Introduction
Security by design is a fundamental principle that transcends the traditional approach to software development. It involves embedding security within the very blueprint of an application's architecture, rather than treating it as an afterthought. In this article, we will explore the various aspects of secure software engineering, from threat modeling and risk assessment to password management, access control, and more.
By adopting a security-first mindset and leveraging robust practices, developers can ensure the creation of resilient, reliable, and trustworthy systems. Join us as we delve into the world of software security and discover how it can elevate the efficiency and productivity of your development process.
Security by Design
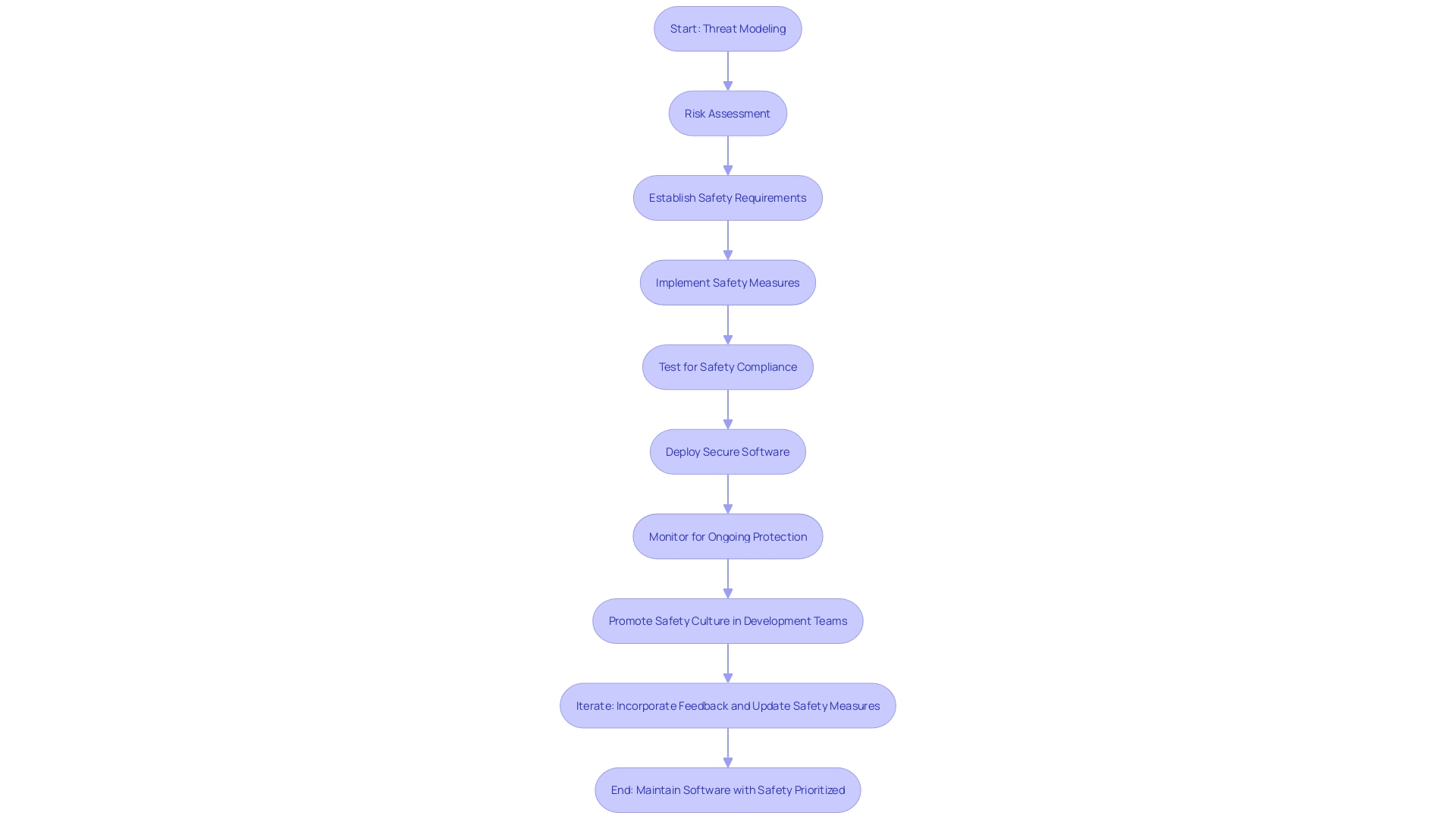
Incorporating safety into the fundamental structure of the application goes beyond the conventional neglect of security in the process of developing software. It's not just a collection of high-minded principles, but a practical workflow that starts with threat modeling, risk assessment, and the establishment of safety requirements. Consider it akin to constructing a building with a robust foundation rather than retrofitting the walls with steel after they've been erected.
In this approach, the assurance of protection isn't a separate feature but an intrinsic characteristic of the software, similar to its usability or performance. As such, engineers are encouraged to consider the aspect of ongoing protection, not as a one-time checklist item. The most innovative products of the next decade will be those acknowledging that traditional protective measures are outdated.
Research in the area of industrial control systems has highlighted a common refrain from engineers: they're willing to take into account safety during the design phase if only they knew how. It's about converting abstract concepts related to safety into actionable measures, thus aiding in the development of intrinsically secure infrastructures.
The significance of this change in perspective is strengthened by the alarming data that highlight the crucial nature of engineering for safeguarding software. Cyber threats are becoming more advanced, requiring high-level development measures to safeguard information, ensure adherence, and uphold customer confidence. Any failure in engineering safeguards can result in severe outcomes, such as monetary damages from data breaches, theft of confidential information, disturbances in operations, and legal repercussions.
Moreover, the discourse regarding design with an emphasis on safety is developing, as observed in recent deliberations at global cybersecurity conferences and evaluations of the legal responsibilities of smart device makers. The emerging consensus is that ensuring the safety and reliability of software development is fundamental to the business's integrity and customer trust, and there's a clear expectation for companies to embed protection into every phase of the Software Development Life Cycle (SDLC).
In conclusion, protection by design is not an optional extra but an essential component of modern software development. It necessitates a cultural change within development teams, placing the protection of information at the core of their processes and mindset, thus guaranteeing the creation of systems that are resilient, reliable, and trustworthy.
Password Management and Authentication
Securing a codebase extends beyond just writing secure code; it involves ensuring that access to the code itself is protected through robust password management and authentication strategies. Enforcing strong password policies that mandate a mix of complexity, length, and regular updates is fundamental. However, password policies alone aren’t enough. Multi-factor authentication (MFA) has emerged as an indispensable security measure, adding an additional verification step that significantly diminishes the risk of unauthorized access.
With the alarming rise in information breaches, the stakes for securing digital identities have never been higher. Incidents like the LinkedIn Data Breach and the Yahoo Data Breach highlight the vulnerabilities that weak passwords introduce. Statistics indicate that the consequences of such breaches are not only confined to information theft but also involve significant monetary losses and enduring harm to brand reputation.
Best practices suggest using password hashing as a secure method of password storage. Unlike encryption, hashing is a one-way process that transforms the password into a unique fixed-size string, making it practically impossible to reverse-engineer. This is vital as developers increasingly rely on open-source packages, which, according to the Python Package Index, can constitute up to 90% of the code in production environments. A lone flaw in these widely distributed packages could have extensive consequences.
In the face of these challenges, the industry is moving towards passwordless authentication. Industry experts predict that by 2025, most applications will adopt passkeys—a more secure and user-friendly alternative to passwords. This shift is driven by the recognition of passkeys' fraud-preventative benefits and their ease of use across various sectors, including finance and healthcare.
As developers and organizations strive to safeguard their applications, it's essential to heed expert advice and embrace these evolving authentication technologies. Every step taken towards stronger password management and authentication is a stride towards securing not just the codebase, but also the trust of users who rely on the integrity of digital systems.
Access Control and Authorization
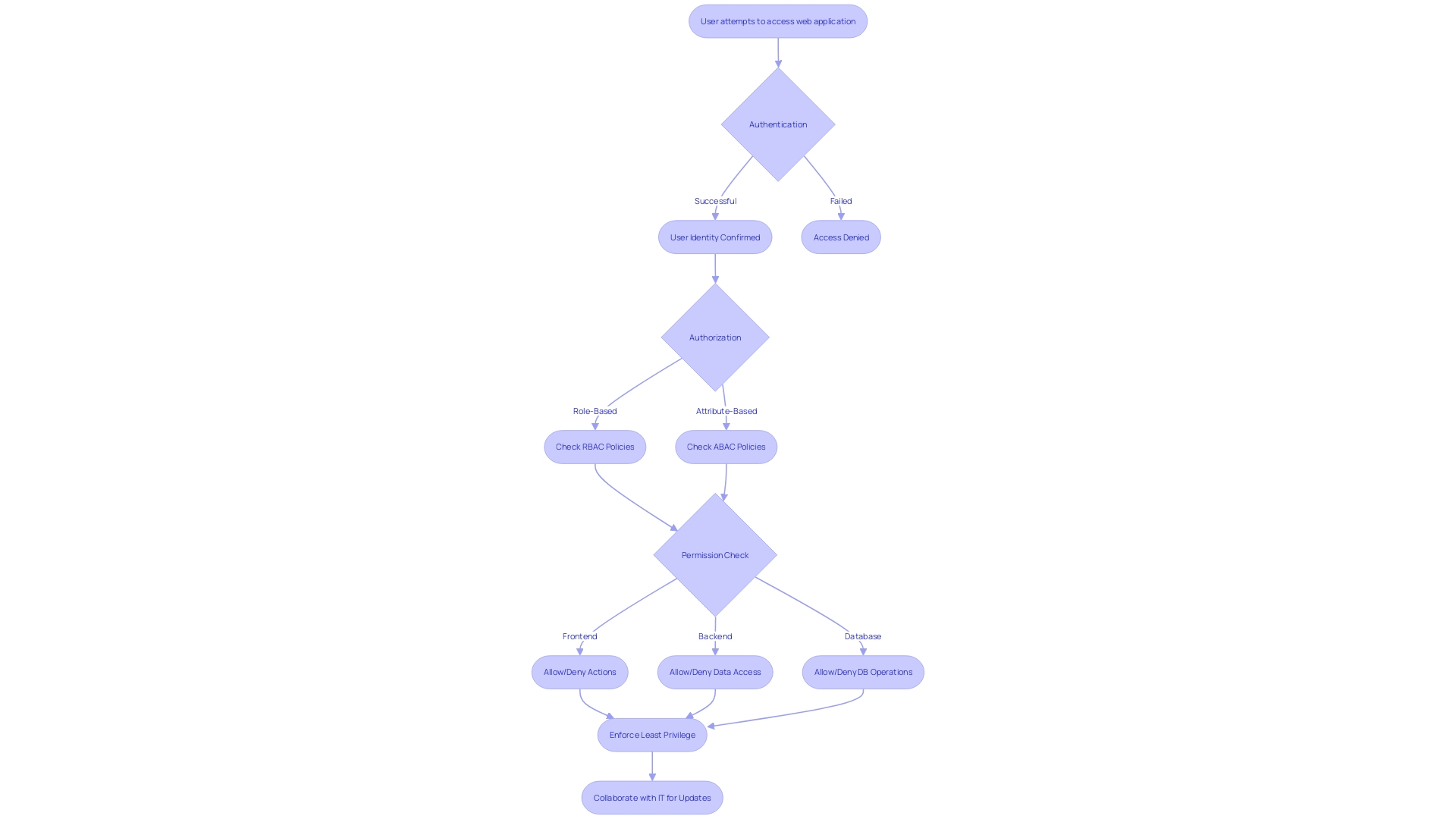
Ensuring secure access to a web application's resources is a complex challenge that involves determining who can perform specific actions and access specific information. Implementing robust access control and authorization mechanisms is not just about keeping unwanted guests out; it's about fine-tuning the level of access each user has to align with their role and need-to-know basis.
For instance, in the case of a web application, permissions are examined at various points, such as the frontend, backend, and database. This is crucial in making sure that, for example, only admins have the ability to ban user accounts, while regular users might be able to read content but are restricted from altering it. Adopting Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC) systems, and adhering to the principle of least privilege, are effective ways to achieve this balance.
In application development today, the distinction between authentication—verifying the identity of users as they log in—and authorization—determining what authenticated users are allowed to do—is vital. To ensure a secure and seamless user experience, both elements must work harmoniously. Drawing parallels from real life, authentication can be likened to showing your ticket at the entrance of a theme park, while authorization relates to the activities you're permitted to engage in once inside.
Recent industry efforts highlight the importance of scalable, interoperable access control solutions. The Connectivity Standards Alliance's introduction of Aliro aims to establish a common protocol and credential for mobile devices and readers, emphasizing simplicity, flexibility, and security. This initiative reflects the growing need for access control systems that not only safeguard data and functionality but also support a wide range of applications and architectures.
The effectiveness of access control systems is not solely dependent on the technology itself but also on the policies, user training, and auditing that support it. Collaboration with key stakeholders, such as IT departments, is crucial to maintain the integrity of these systems and to keep them up-to-date with the latest advancements. Ultimately, a secure web application is one that not only prevents unauthorized access but also ensures that each user operates within the bounds of the necessary privileges.
Error Handling and Logging
Understanding the criticality of error handling and logging in software development cannot be overstated. It's a line of defense that protects against information leakage, which attackers could exploit. A robust error handling strategy ensures that when things go wrong, they do so gracefully, without offering clues that could lead to a system's compromise. Logging, on the other hand, provides a historical record of events that can be invaluable when diagnosing and addressing incidents.
When logging information, it's crucial to assess the sensitivity of the data being recorded. Logging credentials, user identifiers, or any potentially identifying information like client IP addresses or usernames can turn logs from an asset to a liability. As emphasized in a significant post titled 'The top application protection tool is education,' the importance of developer consciousness regarding safety is of utmost importance, particularly taking into account the substantial return on investment it provides, even on a restricted budget.
Recent cybersecurity incidents in 2023, involving the exposure of sensitive information such as API keys and passwords in plain text, highlight the risks associated with insufficient protection measures in the software supply chain. These incidents showcase that from the initial code writing in an IDE to the deployment on servers, the importance of safety must be taken into account at every step.
Moreover, Google's experience suggests that focusing on developer ecosystems to prevent common defects can be practical and effective. By embracing secure coding practices, developers can decrease the probability of implementation-level flaws, such as injection or memory safety vulnerabilities, which are difficult to evade in large, intricate codebases.
In essence, error handling and logging are not only about recording what goes wrong but also about ensuring that the information captured does not become a treasure trove for malicious actors. Developers must continuously educate themselves on best practices and be vigilant about the data they log, always questioning its necessity and potential risks.
System Configuration and Patch Management
Ensuring the protection of system configurations and the prompt application of patches are pivotal elements in safeguarding code. It's crucial to regularly update systems and dependencies to incorporate the latest enhancements for protection. Implementing secure configuration practices, such as disabling unnecessary services and enforcing strong network configurations, is also crucial in minimizing vulnerabilities.
For instance, M&T Bank, with its extensive history in community-focused banking, has faced the digital transformation of the banking sector head-on. This shift requires strict measures of protection and compliance to safeguard sensitive data and transactions. To maintain quality and compliance, M&T Bank has established Clean Code standards across the organization, emphasizing the importance of maintaining and updating their codebase.
Similarly, the revelation of a Cache Poisoning Attack on the npm registryâa critical JavaScript package ecosystemâby Lupin & Holmes, highlights the vulnerability of software supply chains and the importance of attentive protective measures.
Security experts, such as those exploring Linux systems, prioritize identifying privilege boundaries to pinpoint potential privilege escalation vulnerabilities. This approach is crucial for comprehending the protection landscape of a system and for ensuring that configurations are firmly secured.
Furthermore, the latest PCI DSS 4.0.1 update showcases the changing landscape of technology and threats, highlighting the necessity for updated protection measures. Similarly, the September 2024 Patch Tuesday prediction emphasizes the significance of patch administration in preserving system performance and safeguarding.
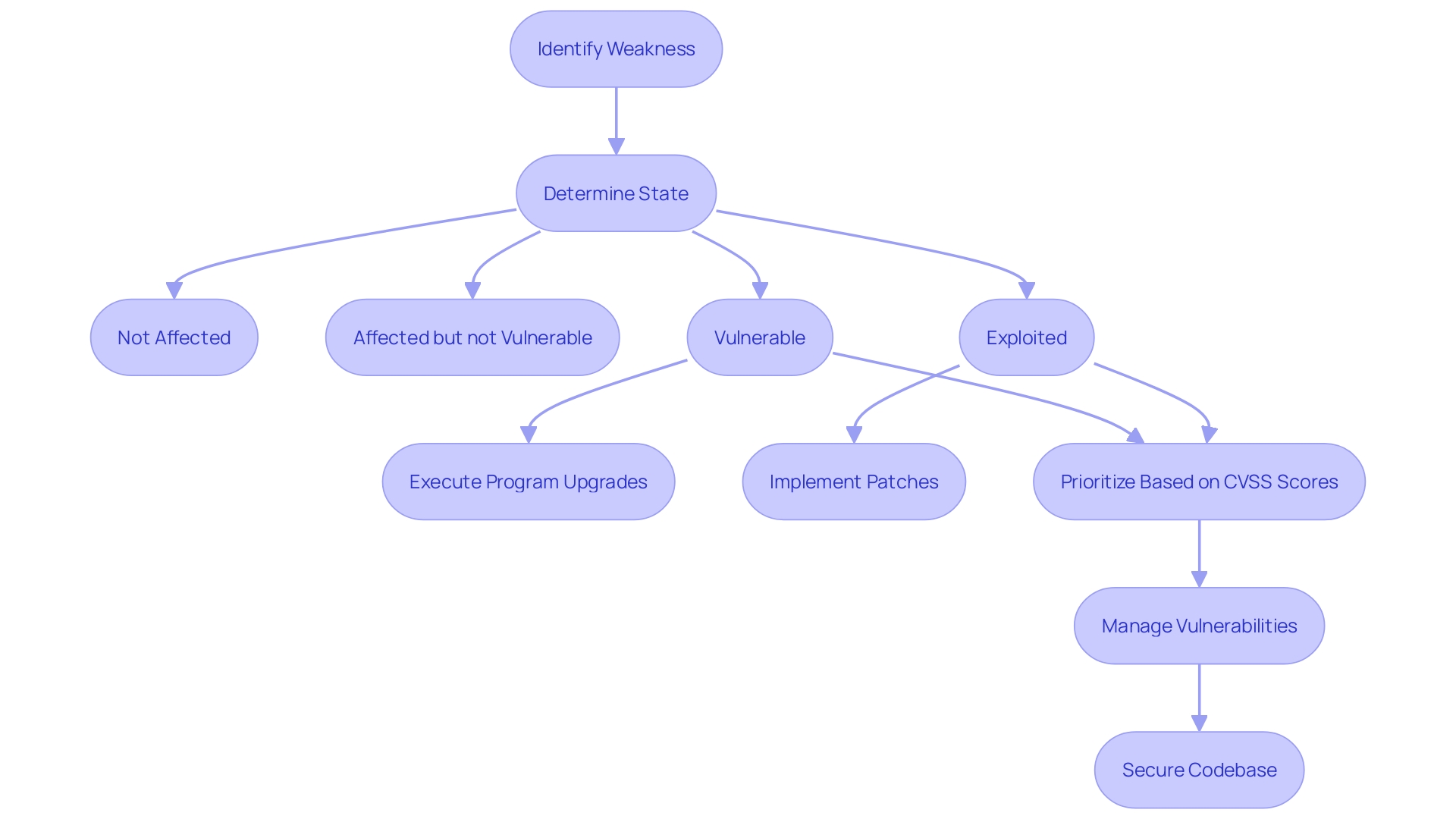
These observations are mirrored in the broader cybersecurity community, where the agreement is that implementing program updates, particularly those tackling vulnerabilities, greatly minimizes risk. A thorough grasp of the states of flaws in computer programs â whether they are unaffected, impacted but not susceptible, exposed, or exploited â is crucial in assessing the real risk and necessary measures for upholding a secure codebase.
Threat Modeling and Risk Assessment
Building a strong software product starts with clearly defining privacy and protection requirements. These requirements are influenced by factors such as data types, known threats, established best practices, regulatory standards, and insights from previous incidents. To effectively address these concerns, developers employ threat modeling and risk assessment. This strategic approach involves identifying potential threats and assessing the risk they pose in terms of likelihood and impact.
For example, analyzing real-life situations, like a penetration test of Moodle, unveils the intricacy and possible implications of widely-utilized systems. Similarly, understanding the intricacies of threat actors' intents, whether malicious or part of adversarial simulations, is crucial for effective threat identification. This knowledge drives the development of threat models and the prioritization of protective measures.
The Security Development Lifecycle (SDL) is a practical framework adopted by many organizations. It emphasizes continuous training in cybersecurity basics and secure development practices, including the application of AI in software testing. This ensures that as the product evolves, so do its safety measures, adapting to new functionalities and threats.
Recent industry statistics underscore the urgency of these efforts, revealing that only a small percentage of organizations feel fully confident in their ability to defend against cyberattacks. The cybersecurity workforce, currently at 4.7 million professionals, continuously adjusts strategies to safeguard against vulnerabilities, which is crucial for maintaining company data integrity. With the average compensation for information protection analysts at $102,600 per year in 2021, it's evident that the stakes are high, and the requirement for capable professionals is constantly increasing.
Considering this, it's clear that ensuring the safety of programs is not only a technical obstacle but also an essential business factor. According to a specialist, the present condition of software safety is critical because of the intricacy of code and the extensive number of external dependencies. It's essential to go beyond traditional security measures to ensure comprehensive protection in today's interconnected digital landscape.
Cryptographic Practices and Key Management
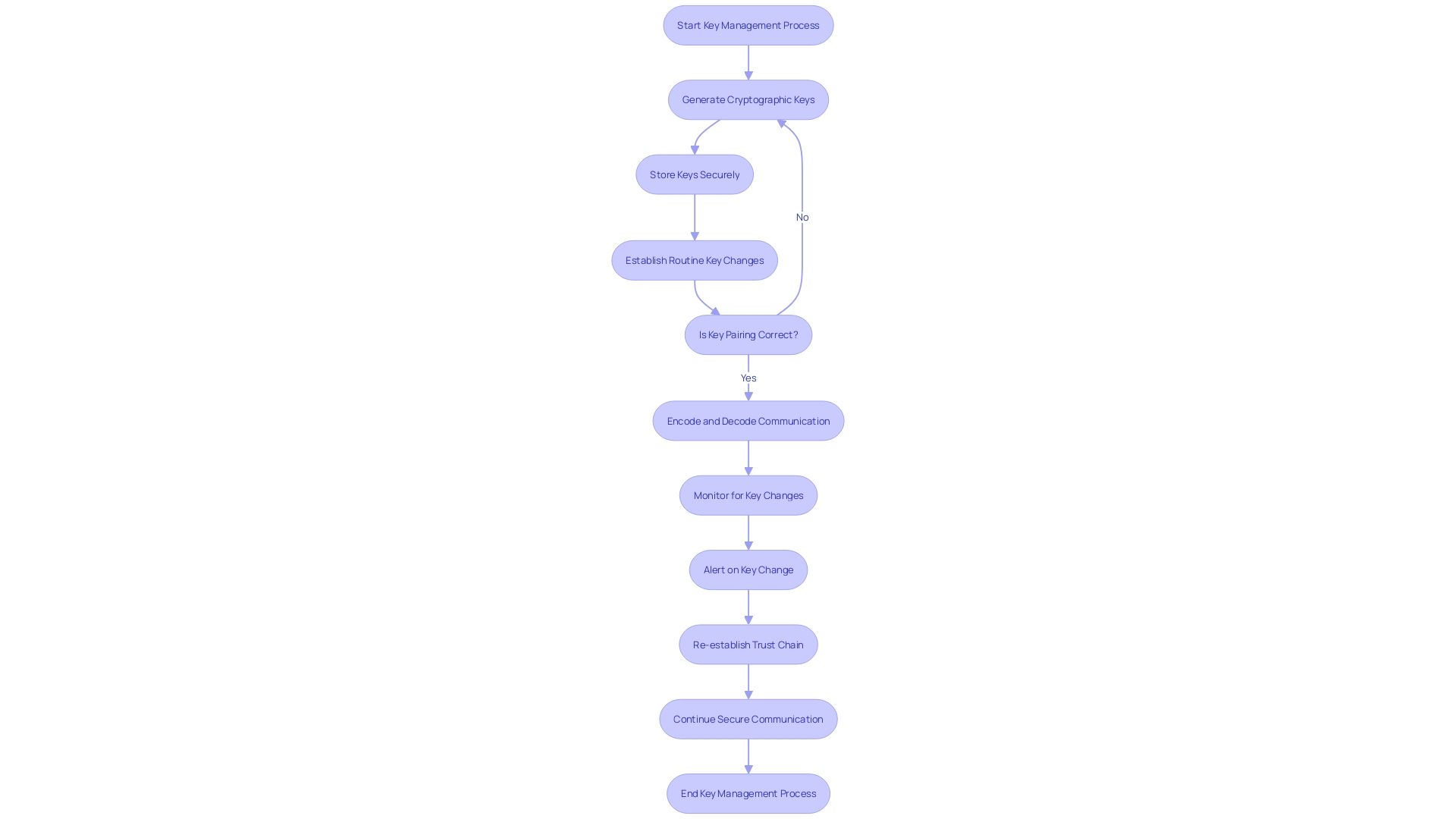
Effective cryptography and key management are vital for safeguarding sensitive information throughout its lifecycle, playing a crucial role in protecting sensitive information. The encryption of information, accomplished by transforming it into a intricate code, is crucial in preventing unauthorized access. Nevertheless, besides encryption, the principles of key management systems (KMS) are crucial in the architecture of protection.
Key management involves not only the generation, storage, and rotation of keys but also ensuring they are isolated from the systems that use them. This principle of isolation safeguards keys in the event of a system compromise. In addition, strict access controls are imperative, permitting only authorized individuals to handle these cryptographic keys. Moreover, a KMS must demonstrate tamper resistance, maintaining key integrity even under unauthorized attempts of alteration.
An incident involving our client and AWS highlights the importance of robust key management. The client was targeted in an attack aimed to misuse Amazon's Simple Email Service (SES), illustrating the potential risks if cryptographic keys fall into the wrong hands. Attackers often seek to exploit services like SES for spam or phishing campaigns, emphasizing the need for stringent key management practices.
In the end, ensuring the safeguarding of information is not just about the encryption procedure but also entails a thorough approach encompassing the safety of physical hardware, administrative controls, and the protection of logical software applications. The guidance of specialists holds accurate: safeguarding is not only about putting in place safeguards but guaranteeing the capability to restore and recover information, emphasizing the essential character of a dependable and protected KMS.
Input Validation and Output Encoding
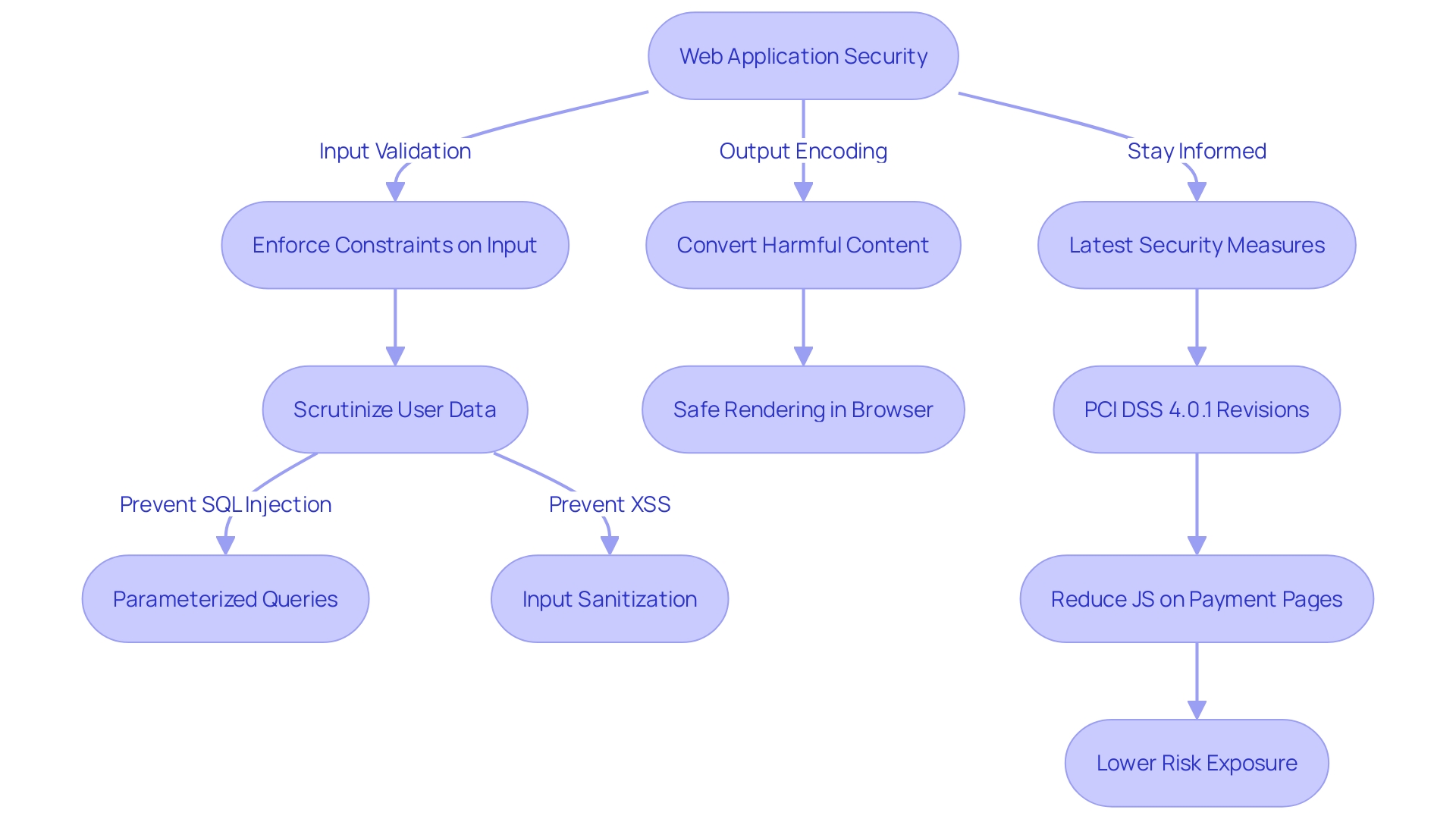
Ensuring the security of web applications is paramount, particularly when it comes to managing user input and system output. Effective input validation serves as a crucial barrier against threats such as SQL injection and cross-site scripting (XSS) by scrutinizing user-supplied information. This process includes enforcing appropriate constraints on input information, like disallowing PHP comments in formulas, as highlighted in examples from the validation.php file in widespread use. Additionally, output encoding is a complementary defense strategy, converting potentially harmful content into a safe format before it is rendered by a web browser, thus mitigating the risk of malicious code execution.
In real-world scenarios, the importance of meticulous validation and encoding practices cannot be overstated. Consider the risks associated with poorly implemented Web Application Firewall (WAF) rules, which can inadvertently lead to Response Filter Denial of Service (RFDoS) incidents, crippling an e-commerce website's functionality by blocking legitimate user comments that resemble sensitive data patterns.
With the constantly changing landscape of cyber threats, staying informed on the latest measures and vulnerabilities is crucial. For example, the recent revisions to the Payment Card Industry Data Security Standard (PCI DSS) version 4.0.1 demonstrate an increased emphasis on updating digital protection. Moreover, perspectives from industry leaders highlight the necessity for a collective transition towards enhanced construction practices, diminishing dependencies, and fortifying the security of the codebase.
Understanding the nuances of these vulnerabilities allows developers to fortify their applications effectively. By integrating robust validation and encoding techniques, teams can build resilience into their software, ensuring that only validated, expected input is processed, and safeguarding against the display of harmful data. This strategic approach to safeguarding is a cornerstone of maintaining a secure, trustworthy, and efficient codebase.
Database Security and Query Practices
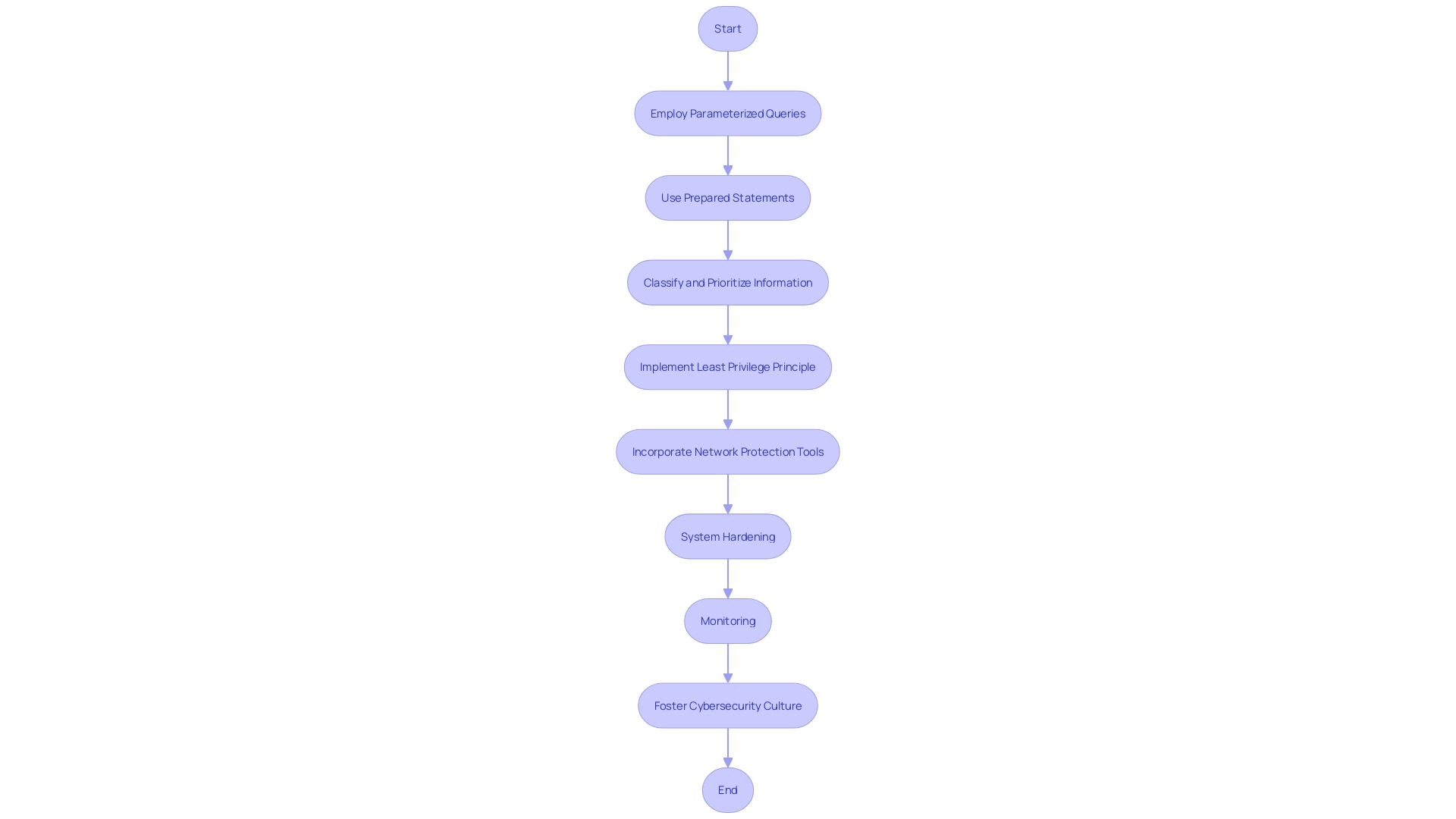
Ensuring database protection is a crucial aspect of constructing a robust codebase, especially in sectors like banking where the risks are extremely high. For example, M&T Bank, with its rich history and large workforce, has encountered the challenge of digitizing its customer experience while satisfying stringent safety and regulatory requirements. To safeguard sensitive information against SQL injection attacks, developers must employ parameterized queries and prepared statements, which effectively neutralize malicious input.
A comprehensive approach to database security also involves meticulous information classification and prioritization. By understanding and classifying the sensitivity of stored information, organizations can focus on securing the most critical data with robust measures such as encryption and stringent access controls. This not only aligns with legal requirements but also emphasizes the protection of financial and personally identifiable information.
In the realm of secure user access, the principle of least privilege is paramount. Users should be granted the minimum level of access necessary for their job functions, avoiding the risks associated with excessive privileges. This strategy is critical in mitigating insider threats, including those stemming from negligence or misuse.
Furthermore, with the increase of cyber threats, according to the Ponemon Institute and IBM Security, the average expense of breaches has reached a record peak. It is clear that database protection programs must extend beyond the database itself to encompass the entire data management system and associated applications. The addition of open-source tools can improve the defense against external threats, offering a robust network protection, system hardening, and vigilant monitoring.
Lastly, it's essential to recognize that vulnerability management goes beyond prioritization. Organizations must foster a positive cybersecurity culture to prevent breaches that could lead to catastrophic consequences. As the banking industry and other sectors continue to evolve digitally, the foundation of a secure codebase lies in the rigorous adherence to database safeguarding best practices. This commitment safeguards the integrity and confidentiality of data, ensuring trust and reliability for customers and stakeholders alike.
File and Resource Management
Ensuring the safety of a codebase involves diligent management of files and resources. Developers must rigorously inspect and cleanse file uploads, barring the execution of harmful files. By establishing robust file permissions and restricting access strictly to verified users, the likelihood of unauthorized manipulation plummets. Continual examination and immediate removal of unnecessary resources further strengthen the posture.
Take the case of DICOM, a ubiquitous medical imaging protocol. Security researchers discovered that DICOM files could harbor polyglot payloads—files that are currently valid in multiple formats, thus serving as a potent tool for cyber attackers. This underscored the necessity for thorough validation of file uploads in healthcare systems and beyond.
This point was driven home by the recent cybersecurity incidents of 2023, where sensitive credentials were discovered in plaintext, illustrating the dire consequences of poor resource management in supply chains for computer programs. The supply chain for programs covers all aspects of software creation, from the integrated development environment (IDE) to deployment, emphasizing the significance of comprehensive security measures.
Furthermore, the 2024 OSSRA report emphasizes the prevalence of open-source components in software, making it imperative for organizations to maintain a Software Bill of Materials (SBOM). This inventory provides crucial insights into the components used, their versions, and associated risks, stressing the need for regular updates to mitigate vulnerabilities.
Integrating Safety as Code (SaC) into development workflows, where safety policies and checks are codified and automatically executed, represents a proactive approach to safeguarding a codebase. This aligns with the 'shift left' philosophy, addressing safety early in the software development life cycle (SDLC) and integrating it into each stage.
Lastly, a study on the safety of Visual Studio Code at DEF CON 31 emphasized that most vulnerabilities in code editors and their plugins require some form of user interaction. These findings accentuate the importance of a vigilant development environment, where even seemingly benign actions like opening a project could trigger an exploit.
In conclusion, secure file and resource management are cornerstones of a resilient codebase, demanding persistent vigilance and a multifaceted strategy of validation, restriction, monitoring, and education to thwart potential threats.
Session Management and Token Security
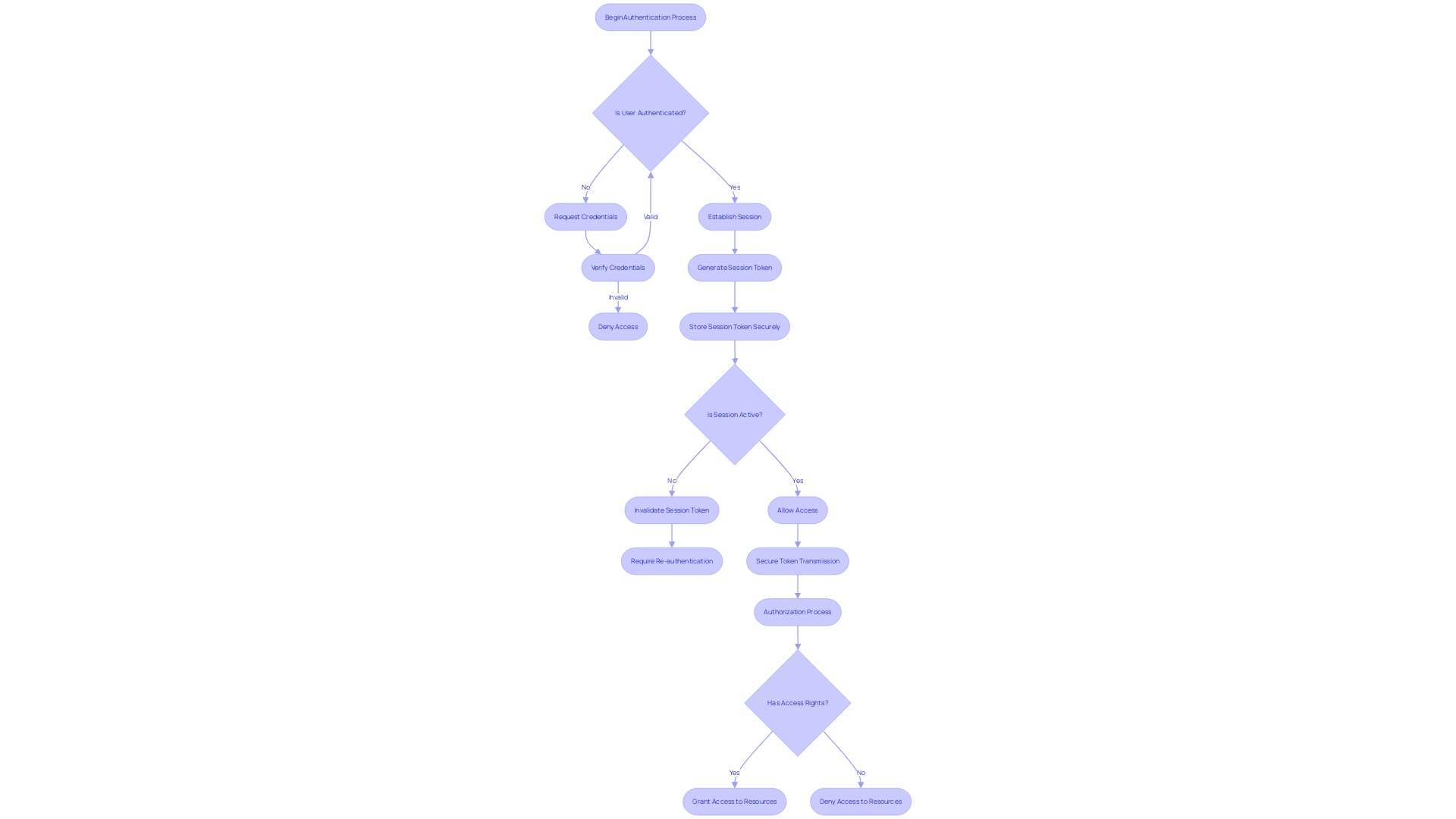
To fortify web applications against security breaches, it's essential to establish robust session management and token security measures. This is foundational in preventing session hijacking, where unauthorized users attempt to take over legitimate sessions. A pivotal step in this defense strategy is the generation, storage, and timely invalidation of session tokens. They must be created with a high degree of randomness and stored securely to withstand intrusion attempts. Upon a user's logout or after a predefined period of inactivity, these tokens should be promptly invalidated to nullify any potential misuse.
Furthermore, the secure transmission of session tokens and sensitive information across the network is non-negotiable. Implementing secure transport protocols like HTTPS is a critical layer of defense, ensuring that data in transit is encrypted and thus, safeguarded from eavesdroppers and man-in-the-middle attacks.
In the broader context of digital commerce and software solutions, where companies strive to offer secure yet seamless user experiences across various platforms, robust authentication mechanisms are indispensable. It becomes a balancing act between enhancing safety and maintaining user convenience. JavaScript-based Single Page Applications (Spas), which often incorporate numerous libraries and dependencies, can inadvertently introduce vulnerabilities. The intricacy of these ecosystems emphasizes the significance of watchful precautions in the face of potential threats.
The digital landscape today is fraught with risks, evidenced by alarming statistics such as the 236.1 million ransomware attacks reported globally in the first half of 2022. Such figures highlight the importance for businesses, especially SMBs that may lack in-house expertise, to embrace comprehensive protection strategies. With 67% of SMBs acknowledging their unpreparedness for data breaches, the rise in collaboration with Managed Service Providers marks a proactive shift towards enhanced cybersecurity measures.
In brief, the intersection of appropriate authentication, reliable session management, and conscientious token safeguarding practices are indispensable elements of a secure web application. They serve as the linchpins of trust and reliability in a digital ecosystem where user confidence and regulatory compliance are paramount.
Leveraging Security Frameworks and Libraries
When it comes to safeguarding your application's codebase, the adoption of sturdy frameworks and libraries plays a vital role. These established resources are the outcome of thorough testing and refinement, providing developers with dependable features such as authentication protocols, encryption methods, and access management controls. One such example includes next.js, a technology stack that can be strengthened with tests using simple commands like npx create-next-app@latest and installation of protection SDKs. By integrating these elements into your development process, you not only safeguard your application against vulnerabilities but also streamline the task of coding secure features from scratch.
It's crucial to recognize that in our digital age, where cyber threats are ever-evolving, the importance of a secure codebase cannot be overstated. As emphasized in recent news, developments like ML-KEMâthe post-quantum standard integrated into Microsoft's SymCryptâare evidence of the industry's dedication to enhancing protocols to withstand even threats at the quantum level.
Furthermore, by following the principles of Code-based Security (SaC) and DevSecOps, which includes integrating safety checks within the development pipeline, has been demonstrated to be a budget-friendly approach. Not only does it improve the posture of applications, but it also aligns with the modern need for automation and early integration of measures throughout the Software Development Life Cycle (SDLC).
Industry statistics further underscore the criticality of maintaining a Software Bill of Materials (SBOM) to manage open source components within your code. Such vigilance is essential given that popular open source elements are frequently targeted by attackers. Moreover, the combination of test results across various tools can greatly decrease the time to fix important vulnerabilities, as almost 75% of organizations state that it takes them weeks to a month to deal with these concerns.
Ultimately, the goal is to foster a development ecosystem characterized by safe coding practices, which, as experts from Google suggest, can dramatically reduce common defects across vast codebases handled by numerous developers. By integrating proven frameworks and libraries, and adopting a mindset focused on safeguarding, we establish a basis for applications that are not only functionally strong but also resistant against the numerous risks that exist in the digital realm.
Quality Assurance and Security Testing
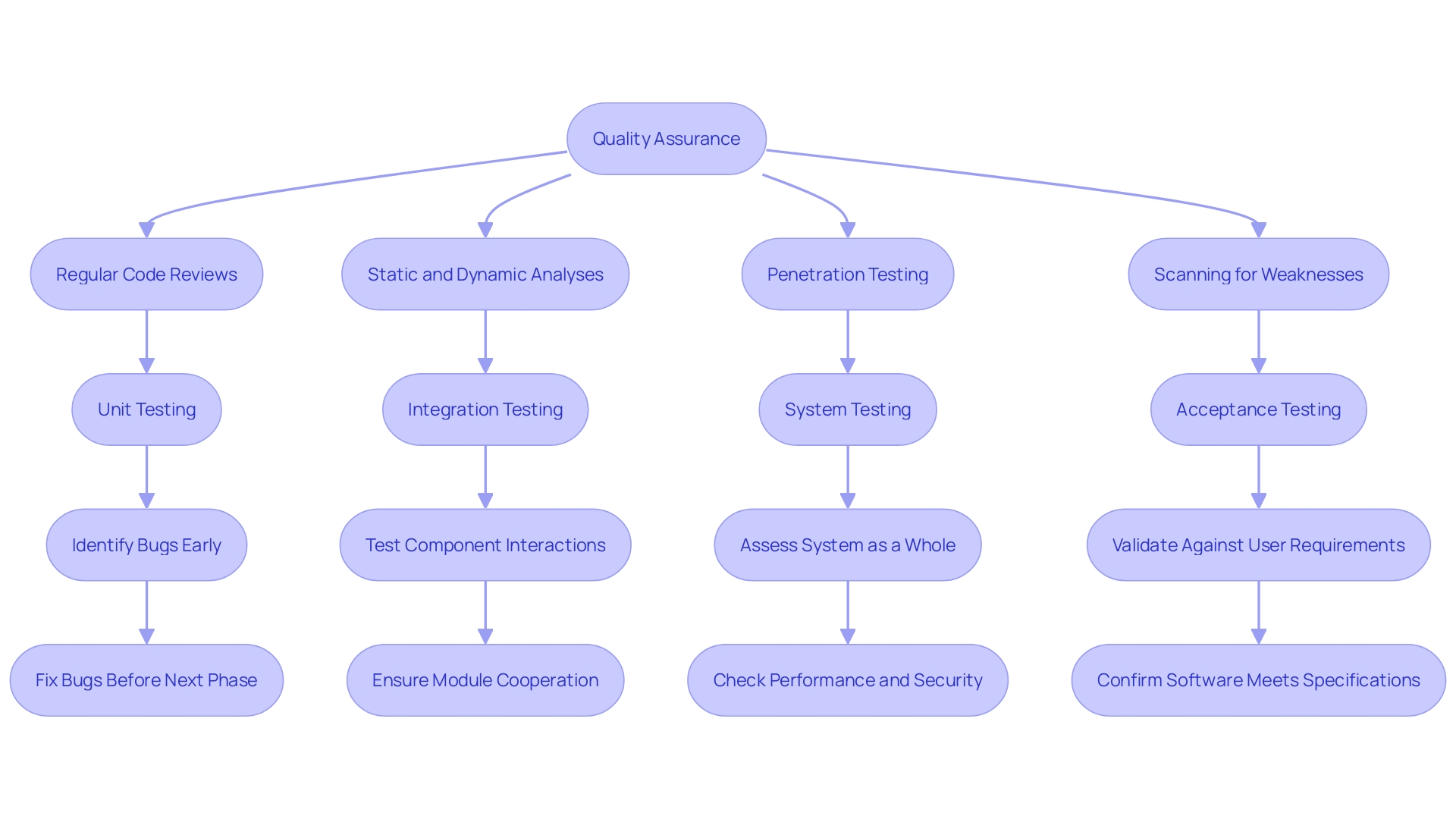
To uphold a safe codebase and follow strict standards, it is crucial to enforce a thorough quality assurance and testing regimen. Banking institutions like M&T Bank, with its impressive 165-year history, have demonstrated the critical importance of such measures in an industry marked by rapid digital transformation and sensitive data handling. Regular code reviews, static and dynamic analyses are foundational practices in identifying weaknesses early on. These proactive measures are enhanced by penetration testing and scanning for weaknesses, which serve as crucial techniques in revealing and reducing potential risks before they can be exploited.
In alignment with insights from Google's experience, prioritizing developer ecosystems significantly reduces the rate of defects in application development. Emphasizing on safe coding practices can help avoid common defects, such as injection or memory safety vulnerabilities, which are otherwise difficult to eliminate in complex codebases. Additionally, the implementation of Clean Code principles by the banking sector emphasizes the importance of developing strong procedures to ensure maintainability, performance, and protection.
Recent reports, like Veracode's State of Software Safety and ASIS International's findings on access control, further emphasize the significance of rigorous protection measures. These studies highlight the repercussions of disregarding weaknesses in computer programs, which can result in extensive effects throughout institutions and industries. As the field advances, the implementation of sophisticated metrics such as the CVSS v3.1, which encompasses additional metrics for a more detailed evaluation of weaknesses, becomes increasingly valuable for prioritizing and overseeing efforts effectively.
Ultimately, the integration of comprehensive testing strategies, consisting of unit, integration, system, and acceptance testing, ensures not only the robustness and security of applications but also enhances customer satisfaction and fortifies an organization's reputation in the market.
Vulnerability Management and Patching
To maintain a secure codebase, a strong weakness management process is essential. Recognizing the different states a flaw can assume is crucial: not affected, affected but not vulnerable, vulnerable, and exploited. These states indicate that the presence of a flaw does not necessarily imply that a system is at risk; instead, it is the context of use that determines susceptibility. Successful administration depends on comprehending these subtleties and executing program upgrades, especially for fixes targeting vulnerabilities.
In the past, as emphasized in NISTIR 5153, the emphasis was on limiting applications usage and ensuring appropriate configuration and monitoring. Over the course of time, the act of implementing patches became recognized as a recommended approach, based on the idea that updating software mitigates the potential harm caused by weaknesses in its protection. However, simply knowing a code is vulnerable doesn't equate to it being exploited, and the industry has started to pay more attention to exploitation rates.
The Common Scoring System (CVSS) helps organizations by providing a numerical score that reflects the severity of security weaknesses. With CVSS v3.1, additional metrics such as Safety, Automatable, Recovery, Value Density, and Provider Urgency have been introduced to enhance the granularity of assessments. These scores, encompassing Base, Threat, and Environmental factors, are instrumental in prioritizing vulnerability management, ensuring that developers can safeguard their code against the most critical risks first.
Education and Training for Developers
Arming developers with a strong foundation in secure coding practices is critical for ensuring a robust codebase. Tailored education and hands-on training empower developers to identify and defend against prevalent threats to safety. This proactive approach is the cornerstone of a security-first culture in software development. Engaging in continuous learning, developers can keep pace with the evolving landscape of cybersecurity threats.
-
Importance of Continuous Education: As cybersecurity threats evolve, so must the knowledge of developers. A commitment to regular security training equips teams with updated strategies to counteract these threats, fostering a culture of vigilance and proactive security.
-
Effective Training Modalities: A combination of interactive workshops, online modules, and scenario-based exercises can provide a well-rounded education. These methods ensure that learning is not only comprehensive but also retains the practical application at its core.
-
Understanding Software Weaknesses: The foundational step of securing coding is comprehending the weaknesses themselves. Understanding how threat actors exploit weaknesses in programs is crucial for developers to adequately protect applications.
-
Memory Safety: Addressing memory unsafety is a pressing issue, with far-reaching implications for program protection. Efforts to create safer programs through intentional design, with a focus on memory safety, are pivotal in reducing vulnerabilities.
The incorporation of protection into computer science curricula is gaining recognition as a fundamental discipline rather than an elective. Addressing the challenges in this area, such as resource scarcity and outdated educational models, is imperative for the development of security-savvy professionals.
- Real-World Application: Despite the availability of theoretical knowledge on secure application development, its integration into standardized processes in the industry remains incomplete. Closing this divide through hands-on implementation is vital for improving the protection of computer programs.
A recent workshop at the National Cybersecurity Education Colloquium emphasized the importance of integrating protection into the academic foundation of computer science, altering how future developers perceive and implement safeguarding measures.
"Security knowledge should not just be an elective, but a fundamental area of knowledge for all computer science students," as discussed in a workshop at the National Cybersecurity Education Colloquium.
In line with the upcoming surge of global elections, the importance of security in software applications becomes even more pronounced, underscoring the need for well-informed and well-trained developers capable of producing secure code that withstands the complexities of the digital world.
Conclusion
In conclusion, this article emphasizes the importance of adopting a security-first mindset and integrating robust practices into the software development process. Security by design, embedding security within the application's architecture, is a fundamental principle that ensures the creation of resilient and trustworthy systems.
The article covers various aspects of secure software engineering, including password management, access control, error handling, system configuration, threat modeling, cryptographic practices, input validation, database security, file management, session management, leveraging security frameworks, quality assurance, vulnerability management, and developer education.
By implementing best practices in these areas, developers can enhance the security of their codebases and protect against cyber threats. The article provides real-world examples and industry insights to underscore the importance of comprehensive security measures.
Integrating security frameworks and libraries, adopting security as code and DevSecOps practices, and prioritizing quality assurance and security testing are effective strategies for creating secure software applications.
Continuous education and training for developers are crucial to staying updated on evolving cybersecurity threats. Recognizing security as a core discipline in computer science education and applying security knowledge in practical settings are vital for maintaining secure codebases.
In summary, following secure software engineering practices and prioritizing security measures throughout the development lifecycle are essential for creating secure, reliable, and efficient applications. These measures protect sensitive data, ensure compliance, and enhance the overall productivity of the development process.
Implement best practices to enhance code security and protect against cyber threats.
Frequently Asked Questions
What is 'Security by Design' in software development?
Security by Design refers to the integration of security measures into the software development process from the beginning. It involves developing software with a strong foundation in safety, where protection is an inherent characteristic, not an afterthought.
Why is password management important in software security?
Password management is crucial because it helps protect access to the codebase, ensuring that only authorized individuals can make changes. It involves creating strong password policies and utilizing multi-factor authentication (MFA) to reduce the risk of unauthorized access.
How does access control and authorization contribute to software security?
Access control and authorization ensure that only users with the necessary permissions can perform specific actions or access certain information within a web application, aligning access levels with roles and responsibilities.
What role does error handling and logging play in security?
Error handling ensures that software failures do not provide attack vectors, while logging keeps a record of events for diagnosing issues. Both need to be managed carefully to avoid leaking sensitive information.
Why is system configuration and patch management important?
Proper system configuration and timely patching of software are essential to minimize vulnerabilities and protect against threats. This includes disabling unnecessary services and applying updates to address security flaws.
What is threat modeling and risk assessment in software development?
Threat modeling and risk assessment involve identifying potential threats to software and analyzing the risks they pose. This helps define safety requirements and prioritize security efforts.
How important are cryptographic practices and key management?
Cryptographic practices and key management are vital for securing sensitive information, ensuring that data is encrypted and that the cryptographic keys are managed and stored securely.
Why is input validation and output encoding significant for web application security?
Input validation prevents malicious data from entering a system, while output encoding ensures harmful content is safely rendered by browsers. Both practices protect against common attacks such as SQL injection and XSS.
What measures are taken to secure databases?
Database security involves using parameterized queries to guard against SQL injection, classifying and prioritizing sensitive data, and following the principle of least privilege to limit user access levels.
How does file and resource management affect software security?
Secure file and resource management prevent the execution of malicious files and resources, which includes rigorous validation, setting robust file permissions, and removing unused resources.
What is necessary for secure session management and token security?
Secure session management requires generating random session tokens, securely storing them, and invalidating them when necessary. Secure transmission protocols like HTTPS are also used to protect data in transit.
Why should developers leverage security frameworks and libraries?
Using established security frameworks and libraries provides developers with tested and reliable tools for implementing security features, which helps protect the application against known vulnerabilities.
How does quality assurance and security testing enhance software protection?
Quality assurance and security testing, including code reviews and penetration tests, help identify and mitigate weaknesses early in the development process, ensuring the robustness and security of the application.
What is involved in vulnerability management and patching?
Vulnerability management involves identifying and categorizing software flaws and applying patches to address them, which helps protect the codebase from potential security breaches.
Why is education and training for developers important?
Educating and training developers in secure coding practices is essential to empower them to defend against threats and build secure software. Continuous learning ensures developers stay updated on the latest cybersecurity threats and solutions.




