Introduction
API keys are crucial for securing and managing access to application programming interfaces (APIs). They serve as unique identifiers that authenticate and authorize users or applications to access an API. With the increasing reliance on APIs and the rising number of API breaches, robust API security protocols are more important than ever.
API keys provide secure authentication, granular access control, and scalability for API services. However, managing a multitude of API keys can be challenging, and unsecured keys can lead to security risks. Despite these drawbacks, API keys are indispensable tools for enabling secure integration, implementing rate limiting, and tracking usage.
Organizations must prioritize the proper management and security of API keys to prevent data breaches and safeguard sensitive information.
What is an API Key?
API keys are a cornerstone of web security, functioning as unique identifiers that authenticate and authorize users or applications to access an API. In essence, an API key is like a secret handshake between the software making the request and the API that responds to it. Each key is unique and generated by the API provider, ensuring that only authorized entities can make requests.
The significance of API keys arises from the sensitive data that APIs often handle. Personal and financial information such as contact details, passwords, and banking information are all at risk if API security is compromised. According to recent reports, API breaches have spiked, highlighting the urgent need for robust API security protocols.
A staggering 78% of cybersecurity teams have encountered an API-related incident in the past year, and 81% now prioritize API security more than before.
Proper authentication processes are critical. They're the first line of defense in verifying the identity of users or systems, traditionally involving credentials like usernames and passwords. More sophisticated methods such as Two-Factor Authentication (2FA) add another layer of security, requiring a second verification form alongside the password.
However, it's crucial to distinguish between API keys and tokens. API keys are static, created once through a user interface, and remain the same until rotated. Tokens, on the other hand, represent a user session or specific privileges and are used for a limited time.
Misunderstanding or misusing these can lead to security vulnerabilities. As the digital landscape evolves, it's clear that API security is not just a technical issue but a fundamental business concern that demands attention and understanding from all levels of an organization.
How API Keys Work
API keys serve as a critical security feature in modern software development, facilitating secure interactions between applications. When a request is made to an API, the API key must be included in the request headers or parameters. The server then verifies the validity of this key and, if recognized as legitimate, grants access to the resources being requested.
This process is a cornerstone of authentication, a method of verifying user credentials to restrict access to a system, ensuring only verified individuals can interact with the application.
As the digital landscape evolves and the reliance on web applications surges, APIs have become essential for enabling different software to communicate effectively. However, this increased dependency has also escalated the risks of API breaches, where unauthorized entities might gain access to sensitive data. Recent data reveals that 78% of cybersecurity teams have encountered an API-related security incident within the last year, underscoring the critical need for robust API security measures.
API security protocols, including methods for authentication and authorization, are structured frameworks designed to safeguard data transfer and prevent unauthorized access. While API keys are a static form of authentication, created once and often through a user interface, it is crucial to understand their distinction from tokens, which are temporary and represent user sessions or specific privileges. Clear terminology is vital to avoid confusion, as mixing up API keys and tokens could lead to security lapses.
Given the potential for exposure of personal and financial information through API breaches, ensuring the security of APIs is more critical than ever. Organizations are urged to maintain a full inventory of their APIs, with visibility into which ones return sensitive data. Yet, statistics indicate that only 40% of organizations with a full API inventory have this level of insight.
The gravity of API security is being recognized more widely, with 81% of organizations now prioritizing it more than they did a year ago. This trend highlights the importance of not only implementing robust security protocols but also providing adequate cybersecurity training for employees to reinforce the overall defense against cyber threats.
Types of API Keys
Understanding API Keys and Their Functions
API keys are crucial for managing the interaction between different software applications. Here are the key types of API keys you should know:
-
Public API Keys: These keys are accessible to anyone and enable interaction with public resources or certain limited actions. They're akin to a library's open shelves where select books are available to everyone.
-
Private API Keys: Think of these as the keys to a private vault. They grant comprehensive access to an API's resources and capabilities, and are typically reserved for more in-depth operations. Due to their power and potential for misuse, they're safeguarded with stringent security measures.
-
Rate-Limited API Keys: To prevent misuse or system overload, these keys impose a cap on the number of requests that can be made in a given timeframe. It's like a tap that controls the flow of water to avoid wastage or flooding.
-
Scoped API Keys: These keys are tailored to provide access to specific parts of an API's resources or features, offering granular control over what actions can be performed by a user or application. Imagine having a key that only opens certain drawers of a cabinet, restricting access to only what's necessary.
In the backdrop of these types, recent incidents highlight the importance of careful API key management. For instance, an unexpected request to increase AWS Simple Email Service (SES) sending limits signaled a red flag for a client, uncovering unauthorized activity since the client wasn't using SES. In another case, a critical microservice depending on a third-party API was disrupted due to exceeding the request rate, showcasing the impact of rate-limited APIs.
The rise in API usage has unfortunately also seen a rise in breaches, with 78% of cybersecurity teams reporting API-related incidents over 12 months. This calls for rigorous API management and security measures, considering that only 40% of teams have visibility into which APIs return sensitive data, even though 72% have a full inventory of APIs. As APIs facilitate essential data exchanges in today's digital world, understanding the various types of API keys and implementing robust security practices is more critical than ever.
Best Practices for Using API Keys
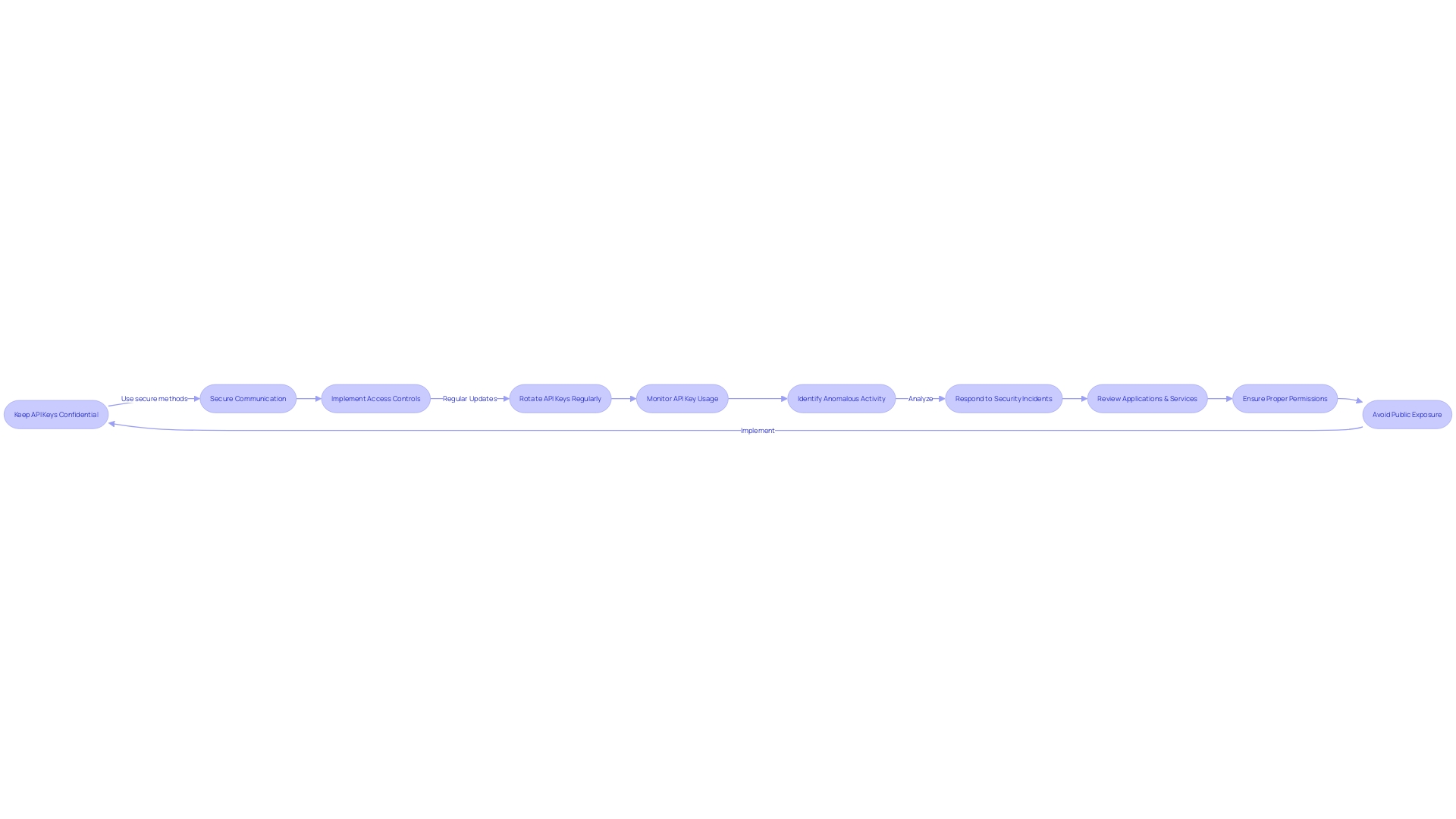
When securing your API keys, it's crucial to adopt a strategy that encapsulates confidentiality, secure communication, access controls, routine changes, and diligent monitoring:
- Keep API Keys Confidential: API keys are akin to digital keys to your house; they must remain undisclosed. Guard them as you would any confidential credential, ensuring they don't get exposed or stored carelessly.
- Use Secure Communication: To prevent your API keys from being intercepted or accessed by unauthorized entities, always opt for secure channels like HTTPS for their transmission.
- Implement Access Controls: Your APIs should have the ability to validate and authorize API keys, restricting access to the API's resources to only those who are permitted.
- Rotate API Keys Regularly: Changing your API keys on a regular basis is a defensive strategy to reduce the risk of key exposure. By generating new keys and deactivating old ones periodically, you maintain a moving target for potential threats.
- Monitor API Key Usage: Vigilant observation of how your API keys are used can alert you to unusual or suspicious behavior, enabling prompt action to avert security risks.
These practices are not an overstatement; they reflect lessons learned from real-world breaches. For instance, in a scenario involving a popular open-source library with over 500,000 AI models, an API compromise had the potential to transform benign models into malicious ones, illustrating the dire consequences of inadequate API security.
Furthermore, with the digital realm's escalation, the role of APIs as communication enablers between software components has become critical. APIs often harbor sensitive data and are hence prime targets for cyber threats. A staggering 78% of cybersecurity teams have encountered an API-related security incident in the past year, emphasizing the need for comprehensive security measures.
In summary, the integrity and security of APIs are paramount. By adopting these practices, organizations can safeguard their digital assets against the rising tide of API breaches, ensuring the trust and safety of their users and the protection of sensitive data.
Security Considerations for API Keys
Maintaining the integrity of API keys is paramount in safeguarding online platforms. Encryption is the first line of defense, ensuring keys are obscured during storage and transit. To illustrate, consider a repository hosting a vast array of AI models and datasets.
With such a repository's API keys compromised, the door opens to manipulate models, transforming them into potential threats. Role-Based Access Control (RBAC) further tightens security by assigning precise access levels, tailoring permissions to the user or application's role. The case of an open-source library, which narrowly avoided disaster after a breach, underscores the necessity of rapid key revocation protocols to curb unauthorized access swiftly.
Effective API Key Management is non-negotiable; it includes meticulous storage, regular key rotation, and vigilant monitoring to quickly spot and rectify security issues. Secure development practices coupled with frequent security assessments are crucial in identifying and remedying API key management vulnerabilities.
The prevalence of digital platforms has elevated APIs to a critical component in software development. However, this has also increased API breaches, highlighting the exposure of sensitive data as a primary concern. With 78% of cybersecurity teams reporting API-related security incidents in the past year, the call for stringent API security practices is louder than ever.
Enterprises are urged to adopt comprehensive API security measures, recognizing that robust protocols and diligent monitoring are indispensable in preventing data breaches and safeguarding sensitive information.
Common Use Cases for API Keys
API keys are essential tools in today's interconnected software landscape, performing a variety of critical functions. They enable secure integration with third-party services, providing a mechanism for seamless data exchange and augmenting applications with additional capabilities. As authentication tokens, API keys confirm the identity and permissions of users or services trying to access an API, safeguarding sensitive information and resources.
Moreover, API keys are fundamental in implementing rate limiting and usage tracking. They help maintain system integrity by preventing abuse and ensuring equitable resource distribution. This is particularly important given recent statistics revealing that 78% of cybersecurity teams have faced API-related security incidents in the past year, underscoring the need for robust usage oversight.
In the realm of monetization, API keys are indispensable for tracking service consumption, enabling accurate billing, and facilitating the creation of revenue-generating API strategies. They also unlock the potential for greater customization and personalization, allowing for tailored experiences that cater to individual user or application preferences.
For instance, integrating an API key from OpenWeatherMap into a Swift application not only grants access to a wealth of weather data but also allows for the personalization of data delivery according to user requirements. Similarly, Kayak's use of the Credential Manager API on Android showcases how API keys can enhance security and user experience, moving away from the vulnerabilities associated with traditional password-based authentication.
APIs, including their keys, have become the backbone of modern applications, with evidence pointing to their growing significance. A Vanson Bourne research indicates that 93% of organizations consider APIs crucial, while 86% acknowledge that their absence would result in operational silos.
This centrality of APIs to business operations and their associated security concerns, as highlighted in the recent spate of breaches, make it clear that the proper management of API keys is not just a technical detail but a business imperative.
Examples of API Key Usage
Discover the versatile roles of API keys across various online services:
-
Enabling photo-sharing capabilities, signing off rights, and viewing functionality on photo-sharing apps.
-
Authenticating and authorizing transactions for users and merchants via payment gateways like PayPal and Stripe.
-
Accessing mapping and geolocation features, such as integrating Google Maps or Mapbox for location-based services.
-
Fetching real-time weather data for applications that provide weather updates and forecasts.
-
Sending emails or notifications through platforms like SendGrid or Mailgun, leveraging API keys for secure communication.
These use cases underscore the critical role of API keys in securing and streamlining digital interactions, from social media to financial transactions.
Benefits and Drawbacks of Using API Keys
API keys serve as a powerful method for securing and managing access to application programming interfaces (APIs), presenting both benefits and challenges:
Benefits:
-
Secure Authentication: They offer a robust mechanism for authenticating user and application identities, ensuring that only authorized parties can tap into API functionalities.
-
Granular Access Control: With API keys, there’s an added layer of precision in access management, enabling the creation of fine-tuned access controls that align with organizational roles and responsibilities.
-
Scalability and Performance: These keys facilitate efficient scaling of API services, adeptly handling an influx of requests without compromising on performance.
Drawbacks:
-
Key Management: Managing a multitude of API keys, especially in large-scale or multi-application environments, can become a sophisticated task requiring diligent oversight.
-
Key Leakage and Security Risks: Unsecured API keys are prone to leaks or hacks, potentially opening doors to unauthorized access and far-reaching security incidents.
-
Lack of Flexibility: The specificity of API keys to particular APIs may restrict adaptability, posing challenges in more advanced or intricate workflow scenarios.
A real-world illustration of the importance of secure authentication is the Kubernetes API gateway, a vital component in safeguarding application entry points from unauthorized entities in dynamic environments like Kubernetes. Similarly, Rapyd, a global payment platform, illustrates the practical application of API keys in securing financial transactions, providing services like Rapyd Collect and Rapyd Disburse to businesses across over 190 countries.
The security implications of API keys are underscored by a JWT example, which encapsulates details about the issuer, the scope of use, and expiration, illustrating the necessity of safeguarding such sensitive information. The urgency of API security is further reinforced by recent trends in API breaches, which have exposed sensitive data and heightened the prioritization of API security among cybersecurity teams, as evidenced by the report stating that 78% of them experienced an API-related security incident in the past year.
To bolster security, it's clear that organizations must not only implement robust API management protocols but also ensure that their teams are well-versed in cybersecurity best practices. With APIs essential to organizational functioning and integration, as 93% of organizations acknowledge, the management and security of API keys are critical to preventing data silos and enhancing overall performance, ultimately leading to improved customer satisfaction and productivity.
References/Citations
Comprehensive API documentation is the linchpin of successful software integration, acting as the user manual that guides developers through the intricacies of an API. Good documentation is akin to a compass that directs users to effectively utilize an API's functionalities, providing clear, structured information on endpoints, request/response examples, authentication methods, and error handling.
When constructing API documentation, it is critical to pinpoint the essential elements that bolster a developer's journey from discovery to mastery. The initial encounter with your API documentation should be enlightening, equipping potential users with the knowledge to swiftly engage with your offerings. Developers seek to comprehend the benefits of your API expeditiously, and your documentation should facilitate a seamless onboarding process, ensuring they can reap these advantages without undue delay.
In the realm of API documentation, the narrative woven around your API is paramount. With a multitude of APIs vying for attention, developers are immediately drawn to understanding the unique value proposition of your API. It's imperative to articulate how your API addresses specific market needs, differentiating it from the plethora of available options.
To enhance the clarity of your documentation, consider the perspective of a novice developer. Terms and concepts should be accessible, with links to glossaries or tooltips to demystify complex jargon. For example, Infobip's API reference thoughtfully includes such links, ensuring that even beginners can navigate the technical landscape with confidence.
Furthermore, your API's status and error codes are not merely technicalities; they are vital channels of communication with your users. By ensuring these messages are informative and maintained, you transform them into a dynamic extension of your documentation.
Insights from industry research accentuate the burgeoning significance of APIs. According to a study by Vanson Bourne, 'The State of APIs, Integration, and Microservices,' a staggering 93% of organizations acknowledge the crucial role of APIs in their operations. Moreover, 86% concur that APIs prevent operational silos, underscoring their integral role in organizational coherence.
The study also reveals that a harmonious integration of APIs and microservices is recognized by 97% of respondents, who agree that such a bundling fosters enhanced performance, heightened customer satisfaction, and elevated productivity.
In the vein of quality management, Peter Drucker's customer-centric view of quality asserts that it is the customer's experience that defines a product's caliber. Taking cues from this philosophy, API documentation should be crafted with the user's satisfaction as the ultimate benchmark. Similarly, Philip Crosby's insights remind us that any friction in using an API is antithetical to quality, propelling the need for documentation that is as frictionless as possible.
In the spirit of community and collaboration, it's worth noting the efforts of companies like Microsoft and SmartBear, who have cultivated active peer-to-peer communities to support technological advancement and ethical practices.
In summary, exceptional API documentation is characterized by its ability to clearly convey the API's value, facilitate user onboarding, maintain clarity for beginners, and provide up-to-date and informative error messages. By adhering to these principles, developers are empowered to integrate and utilize APIs effectively, leading to optimal outcomes for both users and organizations.
Conclusion
In conclusion, API keys are crucial for securing and managing access to APIs. They provide secure authentication, granular access control, and scalability for API services. Despite the challenges of managing multiple keys and the potential for security risks, API keys are indispensable tools for enabling secure integration, implementing rate limiting, and tracking usage.
Organizations must prioritize API key management and security to prevent data breaches and safeguard sensitive information. The increasing reliance on APIs and the rising number of API breaches highlight the urgent need for robust API security protocols. By following best practices such as keeping API keys confidential, using secure communication channels, implementing access controls, regularly rotating keys, and monitoring key usage, organizations can mitigate security risks and protect their digital assets.
API keys offer benefits such as secure authentication, granular access control, and scalability. However, they also have drawbacks, including the challenge of managing multiple keys and the potential for key leakage. Despite these drawbacks, API keys are essential for secure and streamlined digital interactions.
In conclusion, organizations must prioritize API key management and security to prevent data breaches and enhance overall performance. By implementing robust security protocols and providing cybersecurity training, organizations can safeguard their digital assets, protect sensitive information, and ensure the trust and safety of their users.
Frequently Asked Questions
What is an API key?
An API key is a unique identifier used to authenticate and authorize users or applications to access an API. It serves as a secret handshake between the software making the request and the API responding to it, ensuring that only authorized entities can interact with the API.
Why are API keys important for security?
API keys are significant for security because they help protect sensitive data that APIs often handle, such as personal and financial information. With an increase in API breaches, robust API security protocols are necessary to prevent unauthorized access and data exposure.
How do API keys work?
API keys are included in the request headers or parameters when a request is made to an API. The server verifies the validity of the key and grants access to the requested resources if the key is recognized as legitimate.
What is the difference between API keys and tokens?
API keys are static and remain the same until they are rotated, whereas tokens are temporary and represent a user session or specific privileges. Tokens are often used for a limited time.
What are the different types of API keys?
The different types of API keys include:
- Public API Keys: Accessible by anyone for limited actions or public resources.
- Private API Keys: Grant comprehensive access and are highly secured.
- Rate-Limited API Keys: Impose a limit on the number of requests within a timeframe.
- Scoped API Keys: Provide access to specific parts of an API's resources or features.
What are the best practices for using API keys?
The best practices include keeping API keys confidential, using secure communication (like HTTPS), implementing access controls, rotating API keys regularly, and monitoring API key usage for suspicious behavior.
What are the security considerations for API keys?
Security considerations for API keys involve encryption during storage and transit, Role-Based Access Control (RBAC) for precise access levels, rapid key revocation protocols, meticulous storage, regular key rotation, and vigilant monitoring.
What are common use cases for API keys?
API keys are used for secure integration with third-party services, rate limiting, usage tracking, monetization through service consumption tracking, and enhancing customization and personalization in various applications.
What are the benefits and drawbacks of using API keys?
Benefits include secure authentication, granular access control, and scalability. Drawbacks encompass the complexity of key management, the risk of key leakage and security breaches, and the lack of flexibility in certain scenarios.
What real-world examples illustrate the use of API keys?
Examples include enabling photo-sharing in apps, authenticating transactions via payment gateways, accessing mapping and geolocation services, fetching weather data, and sending emails or notifications through various platforms.




