Introduction
In today's rapidly evolving digital landscape, safeguarding sensitive information and maintaining robust cybersecurity measures is paramount for businesses of all sizes. Understanding the unique cybersecurity needs of a business is the first crucial step in selecting the right software to protect critical assets and comply with industry regulations. This article delves into the essential features to look for in cybersecurity solutions, guiding businesses on how to evaluate and implement effective security measures.
Additionally, it explores best practices for the successful deployment of cybersecurity software and underscores the importance of continuous monitoring and timely upgrades to stay ahead of emerging threats. By integrating these strategies, businesses can ensure they are well-protected, build consumer trust, and maintain a competitive edge in the market.
Understanding Your Business's Cybersecurity Needs
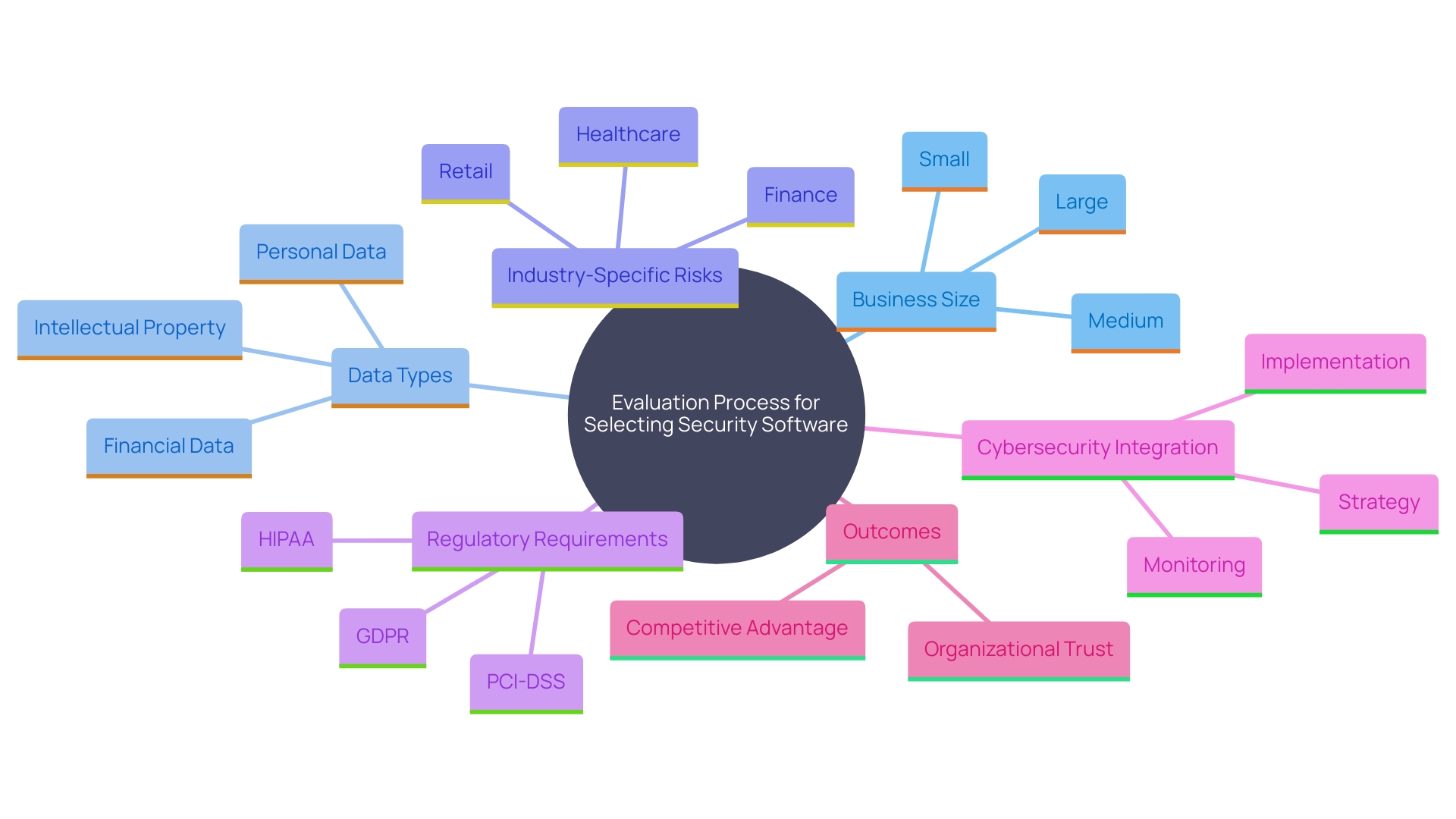
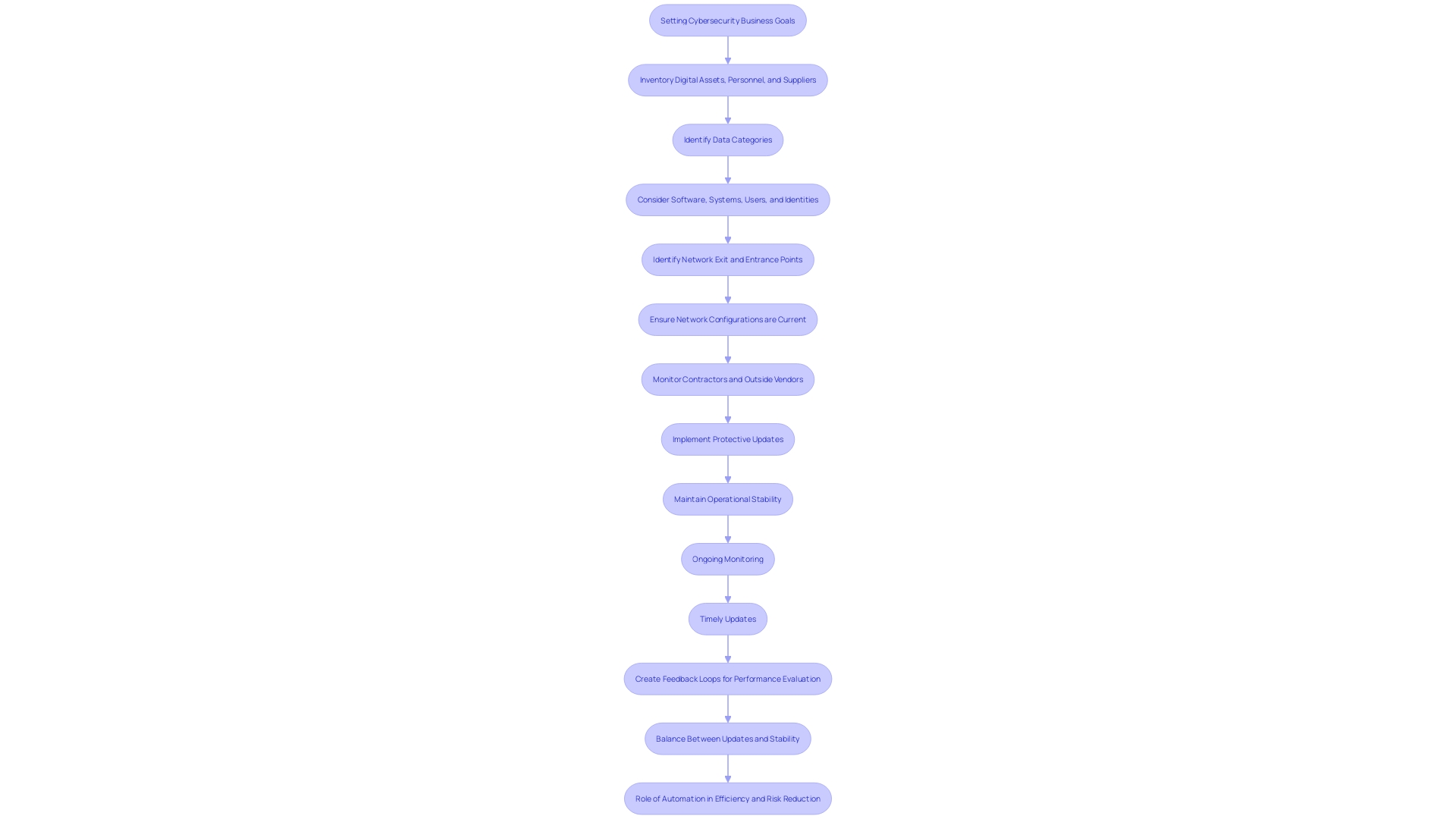
Selecting the appropriate security software begins with a comprehensive evaluation of your particular requirements. Begin by determining the size of your business and the type of data you handle. It's essential to identify potential risks that are specific to your industry, as well as critical assets that require protection. Understanding the regulations applicable to your business is also crucial.
A forward-looking approach to cybersecurity treats it as a core element of business architecture. It's important to put in place a framework that helps identify major risks and mitigation measures early on. This not only corresponds with your protection goals but also facilitates future expansion. A recent survey revealed that 53% of consumers make purchases from companies they trust with their data, and 40% stop using services if they learn customer data isn't protected.
To bridge gaps in understanding between technical teams and management, metrics provide a common language using trends and numbers. This aids in assessing the effectiveness of controls, policies, and procedures, and helps prioritize areas for improvement. Establishing a Community of Interest (Coi) for those interested in information security measurement can further refine the body of knowledge and identify opportunities for growth.
Integrating online security into your strategy from the beginning can avoid rework and foster trust and confidence in your products, providing your company a competitive advantage in the market. By adhering to best practices and industry standards, such as managing open-source applications and material lists (SBOM), you boost transparency and access to risk information, ultimately improving your organization's security stance.
Key Features to Look for in Cybersecurity Software
When selecting cybersecurity software, it's essential to focus on features that bolster your security stance. Choose options with strong danger detection and real-time monitoring abilities, as these are crucial in quickly recognizing and reducing risks. Automated response options are also crucial, allowing for rapid and effective reactions to threats without overwhelming your IT team.
Advanced encryption methods and comprehensive vulnerability management are non-negotiable, ensuring that your data remains secure and that potential weaknesses are promptly addressed. Compliance reporting tools are equally important, helping you to meet regulatory requirements and avoid costly penalties.
A user-friendly interface is indispensable, as it facilitates easy navigation and management, making it simpler for your team to adopt and effectively use the software. As observed in practical use cases, platforms such as Trend Vision One have demonstrated improvements in protective measures and operational efficiency by offering comprehensive reports and immediate insights, which facilitate decision-making and compliance procedures.
Furthermore, staying informed about the latest safety news and trends is essential. For instance, the ongoing development of AI-powered protective solutions underscores the importance of integrating advanced technologies into your defense strategy. By 2025, the global market for AI-driven cybersecurity tools is expected to reach $38.2 billion, with 50% of organizations actively relying on them by 2023. This trend emphasizes the increasing acknowledgment of AI's worth in improving protective measures and safeguarding networks from harmful individuals.
In conclusion, prioritize features that not only enhance security but also improve operational efficiency and ease of use, ensuring a holistic approach to safeguarding your digital assets.
Best Practices for Implementing Cybersecurity Software
Successfully applying cybersecurity tools requires a multi-faceted strategic approach. Begin with a meticulous installation process that ensures seamless integration with your existing systems. This includes comprehensive threat detection and analytics to keep your threat feeds consolidated and operationalize intelligence effectively. Create a comprehensive strategy for setting up the system to align with your particular security guidelines, making sure that you are ready to address possible weaknesses. Involve your team in comprehensive training sessions to help them understand the system’s features and optimal methods for enhancing its efficiency. Consistently examine and refresh the settings to stay alert to new dangers and shifts in your business context. This proactive approach is crucial, as highlighted by Gartner, emphasizing the need for a robust management plan to confidently embrace emerging solutions without compromising security. Real-world examples, such as M&T Bank's efforts to establish Clean Code standards, underscore the importance of maintaining high-quality, compliant software to protect sensitive data and operations. This ongoing vigilance and adaptability are essential in the ever-evolving landscape of cybersecurity.
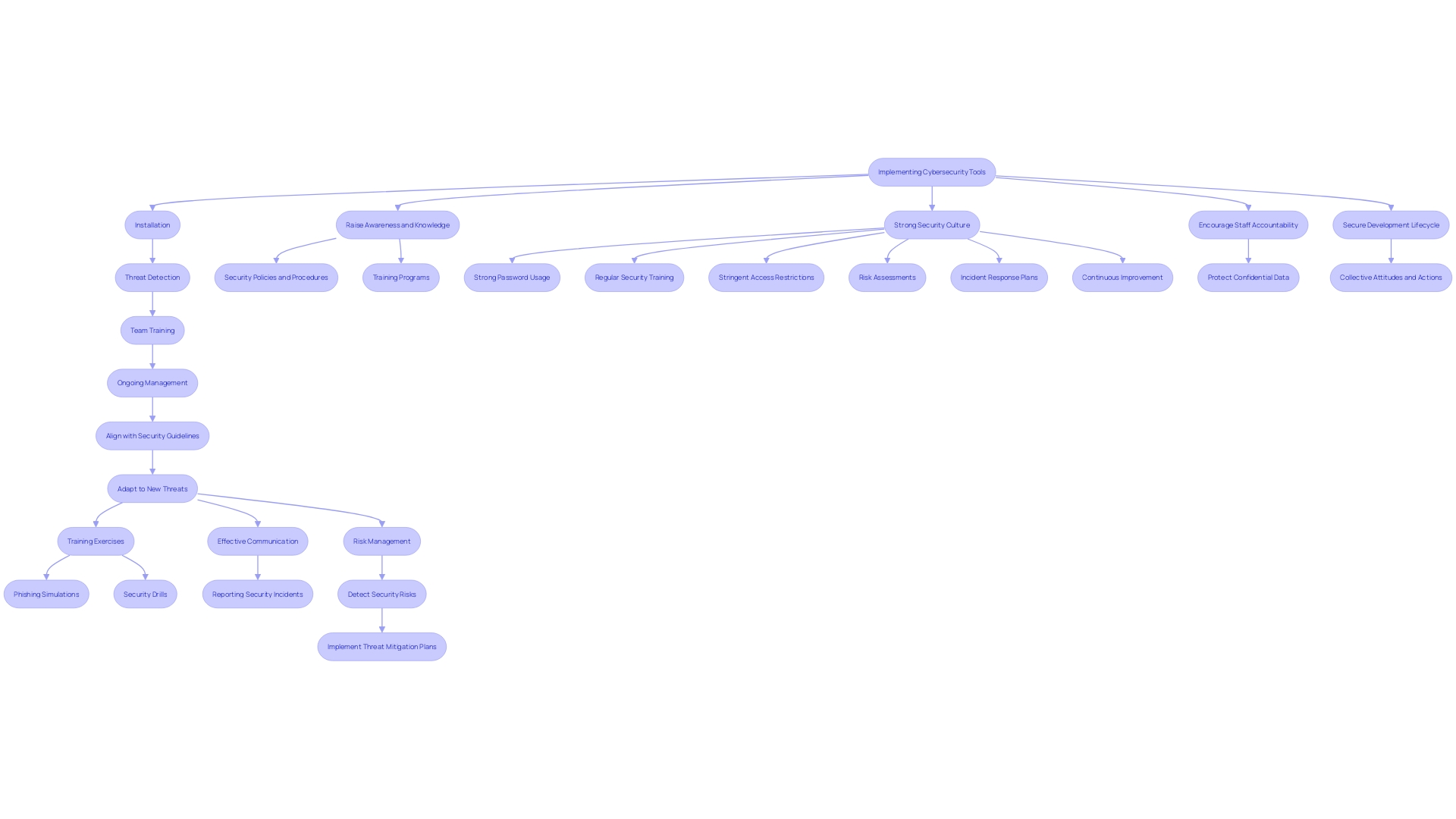
Continuous Monitoring and Upgrades
Cybersecurity demands constant vigilance and timely updates to stay ahead of emerging threats. Ongoing monitoring allows for immediate identification and reaction, greatly improving an organization's protective stance. Regular updates are essential, as they bring important protection patches and new functionalities; however, they must be carefully overseen to prevent introducing new weaknesses. Creating a feedback loop to evaluate system performance ensures continuous improvement. For instance, the recent global IT outage caused by a faulty software update highlights the importance of balancing updates focused on protection with operational stability. Chris Peters from United Airlines highlights the necessity for a clear comprehension of all devices within a network to uphold strong protective measures across their extensive operations. By automating threat detection and response, organizations can reduce the workload on IT staff and focus on strategic tasks, ultimately leading to cost savings by preventing breaches and minimizing downtime. As our reliance on IT systems grows, adopting a proactive and adaptive security strategy is more critical than ever.
Conclusion
In the dynamic realm of cybersecurity, understanding the unique needs of a business is essential for selecting the right protective measures. A thorough assessment of risks, compliance requirements, and critical assets not only informs the choice of software but also lays the groundwork for a robust security framework. By integrating cybersecurity into the core strategy, businesses can build consumer trust and gain a competitive advantage, ultimately ensuring their longevity in the market.
Key features of cybersecurity software play a pivotal role in fortifying an organization's defenses. Solutions that offer real-time monitoring, automated responses, and advanced encryption are non-negotiable in today's threat landscape. Emphasizing user-friendly interfaces and compliance tools further enhances operational efficiency, making it easier for teams to navigate and utilize these systems effectively.
As the industry shifts towards AI-driven tools, staying informed about the latest developments is crucial for maintaining a strong security posture.
Successful implementation of cybersecurity software hinges on a strategic approach that includes meticulous installation, comprehensive training, and ongoing updates. This proactive stance, supported by continuous monitoring, enables organizations to adapt swiftly to new threats while optimizing their security measures. By embracing best practices and fostering a culture of vigilance, businesses can not only protect their sensitive information but also ensure operational stability and resilience in an increasingly complex digital landscape.
Frequently Asked Questions
What is the first step in selecting appropriate security software for my business?
Begin with a comprehensive evaluation of your specific requirements, including the size of your business and the type of data you handle. Identify potential risks specific to your industry and critical assets that require protection.
Why is understanding regulations important when selecting security software?
Understanding applicable regulations is crucial to ensure compliance and avoid potential penalties, thereby protecting your business's reputation and financial standing.
How can I bridge the gap between technical teams and management regarding cybersecurity?
Using metrics can provide a common language for both teams, helping to assess the effectiveness of controls, policies, and procedures while prioritizing areas for improvement.
What features should I prioritize when choosing cybersecurity software?
Focus on options with strong threat detection, real-time monitoring, automated response capabilities, advanced encryption, comprehensive vulnerability management, and compliance reporting tools.
Why is a user-friendly interface important in cybersecurity software?
A user-friendly interface facilitates easy navigation and management, making it easier for your team to adopt and effectively use the software.
What recent trends should I be aware of in cybersecurity?
Stay informed about the development of AI-powered protective solutions, as the global market for these tools is expected to grow significantly, highlighting the importance of integrating advanced technologies into your security strategy.
How should I approach the installation of cybersecurity tools?
Begin with a meticulous installation process that ensures seamless integration with existing systems. This should include comprehensive threat detection and analytics aligned with your security guidelines.
What should I do after installing cybersecurity software?
Involve your team in comprehensive training sessions to help them understand the system’s features. Consistently examine and refresh settings to stay alert to new dangers and shifts in your business context.
How can I maintain effective cybersecurity over time?
Implement ongoing monitoring for immediate threat identification and response, regularly update the system to incorporate new protections, and establish a feedback loop to evaluate performance and drive continuous improvement.
What is the importance of balancing updates in cybersecurity?
Regular updates are essential for maintaining security, but they must be managed carefully to avoid introducing new vulnerabilities. A balanced approach is crucial for operational stability.




