Introduction
In today's digital landscape, upholding strict codebase standards is not just a matter of preference, but a critical requirement. Consistent and clean coding practices lead to software that is easier to understand, maintain, and more secure. The importance of this is exemplified by institutions like M&T Bank, operating in the high-risk banking industry, where adherence to Clean Code standards is pivotal in maintaining software performance and ensuring compliance with stringent security regulations.
The use of open-source code has also increased, offering efficiency and speed in building software, but with heightened security risks. To achieve a secure and efficient development process, safe coding practices and a focus on developer ecosystems are key strategies. By embracing these practices, programmers can enhance their skills, contribute to a more reliable digital environment, and become more competent in their field.
Investing in code quality and security is not just beneficial but essential for the sustainability of our digital world.
Why Enforce Codebase Standards?
Maintaining rigorous codebase guidelines is not only a matter of preference, but also an essential necessity in the current digital environment. Consistent and clean coding practices lead to applications that are not only easier to understand and maintain but also significantly more secure. This importance is underlined when considering the stakes for institutions like M&T Bank, which operates in the high-risk banking industry. In order to maintain performance and ensure compliance with stringent regulations, the bank's commitment to Clean Code standards is crucial in the face of the challenges of a digital transformation.
Moreover, as the software development ecosystem evolves, the use of open-source code has increased, offering efficiency and speed in building software. However, as emphasized by Mike McGuire from Synopsys Software Integrity Group, the convenience of open-source components comes with increased safety hazards. It's vital for organizations to be well-informed about the contents of their code to mitigate these risks effectively.
To achieve such a secure and efficient development process, Google's experience suggests two key strategies: safe coding practices to prevent bugs, and a focus on developer ecosystems to reduce defects on a large scale. Avoiding typical vulnerabilities, like injection or memory safety problems, demands developers to be watchful with every line of code, particularly in intricate codebases.
By embracing these practices, programmers can enhance their skills, contribute to a more secure and reliable digital environment, and ultimately become more competent and respected in their field. As we keep progressing through the intricacies of software development, it's evident that dedicating resources to code quality and protecting information is not only advantageous but crucial for the endurance of our digital realm.
Benefits of Adhering to Coding Standards
Adopting established guidelines is not only a matter of protocol; it's about becoming proficient in the language of cooperation and efficiency that sets professional programmers apart in the corporate realm. Meticulous code formatting and organization streamline the development process, making the codebase more accessible and improving teamwork. This approach to programming is a vital component in sectors like banking, where companies such as M&T Bank have implemented Clean Code standards to enhance application maintainability and security amidst a digital transformation. In the realm of software development, where new technologies like generative AI are swiftly being embraced, guidelines for writing ensure a high level of code quality and regulatory compliance, essential for safeguarding sensitive data and transactions.
The Ford Foundation's initiative to develop a new video accessibility plugin for the WordPress community highlights the necessity for coding guidelines that can adapt to the rapid growth in content creation and the varied requirements of a changing audience. By following such guidelines, developers can decrease bugs, minimize vulnerabilities, and promote a culture of clear communication and efficient collaboration. According to Michael Ameling, Senior Vice President at SAP, generative AI not only accelerates development but enhances code quality, making the development process more efficient.
Coding standards are the compass that guides developers to success in the dynamic realm of corporate application development. Consistent programming styles facilitate collaboration, while proper indentation and comprehensive commenting enhance readability and maintainability. These practices are crucial for creating programs that not only function efficiently but also meet the rigorous expectations of industry experts. Additionally, as programming becomes more intertwined with AI tools like GitHub Copilot, which greatly enhances productivity for developers of all levels, the significance of a well-structured and comprehensible codebase becomes even more evident. The pursuit of clean code, as defined by industry leaders, is a journey towards writing code that not only meets the needs of the present but also stands the test of time, benefiting entire development teams.
Industry-Accepted Standards for Secure Coding
In the changing environment of software development, following secure coding practices is not only a suggestion, it is essential. These standards serve as a guiding light, leading developers towards creating resilient code that can withstand the onslaught of threats. For institutions like M&T Bank, with over a century and a half of trusted financial services, the digital era presents both opportunities and challenges. While they maneuver through the digital transformation, the stakes are high; a single vulnerability can prompt a chain reaction of breaches, financial loss, and lasting reputational damage.
To mitigate these risks, the development community is coming together, as evidenced by the whitepaper co-sealed by ten U.S. and international partners. This collaborative effort, which now encompasses contributions from eight additional countries and organizations, highlights a collective commitment to shift the security paradigm.
Secure programming principles are solidified within the broader concept of 'Secure by Design,' a proactive stance in software development. It's about aligning cybersecurity objectives across an organization's fabric, ensuring that every line of code contributes to a robust defense. As the whitepaper suggests, it's not about ticking boxes, but about understanding risk and making informed decisions.
The three 'Secure by Design' principles offer a framework to support these secure programming standards. They are not just abstract concepts but are supported by tangible evidence in the form of artifacts. These artifacts tell a compelling story of a company's dedication to secure programming practices and are part of a broader narrative that also includes pattern detection over time and trend analysis. By analyzing these trends, we can determine which entities are progressing towards security excellence and which ones need to enhance their quality improvement programs.
This collective endeavor aligns with the increasing demand for transparency and accountability in development, emphasized by the request for a Bill of Materials (BOM) and precautions against risks introduced by AI coding tools. With the Open Source Security and Risk Analysis (OSSRA) report highlighting the critical question, 'Do you know what's in your code?', the industry acknowledges the urgency of this issue in the context of the burgeoning use of open source and AI-generated code.
In the end, the objective is to establish a secure codebase that not only meets strict industry regulations but also showcases the utmost quality benchmarks. And for organizations like M&T Bank, this is not just about maintaining software; it's about upholding a legacy of trust and excellence in an all-digital world.
Key Areas to Focus on in Secure Coding Practices
Crafting a secure codebase is a multifaceted endeavor, essential in safeguarding digital identities and sensitive data. At the forefront of this challenge, M&T Bank, with its 165-year legacy, has pioneered the adoption of Clean Code standards across its development teams. This proactive stance is a testament to the industry's shift towards digital banking, where the stakes for protection are at their highest due to the sensitive nature of financial data.
The digital transformation has fueled the rapid introduction of technology, heightening the importance of robust access control measures. It's not just about creating complex passwords, but also about managing them effectively to prevent incidents similar to the LinkedIn and Yahoo data breaches. The development culture within software teams plays a critical role here, as continuous education on protection best practices and staying abreast of the latest threats are non-negotiable.
One cannot overlook the management of secrets such as API keys and database credentials, which if compromised, can lead to severe consequences. Tools for secrets detection have become indispensable in a developer's arsenal to prevent unauthorized access or exposure.
In addition, the latest enhancements made by Microsoft to its cryptographic library, SymCrypt, integrating post-quantum algorithms, demonstrate the industry's movement towards encryption protocols that are resistant to future advancements. Such measures are crucial as they lay the foundation for safe digital experiences, ensuring that every online transaction, storage, or communication is underpinned by unassailable protocols.
In summary, the adoption of secure coding practices is not just about adhering to rules, but about fostering a mindset of protection within development teams, supported by regular education and the utilization of state-of-the-art cryptographic standards. This comprehensive approach is what allows institutions like M&T Bank to maintain the integrity of their operations and the trust of their customers in an ever-evolving digital landscape.
Security by Design and Threat Modeling
Incorporating principles of protection into the development process from the beginning is crucial for establishing a safe codebase. Focusing on design, a proactive approach, emphasizes the importance of addressing safety concerns as early as possible. This method allows developers to anticipate and neutralize threats before they manifest into vulnerabilities. For instance, Node.js developers can follow a set of best practices that provide a simplified and condensed view of implementing secure by design principles within their projects. These best practices include conducting threat modeling to map out and address potential safety concerns.
Threat modeling, in essence, serves as a structured approach for identifying and prioritizing potential threats to a system, and determining the value that potential mitigations would have in reducing or neutralizing those threats. It involves a clear understanding of the system's architecture, including key components and functionalities, to pinpoint attack surfaces. For example, in assessing the Home Assistant architecture, the focus was directed at remote attack surfaces, such as the web application's frontend and backend APIs, while noting that local surfaces like IoT interactions could be examined later.
Open source supply chain protection, as discussed in a presentation on Google's efforts in the field, is a contemporary area where secure by design principles are critically important. The talk highlighted the enduring development of supply chain protection and how contemporary methods are influenced by the experiences of the past. The notion of 'commitment' in cryptographic exchanges, as described in Blum's paper on coin flipping by telephone, can be seen as a metaphor for secure design: locking down predictions (or code) to prevent cheating (or vulnerabilities).
Indeed, the industry is moving towards a consensus on the importance of secure by design principles. A whitepaper, co-sealed by ten U.S. and international partners, has received feedback from a wide spectrum of stakeholders, including software manufacturers, customers, non-profits, and government agencies. This feedback has been crucial in shaping the 'secure by design' discussion, highlighting the collective responsibility for safety and the need for evidence in the form of artifacts to demonstrate commitment to these principles. The shared goal is to move beyond reliance on any single artifact and instead build a compelling tale of safety through a collection of practices and evidence.
Access Control and Password Management
Understanding the interplay between access control and password management is fundamental to maintaining a secure codebase. Access control systems are the gatekeepers of digital resources, ensuring that only those with appropriate authorization can interact with sensitive data and functions. This is crucial in the context of a world where our digital identities can be as important as our physical ones. The alarming rate of data breaches, such as those at LinkedIn and Yahoo, underscores the vulnerability of digital systems to weak passwords, which often serve as the first line of defense against unauthorized access.
Effective password management is about more than just creating complex passwords; it's about safeguarding the keys to our digital kingdom. It's a lesson painfully observed from incidents like the GoDaddy breach, where insufficient password protection can lead to catastrophic results. By enforcing robust password policies and secure storage practices, developers play a critical role in protecting user data from those who might exploit weak passwords to gain unauthorized access.
Moreover, as we approach a significant number of global elections, the integrity of digital platforms takes on a heightened level of importance. The top practices outlined by experts, including ongoing safety training and the administration of digital secrets, are not just recommendations but necessities for ensuring the protection of applications. With over 1,000 practitioners specializing in the study of access control and password management, it's evident that these practices are not just theoretical but are actively shaping the way we protect our digital spaces.
In essence, a secure codebase depends on a combination of vigilant access control and diligent password management. By implementing these protective measures, developers can ensure that their applications stand up to the evolving threats of the digital landscape, thereby maintaining the trust and privacy of their users.
Error Handling and Logging
Error handling and logging are foundational elements for securing and stabilizing a codebase. Skillful error management not only safeguards against the inadvertent exposure of sensitive information but also ensures a smooth user experience by deftly managing program exceptions. Meanwhile, diligent logging is crucial for identifying and resolving issues quickly, enhancing the overall safety and strength of the application.
Efficient error handling and recording are more than just recommended; they are crucial for program safety and protection. As the software supply chain becomes increasingly reliant on open source components, which make up over 80% of today's global software infrastructure, the integration of reliable error handling and comprehensive logging becomes paramount. This is particularly accurate in a landscape where open source governance models are still developing and often lack definite standards for reliability and safety.
In the realm of coding, the preference for 'happy path' programming, where error handling is often neglected, can lead to significant vulnerabilities. Acknowledging this, industry experts emphasize two central questions developers should ask before logging information: 'Is this log entry exposing sensitive data?' and 'Does this log provide the necessary insight for debugging without compromising safety?' Addressing these questions can substantially reduce the risk of information leaks and enhance the code's defense against cyberattacks.
Additionally, programming language safety, which encompasses assurances such as type and memory safety offered by languages and their libraries, is acknowledged as an essential factor in both security and safety of code. With the growing occurrence of cyberattacks on critical infrastructure and the incorporation of software in life-critical systems, such as autonomous vehicles, the necessity for secure programming practices has never been more pressing. In response to this challenge, organizations are now advocating for standards that require developers to 'act reasonably' in the face of diverse cyber threat profiles, striving to balance flexibility with the need for clear guidelines.
Google's experience with developer ecosystems suggests that emphasizing secure programming techniques is both achievable and successful in significantly reducing common defect rates across large-scale applications. Preventing bugs through safe coding reduces the burden on developers to avoid each potential vulnerability, ultimately resulting in more secure applications. With regulations such as the Cyber Resilience Act (CRA) looming on the horizon, set to take effect in 2027, the emphasis on secure-by-design principles and robust supply chain safeguards becomes increasingly critical. The software industry, particularly open source, must now navigate the intricate challenge of aligning practices and thoroughly documenting approaches to fulfill these emerging cybersecurity guidelines.
System Configuration and Patch Management
To build a truly secure codebase, it's essential to focus on robust system configuration and diligent patch management. This requires hardening the computing environment to minimize potential attack vectors and protecting critical configuration files. For example, M&T Bank, a prominent commercial bank, encountered the challenge of adjusting to a digital-first customer experience, which required the implementation of strict measures to ensure the protection of sensitive data and transactions. Their goal was to implement Clean Code standards throughout the organization to guarantee the durability and protection of their applications in light of these new requirements.
Similarly, Jenkins, a widely used automation server, demonstrates the importance of security practices, as its prominence in the market underscores the vast impact potential vulnerabilities could have. In this context, patch management plays a crucial role by keeping program dependencies and libraries up-to-date, thereby mitigating the risks associated with known vulnerabilities.
Recent reports from the Enduring Security Framework (ESF) have highlighted an increase in cyberattacks targeting supply chains for programs. These attacks exploit design flaws, incorporate vulnerable third-party components, or introduce malicious code during development. To tackle these concerns, the ESF report highlights the administration of open-source programs and programs bills of materials (SBOMs), with the goal of enhancing the transparency of program management cycles and offering risk information to organizations.
In accordance with these best practices, Infrastructure as Code (IaC) Scanning and Policy as Code are crucial tools for maintaining safety measures. These methods allow for automated checks against predefined policies, ensuring that infrastructure deployments are secure by design. According to Christophe Limpalair, the creator of Cyber, constructing secure applications is a widespread challenge for companies, which is why automation and adherence to recommended approaches in configuration and patch management are crucial for minimizing risks and upholding compliance with security guidelines.
Cryptographic Practices and Data Protection
Comprehending the complexities of secure programming is essential, particularly when contemplating the susceptibility of software to cyber threats. Cryptographic protocols and data protection measures are the cornerstone of a robust codebase standard. For example, employing End-to-End Encryption (E2EE) safeguards data in transit, ensuring only the intended recipients can decrypt and access the information. This is critical in preventing unauthorized interception or alteration of sensitive data.
When discussing secure programming best practices, it's crucial to emphasize the importance of SQL, a widely used language for database management. The importance of secure programming to prevent SQL injection attacks is highlighted by SQL's capability to execute CRUD operations.
Furthermore, a case study demonstrates the importance of encrypting data by utilizing the public keys of all participants, particularly in real-time applications, to uphold both protection and efficiency. The advent of post-quantum cryptography, as seen with Microsoft's integration of ML-KEM into SymCrypt, points to the industry's forward-thinking approach to evolving cyber threats.
'Continual training in the area of safety, highlighted by the growing emphasis on protection within institutions, is essential for keeping development teams well-informed about present dangers and ready to execute secure programming methodologies.'. Moreover, giving priority to data protection is not just about safeguarding information but also about preserving an enterprise's reputation and financial stability, as data breaches can result in substantial losses.
Industry experts agree that a proactive approach to secure coding, such as the principles advocated by Google for preventing bugs through Safe Coding, can result in a substantial reduction of common defects. In-toto's standardized metadata schemas and the SLSA framework embody collaborative endeavors to enhance the supply chain integrity, guaranteeing the origin and integrity of artifacts.
Statistical data shows a worrying 21% rise in incidents affecting GitHub users in 2023, emphasizing the pressing requirement for integrating safety at the beginning of the software development lifecycle, as advocated by the DevSecOps model. This approach is crucial in mitigating vulnerabilities like Repojacking, which posed significant threats to the GitHub community in the previous year. Highlighting cryptographic practices and data protection is not only a technical necessity but a foundational aspect of maintaining trust and safeguarding in our digital world.
Input Validation and Output Encoding
Input validation and output encoding are critical components in maintaining a secure codebase, providing a strong defense against pervasive threats such as SQL injection and cross-site scripting (XSS). By rigorously validating user-supplied data, we ensure that only sanitized information enters our systems, protecting the integrity of our databases and applications. Output encoding is equally vital, as it safeguards end-users from malicious scripts that could be executed in their browsers.
In the realm of web application protection, these practices are not just recommendations but essential standards. For instance, during a penetration test of Moodle, a widely-used learning management system, the startling discovery that users with the 'trainer' role could execute XSS attacks by design underscored the importance of strict output encoding.
Moreover, the extensive utilization of open-source, pre-trained AI models introduces a novel domain. These models, while facilitating rapid deployment and innovation, also introduce unique vulnerabilities that must be addressed through stringent validation and encoding practices.
Recognizing the significance of these vulnerabilities, experts like Tanya Janca, a specialist in application protection, stress the importance of focusing on the root causes of safety concerns. Janca's insights reveal that preventing such problems in our applications is paramount to ensuring a secure digital environment.
Furthermore, as AI-assisted applications become more prevalent, developers and professionals must stay watchful. By implementing robust input validation and data sanitization, as recommended by experts in the field, we can mitigate potential risks and enhance the protection level of our systems.
In conclusion, embracing input validation and output encoding is not only about adhering to best practices; it's about recognizing the evolving landscape of software security and taking proactive steps to safeguard our digital infrastructure against emerging threats. These measures are crucial in establishing and maintaining secure codebase guidelines.
Enforcing Coding Standards with Automated Tools
The traditional approach to maintaining programming guidelines through manual code reviews is similar to searching for a needle in a haystack—it's exhaustive and not immune to human error. Nevertheless, the emergence of automated software development guideline tools is transforming this procedure. These advanced systems analyze codebases with accuracy, identify deviations, and provide corrective suggestions, thereby enhancing the enforcement of coding guidelines.
In the domain of development, code reviews are crucial. They ensure code follows established guidelines before deployment. Yet, manual reviews are arduous, sifting through code line-by-line, a process that's not just slow but also prone to oversights due to fatigue. Organizations like M&T Bank, with its storied 165-year history in the financial sector, have embraced the necessity for automated tools to maintain Clean Code standards, crucial for software maintainability and performance amidst stringent safety and regulatory demands.
The value of these automated tools is underscored by recent advances in AI, such as the integration of large language models (LLMs) in the code generation process. These AI-driven tools have shown a significant boost in developer productivity across the board, with the most notable gains observed among junior developers. GitHub's research highlights that AI suggestions during programming not only reduce task time and cognitive load but also enhance product quality, enjoyment, and learning. With the rapid transition of the banking industry to digital platforms, ensuring the adoption of automated tools for enforcing efficient and protected coding practices becomes crucial to mitigate potential risks, including breaches in security and damage to reputation.
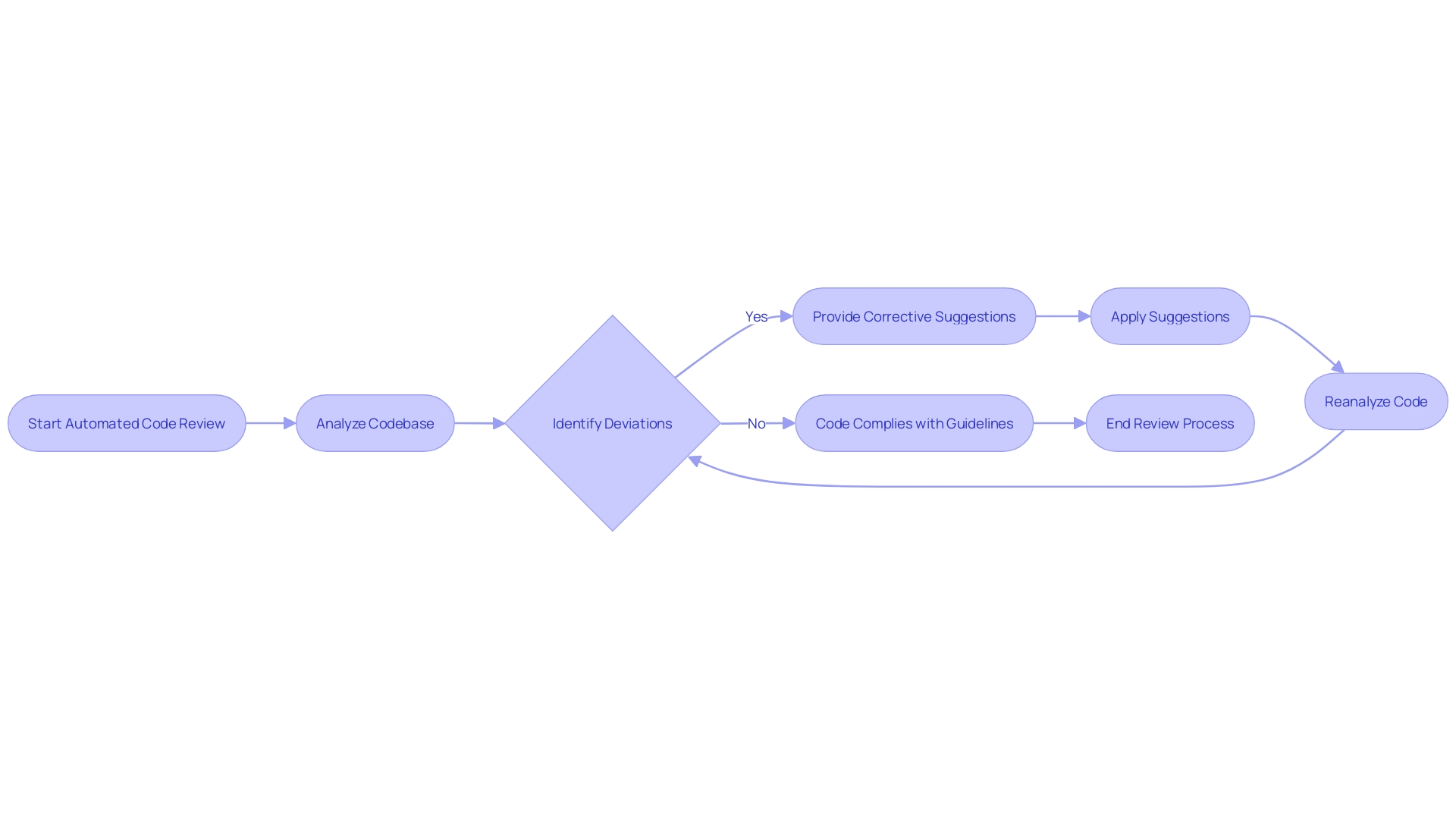
Using Automated Static Analysis for Compliance
Implementing guidelines and ensuring security through automated static analysis tools has become increasingly crucial for organizations undergoing digital transformation. One example is M&T Bank, which has over 21,000 employees and has been serving the community since 1856. As the banking sector faces the challenges of an all-digital customer experience, the need for impeccable code quality and compliance is paramount to safeguard sensitive data and transactions. Automated static analysis provides an answer to these challenges by examining the codebase for vulnerabilities and deviations from established coding norms.
By incorporating such tools into the development cycle, businesses like M&T Bank can proactively detect and rectify problems, which is crucial in an industry where technology issues can be financially devastating and harmful to reputation. Indeed, the implementation of organization-wide 'Clean Code' guidelines is crucial to guarantee software maintainability and performance.
Global compliance testing, as discussed by experts like Christophe Limpalair, is a strategic imperative in digital transformation. It confirms that digital products are safe and compliant, facilitating innovation within regulatory frameworks. Automated static analysis plays a critical role in this process by enabling businesses to navigate the complexities of regulations across various industries, thereby enhancing competitive advantage.
As stated by industry observers, understanding the broader aspect of a system's quality is crucial before integrating Static Code Analysis (SCA) tools. Such tools not only contribute to code security but also to the quality culture within teams and companies. They help tailor system behavior to operate optimally and reliably, as per the requirements of the environment.
In conclusion, automated static analysis is not just a compliance exercise; it is a proactive measure that supports digital innovation and competitive differentiation in a secure and regulated manner.
Best Practices for Implementing Coding Standards
For developers and teams looking to improve their codebase, adopting coding guidelines is not only a technical decision but also a strategic one. A prime example is M&T Bank, which, amidst the digital transformation of the banking industry, recognized the need for Clean Code guidelines to maintain high software performance and compliance. Similarly, in the realm of business intelligence, Pentaho's robust data handling capabilities revealed the importance of having a standardized method for data integration and management to ensure consistent and high-quality outcomes.
In order to attain such elevated expectations, accurate code documentation is crucial. It should serve as a comprehensive manual, detailing the software's functionality and offering a project overview, which is especially beneficial to new contributors and users. An eloquent example is TypeScript, which celebrated its 10-year anniversary with the release of TypeScript 4.9, demonstrating the longevity that comes with a commitment to clear and well-documented codebases.
Moreover, code reviews are an essential component of the process, designed to improve code quality, identify bugs, and confirm the adherence to best practices. By establishing and adhering to a consistent set of guidelines for programming, such as naming conventions and formatting styles, the review process becomes more efficient and less prone to errors.
Statistics further underscore the significance of these practices: AI pair-programming tools like GitHub Copilot have markedly improved developer productivity across all levels. Such tools offer real-time code recommendations, decreasing task time and mental effort while improving product quality and the overall experience of writing code.
In essence, effective implementation of programming guidelines depends on explicit criteria, uniform documentation, and frequent code evaluations. As technology advances and the need for secure, high-quality code increases, these practices are now essential for developing maintainable, readable, and reliable applications.
Challenges and Solutions in Enforcing Coding Standards
Implementing guidelines is crucial in the face of evolving security threats and stringent regulatory demands, especially in industries handling sensitive data, such as banking. M&T Bank, with its rich history and commitment to community-focused banking, has faced the digital transformation head-on. By establishing guidelines for Clean Code, they have addressed the issue of preserving software quality and adherence, which is crucial in averting breaches and guaranteeing seamless operations.
Automated Testing, including Unit Testing and Test Driven Development (TDD), is integral to enforcing coding standards. Automated Testing, which encompasses a variety of tests without manual intervention, and Unit Testing, which focuses on the smallest code segments, can significantly enhance code quality and security.
AI and machine learning are reshaping the software development landscape. Tools like GitHub Copilot and ChatGPT have experienced rapid adoption, demonstrating the potential of AI in code generation. However, the code review process still relies on outdated tools and manual labor, which can be slow and prone to errors.
Enforcing coding standards requires a multifaceted approach that addresses potential resistance and educates developers about best practices. It's a journey that involves fostering a culture of code quality and leveraging both cutting-edge AI technologies and proven testing methodologies to maintain a secure and efficient codebase.
Conclusion
Upholding strict codebase standards is crucial in today's digital landscape. Clean coding practices lead to software that is easier to understand, maintain, and more secure. Embracing coding standards enhances collaboration, streamlines development processes, and ensures regulatory compliance.
Secure coding practices protect sensitive data and transactions. Access control, password management, error handling, and logging mitigate vulnerabilities. Robust system configuration, patch management, and encryption protocols enhance codebase security.
Input validation and output encoding prevent common threats.
Automated tools enforce coding standards, improving code quality and security. Automated static analysis detects and rectifies issues, while unit testing and test-driven development enhance code quality.
Implementing coding standards requires clear guidelines, consistent documentation, and regular code reviews. Proper code documentation serves as a comprehensive manual, while code reviews improve quality and adherence to best practices. Automated tools enhance productivity and ensure compliance.
Embracing coding standards fosters a culture of code quality, enhances collaboration, and maximizes efficiency. By investing in code quality and security, developers contribute to a more secure digital environment.
In conclusion, adhering to coding standards is essential for software performance, regulatory compliance, and data protection. By embracing these practices and utilizing automated tools, developers achieve efficiency and productivity while maintaining a secure codebase.
Take your code quality and security to the next level with our automated tools!
Frequently Asked Questions
Why are codebase standards important?
Maintaining rigorous codebase standards is essential for ensuring applications are easier to understand, maintain, and secure. This is particularly crucial in high-risk industries, such as banking, where compliance with regulations is critical.
What impact does open-source code have on coding standards?
While open-source code can enhance efficiency and speed in software development, it also introduces safety hazards. Organizations must be aware of the components in their code to mitigate potential risks effectively.
What are the key strategies to ensure secure coding practices?
Two key strategies suggested by Google are adopting safe coding practices to prevent bugs and focusing on developer ecosystems to reduce defects on a larger scale.
How do coding standards benefit developers?
Adhering to coding standards helps developers enhance their skills, fosters collaboration, and contributes to a more secure digital environment, ultimately increasing their competence and respect in the field.
What are the key areas to focus on in secure coding practices?
Key areas include access control and password management, error handling and logging, system configuration and patch management, cryptographic practices, and input validation and output encoding.
What is 'Secure by Design'?
'Secure by Design' is a proactive approach in software development that integrates security principles into the development process from the outset, minimizing vulnerabilities and enhancing overall security.
How can automated tools help enforce coding standards?
Automated tools analyze codebases for deviations from established guidelines, providing corrective suggestions and enhancing the overall enforcement of coding standards, thus reducing the potential for human error during manual reviews.
What role does automated static analysis play in compliance?
Automated static analysis tools help organizations detect vulnerabilities and ensure adherence to coding standards, which is vital for maintaining software quality and meeting regulatory requirements.
How can organizations manage access control and password security effectively?
Implementing robust password policies, secure storage practices, and ongoing training for developers are essential for safeguarding user data and preventing unauthorized access.
Why is error handling and logging crucial in coding standards?
Efficient error handling prevents the exposure of sensitive information and ensures a smooth user experience, while diligent logging is necessary for quickly identifying and resolving issues.
What challenges do organizations face in enforcing coding standards?
Organizations may encounter resistance to change, the complexity of integrating new tools, and the need for continuous education on best practices. Adopting a multifaceted approach can help address these challenges.
How can teams effectively implement coding standards?
Effective implementation involves clear documentation, regular code reviews, and adopting consistent guidelines for programming styles. Utilizing automated tools can also streamline this process and enhance code quality.




