understanding how to implement authorization logic effectively.
Furthermore, as engineers explore authorization as a service—a relatively new software category—guidance on key features, testing approaches, and documentation becomes invaluable. Learning from the experiences of companies like ProductBoard and Oyster HR, who have tested these products, can provide insights into the practical aspects of implementing authorization systems.
Step 3: Configure API Gateway Integration
To effectively manage your API requests and ensure proper access control, configuring your API Gateway to utilize an authorizer is crucial. As enterprises face growing demands and frequent personnel changes, the flexibility and security provided by API gateways become indispensable. With LDAP Single Sign-On (SSO) support, API gateways offer a unified access point that simplifies the development process by enabling easier access and management of services.
This centralization is not merely about convenience but also about bolstering security and reliability while diminishing security risks such as password leaks.
Furthermore, a fully managed API gateway service relieves developers from the burdens of infrastructure and security management. It's a service where maintenance, updates, scalability, and disaster recovery are all handled by the cloud provider. This managed service offers multiple operational advantages like request validation, authentication, rate limiting, and routing, enhancing the developer's focus on service development rather than on managing these aspects.
API gateways also play a pivotal role in authorizing access, which is distinct from authentication. Authorization ensures that only permitted actions can be performed by a user within a system, akin to having 'comment' only access in a shared document. This differentiation is vital for maintaining secure and controlled access to APIs.
In a microservice architecture, an API gateway acts as a central authority for access management, comparable to a club with various rooms, each guarded by its own bouncer. This central authority checks credentials and authorizes entry, ensuring that information is shared securely within the architecture.
Integrating an authorizer with your API Gateway is analogous to using a secret code language for secured conversations among team members. It's an essential step in safeguarding your APIs and maintaining the secure and efficient operation of your enterprise's services. By leveraging an API Gateway's capabilities, you can enhance user experience and operational efficiency, while simultaneously reducing management complexities and operational costs.
Understanding the API Gateway Authorizer Workflow
Exploring the API Gateway Authorizer requires a step-by-step breakdown to appreciate its role in modern enterprise systems. As a pivotal element in facilitating secure and flexible resource management, an API Gateway Authorizer operates as a centralized authority that oversees user authentication and authorization. By implementing LDAP Single Sign-On (SSO), it provides a robust solution for enterprises managing frequent internal personnel changes and the growing demand for secure access to both internal and external services.
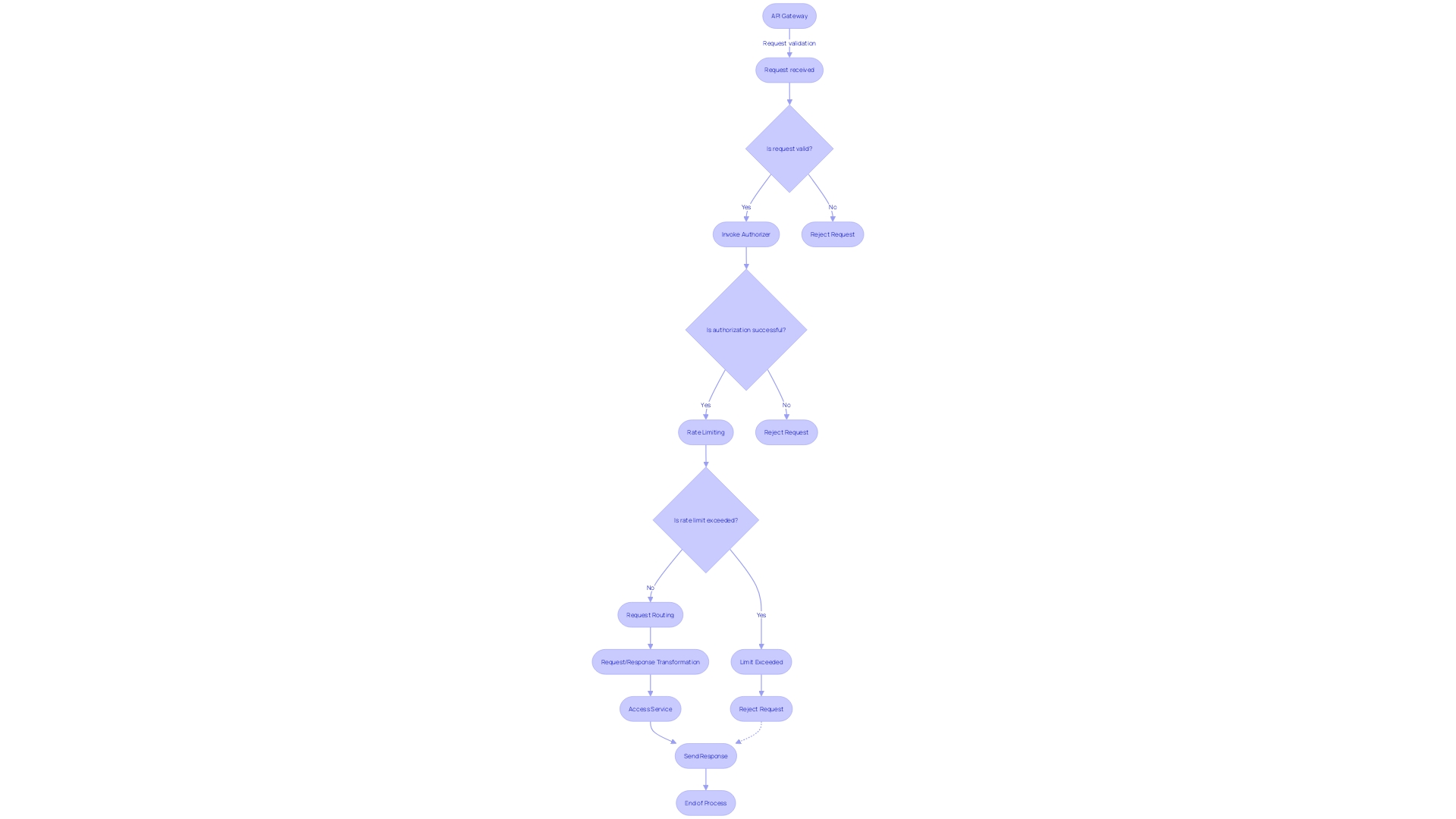
Delving into the mechanics, the API Gateway Authorizer performs a series of critical functions to ensure secure and efficient service management. These include:
- Request Validation: Each incoming request is meticulously checked to ensure it conforms to predefined standards, much like a bouncer checking IDs before allowing entry.
- Authentication and Authorization: This two-stage process first confirms user identity and then grants permissions, akin to an owner in a collaboration document allowing 'comment' access but not the ability to edit.
- Rate Limiting: To maintain service quality and prevent overuse, the gateway imposes limits on the number of requests per second, much like a club controlling the flow of guests to prevent overcrowding.
- Request Routing: Directing traffic to the appropriate services, the API Gateway functions similarly to a maître d' in a restaurant, guiding guests to their tables based on their preferences and reservations.
- Request and Response Transformation: It adapts incoming and outgoing data to ensure compatibility between different service formats, streamlining communication.
In the context of cloud computing, an API Gateway is often a fully managed service, which means all aspects from maintenance to disaster recovery are handled by the cloud provider. This lifts the burden from developers, allowing them to focus on creating and developing services rather than managing the infrastructure.
However, such convenience comes at the cost of reduced flexibility, as gateways have inherent limits on request volumes they can handle. Nonetheless, the benefits of an API Gateway in enterprise environments, such as enhanced security, reliability, and user experience, can outweigh these limitations, resulting in a more streamlined and cost-effective management of services.
Client Sends Request to API Gateway
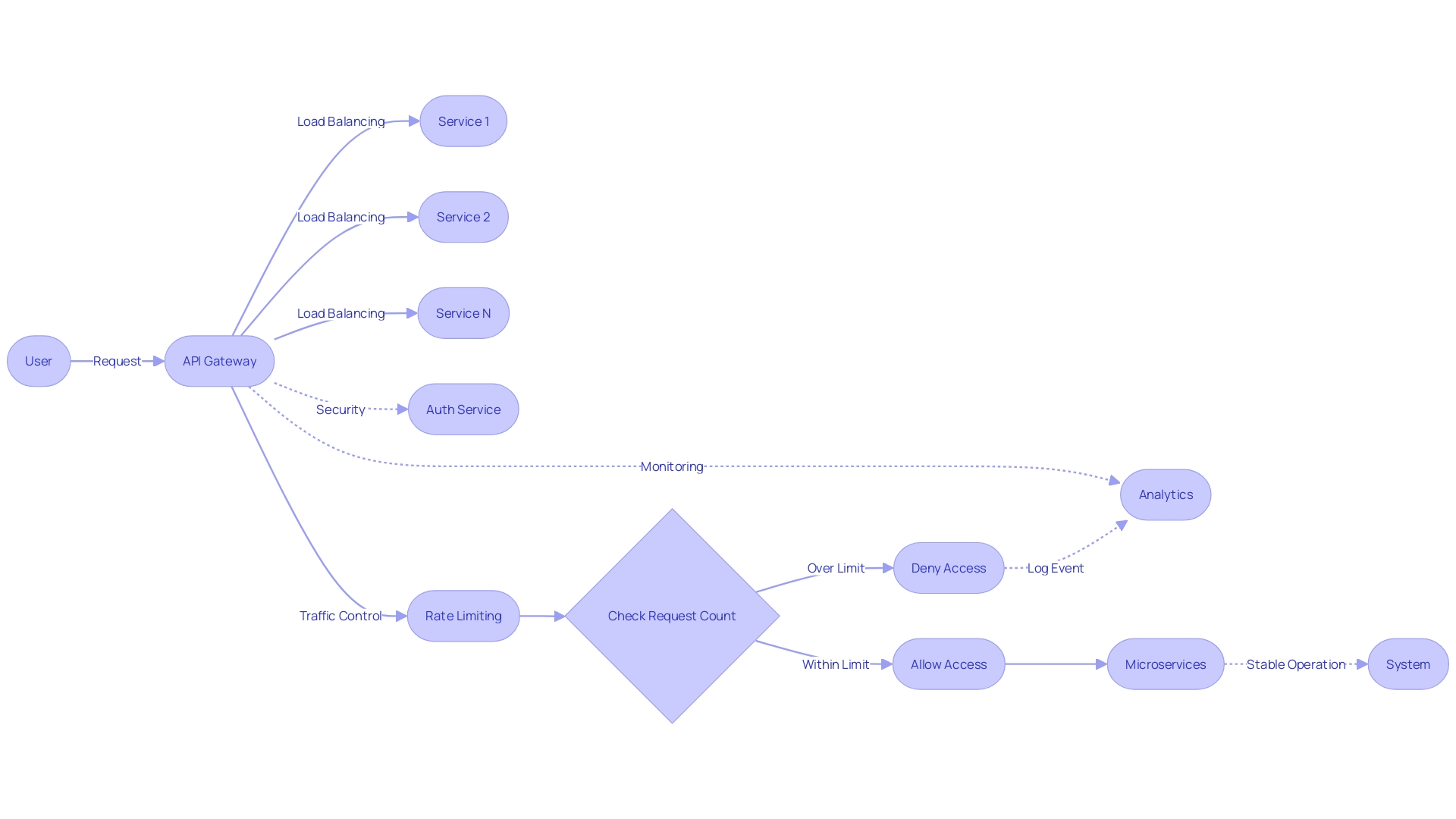
When a client initiates a request, it's routed through an API Gateway, marking the start of a sophisticated workflow. An API Gateway serves as the central hub for all requests, offering a single point of entry for various services. Its role is akin to a conductor, orchestrating the flow of information between clients and the applications they seek to interact with.
This orchestration is critical in modern enterprise ecosystems, where the seamless integration of services is a paramount concern.
API Gateways are not just about routing traffic; they are the linchpin in a system's security and efficiency. By implementing protocols like LDAP for Single Sign-On, they ensure that access is both flexible and secure—a necessity given the high turnover of personnel and the growing need for dynamic resource management. These gateways bring a multitude of advantages, such as improved security, easier access for developers, and the ability to manage traffic, monitor services, and maintain the reliability of the system.
For example, when constructing an API client for a service like Netflix, developers might follow a naming convention like ApiHarbor.RapidApi.Author.API Name to maintain clarity and organization. This systematic approach minimizes coding effort and maximizes efficiency, aligning perfectly with the 'less code, more efficiency' principle. From the initial setup to the implementation of an actual client, such as NetflixApiClient.cs, every step is geared towards creating a streamlined process that connects to the Netflix API with ease.
The importance of API Gateways is further highlighted by the ongoing developments in the industry. Notably, the Gateway API project for Kubernetes has shown that advancements in API management are continuously being made. With such projects, users don't need to upgrade their entire system to benefit from the latest API features—demonstrating the agility and forward-thinking that is inherent in modern API solutions.
Statistics underscore the critical nature of APIs in today's digital landscape. According to Vanson Bourne's 2021 research, 'The State of APIs, Integration, and Microservices,' a staggering 93% of organizations consider APIs crucial to their operations, with 86% acknowledging that without APIs, operational silos would be a significant issue. Furthermore, 97% believe that APIs and microservices are complementary, suggesting a trend towards integrated solutions that can enhance customer satisfaction, increase productivity, and save valuable time.
In essence, the API Gateway is the entryway to a world of interconnected services, defining the way modern enterprises operate, innovate, and deliver value to their customers.
API Gateway Invokes the Authorizer
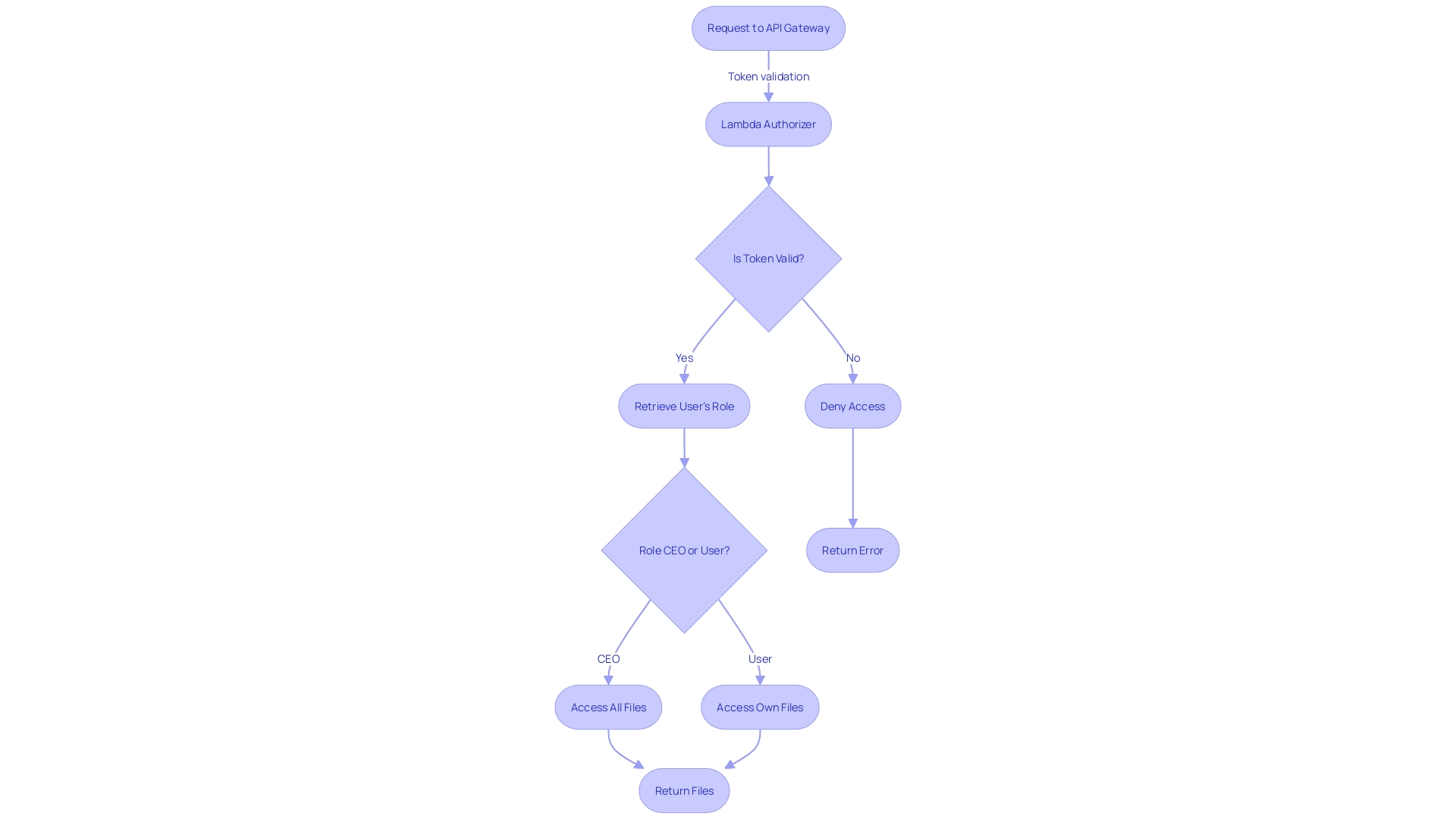
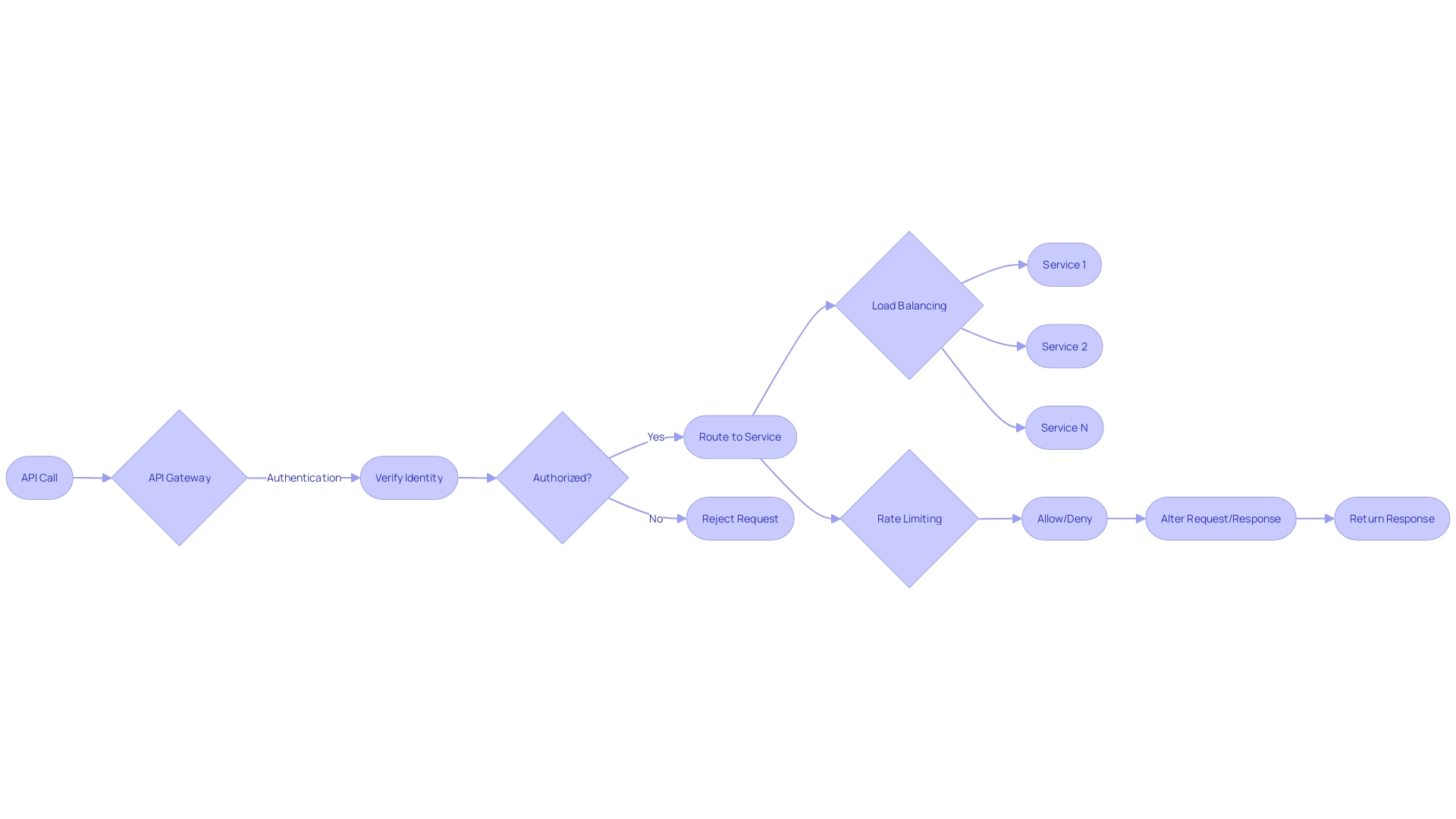
When a request arrives at an API gateway, it acts as a central authority, akin to the maitre d' of an upscale restaurant, ensuring that every interaction is secure and meets the necessary protocols. It validates the request, much like checking a guest's reservation, and then invokes the appropriate authorizer, which can be compared to a bouncer ensuring only authorized patrons enter different rooms in a club. This central management of access, provided by a gateway, is essential in microservices architecture, where services may be developed in various languages or tech stacks, each acting as its gatekeeper.
The gateway simplifies the complexity of authentication and authorization across the multitude of services, offering a unified point of control for these operations. It's not just about controlling access; the API gateway also handles rate limiting, routing, and request/response transformation, enhancing the scalability and reliability of the system. With the cloud provider managing the underlying infrastructure, developers can focus on building services rather than on the maintenance tasks, although this abstraction might limit the flexibility in handling requests per second (RPS).
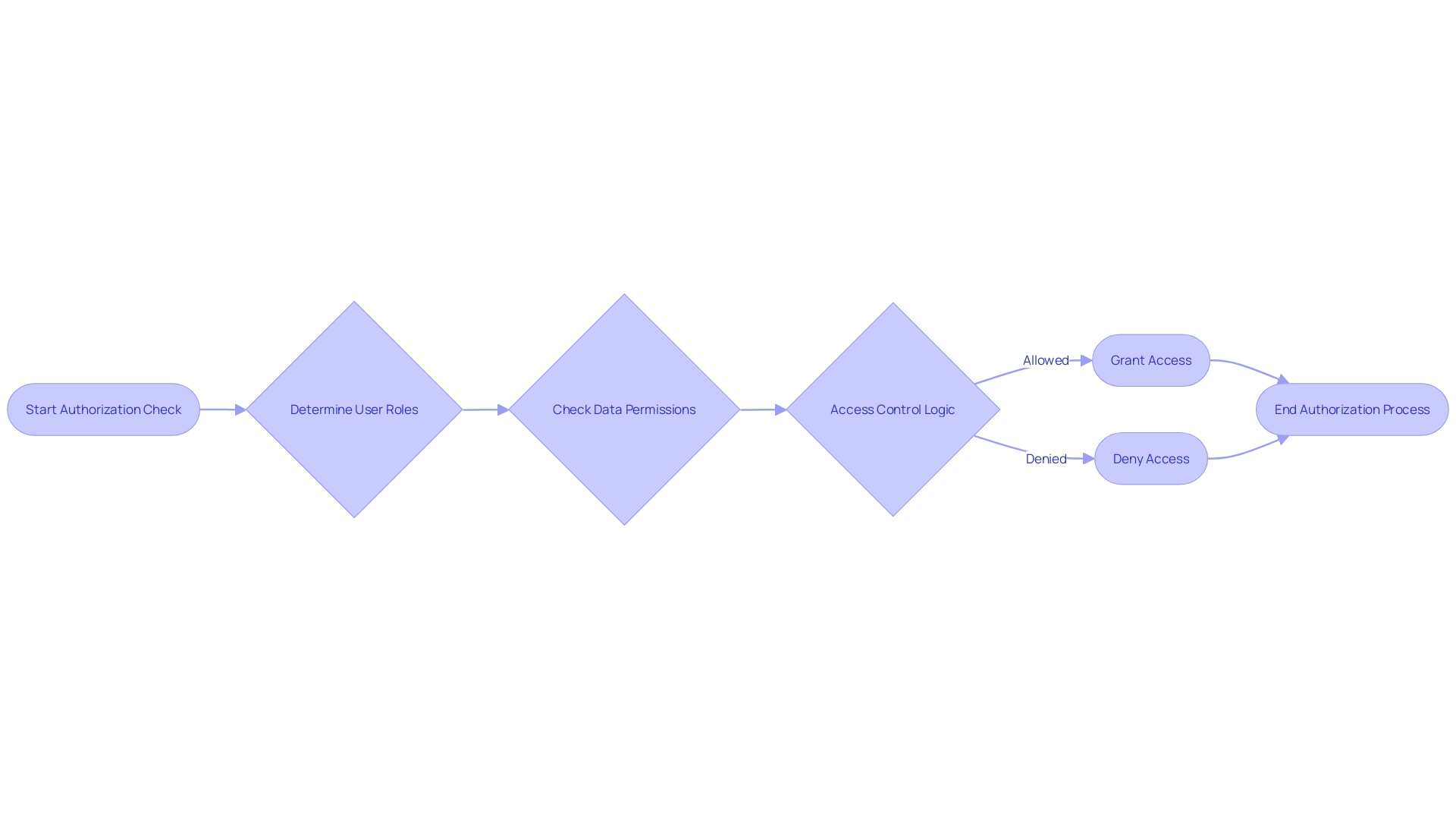
Authorizer Authenticates and Authorizes the Request
When securing software systems, clarity in roles is pivotal. The authorizer's job is to verify not just the identity but also the permissions of any entity requesting access to resources. This is a sophisticated dance between authentication—confirming an entity's identity—and authorization—ensuring the entity has the right to perform specific actions.
In the landscape of service-to-service communication, imagine two applications needing to converse. They must be authenticated, perhaps through credentials that are meticulously verified, and then authorized, with careful checks on what actions they're allowed to perform. These aren't just binary operations; they're nuanced processes that demand precision and context.
For example, sensitive operations might require an additional layer of verification, much like heightened security checks for significant financial transactions.
Let's take a practical example: setting up a DynamoDB table. The table, named 'notesTable,' uses 'userId' as the partition key and 'noteId' as the sort key. The partition key segregates and organizes data, while the sort key arranges it within those partitions.
Recent developments in security practices reflect the sophistication needed for robust authentication and authorization. PyPI's inaugural external security audit, backed by the Open Technology Fund, is a testament to this evolution. Similarly, Databricks now allows jobs to run under a service principal's identity, not just the job owner's, enhancing security and operational continuity.
What does this mean for API documentation? It necessitates a structured approach. Documentation should be broken down into digestible sections, with subheadings and bulleted points guiding users through the authentication and authorization processes.
Clear, concise communication is vital, starting with the basics and expanding to more complex concepts.
A comprehensive API documentation should address the story of the API, the potential it offers, and how users can leverage that potential. As users first encounter your API, they're asking, 'What does it offer me?' Your documentation should answer this promptly, aiding them in onboarding and experiencing the benefits.
In summary, authentication and authorization are the gatekeepers of security, as they discern who you are and what you can do. Properly implemented, they underpin the safety of our digital interactions. As we continue to witness global internet traffic surging by 25%, the importance of robust security practices becomes ever more apparent, and our documentation must rise to the challenge.
API Gateway Responds with the Result
API Gateways serve as the linchpin in modern enterprise information systems, particularly in light of increasing demands and frequent personnel changes which call for more secure and flexible management of resources. They act as a secure, encrypted communication channel—akin to a secret code language—between services and users.
In a microservices architecture, there are different approaches to managing access, such as each service acting as its own gatekeeper, or a centralized authority like an API Gateway. The latter not only streamlines access across services but also incorporates essential features such as security, monitoring, and traffic control. This boosts the reliability and security of enterprise systems, mitigating risks like password leaks and enhancing the user experience.
A real-world example of the API Gateway's capability is its support for LDAP Single Sign-On (SSO), which simplifies system management and reduces operational costs. Moreover, the adoption of fully managed API Gateway services frees developers from the intricacies of underlying infrastructure and maintenance, allowing them to focus more on service development.
However, with every abstraction comes trade-offs, such as potential constraints on request handling capacity. Therefore, it's crucial to implement precise rate limits and robust authorization mechanisms to minimize attack surfaces and enhance system security. As API gateways evolve, they continue to play a critical role in connecting and managing multiple services, ensuring that upon authorization, they seamlessly forward requests to the appropriate backend service.
Request Parameter-Based API Gateway Authorizers
To ensure secure access to API endpoints, a technique known as Request Parameter-Based API Gateway Authorizers can be employed. This method involves embedding authorization credentials within the request parameters themselves. It's particularly effective in scenarios where you aim to include authorization details directly within the request for streamlined processing.
By strategically extracting these parameters, the API gateway can authenticate requests before granting access to the backend services, safeguarding them against unauthorized use.
In a practical example, consider a DynamoDB table named notesTable with primary keys UserId (partition key) and note Id (sort key). When a request is made to this database, the API gateway can check the provided request parameters against these keys to authenticate the user and validate the access to the requested note.
Furthermore, API gateways play a critical role in modern cloud environments. They act as the maitre d' of a digital ecosystem, guiding requests to their proper destinations, managing authentication, and ensuring overall security. This is of utmost importance in Kubernetes, where the API gateway stands as the primary defense against bad actors.
By using a fully managed API gateway service, developers can focus on building functionalities without the added burden of managing the underlying infrastructure, security, and scalability concerns. However, it's essential to remember that such convenience may come with certain trade-offs, such as limitations on request handling capacity.
Token-Based API Gateway Authorizers
Token-Based API Gateway Authorizers are essential for ensuring secure and flexible management of a company's internal and external resources. As businesses face growing demands and frequent personnel changes, these authorizers provide robust authentication by verifying user identities through tokens, such as JSON Web Tokens (JWT) and OAuth2 tokens. This verification process is crucial in a microservices environment where each service could act as its own gatekeeper, much like individual rooms in a club, each with its own set of requirements for entry.
An API gateway, likened to a secret code language for secure communication, is not just about access; it's about managing services with enhanced security and reliability. It stands as the unified entry point, simplifying access for developers and offering functions like monitoring and traffic control. The gateway plays a pivotal role in system reliability and security, and its importance is underscored by the alarming rate of API-specific security incidents reported by 78% of cybersecurity teams within the last year.
Inadequate security measures have left many APIs vulnerable, making them targets for sophisticated cybercriminals who exploit API weaknesses to access sensitive data.
To counter these risks, API gateway authorizers are a critical infrastructure component, reducing security risks such as password leakage and unauthorized access. These solutions, which support protocols like LDAP Single Sign-On (SSO), are becoming increasingly important for enterprise managers seeking to enhance user efficiency and experience while simplifying system management and reducing operational costs. With 93% of organizations acknowledging the relevance of APIs and 97% agreeing on the synergy between APIs and microservices, token-based API gateway authorizers are indispensable for safeguarding systems and optimizing performance, ultimately leading to higher customer satisfaction and productivity gains.
Implementing Custom Authorization Logic
Customizing authorization in your applications can be a critical aspect of securing your user's data. For instance, in a serverless environment, where multitenancy and role-based access control are essential, a Lambda Authorizer can be implemented to enforce precise access rules. Take the scenario of an application designed for organizational file management.
Here we have two user roles: the CEO, who is granted access to every file within their organization, and the general user, who can only view files they have personally created. The challenge comes in crafting a robust authorization mechanism that doesn't entangle authorization logic with the business logic, a common pitfall that can lead to maintenance headaches and potential security flaws.
In the context of serverless functions, while the benefits such as ease of deployment, scalability, and cost efficiency are compelling, authorization is often a complex aspect that's difficult to get right. By leveraging a Lambda Authorizer, the authorization code is centralized, reusable across all functions, and decoupled from the business logic. This approach not only simplifies the authorization process but also enhances security by providing a clear separation of concerns.
This method is particularly beneficial when dealing with complex access requirements that may evolve over time, ensuring that your authorization strategy remains robust and adaptable.
Caching and Performance Optimization
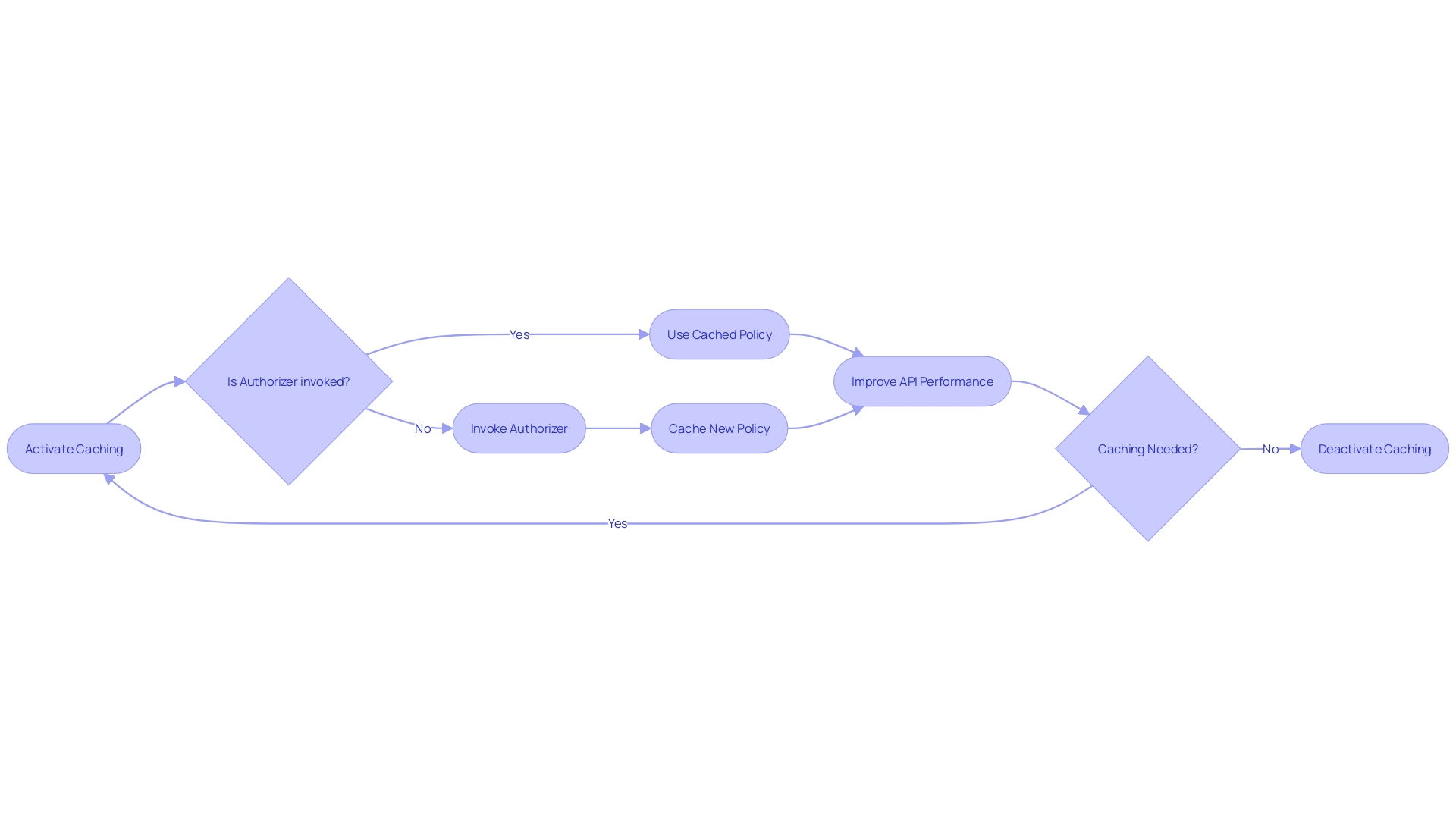
Harnessing caching mechanisms within your API Gateway Authorizers provides a significant boost to performance. When caching is activated, the necessity of invoking the authorizer for each incoming request diminishes, leading to a more responsive API experience. This enhancement is particularly valuable as it can handle a high volume of requests while maintaining optimal speed and reducing latency.
An API gateway, serving as the maître d' of requests, facilitates the smooth handling of numerous tasks such as request validation, authorization, rate limiting, and routing. In this context, remember that authorization—distinct from authentication—is about granting access to resources, not just verifying identities.
Recent discussions in the tech community, including insights on distributed and federated API platforms, stress the importance of robust API management. In line with these advancements, employing caching as a strategy within API gateways aligns perfectly with the drive for efficiency in modern software architecture.
Moreover, practical examples highlight the real-world benefits of caching. Consider the case where API latencies were significantly reduced by implementing caching, thus avoiding time-outs caused by processing multiple requests in succession. These improvements underscore the importance of a well-architected API gateway in today's tech landscape, which is not only about handling requests but also about optimizing the experience for both developers and end-users.
Handling Errors and Responses
Effective management of errors and responses is a critical aspect of working with API gateways. When an API exceeds a set rate limit, such as 100 requests per minute, it is crucial to provide clear feedback to the user. A typical error response for exceeding rate limits might look like this:
HTTP/1.1 429 Too Many Requests Content-Length: 1234
In a real-world scenario, an overburdened API can significantly disrupt operations. For instance, a critical microservice may rely on a third-party API to process events. If this service encounters a 429 error, it can have a severe impact on the flow of operations.
To mitigate such issues, centralized control through an API gateway is advantageous. It acts as a single point of entry for all requests, allowing for the enforcement of resiliency patterns such as rate limiting and error management across all services. This centralization also streamlines the implementation and maintenance of these features.
As one expert in the field puts it, 'The use of APIs as a middle layer between frontend and backend wasn't common; database calls were made directly from page templates. When the need for separation between the front and backend emerged, so did APIs as a middle layer.' This evolution underscores the importance of handling API responses and errors effectively.
Moreover, a fully managed API gateway offers relief to developers by handling the underlying infrastructure, software updates, security, scalability, availability, and disaster recovery. However, it's important to note that such abstractions can come with trade-offs, such as a loss of flexibility and hard limits on request rates imposed by the gateway.
In summary, understanding and implementing effective error and response handling mechanisms at the API gateway level can prevent operational disruptions and improve the overall user experience.
Best Practices for Using API Gateway Authorizers
API gateways play a critical role in modern enterprise information systems, particularly when it comes to securely managing both internal and external resources. The increasing need for flexibility, coupled with frequent personnel turnover, requires a system that can handle secure access management efficiently. API gateways meet this demand by providing a unified point of entry for services, simplifying access and management for developers.
To illustrate the importance of an API gateway, consider LDAP (Lightweight Directory Access Protocol) Single Sign-On (SSO). It's an effective solution for enhancing security and improving user efficiency. By using an API gateway with LDAP SSO, enterprises can reduce risks such as password leakage while also streamlining system management and lowering operational costs.
When discussing access management strategies in microservices, there are generally two approaches. One is where each microservice manages its own access, akin to individual rooms in a club with separate bouncers checking IDs. The other centralizes authority through an API gateway, which then becomes responsible for authorisation, authentication, and more.
A fully managed API gateway service allows developers to focus on service development rather than management. This is because the cloud provider handles responsibilities like maintenance, software updates, security, and disaster recovery. However, this convenience can come at the cost of flexibility, as there might be limits on the number of requests per second the gateway can handle.
Lastly, the community plays an essential role in maintaining and improving API gateway technologies. For example, the Kubernetes Gateway API has evolved thanks to the contributions of many community members who have shared the maintenance load and provided vital input since its inception.
In summary, when using API Gateway Authorizers, it's crucial to understand the balance between security and flexibility, the role of community in development, and the way fully managed services can ease the burden of API management while imposing certain limitations. By keeping these factors in mind, developers can make informed decisions about their API gateway strategy.

Use Strong Authentication Mechanisms
The importance of robust authentication mechanisms in web applications cannot be overstated, especially given the increasing occurrences of API breaches and the resulting exposure of sensitive data. Authentication is the cornerstone of security, acting as the gatekeeper by verifying the identities of those attempting to gain access to an API. One must differentiate it from authorization, which determines what authenticated users are allowed to do.
For developers, it's not just about locking down data; it's about creating a seamless user experience where users are confident in the security of their transactions.
To tackle the challenge of authentication, several tried-and-tested technologies are available. OAuth, for example, is a widely adopted standard for authorization and, with the right extensions, it also supports authentication. Since its inception in 2006, OAuth has been embraced for its ease of use, enabling developers of all skill levels to integrate social logins into their services.
However, ease of use doesn't mean it lacks complexity. OAuth is a multifaceted protocol with numerous features quietly working in the background to ensure secure interactions.
Another potent authentication technology is JWT (JSON Web Tokens), which securely transmits information between parties as a JSON object. It's particularly useful for single sign-on (SSO) scenarios, where users can be authenticated just once and gain access to multiple services without the need to log in again.
For those requiring a more tailored solution, Amazon Cognito User Pools offer a fully managed user directory that can scale to hundreds of millions of users. It's a comprehensive solution for user management, authentication, and access control.
Incorporating such robust authentication mechanisms into API documentation is not merely about preventing unauthorized access; it's a fundamental aspect of creating a trustworthy digital environment where sensitive data is protected from attacks. With 78% of cybersecurity teams experiencing an API-related security incident in the past year, and only 40% having visibility into which APIs return sensitive data, the focus on secure authentication strategies has never been more critical.
As we've seen with companies like Stripe and their meticulous attention to documentation, clear and secure guidance on authentication practices is essential for any API's users. Whether it's through manual documentation or code-first approaches, the goal remains the same: to provide developers and end-users with the information they need to use APIs securely and effectively.
Implement Authorization Checks
Efficient authorization checks are crucial in safeguarding resources within any application. The complexities of authorization often intertwine with your application's business logic, as seen in cases of managing user roles and data permissions. For instance, let's consider a common scenario: a multi tenant file management application with two user types, CEOs and regular users.
CEOs should access all files within their organization, while regular users should only access files they've created. In such a setup, a robust authorization mechanism ensures that the CEO can access all files without mistakenly allowing regular users the same privilege.
Function Level Authorization is particularly pivotal. It controls access to specific functions within an application, ensuring users perform only actions they're permitted to. For instance, you wouldn't want a regular user to access administrative functions by simply changing the HTTP method from GET to DELETE.
Here, the deep analysis of authorization mechanisms comes into play, scrutinizing user hierarchies and role-based permissions.
The decision of whether to embed authorization directly within your application or to use it as a separate service is non-trivial. It influences how intertwined your authorization logic is with your application's core functions. Embedded authorization can be more straightforward for simple applications but may become a bottleneck as complexity grows.
On the other hand, an external service can offer more flexibility and easier maintenance but requires careful integration.
In practice, effective API documentation serves as the 'user manual' for authorization within applications, delineating which roles have access to which operations and data. It is as essential as the user manual for a laptop, guiding users on operations and functions. Just as SmartBear commits to helping customers navigate a technology-driven world, clear API documentation helps developers navigate application authorization.
Ultimately, the key to thorough authorization lies in understanding the intricacies of your application's data and user permissions, as well as being mindful of potential overlaps between the two. By carefully designing your authorization logic and documenting it clearly, you can ensure that only authorized users access specific resources, aligning with the needs of a secure and efficient application infrastructure.
Leverage Authorization Caching
Utilizing an API gateway that supports LDAP Single Sign-On (SSO) is essential in modern enterprise systems, where the need for flexible and secure resource management is paramount. The API gateway acts as a unified entry point, simplifying access and management of services. It facilitates developers with features such as security, monitoring, and traffic control, increasing system reliability and security.
Implementing authorization caching is a strategy that can significantly enhance the performance of your authorizers. As services transition from monolithic to microservice architectures, assumptions about having immediate access to all necessary authorization data are no longer valid. The required data for authorizing user actions might be distributed across multiple microservices, necessitating a centralized authorization service.
In response to this challenge, leveraging caching mechanisms, such as Memcached or Redis, to store frequently accessed authorization data can reduce latency and improve API response times. Memcached, known for its high performance, is particularly effective for projects with heavy API traffic and substantial data storage needs. Redis offers flexibility and scalability, making it suitable for projects requiring a variety of data types and the ability to handle a large user base.
By caching authorization information, API gateways can minimize redundant database queries, thereby speeding up the process of determining if a user has the necessary permissions for a given action.
To ensure that your API documentation is as efficient as the technology you're implementing, start by organizing the content into clear sections. Use subheadings and concise descriptions to guide users through your API, employing lists to outline key concepts. Include examples and code snippets to illustrate API usage, catering to varying experience levels.
A search function in your documentation further enhances user experience, allowing quick access to specific information. Remember, the goal is to provide users with a clear path to understanding and using your API, from the basics to more advanced interactions. As Nick Tune highlights, the complexity of domains like 'Accounts' requires careful consideration and explicit definition in your documentation to avoid confusion and misinterpretation.
Example Use Case: Securing an API with API Gateway Authorizers
Securing an API through an API Gateway Authorizer is a critical step in safeguarding digital systems. API gateways act as the maitre d' of an enterprise's digital restaurant, efficiently managing the flow of data traffic and securing the entrance. They perform a multitude of essential functions, including request validation, authorization and authentication, rate limiting, and request routing.
Imagine a digital ecosystem as an exclusive club, where the gateway controls who gets to enter each room, ensuring only authorized personnel can access sensitive information.
With API-specific attacks on the rise, it's reported that 78% of cybersecurity teams have encountered an API-related security incident in the past year. This highlights the importance of robust API security, which encompasses practices and products to thwart malicious attacks and misuse. Think of it as employing a team of vigilant security guards who monitor every interaction, ready to respond to any threat.
Authorization, a key component of API security, is like assigning specific access levels to different users. For instance, someone might have 'comment' access to a document, allowing them to leave feedback without altering the original content. This distinction is pivotal for maintaining the integrity of digital assets.
API gateways have become indispensable in modern information systems, particularly with frequent personnel changes and the need for secure, flexible resource management. They offer a unified access point that simplifies the user experience while bolstering security and reliability. As enterprises continue to embrace digital and cloud-based infrastructures, the role of API gateways in ensuring secure and efficient operations has never been more critical.
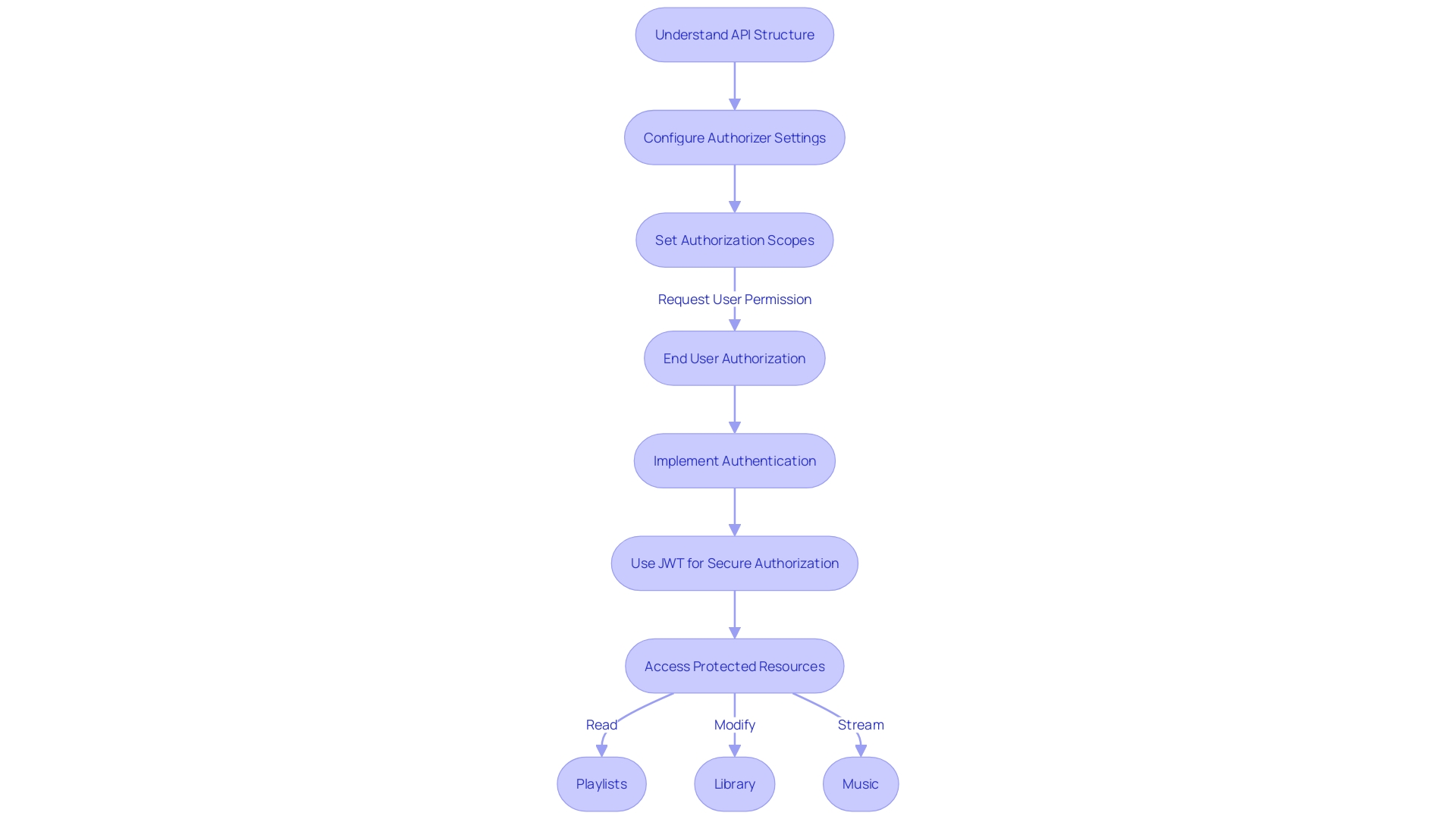
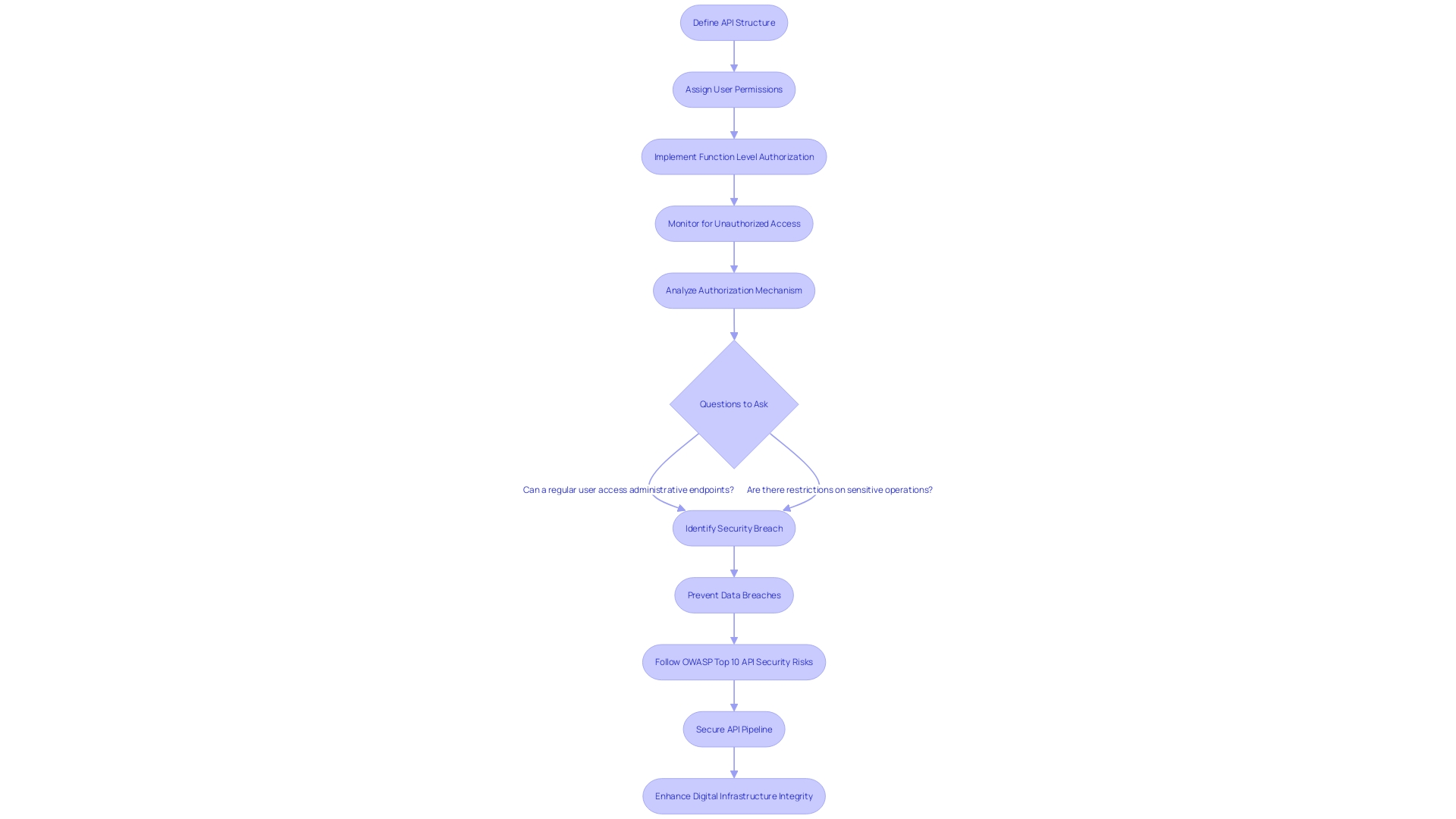
Define the API Structure
In the digital age, constructing secure API architectures is paramount. The first step in this process involves meticulously defining the structure of your API, which encompasses the various endpoints, methods, and the resources they interact with. This structure acts as the foundation for Function Level Authorization, a security practice that grants access to functions or operations based on specific user permissions.
Such an approach not only enhances security by limiting access to authorized actions but also provides a more tailored user experience by restricting functionalities to appropriate user roles.
This detailed approach to API security is especially crucial given the vulnerabilities facing internet-facing APIs. With digital systems increasingly relying on APIs for data transfer between applications and users, there's a heightened risk of unauthorized access and data breaches. In fact, recent studies highlight the alarming trend of API breaches, with 60% of surveyed organizations reporting at least one incident in the past two years.
It's evident that robust security protocols and vigilant monitoring are necessary to safeguard sensitive data managed by APIs. Ensuring that regular users cannot access administrative endpoints is just one of many strategies needed to spot and fix broken Function Level Authorization. With an estimated 20,000 APIs used by organizations, the task is challenging but essential.
As you structure your API, consider these security challenges and the role of Function Level Authorization in preventing unauthorized access and maintaining the integrity of your digital infrastructure.
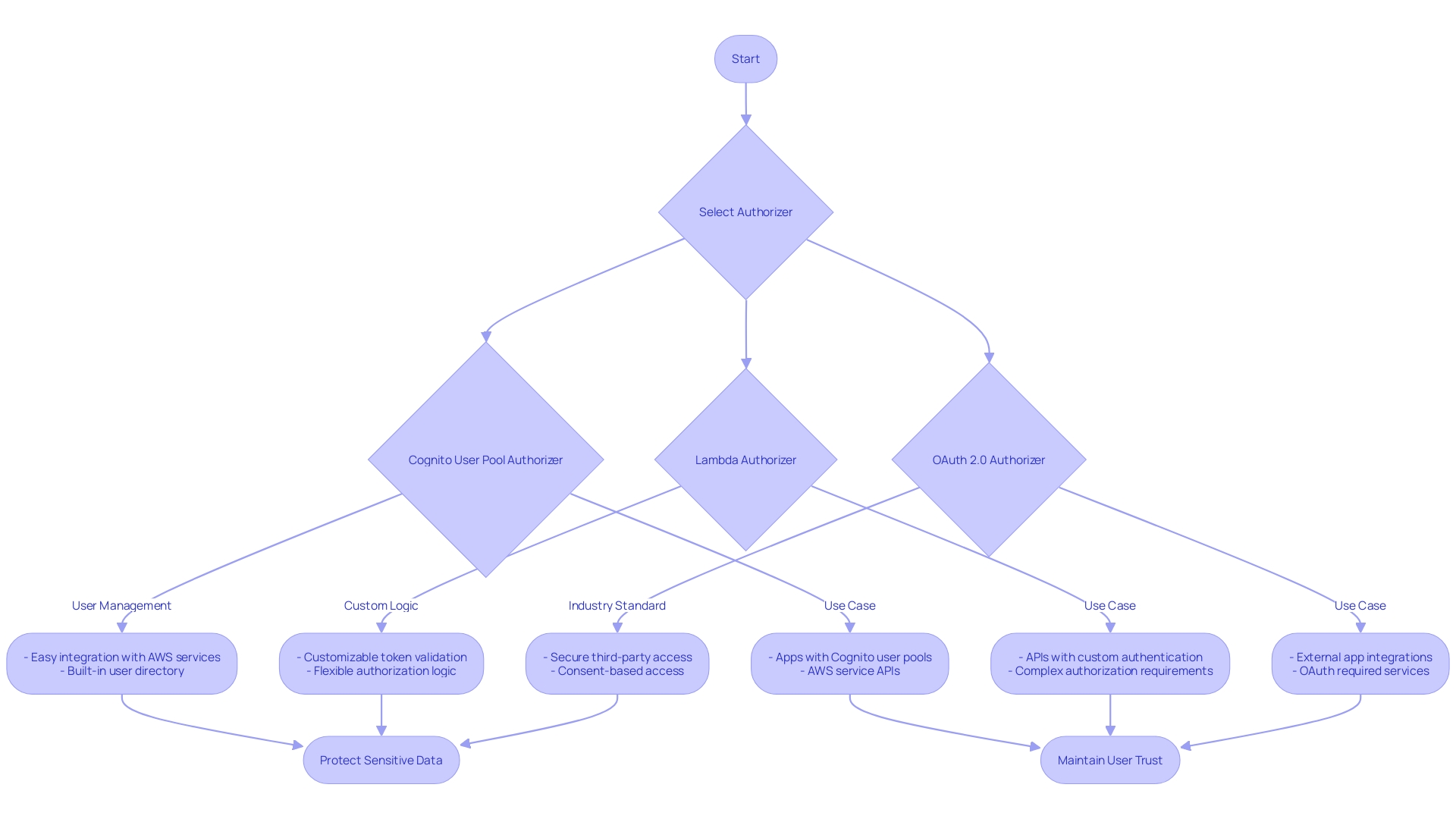
Choose the Authorizer Type
Selecting the correct authorizer for your API is a critical decision that impacts the security and usability of your services. There are several types of authorizers to choose from, each with its own strengths and applications. A Cognito User Pool Authorizer integrates with Amazon Cognito to provide user authentication, offering a solid solution for controlling user access.
The Lambda Authorizer is a flexible option that runs a Lambda function to handle the authentication, allowing custom logic for more complex scenarios. Lastly, the OAuth 2.0 Authorizer supports the OAuth 2.0 framework, making it suitable for integrating with external identity providers. Each type of authorizer plays a pivotal role in ensuring that only authorized users can access your API, a concern underscored by the 78% of cybersecurity teams who've experienced an API-related security incident in the last year.
As API security becomes an increasingly high priority, choosing the right authorizer is more important than ever to protect sensitive data and maintain user trust.
Implement the Authorization Logic
Crafting robust authorization logic is a cornerstone of secure app development. In the realm of API documentation, it's crucial to provide clear guidelines on implementing these safety measures. Authorization, distinct from authentication, is all about confirming a user's permissions to access certain resources.
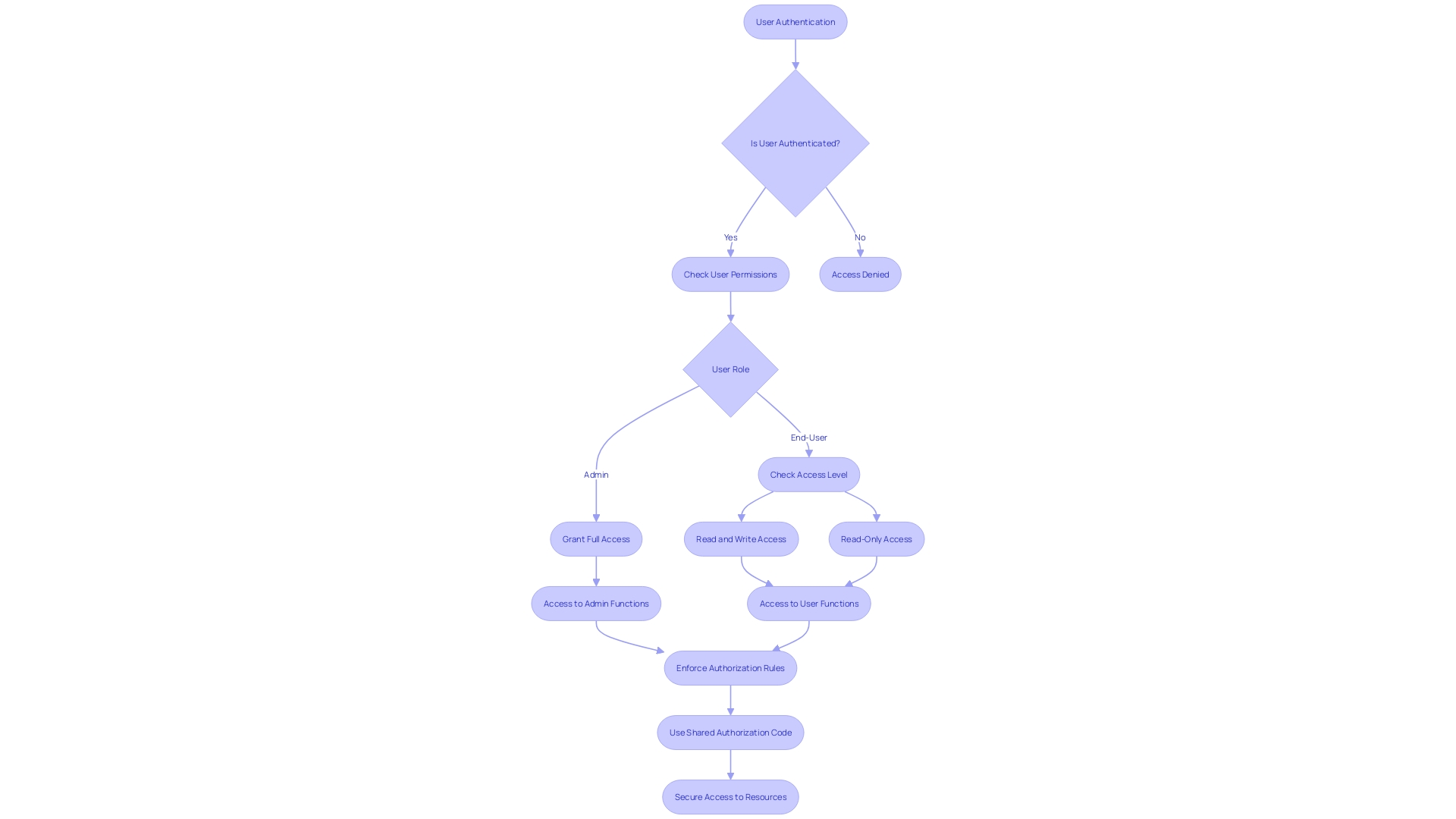
For example, in a Phoenix LiveView application, you might be setting up distinct access levels for admins and end-users. Admins might have the ability to modify or delete any record, while end-users can only interact with the records they've created. A shared authorization code snippet can be used across functions to enforce these rules.
Consider a multitenant file management system. Here, CEOs can access all organizational files while regular users are limited to files they've created. The authorization code must be carefully crafted to reflect these constraints without being intertwined with business logic, ensuring easy maintainability and scalability.
Moreover, when exploring Function Level Authorization, one must dive deep into the application's user hierarchy and roles. Questions to ponder include: What operations should each role perform? How does the authorization mechanism reflect the user hierarchy and groups within the application?
An API gateway with LDAP Single Sign-On (SSO) support is a prime example of implementing such authorization measures. It not only provides a secure entry point for various services but also facilitates functions like security, monitoring, and traffic control. The gateway's role in enhancing system reliability, user efficiency, and experience shouldn't be understated.
In summary, documentation should guide developers on setting up authorization logic that's decoupled from business logic, ensuring that permissions are handled consistently and securely across the application.
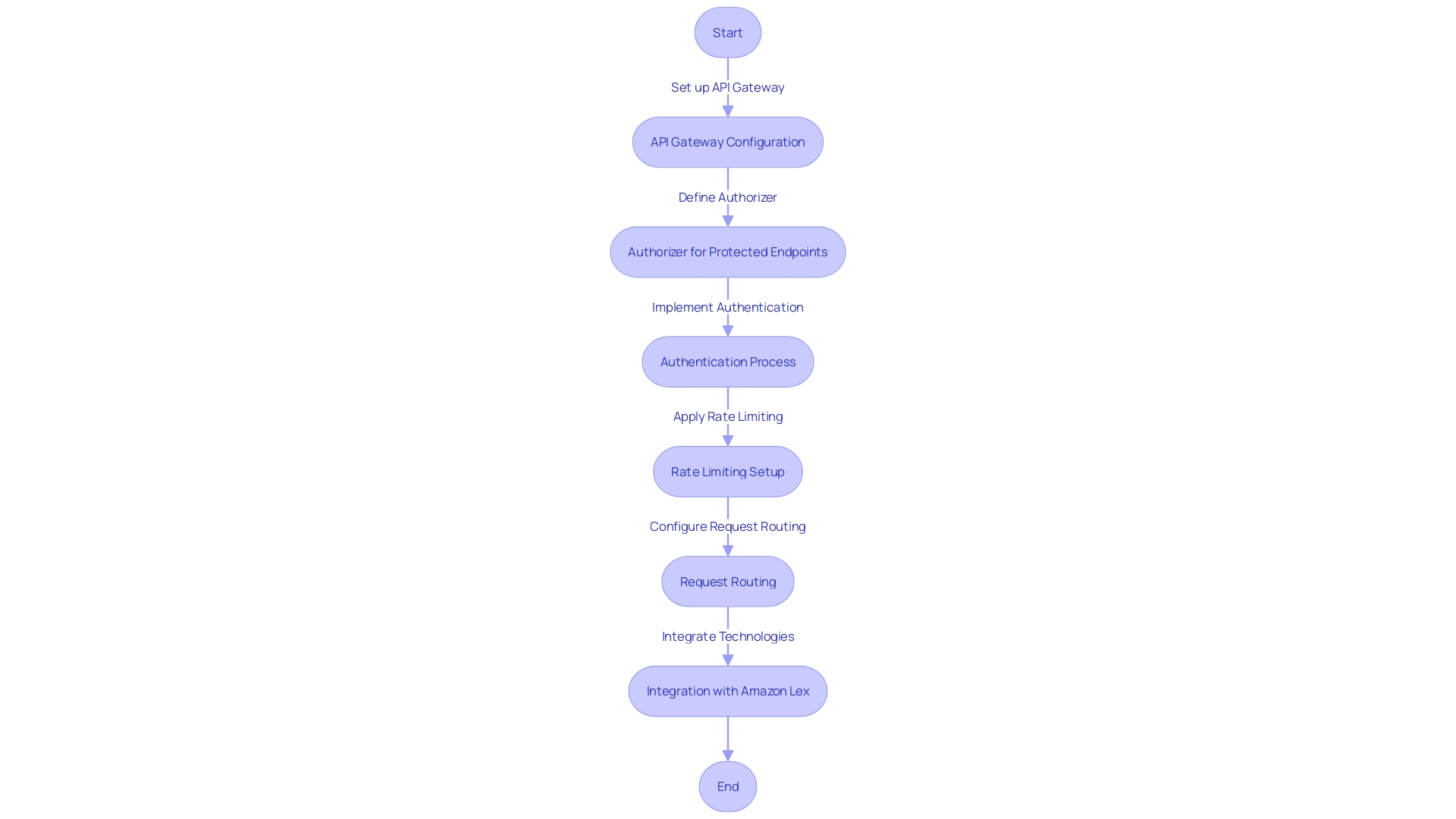
Configure API Gateway Integration
To intertwine security and efficiency in your systems, configuring your API Gateway is a pivotal step. By setting up the gateway to use an authorizer for every protected endpoint, you establish a safeguard that is invoked with each request. This is not just a barrier; it's a gatekeeper ensuring that only authenticated and authorized users can interact with your endpoints.
An API Gateway acts as a sentinel at the entrance to your digital services, managing requests through functions like authentication, rate limiting, and request routing. In the bustling landscape of enterprise information systems where internal dynamics shift frequently, this gateway isn't merely a door—it's a versatile tool that enhances security and streamlines user access, particularly through solutions like LDAP Single Sign-On.
The robustness of the API Gateway is illustrated by its ability to unify access across services, enhancing the reliability and security of systems. Developers benefit from the abstraction provided by a fully managed service, which covers underlying infrastructure, software updates, and disaster recovery, allowing them to concentrate on innovation rather than maintenance. However, with great abstraction comes a trade-off in flexibility, which is evident in the hard limits on the number of requests per second that the gateway can handle.
Moreover, the usage of API Gateways is on a relentless rise, as pointed out by 'The State of APIs, Integration, and Microservices' report by Vanson Bourne. A staggering 93% of organizations acknowledge the crucial role of APIs, and 86% recognize the potential isolation without them. These statistics underscore the gateway's role in improving visibility and access to key data assets.
In the same vein, technologies like Amazon Lex exemplify the advancements in conversational interfaces, leveraging the same technology behind Amazon Alexa to create natural language understanding models. This adds another layer of sophistication to the API Gateway's capabilities, further enhancing the interaction between users and services.
By integrating such authorizers, you're not just adhering to best practices; you're also elevating the security and efficiency of your enterprise's digital ecosystem, ensuring a seamless and secure user experience.
Conclusion
In conclusion, API Gateways are essential for securing and managing APIs by filtering requests and granting access only to authenticated users. They serve as centralized and secure conduits for service management, providing monitoring, traffic control, and reliability. API gateways simplify developers' tasks by offloading infrastructure management to cloud providers in the microservices architecture.
Different types of API Gateway authorizers, such as Cognito User Pool Authorizer, Lambda Authorizer, and OAuth2 Authorizer, enhance the security and efficiency of API ecosystems. These authorizers ensure that only authenticated entities are allowed entry, improving overall system integrity.
To create an API Gateway Authorizer, understanding the gateway's significance as a unified entry point and reviewing authentication mechanisms are crucial. Fully managed API Gateway services relieve developers from infrastructure management, and features like rate limiting and request routing contribute to efficient traffic control.
The API Gateway Authorizer workflow involves request validation, authentication, authorization, rate limiting, and routing. API gateways act as centralized authorities, ensuring secure and controlled access to APIs. By selecting the appropriate authorizer type and configuring API Gateway integration, organizations can optimize security, usability, and management of their APIs.
To maximize efficiency and productivity, it is important to follow best practices when using API Gateway Authorizers. Strong authentication mechanisms, implementing custom authorization logic, leveraging authorization caching, and handling errors and responses effectively are key considerations. Clear API documentation guides developers and users through API integration and usage.
In summary, API Gateways and their associated authorizers are indispensable for modern IT infrastructure. They enhance security, efficiency, and reliability, allowing organizations to optimize access management, user experience, and operational costs. By implementing the right API Gateway Authorizer, enterprises can achieve maximum efficiency and productivity in their API ecosystems.
Start optimizing your API ecosystem today with Kodezi's comprehensive suite of tools!
Frequently Asked Questions
What is an API Gateway?
An API Gateway serves as a central hub for managing, routing, and securing API requests between clients and backend services. It provides a single entry point for all API interactions and includes features such as authentication, authorization, rate limiting, and request transformations.
Why are API Gateway Authorizers important?
API Gateway Authorizers are essential for security, as they ensure that only authenticated and authorized users can access protected API resources. They help prevent unauthorized access and potential data breaches, maintaining the integrity of the system's data.
What types of API Gateway Authorizers are available?
The main types of API Gateway Authorizers include Cognito User Pool Authorizers, Lambda Authorizers, and OAuth2 Authorizers. Each type serves a specific purpose, from integrating with Amazon Cognito for user authentication to enabling custom authorization logic or supporting OAuth2 protocols.
How does a Cognito User Pool Authorizer work?
A Cognito User Pool Authorizer integrates with Amazon Cognito to authenticate users. It verifies user credentials against the Cognito User Pool and issues access tokens, allowing authenticated users to access secured API endpoints.
What is the role of a Lambda Authorizer?
A Lambda Authorizer allows the execution of custom authentication and authorization logic via AWS Lambda functions. It is used for scenarios that require more complex and tailored authorization strategies beyond standard permission sets.
How does an OAuth2 Authorizer enhance API security?
An OAuth2 Authorizer uses the OAuth2 framework to validate tokens and ensure that only authorized entities have access to protected resources. It is crucial for integrating APIs with external OAuth2 providers and managing access based on token permissions.
Can API Gateway Authorizers be customized?
Yes, API Gateway Authorizers, such as Lambda Authorizers, can be customized to suit specific authorization requirements by defining custom logic within the Lambda function.
What is the significance of authorization caching in API Gateways?
Authorization caching enhances API performance by storing authorization data and reducing the need for repeated authorizer invocations. This leads to faster API response times and improved user experience.
How do API Gateways handle errors and responses?
API Gateways manage errors and responses by providing feedback on issues such as rate limit exceedance. They centralize error management across all services, ensuring consistent and clear communication with users.
What are the best practices for using API Gateway Authorizers?
Best practices for using API Gateway Authorizers include choosing the appropriate authorizer type for your needs, implementing robust authorization logic, properly configuring the API Gateway integration, leveraging authorization caching for performance, and ensuring strong authentication mechanisms.
How do API Gateways contribute to the overall security of enterprise systems?
API Gateways play a critical role in the security of enterprise systems by managing access control, enforcing security protocols, and offering features like LDAP Single Sign-On support, which enhances system reliability and reduces risks such as password leaks.




