Introduction
Apigee API is a powerful platform that allows businesses to create, secure, supervise, and scale APIs effectively. With a robust suite of tools, Apigee API ensures that APIs are not only functional but also secure and efficient, accommodating growth in today's digital landscape. This article dives into the critical features of Apigee API, such as API design and development, security and access control, analytics and monitoring, policy enforcement and management, and integration with other tools and services.
By leveraging Apigee API, developers and businesses can meet the demands for efficient and secure API management while anticipating the needs of their users. Just as E. Leclerc revolutionized the retail industry by empowering customers, Apigee API empowers developers to create self-serving, responsive systems for modern enterprises.
What is Apigee API and Its Features
Apigee API offers a robust platform for businesses to create, secure, supervise, and scale APIs effectively. It's armed with an impressive suite of tools that cater to the diverse needs of API management, ensuring that APIs are not only functional but also secure and efficient to accommodate growth. A closer look at Apigee API's capabilities reveals several critical features:
- API design and development: Enabling a smooth and coherent process for building APIs that serve as bridges for communication between different software applications.
- Security and access control: Implementing robust measures to protect APIs from unauthorized access and potential security threats, which is essential in today's digital landscape where API-related security incidents are on the rise.
- Analytics and monitoring: Providing insights into API performance and usage, which is crucial for understanding how APIs are being utilized and for making informed decisions on optimizing them.
- Policy enforcement and management: Allowing precise control over how APIs are used and ensuring that they adhere to organizational and industry policies.
- Integration with other tools and services: Facilitating seamless connections with other software, enhancing the capability to build more complex and powerful applications.
By leveraging Apigee API, developers and businesses can not only meet the current demands for efficient and secure API management but also anticipate the needs of their users, echoing the historical shift in consumer empowerment seen in the retail revolution led by E. Leclerc. Just as Leclerc transformed the shopping experience by enabling customers to serve themselves, Apigee API empowers developers to craft self-serving, responsive systems that cater to the evolving needs of modern enterprises.
Basic Terminology and Concepts in Apigee
Grasping the essential vocabulary of Apigee API unlocks the full potential of its features. So let's decode the jargon. An 'API proxy' acts as a mediator, processing requests in place of the actual API, which can shield it from overuse, enforce security measures, and gather analytics.
'API products' bundle several APIs for specific use cases, simplifying developer access to a suite of services. Speaking of developers, they're the architects who build 'developer apps' to harness these APIs, crafting innovative solutions from the plethora of data and capabilities available.
This mastery of terms is not just academic; it's practical. For example, analytics are the lifeblood of digital strategy, with API analytics providing essential insights that guide business decisions and enhance user experiences. By analyzing how APIs are used, we can pinpoint areas for enhancement, bolster security, and cater to user preferences.
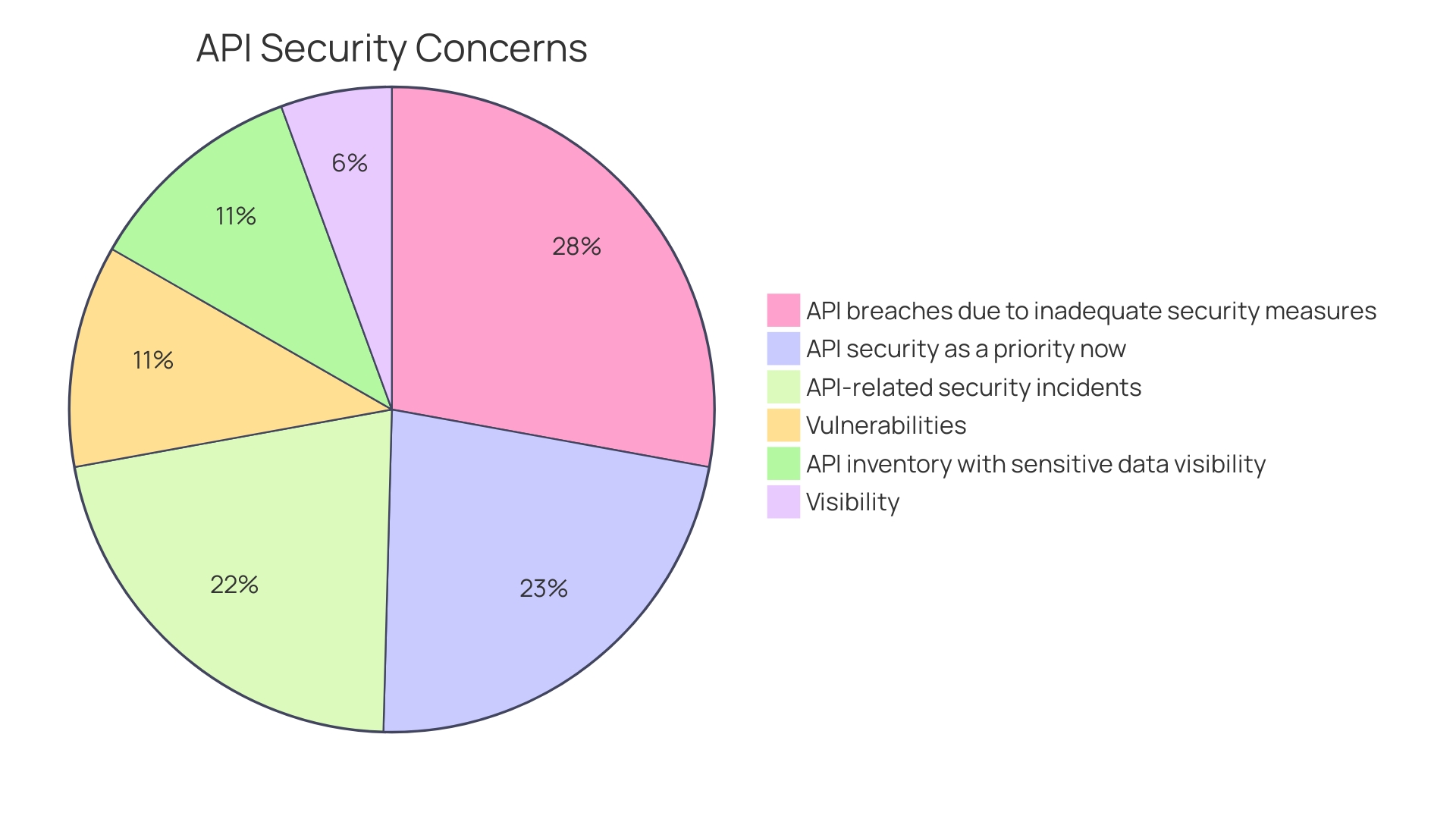
Moreover, with cybersecurity threats on the rise, understanding these components is critical. A staggering 78% of cybersecurity teams have faced an API-related incident in the past year, emphasizing the need for robust API management solutions that prioritize security.
Remember, whether you're streamlining operations for a fledgling startup or optimizing an established enterprise, familiarity with these concepts is key to tapping into the power of Apigee API and ensuring your digital ecosystem thrives in today's interconnected world.
Getting Started with Apigee API Management
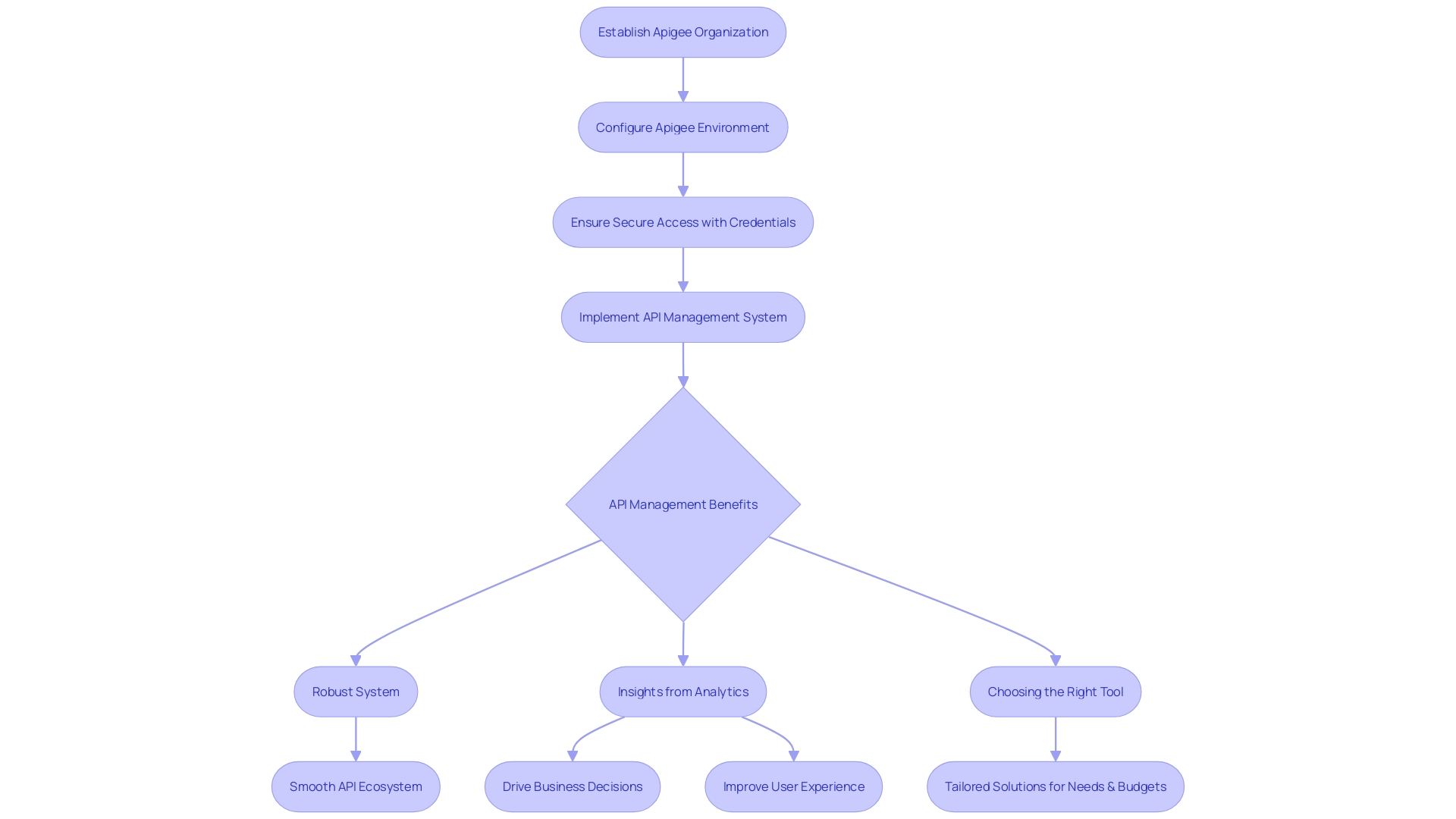
Embarking on the setup of an Apigee API management system is a strategic move for any organization looking to streamline and secure their API infrastructure. The journey begins with establishing an Apigee organization and environment, which are the foundational elements of your API management platform. This entails configuring your environment to suit your specific needs, whether you're a nimble startup or a large enterprise, and ensuring that you have the appropriate credentials in place for secure access.
The significance of a robust API management system cannot be overstated, given the increasing reliance on APIs in today's digital landscape. With a correctly configured Apigee setup, you can look forward to not only managing traffic effectively but also gaining valuable insights through analytics. This will keep your API ecosystem operating seamlessly, much like the success story of apree health, which leveraged Akamai's solutions to securely manage sensitive personal health information.
Moreover, the importance of choosing the right API management tool is crucial, as the market offers a plethora of options. By following the guidance in this section, you will not only be setting up an Apigee environment but also investing in a tool that has been recognized for its excellence in addressing a variety of API-related needs, ensuring that your APIs are not just operational but also primed for future growth and integration challenges.
Creating and Deploying API Proxies
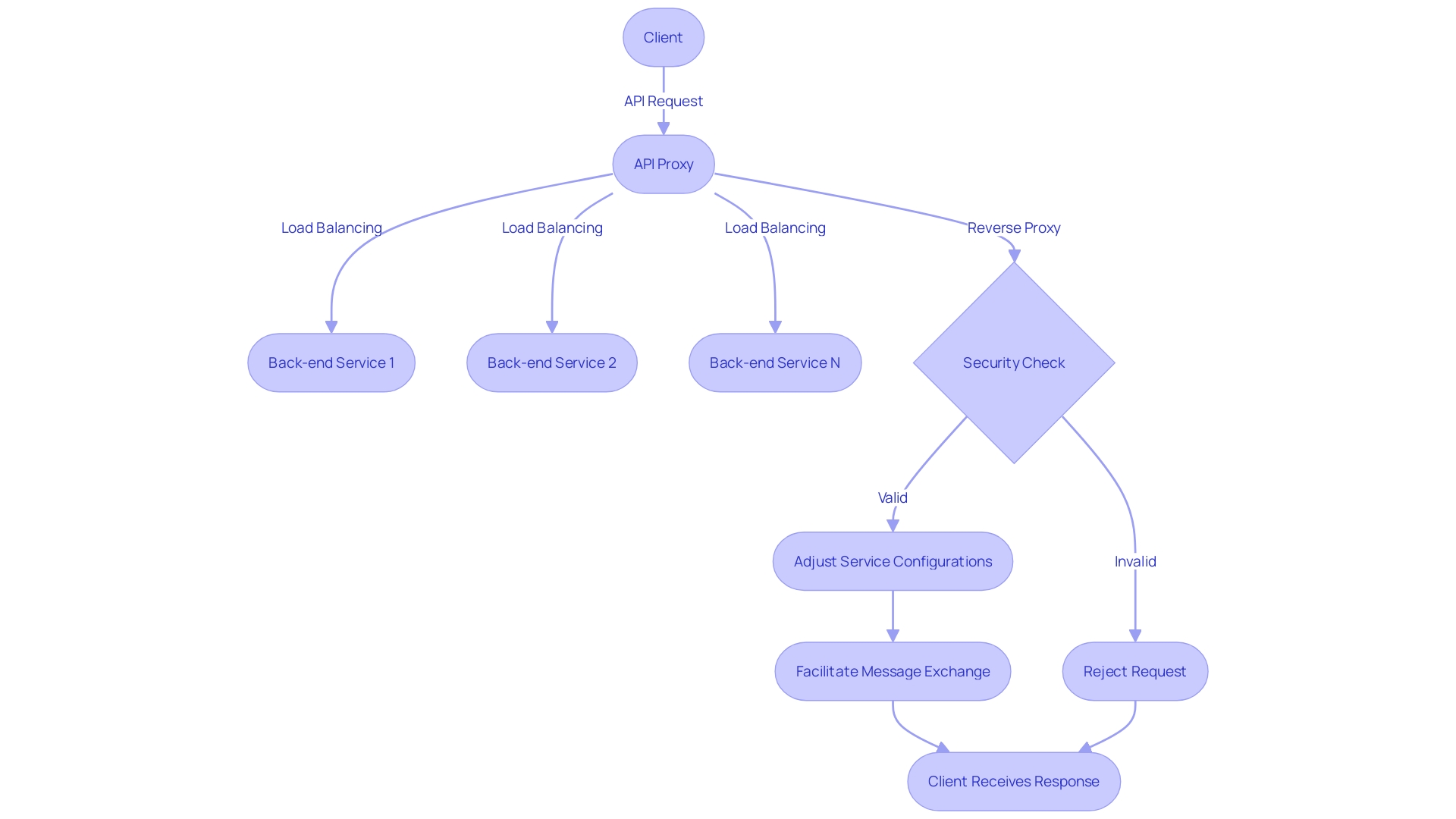
Apigee API management incorporates a key feature known as API proxies, which serve as the conduit between clients and the back-end services they need to access. These proxies offer a dual benefit: they act as a buffer that adds a layer of security, and they abstract the backend to simplify client interactions. For developers, mastering the creation and deployment of API proxies is a critical skill, as it enables them to effectively manage incoming API requests and adjust their services based on specific configurations.
To illustrate, consider a scenario involving two people, Alice and Bob, with a proxy situated in between. Alice communicates to Bob through the proxy, and vice versa; the proxy facilitates the exchange of messages, analogous to how an API proxy operates. Imagine this proxy as a robust server that not only relays messages but also ensures they are delivered securely and efficiently to the correct recipients.
This concept extends to the digital realm, where a client's request to a website is managed by a proxy server, which then returns the appropriate response. By utilizing a widely adopted server like Apache2, with its extensive module support, the construction of an API proxy becomes streamlined.
The necessity of API proxies is highlighted by recent research indicating that a significant 78% of cybersecurity teams have encountered API-related security incidents over the past year. A substantial 81% now view API security as a higher priority than before. These statistics underscore the crucial role that API proxies play in defending against cyber threats.
API gateways further reinforce this defense mechanism by implementing a variety of functions, such as request validation, authorization, authentication, and rate limiting. These gateways operate much like a maître d’ in a restaurant, orchestrating the flow of requests and responses and ensuring that everything runs smoothly. They are considered fully managed services, meaning the cloud provider handles all aspects of maintenance and management, allowing developers to focus on building their services rather than managing the infrastructure.
With APIs serving as the backbone of modern software, their security and efficiency are paramount. As we delve into the world of API proxies, we'll discover how to leverage Apigee's capabilities to construct proxies that are not only robust but also aligned with the current trends and best practices in API management. This endeavor is all about ensuring a seamless, secure, and efficient experience for both the developers creating the APIs and the end-users who rely on them.
API Proxy Configuration and Management
Crafting and maintaining API proxies is akin to orchestrating a seamless conversation between different software applications. It's crucial to establish clear routing rules, robust security policies, and effective traffic management to ensure these digital dialogues are both fluid and secure. Consider the proxy as a diligent intermediary, much like a messenger between Alice and Bob, ensuring messages are conveyed accurately and efficiently.
Advanced configurations, such as caching and rate limiting, also come into play, refining the process and optimizing the flow of information.
Analogous to building an Apache2 Proxy server, setting up API proxies involves selecting the right tools and implementing them with precision. Moreover, given the recent spike in API-related security incidents, with 78% of cybersecurity teams reporting an API breach in the past year, the stakes for tight security and comprehensive management have never been higher. As APIs continue to underpin modern digital infrastructures, the demand for cutting-edge API management tools that offer traffic control and detailed analytics is growing.
These tools are designed to cater to the diverse needs of any organization, regardless of its size, and are integral to maintaining a smoothly operating API ecosystem.
Furthermore, the integration of API analytics into this ecosystem is indispensable. They serve as a beacon, guiding businesses with actionable insights derived from API usage patterns and performance metrics. For instance, usage analytics can unveil the most popular endpoints, while performance analytics shed light on the APIs' responsiveness and stability.
This information is invaluable, as it helps organizations identify growth opportunities, enhance user experiences, and fortify their digital assets against potential threats.
Security in Apigee API Management
The security of APIs is a cornerstone of modern digital business, where the seamless exchange of data is essential for innovation and growth. However, the surge in API adoption has been shadowed by a rise in security breaches, exposing sensitive data and potentially causing significant damage to businesses and individuals. Apigee API steps into this landscape with a suite of security capabilities designed to protect your digital assets effectively.
Apigee's approach aligns with the 'Zero Trust' model, which has become a security imperative in the digital age. This model operates on the principle that trust must be earned and verified, with no automatic trust granted, whether the request originates inside or outside the network. The adoption of such a model is not just a trend but a necessary evolution in API security, considering that traditional perimeter-focused defenses fail to thwart the sophisticated threats of today.
Understanding the API security landscape requires a comprehensive view of your digital ecosystem. It's crucial to have full knowledge of your APIs: which business units they serve, the data they handle, their structure and architecture, and their security attributes like authentication and rate-limiting. By gaining this intelligence, organizations can define their 'good' security posture, documenting API standards and policies that align with best practices and regulatory requirements.
The experience of apree health, a company that handles personal health information (PHI), underscores the need for robust API security. They partnered with Akamai to enhance their security posture, as the sharing of sensitive information requires diligent protection against today's array of attacks, including social engineering and bot-enabled API attacks.
Recent statistics further highlight the urgency: 78% of cybersecurity teams have faced an API-related incident in the past year. Yet, only 40% of those with a full inventory of APIs have visibility into which ones return sensitive data. The importance of API security has never been more pronounced, with 81% of professionals acknowledging it as a higher priority now than just a year ago.
The future of API security is promising, with advancements like AI-powered solutions capable of autonomously detecting and responding to threats, and blockchain-based mechanisms for authentication and access control. These innovations will undoubtedly play a critical role in the ongoing quest to secure the vast networks of APIs that underpin our digital infrastructure.
Incorporating these advanced measures, along with vigilant monitoring of API traffic and logs, is crucial for quick detection and response to security incidents. By implementing and continually refining these security practices, businesses can safeguard the integrity and confidentiality of their API data, ensuring a secure and resilient digital environment.
Best Practices for API Design and Development
Embarking on API design and development requires a keen understanding of the intricate communication pathways that APIs create among software applications. These pathways are the conduits for data retrieval, such as when a weather service API shares real-time conditions or forecasts. The API-First Development approach, a modern paradigm in software creation, prioritizes the construction of these APIs at the outset.
This method ensures that the resulting APIs are not only functional but also integral to the software's architecture, promoting efficiency and scalability.
To craft APIs that stand the test of time and technology, it's crucial to adhere to RESTful design principles, which emphasize a stateless, client-server, cacheable communications protocol — the backbone of the web. Additionally, implementing effective error handling is paramount. Integrating HTTP problem details can offer contextual information, aiding developers in swiftly resolving issues that arise.
Versioning plays a critical role in the longevity and adaptability of APIs. As business requirements evolve, so too must the APIs, without disrupting the existing ecosystem of applications that rely on them. Therefore, a well-thought-out versioning strategy is essential.
Documentation is the roadmap that guides developers through the API's functionalities, making it indispensable for both seasoned developers and newcomers alike. A comprehensive API glossary and curriculum can empower developers to better understand and utilize these interfaces. As we've seen with platforms like Google Maps, effective API integration can vastly simplify complex processes, proving the transformative power of well-documented APIs.
By following these best practices, developers can create APIs that are not only developer-friendly but also robust enough to enhance user experiences across the digital landscape.
Using Policies in Apigee
Apigee API's policies are power tools that bolster your API proxies with advanced functionalities and robust security measures. These policies are the linchpin for maintaining stellar API performance, security, and reliability. For instance, a spike arrest policy acts like the multiple access gates at a subway station during peak hours—it ensures smooth operation by regulating the flow of requests.
Similarly, quota policies help keep a tab on the number of requests that an API can handle within a set time, akin to a subway's turnstile limiting the number of people entering. Furthermore, OAuth policies serve as a permission boundary, creating a 'wall' that defines what actions users can perform, enhancing security and preventing permission misuse.
Reflecting on recent advancements, API7 Enterprise v3.2.14.4 has introduced permission boundaries, highlighting the industry's focus on granular user permissions for improved enterprise security. Indeed, with 60% of organizations reporting breaches due to API vulnerabilities, the need for tight security policies is more pressing than ever. As experts suggest, focusing on 'Needs' versus 'Wants' is crucial.
This means not just implementing what seems desirable but deploying policies that genuinely meet the essential requirements for security and efficiency.
By proactively managing your API landscape with these policies, you can mitigate common management challenges. This ensures that your APIs are not just functional but are also safeguarded against potential threats and aligned with best practices for data privacy and information security. The governance of API ecosystems, through vigilant mapping and maintenance, is key to avoiding unnecessary data exposure and aligning with the principle of data minimization.
With an eye on the right security measures and a clear understanding of your API's role in data exchange, you can ensure that your API infrastructure remains resilient and trustworthy.
Analytics and Monitoring in Apigee
Understanding the performance and usage of APIs is critical for developers and organizations to maintain efficient operations. Apigee API provides a robust suite of analytics and monitoring tools that allow for comprehensive insights into API behavior. Through analytics dashboards, developers can track API traffic, monitor performance indicators, and glean valuable data that informs strategic decisions.
For instance, distributed tracing enables the correlation of data across services, presenting a complete picture of an API request or response's journey. This information is crucial for root cause analysis, allowing teams to pinpoint and resolve issues swiftly. With 78% of cybersecurity teams reporting API-related security incidents in the last year, the importance of analytics for security and performance cannot be understated.
The need for such analytics is amplified by the fact that APIs are now a strategic business asset. They facilitate the flow of vast amounts of data and transactions, making usage analytics an indispensable tool for understanding demand and optimizing resource allocation. In an environment where API downtime can cost companies approximately $5,600 per minute, real-time monitoring is essential for maintaining system reliability and preventing financial loss.
Moreover, API logs serve as a rich source of insights, capturing user behaviors and interactions. This data is pivotal for developing user-centric products and services. As 83% of web traffic involves API calls, these logs become strategic assets for businesses, aiding in swift identification and resolution of performance issues.
In light of these factors, it's clear why 93% of organizations recognize APIs as crucial to their operations, with 86% acknowledging that APIs prevent operational silos. The strategic implementation of API analytics and monitoring with tools like Apigee API is no longer optional but a necessary component of modern digital infrastructure.
Advanced Topics: Flows, Routes, and Environments
Exploring the advanced capabilities of Apigee API, such as flows, routes, and environments, is essential for building robust API management solutions. Flows in Apigee API are critical for handling API requests and responses, and they enable developers to implement sophisticated logic to manage the flow of data through APIs. For instance, flows can be configured to transform request and response payloads, enforce security policies, and route requests to appropriate backend services based on complex criteria.
Understanding routes is equally important as they dictate how API traffic is directed within the digital ecosystem. Properly configured routing ensures that API calls are efficiently processed and directed to the correct services, which is vital for the scalability and resilience of API solutions.
Environments in Apigee API serve as isolated contexts where APIs can be safely tested and deployed. By leveraging multiple environments, organizations can manage API lifecycles effectively, from development and testing to staging and production, ensuring that each API is thoroughly vetted before being released to end-users.
To illustrate the importance of mastering these advanced topics, consider the case of TotalEnergies Digital Factory (TDF). With over 80 digital solutions deployed in 25 countries, TDF relies heavily on APIs to modernize its legacy systems and streamline operations. APIs not only enable seamless integration across diverse platforms but also foster collaboration among developers, as evidenced by the unanimous agreement among TDF's developers on the effectiveness of collaboration tools like Postman.
The digital realm is rapidly evolving, and the significance of API analytics cannot be overstated. They provide invaluable insights that inform business strategies and enhance user experiences. As APIs continue to be the backbone of software applications, understanding and utilizing the advanced features of platforms like Apigee API becomes imperative for organizations aiming to remain competitive and secure in the digital landscape.
Integrating Apigee with Other Tools and Services
Understanding the integral role of Application Programming Interfaces (APIs) is essential for modern software development. APIs serve as translators between disparate software programs, enabling seamless communication and interaction. This has positioned APIs as vital components across various industries, particularly as big data and emerging technologies proliferate.
The increasing importance of APIs is evident, as they empower developers to forge collaborative partnerships with stakeholders to augment agency systems and spur innovation. For instance, the ubiquity of the Google Maps API across billions of devices exemplifies how APIs can facilitate better business services and streamline interactions with customers and partners. Moreover, APIs are lauded as the 'crown jewels' of software development, as Google describes, unlocking the potential for more intricate and potent applications through external connections.
Apigee API exemplifies this innovation by offering robust integration capabilities that augment and leverage current infrastructures. Seamless integration with prevalent tools such as Jenkins, Git, and AWS is just the tip of the iceberg. Apigee API enables the construction of resilient and scalable API ecosystems, a necessity underscored by the challenges faced by companies transitioning to centralized productivity tools.
For example, Riskified's shift to SuccessFactors disrupted their Slack-based Time Off requests, highlighting the need for efficient API integration to maintain workflow continuity. Similarly, apree health's merger necessitated a secure and swift exchange of personal health information, which was facilitated through partnering with Akamai for API solutions.
This capacity for integration extends to simplifying processes, such as setting up webhooks across projects, which can otherwise be cumbersome and inefficient without the right tools. As industries evolve, the demand for such streamlined solutions grows, making API management software more crucial than ever. The key is not just to address the 'wants' but to focus on the actual 'needs' of customers, as highlighted by insights from leading financial institutions.
This approach ensures that API solutions cater to multiple customer requirements, thereby enhancing web-based activities and supporting the development of powerful platforms.
Common Anti-Patterns and Solutions
Achieving a seamless API management strategy necessitates a clear understanding of the potential obstacles and an effective solution to counteract them. A study of TotalEnergies Digital Factory's (TDF) approach reveals how they tackled the challenges of modernizing legacy systems through API-centric solutions, deploying over 80 digital tools across 25 countries. The reliance on APIs has surged, highlighted by a report which found that 93% of organizations consider APIs crucial for their operations, with 86% recognizing that APIs prevent working in silos, thus enhancing data visibility.
However, the rise in API usage comes with increased risks, as 60% of surveyed organizations experienced at least one breach due to API vulnerabilities, emphasizing the need for robust API design and management.
To navigate these complexities, it's paramount to review and adapt standards, as historical practices like prefixing unstandardized parameters with 'X-' have been deprecated due to the evolution of best practices. As one expert critically notes, what was once considered a 'best practice' may not hold true today, urging a reevaluation of current methods. Furthermore, integrating APIs with microservices, as done by TDF, can yield benefits like enhanced customer satisfaction and productivity.
In conclusion, by understanding and applying these insights, organizations can refine their API strategies, avoid common pitfalls, and harness the full potential of API-first development to drive digital transformation and operational excellence.
Conclusion
Apigee API is a powerful platform that enables efficient and secure API management. With its robust suite of tools, organizations can create, secure, supervise, and scale APIs effectively in today's digital landscape.
The critical features of Apigee API include API design and development, security and access control, analytics and monitoring, policy enforcement and management, and integration with other tools and services. By leveraging these capabilities, developers and businesses can meet the demands for efficient and secure API management while anticipating the needs of their users.
Apigee API empowers developers to build APIs that serve as bridges for communication between different software applications. It ensures robust security measures to protect APIs from unauthorized access and potential threats. The analytics and monitoring tools provide valuable insights into API performance and usage, enabling informed decisions on optimization.
Policy enforcement and management allow precise control over API usage, ensuring adherence to organizational and industry policies. Integration with other tools and services facilitates seamless connections, enhancing the capability to build complex and powerful applications.
Just as E. Leclerc revolutionized the retail industry by empowering customers, Apigee API empowers developers to create self-serving, responsive systems for modern enterprises. By following best practices in API design and development, organizations can build functional, scalable, and efficient APIs. The integration capabilities of Apigee API further enhance API management, streamlining operations and driving innovation.
In the face of rising API-related security incidents, Apigee API prioritizes security through its robust security capabilities. The adoption of the 'Zero Trust' model ensures trust is earned and verified, protecting digital assets effectively. By implementing comprehensive security measures, organizations can safeguard their data and maintain a secure digital environment.
Apigee API's analytics and monitoring tools provide valuable insights into API behavior, enabling efficient operations and data-driven decision-making. Exploring advanced capabilities such as flows, routes, and environments enhances API management solutions. The integration capabilities of Apigee API enable organizations to leverage APIs as vital components of modern software development, driving digital transformation and operational excellence.
In conclusion, Apigee API offers a comprehensive platform for efficient and secure API management. By leveraging its critical features, organizations can meet the evolving needs of modern enterprises, protect their digital assets, gain valuable insights, and drive innovation. Apigee API empowers developers and businesses to navigate the complexities of API management in today's interconnected world.
Experience the power of Apigee API and revolutionize your API management today!
Frequently Asked Questions
What is Apigee API?
Apigee API is a platform designed for businesses to create, secure, supervise, and scale APIs, providing a suite of tools for comprehensive API management.
What are the key features of Apigee API?
The key features include API design and development, security and access control, analytics and monitoring, policy enforcement and management, and integration with other tools and services.
What is an API proxy in Apigee?
An API proxy in Apigee acts as a mediator that processes requests on behalf of the actual API, providing security, usage analytics, and protection from overuse.
How does Apigee API contribute to API security?
Apigee API implements robust security measures, such as access control and threat protection, to safeguard APIs against unauthorized access and potential security threats.
What is the importance of API analytics in Apigee?
API analytics provide insights into API performance and usage, helping businesses make informed decisions on optimizing their APIs and understanding user interactions.
How does an organization start with Apigee API management?
An organization begins by establishing an Apigee environment, configuring it to their needs, and ensuring secure access with appropriate credentials.
What is the role of an API gateway in Apigee?
An API gateway in Apigee manages the flow of requests and responses, implementing functions like request validation, authorization, and rate limiting, similar to a maître d' in a restaurant.
How do API proxies protect against cybersecurity threats?
API proxies serve as a security layer that can enforce policies, validate requests, and mitigate cyber threats, contributing to the defense of the API infrastructure.
Why are API proxies necessary?
API proxies are necessary for security, as they act as buffers that protect back-end services and simplify client interactions, ensuring efficient and safe delivery of messages.
What are API products in the context of Apigee?
API products in Apigee bundle several APIs for specific use cases, simplifying developer access to a suite of services and enhancing application development.
What is the 'Zero Trust' model in Apigee API security?
The 'Zero Trust' model operates on the principle that no trust is automatically granted, and trust must be earned and verified, regardless of whether the request comes from inside or outside the network.
How do policies function in Apigee API?
Policies in Apigee API act as tools that add advanced functionalities and security measures to API proxies, such as regulating the flow of requests and managing access.
What are the best practices for API design and development mentioned in the article?
Best practices include adhering to RESTful design principles, implementing effective error handling, proper API versioning, and providing comprehensive documentation.
How can Apigee API be integrated with other tools and services?
Apigee API can be integrated with popular tools such as Jenkins, Git, and AWS, enabling the construction of resilient and scalable API ecosystems.
What are the advanced topics in Apigee API like flows, routes, and environments?
Advanced topics involve managing API requests and responses through flows, directing API traffic via routes, and using environments for isolating and deploying APIs safely.
What is the significance of understanding common anti-patterns and solutions in API management?
Understanding common anti-patterns and their solutions helps organizations refine their API strategies, avoid pitfalls, and fully harness the potential of API-first development.




