Introduction
In the realm of software development, ensuring a secure codebase is not just a commodity, it's a necessity. Code-level vulnerabilities can act as unlocked doors for cybercriminals, providing them with opportunities to compromise systems, manipulate sensitive data, or disrupt services. To combat these exploits, it is imperative for developers to recognize and comprehend the array of vulnerabilities that may lurk within a codebase.
This article explores the significance of secure coding, delves into real-world vulnerabilities, highlights the need for robust security measures, and showcases advancements in code security practices. By staying informed, adopting best practices, and leveraging cutting-edge tools, developers can fortify their applications against threats and achieve a more secure and resilient codebase.
Understanding Code-Level Vulnerabilities
In the realm of software development, a secure codebase is not just a commodity, it's a necessity. Vulnerabilities in code can be likened to unlocked doors for cybercriminals, providing them with avenues to compromise systems, manipulate sensitive data, or disrupt services. To protect against such exploits, it is crucial to identify and understand the range of code-level weaknesses that may hide within a codebase.
For example, in our 'Lessons Learned' series, we analyze real-world weaknesses through the perspective of an application protection engineer. This perspective focuses on the root causes and preventive tactics rather than solely on exploitation methods. Take an example from the series, where we scrutinize a validation function in a PHP file, revealing that even a routine constraint check could lead to complications if not meticulously crafted. Such insights are pivotal for developers to fortify their applications against threats.
Moreover, the significance of secure coding is underscored by events in the tech world. Recent alerts from Amazon Web Services about vulnerabilities in widely-used tools like TorchServe, which could impact AI model integrations, emphasize the urgent need for strong protective measures. The push for software bills of materials (SBOMs) aims to provide greater transparency into the software and its dependencies, enabling organizations to quickly identify and address potential concerns.
In improving code security, contemporary research indicates that large language models (LLMs) are transforming the procedure by skillfully identifying safe versus unreliable code. They can identify vulnerabilities and provide corrective strategies, thereby enhancing the coding process beyond conventional static analysis. This advancement represents a significant leap towards more secure coding practices.
As developers, it's crucial to stay informed about the best practices specific to our technology stack, such as Node.js, and remain vigilant about emerging threats like typosquatting attacks or malicious packages. By utilizing resources like CVE.ICU, an automated system that examines data from the National Vulnerability Database (NVD), we can comprehend and anticipate potential threats more effectively.
To summarize, code protection is not an afterthought but a fundamental aspect of software development. By gaining knowledge from real-life weaknesses, keeping up with the most recent security updates, and embracing state-of-the-art tools and methods, developers can guarantee a more resilient and fortified codebase.
Types of Code-Level Vulnerabilities
Maintaining a secure codebase is essential, and developers must be watchful about different code-level weaknesses. SQL Injection, for instance, poses a threat when attackers manipulate SQL queries using user input, leading to potential unauthorized access or data breaches. Cross-Site Scripting (XSS) weaknesses enable attackers to insert malicious scripts on web pages, putting user data at risk or facilitating unauthorized actions. Similarly, Cross-Site Request Forgery (CSRF) can deceive authenticated users into performing unintended actions on a web application.
Remote Code Execution weaknesses are especially concerning as they allow attackers to execute arbitrary code on systems, gaining unauthorized access and control. Insecure Direct Object References enable attackers to access or manipulate restricted data by bypassing authorization checks.
Understanding these weaknesses is just the beginning; it's the capability to recognize and handle them efficiently that's vital. Recognition can be intricate, necessitating diverse kinds of weakness scanners customized to the distinct levels and artifacts within a program item. As technology advances and we integrate tools like programs' lists of materials (SBOMs), organizations can better understand dependencies and prepare for threats, as emphasized by the recent vulnerability alerts in tools like TorchServe and libcurl.
Developers play a key role in this landscape, often working creatively under constraints to find the simplest and most secure solution. While some may view taking shortcuts as 'lazy', it's often about finding the most efficient path to success. However, the responsibility also lies with software providers to ensure continuous improvement in addressing vulnerabilities. By examining pattern trends, we can determine which companies are making progress in reducing weaknesses and which need to enhance their quality improvement programs.
In the end, the objective is to promote a design process that prioritizes safety, where engineering teams are given the authority to take responsibility for the protection of their digital products. This entails a blend of measures, education, and technology-based automation within a DevSecOps framework to effectively handle weaknesses. By doing so, we can uphold the delicate equilibrium between safeguarding and development velocity, ensuring both sturdy defense mechanisms and the smooth advancement of software innovation.
Identifying and Assessing Code-Level Vulnerabilities
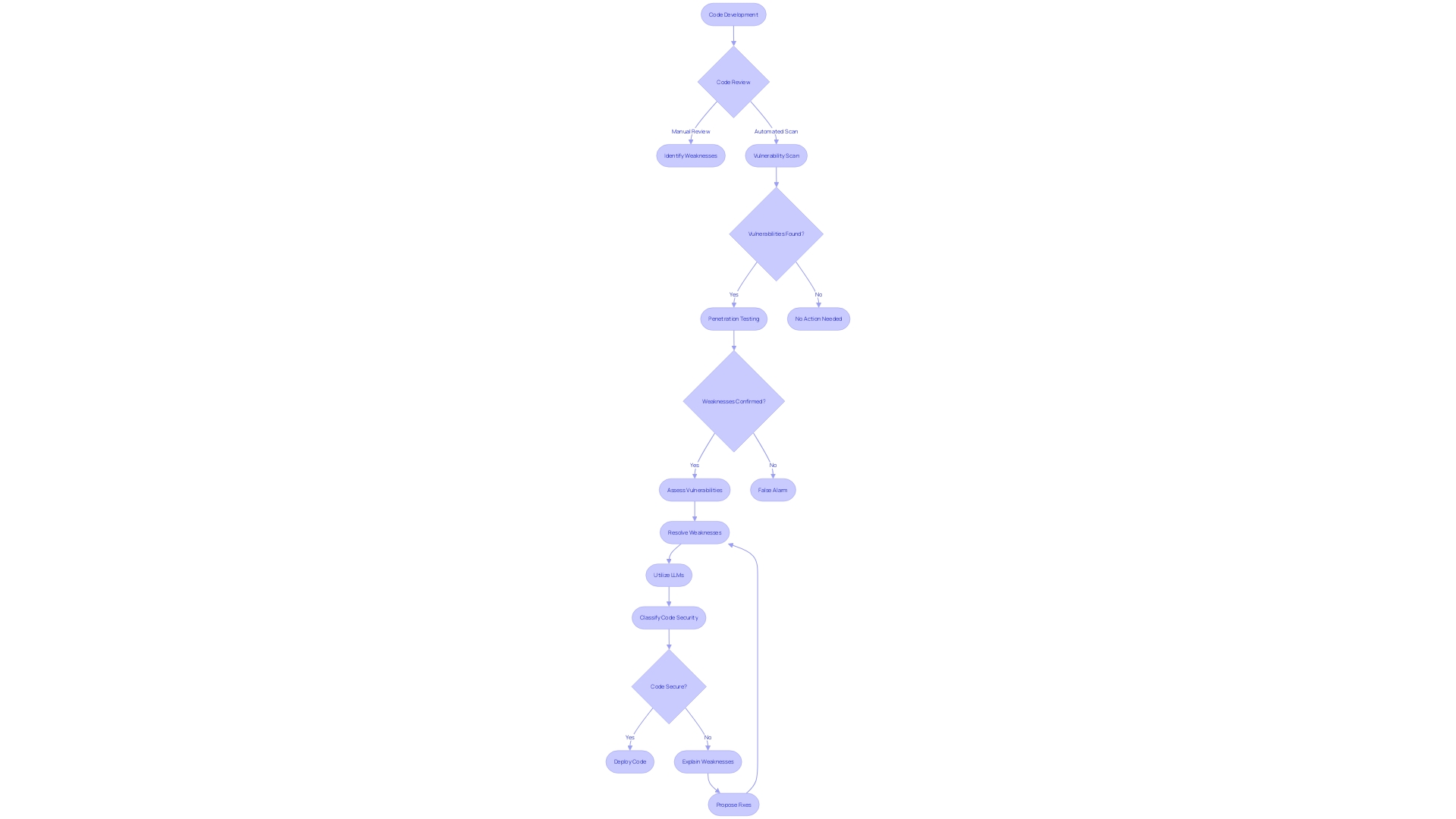
Recognizing and resolving code weaknesses is crucial for developing a strong and safe application. The process typically starts with a Manual Code Review, where developers carefully examine the codebase, identifying common coding errors, lapses in safety, and potential vulnerabilities that could be exploited.
Afterwards, Automated Scans come into action, utilizing specialized tools to scan the code for recognized weaknesses. These tools are crucial for their efficiency in detecting a range of issues that could compromise the code's integrity.
Penetration Testing takes weakness detection a step further by simulating cyber-attacks to uncover hard-to-detect security gaps. This proactive method is crucial in identifying weaknesses that might go unnoticed during automated scans.
After pinpointing the vulnerabilities, it's vital to assess them based on their severity using standards like the Common Vulnerability Scoring System (CVSS). Recent updates to CVSS provide additional metrics, like Safety (S) and Provider Urgency (U), to refine the assessment process.
Furthermore, the incorporation of Large Language Models (LLMs) into the workflow of safeguarding has displayed encouraging outcomes. These models are skilled at classifying code as safe or vulnerable, explaining the flaws, and suggesting fixes, which can significantly streamline the process.
Disturbingly, the State of Software Safety report, examining data from over 27 million scans, emphasizes the urgent requirement for watchful safety measures, particularly as the exploitation of a single weakness can affect thousands of users across diverse sectors.
Developers can also refer to NISTIR 8397 for comprehensive guidelines on crafting secure software, which highlights the significance of integrating protection at every stage, from planning to maintenance.
In summary, developers must utilize a blend of manual evaluations, automated tools, and penetration testing to proficiently handle code weaknesses. By prioritizing the most severe issues and leveraging the latest advancements in security technology, developers can systematically fortify their applications against cyber threats.
Best Practices for Managing Code-Level Vulnerabilities
To protect a codebase, implementing top-tier practices for risk management is crucial. Regular code reviews are a critical line of defense, requiring reviewers with a strong understanding of coding to pinpoint weaknesses. Following secure coding guidelines is essential, averting typical weaknesses and directing developers towards safer practices.
Input validation and sanitization are vital to thwart attacks like SQL injection and cross-site scripting (XSS), ensuring that user input is thoroughly vetted for malicious elements before acceptance. Employing prepared statements and parameterized queries is another bulwark against SQL injection, effectively separating user input from SQL code.
Ensuring that the software is regularly updated with the latest patches is essential, as it addresses known vulnerabilities and shields against new threats. Furthermore, ongoing safety education and consciousness foster a growth environment that gives priority to protection, which is vital in sectors such as banking where the risks are significant.
M&T Bank's initiative to establish Clean Code standards exemplifies the importance of such best practices. With a rich history and the ongoing digital banking transformation, they comprehend the disastrous risks linked to insecure applications. Their approach mirrors the guidelines outlined in NISTIR 8397 and the principles advocated by experts, emphasizing the significance of a meticulous, safety-oriented development process.
As the open-source landscape grows and AI-generated code becomes more prevalent, the need for a comprehensive view of one's code—via a Software Bill of Materials (SBOM), for instance—grows too. The 2024 OSSRA report emphasizes that almost all commercial software includes open-source components, with the typical application comprising more than 500 such elements, emphasizing the need for automated security testing to efficiently handle the magnitude of potential weaknesses. Through such vigilance and adherence to proven practices, developers can substantially diminish the risk of code-level vulnerabilities, achieving a fortified codebase.
Conclusion
In the realm of software development, secure coding is a necessity to protect against code-level vulnerabilities. Real-world vulnerabilities provide insights into preventive tactics, while recent alerts emphasize the need for robust security measures. Advancements like large language models (LLMs) revolutionize code security practices.
Staying informed and recognizing various vulnerabilities is crucial.
Effective vulnerability management involves manual code reviews, automated scans, and penetration testing. Assessing vulnerabilities based on severity using standards like CVSS helps prioritize issues. Implementing top-tier practices like regular code reviews and adherence to secure coding guidelines is paramount.
Input validation, software updates, and continuous security training are essential.
By staying informed, adopting best practices, and leveraging cutting-edge tools, developers can fortify their applications against threats. Prioritizing code security leads to increased efficiency and productivity.
Frequently Asked Questions
What are code-level vulnerabilities?
Code-level vulnerabilities are weaknesses within a codebase that can be exploited by cybercriminals to compromise systems, manipulate sensitive data, or disrupt services. They are like unlocked doors that provide avenues for security breaches.
Why is it important to understand code-level vulnerabilities?
Understanding code-level vulnerabilities is crucial for the protection of applications and systems. It helps developers to identify and fix potential security threats, thereby fortifying their applications against cyber-attacks.
What are some common types of code-level vulnerabilities?
Common types include SQL Injection, Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF), Remote Code Execution weaknesses, and Insecure Direct Object References.
What is the 'Lessons Learned' series mentioned in the article?
The 'Lessons Learned' series analyzes real-world code weaknesses from the perspective of an application protection engineer, focusing on root causes and preventive tactics.
Why are software bills of materials (SBOMs) important?
SBOMs provide transparency into a software's components and dependencies, enabling organizations to identify and address potential security concerns more effectively.
How are large language models (LLMs) contributing to code security?
LLMs are transforming code security by identifying safe versus unsafe code, detecting vulnerabilities, and providing corrective strategies. This enhances the coding process beyond conventional static analysis.
What are some resources developers can use to comprehend potential threats?
Developers can use resources like CVE.ICU and the National Vulnerability Database (NVD) to comprehend and anticipate potential threats more effectively.
How does manual code review contribute to identifying vulnerabilities?
Manual code review involves developers examining the codebase to identify common coding errors, safety lapses, and potential exploits that automated tools might miss.
What role do automated scans and penetration testing play in detecting vulnerabilities?
Automated scans use specialized tools to efficiently detect a range of issues, while penetration testing simulates cyber-attacks to uncover security gaps that might go unnoticed during automated scans.
What is CVSS and how does it help in assessing vulnerabilities?
The Common Vulnerability Scoring System (CVSS) is a standard that helps assess the severity of vulnerabilities. Recent updates to CVSS include additional metrics to refine the assessment process.
What are some best practices for managing code-level vulnerabilities?
Best practices include regular code reviews, following secure coding guidelines, input validation and sanitization, employing prepared statements and parameterized queries, updating software with the latest patches, and ongoing safety education.
What is the significance of M&T Bank's initiative with Clean Code standards?
M&T Bank's initiative to establish Clean Code standards demonstrates the importance of having meticulous, safety-oriented development processes to mitigate the risks associated with insecure applications.
How does the use of SBOMs and automated security testing help in managing vulnerabilities?
SBOMs provide a comprehensive view of a codebase’s components, while automated security testing helps efficiently handle the magnitude of potential weaknesses, especially in open-source components that are prevalent in commercial software.




