Introduction
In the realm of software development, memory management stands as a critical pillar that can make or break application performance. As programs grow increasingly complex, the risk of memory leaks—a silent yet formidable foe—becomes more pronounced. These leaks not only consume precious resources but can also lead to frustrating crashes and degraded user experiences.
Developers who master the art of detecting and resolving memory leaks are equipped to enhance application reliability and efficiency significantly. This article delves into the intricacies of memory leaks, offering a comprehensive guide to:
- Identifying
- Analyzing
- Preventing these issues
While also spotlighting essential tools and best practices that empower developers to maintain optimal performance in their applications.
Understanding Memory Leaks: Definition and Importance
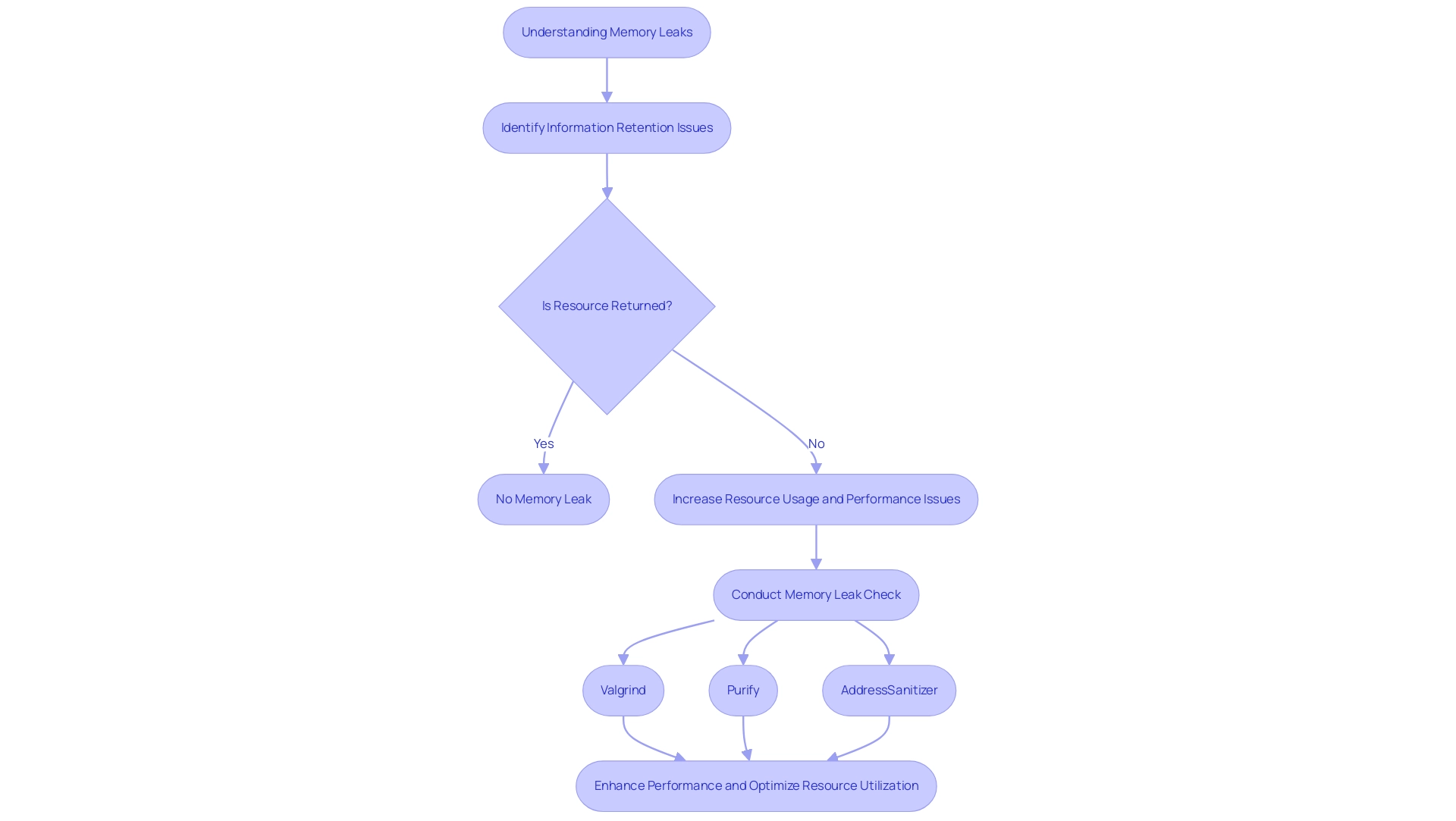
An information retention issue happens when a program assigns space but does not return it to the operating system when it is no longer required. This oversight can result in elevated resource usage, reduced software performance, and, ultimately, system failures. As software systems become increasingly intricate, the significance of comprehending and tackling resource issues cannot be emphasized enough; these problems can severely impact the effectiveness and dependability of programs.
Joe Doe aptly states, 'Extremely well written article. Thank you.' This emphasizes the essential aspect of data handling.
By efficiently conducting a memory leak check and addressing leaks using tools such as:
- Valgrind
- Purify
- AddressSanitizer
developers not only enhance application performance but also significantly improve user experience and optimize resource utilization. Moreover, grasping the constraints and compromises of garbage collection is crucial for developers to enhance resource utilization strategies, ensuring their software remains robust and efficient.
Step-by-Step Guide to Performing Memory Leak Checks
- Identify the Codebase: Begin by targeting sections of your code where effective resource management is crucial. Pay particular attention to areas involving dynamic data allocation, such as complex data structures or resource-intensive operations, and ensure to perform a memory leak check.
- Set Up Monitoring Tools: Utilize robust profiling tools such as MTuner, Valgrind, Memory Profiler, or built-in IDE utilities to closely observe resource usage throughout the program's execution. MTuner, a free C/C++ profiler, supports MSVC, GCC, and Clang compilers, providing features such as leak detection and timeline-based activity history. The right tools significantly enhance detection accuracy, as shown by experimental results indicating the high detection speed and accuracy of advanced methods like MLD, which incorporate a memory leak check.
- Run the Program: Execute your program under standard usage conditions to gather comprehensive data regarding resource allocation and deallocation patterns. This step is essential for establishing a baseline for your application's resource behavior.
- Analyze Resource Usage: Carefully examine the profiling data to uncover discrepancies between allocated and deallocated resources. Focus on identifying patterns that may indicate resources that remain allocated without being released, which is a common source of inefficiencies that a memory leak check can help uncover.
- Trace the Leaks: Utilize your profiling tools to backtrack to the origins of the leaks. This process typically involves a memory leak check by scrutinizing the stack traces provided by the tools to pinpoint where resources are allocated without a corresponding release. As noted by software engineer Zhenjiang Wang, effective detection methods are critical to safeguarding against potential software vulnerabilities.
- Implement Fixes: Refactor your code to guarantee that all allocated resources are adequately released once they are no longer necessary. This could mean inserting appropriate
free()calls in C/C++ or employingdeletein C++. A well-organized method can reduce the risk of resource errors and facilitate a memory leak check, thereby improving system performance. - Reevaluate the Program: Following the execution of essential corrections, conduct your resource assessments to verify that the issues have been successfully resolved and that your program operates effectively. Ongoing testing is crucial, as the False Positive Rate of detection methods can be around 23.8%, making vigilance essential in management. Additionally, the integration of function summaries with Control Flow Graphs (CFG), as demonstrated in the case study titled function Summary Method for Memory operations, can further enhance detection efficiency and minimize scan times.
Tools and Techniques for Effective Memory Leak Detection
A range of tools is crucial for efficiently identifying resource issues in software development, each tailored to specific programming environments:
- Valgrind: This powerful tool specializes in debugging resources, detecting resource issues, corruption, and usage errors in C and C++ programs. Its capability to conduct a memory leak check by producing detailed reports on allocation and deallocation patterns makes it invaluable for optimizing performance. For instance, the allocation tree for snapshot 14 shows 20,000B of useful heap space allocated, providing a concrete example of resource usage that supports the discussion on resource retention detection.
- Resource Profiler: Tailored for Python developers, this tool provides in-depth insights into resource usage, enabling the identification of issues within Python applications. It tracks resource consumption over time, ensuring developers can pinpoint problematic areas efficiently.
- Visual Studio's Diagnostic Tools: For .NET developers, Visual Studio integrates built-in diagnostic tools that monitor usage and detect leaks seamlessly during development. This feature simplifies the debugging process, allowing for immediate feedback on resource health.
- Heaptrack: This tool records allocations and deallocations, facilitating a thorough analysis of usage trends over time. By visualizing storage behavior, it helps developers understand allocation patterns and identify potential leaks.
In addition to these tools, employing coding techniques such as RAII (Resource Acquisition Is Initialization) in C++ can significantly enhance resource management and facilitate a memory leak check. By ensuring that resources are automatically released when no longer required, developers can reduce the risk of resource mismanagement, leading to more efficient and dependable applications.
As noted by Aurimas Mikalauskas, there are considerations regarding the performance penalty of running programs under Valgrind, which can vary significantly, highlighting the importance of assessing whether such tools are suitable for production environments.
Furthermore, a case study example from the Konqueror web browser illustrates resource usage patterns for larger programs. The example graph illustrates various detailed snapshots and a peak snapshot, offering insights into allocation behavior in complex applications, thereby demonstrating the practical use of these tools in real-world scenarios.
Common Mistakes to Avoid When Checking for Memory Leaks
- Neglecting to Monitor All Code Paths: One of the most critical oversights in resource retention detection is focusing solely on specific sections of the code. This narrow approach can result in missed leaks, as unmonitored paths may harbor hidden issues. Effective resource management requires comprehensive monitoring across all execution paths, which includes a memory leak check.
- Ignoring Tool Limitations: Each profiling tool has its own strengths and weaknesses. Grasping the constraints of your selected tool is essential; some may not identify specific kinds of issues, resulting in misplaced assurance in resource management practices.
- Failing to Test Under Realistic Conditions: Testing in environments that don’t accurately reflect production usage can obscure potential resource issues. To achieve meaningful results, it is vital to conduct tests under conditions that closely simulate real-world application scenarios.
- Overlooking Exception Management: Resource drains often occur during exception handling if allocations are not properly released. It is crucial to guarantee that resource management includes a memory leak check to ensure strength, even in error situations, to avert failures from happening during unexpected incidents. As noted by expert Ali Bayat, who holds 3 gold badges, 47 silver badges, and 43 bronze badges, memory issues can stem from a variety of sources. You registered an event but forgot to unregister that event.
- Not Retesting After Fixes: Once resource issues have been identified and resolved, retesting is crucial. This step confirms that the issues have been resolved and includes a memory leak check to ensure that no new leaks have been introduced during the process. Regular retesting promotes a culture of thoroughness and vigilance in information management.
- Real-World Example of Effective Memory Management: Consider the case study of a dynamically growing array in C. This type of dynamic array can automatically resize itself to accommodate more data, overcoming the limitations of static arrays and enhancing the flexibility of data storage. This real-world example highlights the significance of strong resource handling practices in conducting a memory leak check to prevent leaks.
- Advancements in Memory Management: The introduction of the restrict keyword in the C99 standard indicates that a pointer is the only reference to the space it points to, allowing for compiler optimizations. This advancement emphasizes the changing environment of data handling practices.
Best Practices for Preventing Future Memory Leaks
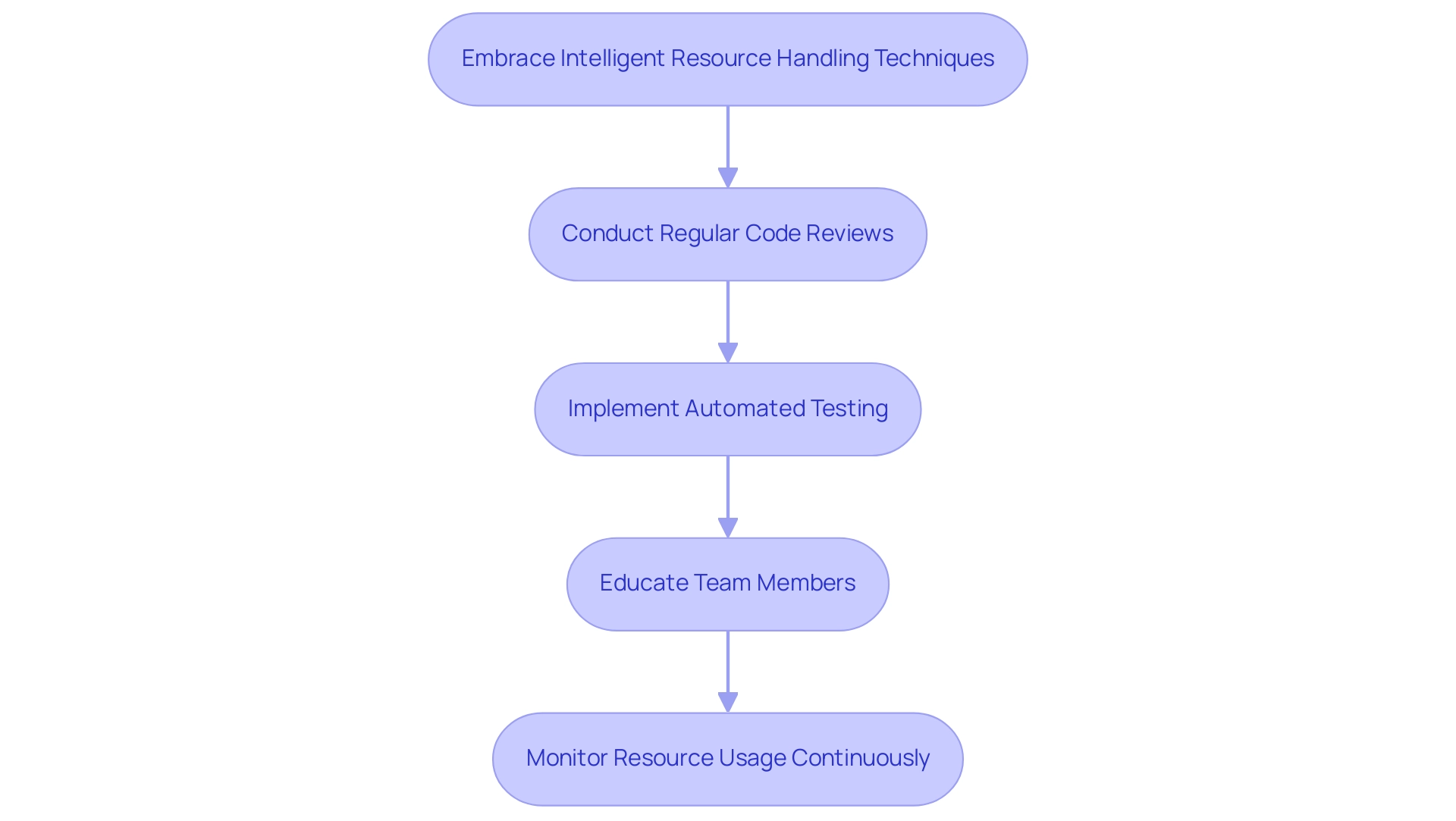
- Embrace Intelligent Resource Handling Techniques: Utilize smart pointers in C++ to automate resource oversight, significantly decreasing the chances of manual mistakes that result in resource failures. This approach not only streamlines the coding process but also enhances overall application stability. As mentioned in industry conversations, smart pointers play an essential role in resource allocation by conducting a memory leak check to ensure that space is released when no longer required, effectively preventing leaks. With a reputation of 7,195 points, Kees de Kooter emphasizes the importance of these practices in the software development community.
- Conduct Regular Code Reviews: Foster a culture of collaboration by encouraging team members to conduct code reviews focused on resource management practices. This peer-review process can highlight potential issues and encourage adherence to best practices, thereby enhancing code quality and efficiency. According to design patterns and principles, which provide general solutions for common software design issues, structured approaches can significantly improve management of resources.
- Implement Automated Testing: Integrate automated tests into your development lifecycle that specifically target detection of resource issues. Regular testing enables early detection of issues, which can be addressed before they escalate into more significant problems, ensuring a robust application.
- Educate Team Members: Provide your team with understanding about resource handling principles and the critical importance of performing a memory leak check to prevent leaks. An informed team is better positioned to implement effective data management techniques, fostering a collective responsibility for code quality.
- Monitor Resource Usage Continuously: Incorporate resource monitoring into your application's performance metrics and logging systems. By keeping a constant check on resource usage and conducting a memory leak check, you can quickly detect and address leaks, maintaining optimal performance and reliability. For example, applying relevant design patterns can optimize memory usage and performance while avoiding anti-patterns that harm memory efficiency, as demonstrated in the case study on design patterns and principles.
Conclusion
Effective memory management is essential for maintaining high-performance applications, particularly as software complexity increases. This article has explored the critical aspects of identifying, analyzing, and preventing memory leaks, which can severely impact application performance and user experience. By utilizing powerful tools such as Valgrind, Memory Profiler, and Heaptrack, developers can accurately detect and address memory issues, ensuring optimal resource management.
Moreover, understanding common pitfalls, such as neglecting all code paths and failing to test under realistic conditions, is crucial for robust memory management practices. Implementing best practices, including:
- Adopting smart pointers
- Conducting regular code reviews
- Integrating automated testing
further fortifies applications against memory leaks. Continuous education and monitoring can empower teams to maintain high standards of code quality and application reliability.
In conclusion, mastering memory management not only enhances application performance but also significantly improves user satisfaction. By actively engaging in detection and resolution efforts, developers can create more efficient and reliable software, ultimately leading to a smoother and more enjoyable user experience. Embracing these strategies will pave the way for more resilient applications capable of meeting the demands of an increasingly complex digital landscape.
Frequently Asked Questions
What is an information retention issue in software?
An information retention issue occurs when a program assigns memory space but fails to return it to the operating system when it is no longer needed, leading to increased resource usage, decreased software performance, and potential system failures.
Why is it important to address resource issues in software systems?
Addressing resource issues is crucial as they can significantly impact the effectiveness and reliability of programs, especially as software systems become more complex.
What tools can developers use to check for memory leaks?
Developers can use tools such as Valgrind, Purify, and AddressSanitizer to efficiently conduct memory leak checks and address any identified leaks.
What is the first step in identifying memory leaks in a codebase?
The first step is to identify sections of your code where effective resource management is essential, particularly areas involving dynamic data allocation, and perform a memory leak check.
How can monitoring tools assist in detecting memory leaks?
Monitoring tools like MTuner, Valgrind, and Memory Profiler can help observe resource usage during program execution, enhancing the accuracy of leak detection.
What should be done after running the program for resource analysis?
After running the program, analyze the profiling data to identify discrepancies between allocated and deallocated resources, focusing on patterns indicating resources that remain allocated without being released.
How can developers trace memory leaks?
Developers can trace memory leaks by using profiling tools to scrutinize stack traces, helping to identify where resources are allocated without a corresponding release.
What actions should be taken to fix identified memory leaks?
Developers should refactor the code to ensure that all allocated resources are adequately released when no longer necessary, such as using free() in C/C++ or delete in C++.
What is the significance of reevaluating the program after implementing fixes?
Reevaluating the program is essential to verify that the memory leak issues have been resolved and that the program operates effectively, as ongoing testing is necessary due to the potential for false positives in detection methods.
How can the integration of function summaries with Control Flow Graphs (CFG) improve memory leak detection?
Integrating function summaries with CFG can enhance detection efficiency and minimize scan times, making it easier to identify and address memory leaks in the program.




