Introduction
In the ever-evolving landscape of cybersecurity threats, it is crucial for Java developers to prioritize the security of their applications. By implementing a set of best practices and utilizing secure coding techniques, developers can safeguard sensitive information and protect against potential vulnerabilities. This article explores key strategies for enhancing Java application security, including the use of tried and tested libraries, secure password storage, input validation, data encryption, access control mechanisms, filtering sensitive information from exceptions, and regularly updating dependencies.
By following these practices, developers can ensure maximum efficiency and productivity while maintaining the integrity and security of their Java applications.
Use Tried and Tested Libraries
Utilizing established libraries that have been thoroughly vetted and tested is critical in crafting secure Java code. These libraries are the result of collective insights and efforts from a vast open-source community, and they have proven their reliability and safety. By integrating these resources, developers can incorporate measures that have been proven to combat vulnerabilities effectively. For instance, when dealing with sensitive information in Java applications, such as customer data or financial transactions, it is imperative to implement strong encryption algorithms to ensure data integrity and confidentiality. This is particularly important in sectors like banking, where organizations like M&T Bank have set high standards for code quality to maintain software maintainability and compliance with strict regulations.
In the context of password management, encryption might seem like the default approach, but it's actually hashing that's preferred, since it doesn't allow for the original text to be retrieved. Meanwhile, the industry at large is preparing for a quantum computing future, as seen with Microsoft's integration of post-quantum algorithms into SymCrypt, their main cryptographic library. Such progressions underscore the constantly changing environment of digital protection and the significance of employing strong, modern cryptographic techniques in the development of Java. By adopting these best practices, developers not only safeguard their applications but also align with the latest trends and insights in the tech sector, ensuring that their skills and output remain at the forefront of the industry's needs.
Avoid Insecure Serialization
'Java's serialization feature, which transforms objects into a byte stream, is crucial for storage and transmission. However, misuse can introduce serious security risks, such as deserialization of untrusted information, potentially leading to remote code execution. To protect applications, developers should only deserialize information from reliable sources, ensuring its integrity and authenticity. Alternatives like JSON or XML offer more secure deserialization control, mitigating these vulnerabilities.
In a telling case, the Telerik Report Server was scrutinized for its server-side processing of reports, demonstrating how serialized report data could be manipulated for exploitation. Likewise, GWT's serialization pattern, which deviates from Java's standard, demonstrates the importance of customized protective measures.
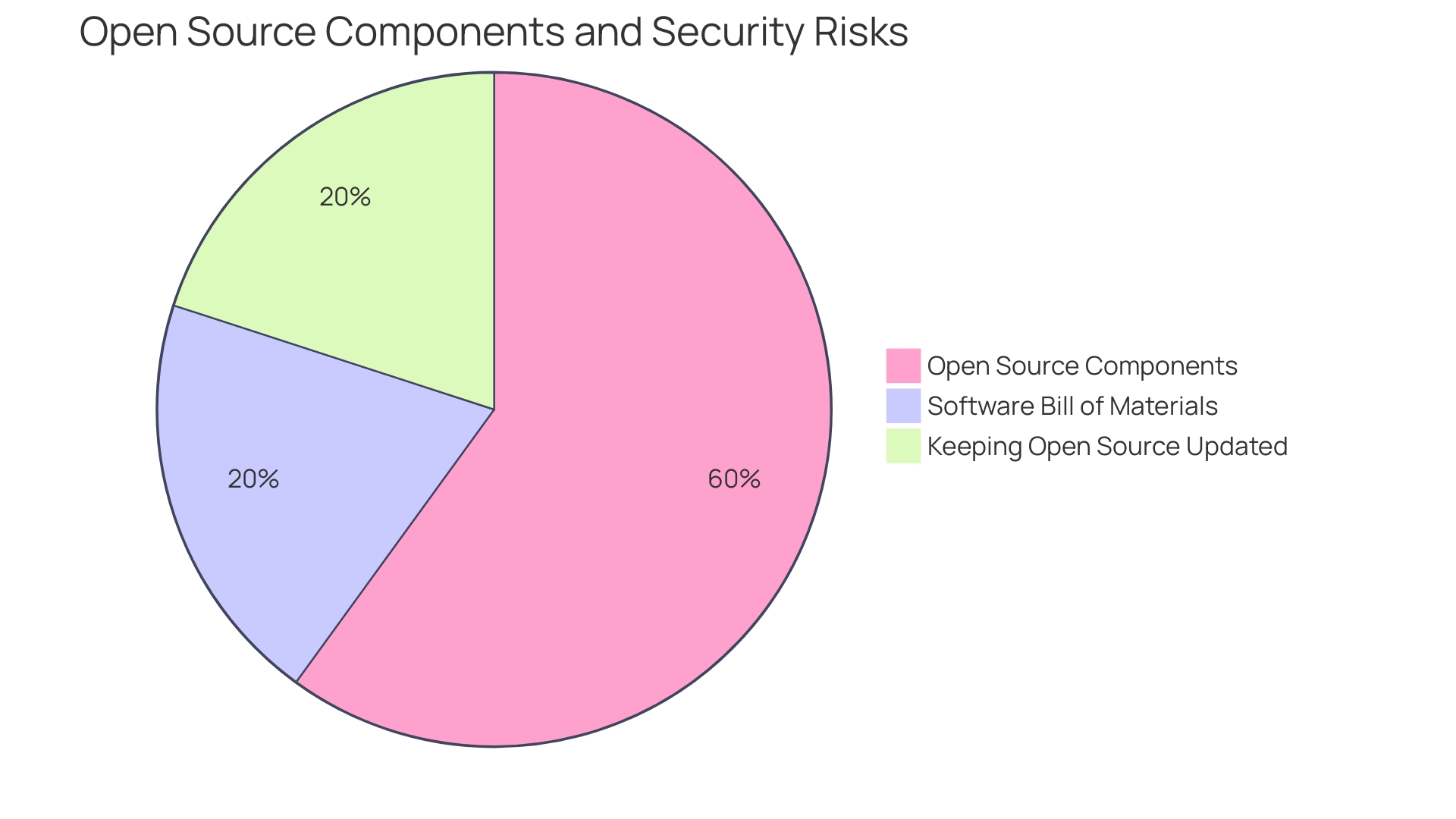
According to the 2024 OSSRA report, an astonishing 96% of scanned codebases included open source components, underscoring the crucial requirement for a comprehensive Software Bill of Materials (SBOM) and automated testing. With the average application containing 526 open source components, manual testing for safety is impractical, further advocating for automated solutions such as software composition analysis (SCA).
As encryption remains a foundation of safeguarding information, it is vital for developers using the programming language to utilize strong algorithms to secure sensitive data. Converting plain information into secret code guarantees that intercepted information stays incomprehensible to unauthorized individuals, with hashing suggested over encryption for passcodes to avoid unscrambling.
Ultimately, giving importance to data classification, implementing secure access controls, and adopting regular training are fundamental to maintaining a Java environment that is safe. These best practices, alongside informed choices about serialization and encryption, form the defensive bulwark necessary to protect against the ever-evolving landscape of cybersecurity threats.
Implement Secure Password Storage
To improve the security of user information, it is essential to prioritize secure storage of login credentials. Instead of keeping sensitive login information in plain text or using inadequate encryption, it is advisable to utilize strong hashing algorithms such as bcrypt or Argon2. Each user should have a unique salt added to their credential hash to further protect their credentials. Enforcing strong password policies, which may include requirements for minimum length and character diversity, is also essential for creating robust passwords.
The requirement for such strict measures is highlighted by the difficulties faced by organizations like British Telecom (BT), which is struggling with access management across different systems. With privileged access management (PAM), identity access management (IAM), and credential management being of paramount importance, the move towards dynamic credential management is imperative to thwart risks like supply chain attacks, exemplified by the SolarWinds incident.
The evolution of safety practices is also evident in the industry's shift towards passwordless authentication methods, pointing towards advancements that not only bolster security but also improve user experience. This is a critical balance to strike, as user experience often feels compromised by stringent security measures. Nevertheless, occurrences such as the LinkedIn, Yahoo, and GoDaddy data breaches, all caused by inadequate codes, demonstrate the vital importance of robust safeguarding mechanisms.
Given the extensive use of secret codes, ranging from online purchases to social networking, the significance of code administration cannot be overstated. A security tool, for example, acts as an encrypted storage for passwords, protected by a master passcode and, frequently, an extra verification element. Not only do managers streamline recall, but they also generate complex passwords, enhancing security.
Ultimately, implementing these best practices is not just about compliance with regulations or adhering to technical requirements; it's about instilling common sense practices into digital identity authentication and preventing the easily guessable credentials of the past. As statistics suggest, complex passwords at least 20 characters in length, incorporating numbers, uppercase and lowercase letters, and special symbols, are the way forward. Moving away from predictable patterns, like "SeasonYYYY," to more secure practices is imperative for safeguarding digital identities in an increasingly interconnected world.
Filter Sensitive Information from Exceptions
Java's exception handling is a sophisticated mechanism that allows developers to manage errors systematically. While exceptions are imperative for debugging, if not handled with discretion they can become a conduit for sensitive information exposure. It is essential to be vigilant about the information that exceptions might reveal to end-users or record in logs. For instance, rather than displaying intricate error details that might inadvertently include confidential data like database details or user credentials, it's advisable to present generalized error messages that are devoid of internal system information. Furthermore, utilizing strong exception handling techniques to smoothly intercept and handle exceptions is essential in preserving the integrity of information.
James Gosling, the creator of Java, underscores the importance of exceptions, highlighting how developers may overlook the significance of return codes, thus emphasizing the role of exceptions in error handling. In line with the 'Shift Left' movement in CI/CD practices, addressing exceptions and security concerns early in the development process is paramount. This proactive approach is similar to ensuring that a reliable individual handles sensitive salary information without disclosing exact figures—a metaphor for the need to manage code vulnerabilities without revealing precise details. Moreover, just like the process of de-identifying individual information in market research to safeguard privacy and promote confidence, comparable principles are relevant in exception handling to secure confidential code details while upholding functionality and user trust.
Validate All Inputs
To fortify Java applications against security threats, rigorous input validation is indispensable. Every piece of user-provided information, garnered through interfaces like forms and APIs or from outside entities, must be meticulously vetted. This diligence is the bulwark against pernicious attacks such as SQL injection, XSS, and command injection. By deploying vetting techniques—utilizing regular expressions, employing validation libraries—you ensure compliance with predetermined formats and constraints.
It's prudent to adopt a resilient input validation system that proactively identifies and obstructs injurious inputs, safeguarding the integrity of your application's data. Institutions such as M&T Bank, with their strong background in banking and forward thinking in digital innovation, emphasize the importance of clean coding standards to enhance software dependability and safety. Similarly, static application security testing (SAST) has been recognized as a critical tool in the developer's arsenal to identify vulnerabilities early in the development process.
Verification and validation stand as twin pillars in the continuous quest for quality in software development. As elucidated by industry experts, verification is about ensuring 'we are building the product right,' with a clear understanding of requirements and a design that meets those specifications. This proactive approach significantly diminishes the risk of costly errors in the final product. The alignment of verification with validation ensures that not only is the product built right, but it also fulfills the actual needs and expectations of users.
Use Strong Data Encryption
Ensuring the confidentiality and integrity of sensitive information is crucial to the development of Java applications, especially in sectors where privacy is of utmost importance, like banking and healthcare. It is crucial to utilize strong encryption algorithms and cryptographic practices to render information unreadable to unauthorized users. For example, encrypting passwords is not recommended since we don't want the potential to reverse engineer the original text; instead, we use hashing to protect such sensitive information.
Java cryptographic APIs and libraries can be used for encrypting other types of sensitive information, such as credit card numbers or personal identification information. It is critical to manage encryption keys securely and to avoid hardcoding them into the source code, as this can be a significant vulnerability. Furthermore, implementing secure communication protocols, like HTTPS, ensures that information remains encrypted during transmission, adding an additional layer of protection against interception.
With the ever-increasing expense of breaches, reaching a record high average cost in recent years, the stakes for safeguarding information have never been higher. By leveraging strong data encryption and management practices, developers can significantly reduce the risk of data breaches and maintain the trust of their customers and users.
Implement Access Control Mechanisms
Securing Java applications demands meticulous attention to access control, a defense mechanism that ensures sensitive resources are only accessible to vetted individuals. Adopting Attribute-Based Access Control (ABAC) can be likened to a security protocol at an amusement park where access to rides is determined by specific qualifications, such as height; similarly, ABAC uses user, resource, or environmental attributes to manage access rights. Conversely, Role-Based Access Control (RBAC) provides access based on predefined roles, which may lack the granularity needed in complex systems.
Consider the scenario at Maricopa County's Recorder's Office, which juggles the voting data for a massive electorate. The office transitioned from RBAC to a more nuanced ABAC system to handle the intricate access demands of its extensive and ever-changing staff, particularly during election cycles. This move underscores the necessity for precision in access management, a lesson that Java developers can apply to their applications.
Besides ABAC, it is essential for access controls to be present everywhere throughout all system layers, including the database level, to establish a strong architecture for protection. Regular audits and updates of these policies are imperative to ensure they remain current with evolving organizational structures and system enhancements.
Authentication and authorization are twin pillars of protection, often mixed up yet separate. Authentication confirms identity, akin to presenting a ticket at Disneyland's entrance, whereas authorization determines access post-entry. Fine-grained authorization, a more precise subset, evaluates specific user and resource attributes to tailor access rights, adapting to dynamic conditions and contexts.
Empirical evidence from ASIS International's study, 'The Essentials of Access Control,' which consulted over 1,000 professionals, underscores the critical nature of advanced access control systems in safeguarding assets. As the programming language continues to progress, with Oracle recognizing the community's efforts in sustaining its dynamism, developers are tasked with ensuring their applications reflect these evolving practices, including the implementation of sophisticated access control mechanisms.
Follow the Principle of Least Privilege
The practice of least privilege is crucial in writing secure code, ensuring that users have only the necessary permissions for their roles. This approach significantly reduces the risk of breaches by limiting the attackable surface area. For example, consider a scenario where an AWS account was compromised because of unauthorized SES limit increase requests. The incident highlights the importance of vigilance in permission assignments. Similarly, in platforms like ServiceNow, access can be granularly controlled down to specific fields within a database table, emphasizing the need for careful privilege management.
In the context of Zero Trust Security, which operates under the mantra of “never trust, always verify,” the principle of least privilege integrates seamlessly. It mandates that constant verification is essential, and by applying this to code development in the Java programming language, each user's access rights are meticulously scrutinized and restricted to what is strictly necessary.
Furthermore, with 83% of organizations having experienced breaches due to compromised credentials, the urgency for strict access control is clear. It's not just about protecting against external threats but also about safeguarding against potential internal risks. Regular audits of user permissions are not just a good practice; they are a critical defense mechanism, as evidenced by Silverfort's intuitive interface that displays access types across different user categories, enhancing visibility and control.
Incorporating the principle of least privilege into the best practices of programming not only aligns with the Zero Trust framework but also with the modern cybersecurity landscape's demands. It's a strategy that supports the ongoing battle against the increasingly sophisticated identity-based attacks threatening our interconnected digital ecosystems.
Regularly Update and Patch Dependencies
Java development involves leveraging third-party libraries and frameworks, which, while essential, also carry potential risks if not properly managed. The key to safeguarding your applications is vigilant maintenance of these dependencies. Consistently updating and patching them guarantees the integration of latest patches and enhancements, which is crucial for maintaining robust standards.
Recent updates, like those in Spring Boot versions 3.1.5, 3.0.12, and 2.7.17, emphasize the significance of keeping up to date with bug fixes and enhancements. Notably, these updates addressed an issue with the spring.jms.listener.concurrency property, aligning it with the documented expected behavior. This correction emphasizes the need for developers to adjust their configurations accordingly.
Tools like Maven and Gradle streamline the update process, allowing for easier management of dependencies and their versions. For example, Spring Security's release candidates and service releases illustrate the inclusion of new features and dependency upgrades, which developers can adopt efficiently using such tools.
In the face of supply chain attacks, understanding your project's dependencies is more than just a good practice—it's a defense mechanism. The discovery of major vulnerabilities in widely-used apps like Google and TikTok reinforces the importance of transparency and proactive measures in minimizing risks. Additionally, the alarming use of abandoned libraries in significant projects serves as a cautionary tale about the chaos that can ensue without proper dependency management.
According to Sharat Chander of Oracle, the vibrancy of this programming language is a testament to the community's ongoing commitment to advancement and safety. A well-maintained codebase not only contributes to the ecosystem's strength but also reflects a developer's dedication to excellence and awareness of safety.
Use Secure Coding Techniques and Best Practices
To enhance the protection of Java applications, it's essential to adhere to established secure coding standards and practices. These include robust input validation to fend off injection attacks; meticulous output encoding to prevent cross-site scripting; steadfast session management to avert session hijacking; and prudent error handling to avoid information leakage. The Open Web Application Security Project (OWASP) provides a comprehensive set of guidelines that act as a guide for safe coding, assisting developers in navigating the complex terrain of software protection.
Furthermore, adopting static application testing (SAST) is essential in the proactive identification of vulnerabilities within your code. SAST scrutinizes the source code or bytecode to unearth vulnerabilities that could be exploited in a cyber attack. In accordance with the 'Shift Left' philosophy in CI/CD, incorporating protective measures early in the software development life cycle is crucial. This proactive approach ensures that potential security issues are addressed at the genesis of development, thereby embedding security into the very fabric of the application.
In the realm of encryption, it's essential to discern when and how to employ this technique. Encrypting information converts it into a cipher, protecting it from unauthorized access. However, it's crucial to recognize scenarios where irreversible data transformation is more appropriate, such as with passwords, where the objective is to prevent the recovery of the original text.
Ongoing education through regular training is the foundation of maintaining a security-conscious mindset among development teams. With the ever-evolving nature of cybersecurity threats, it's critical that teams are equipped with up-to-date knowledge on threat landscapes and mitigation strategies. A combination of interactive workshops, online courses, and scenario-based training can effectively instill a culture of proactive safety practices.
Lastly, understanding the composition of your code is a linchpin in securing your software supply chain. The 2024 Open Source Security and Risk Analysis (OSSRA) report underscores the importance of visibility into the open source components within your code. With an average of 526 open source components per application, manual security testing is no longer viable. Automated solutions like software composition analysis (SCA) are indispensable for managing the complex tapestry of open source usage within modern software development.
Conclusion
In conclusion, enhancing Java application security requires developers to implement a set of best practices and secure coding techniques. By utilizing tried and tested libraries, developers can incorporate security measures that have proven effective in combating vulnerabilities. Secure password storage is crucial, and the use of robust hashing algorithms and strong password policies help protect user credentials.
Filtering sensitive information from exceptions and implementing input validation are essential to prevent data exposure and fortify applications against attacks like SQL injection and XSS. Strong data encryption ensures the confidentiality and integrity of sensitive data, while access control mechanisms like ABAC and RBAC restrict access to authorized individuals. Following the principle of least privilege reduces the risk of security breaches, and regularly updating and patching dependencies is crucial for maintaining robust security standards.
Finally, adhering to secure coding techniques and best practices, along with continuous security training, helps developers stay ahead of evolving threats. By implementing these strategies, Java developers can ensure maximum efficiency and productivity while maintaining the integrity and security of their applications.
Start using tried and tested libraries today to enhance the security of your Java applications!
Frequently Asked Questions
Why is it important to use established libraries in Java development?
Using established libraries that have been thoroughly vetted and tested is critical for crafting secure Java code. These libraries are developed by a vast open-source community and have proven their reliability and safety, helping developers effectively combat vulnerabilities.
What role does encryption play in securing sensitive information in Java applications?
Encryption is essential for ensuring data integrity and confidentiality, especially when handling sensitive information like customer data or financial transactions. Developers are encouraged to implement strong encryption algorithms to protect this data.
Why is hashing preferred over encryption for password management?
Hashing is preferred because it transforms passwords into a fixed-length string that cannot be reversed to retrieve the original text, enhancing security. This method protects sensitive information more effectively than encryption.
What are the risks associated with Java's serialization feature?
Java's serialization can introduce security risks like deserialization of untrusted information, which may lead to remote code execution. Developers should ensure that they only deserialize information from trusted sources.
How can developers prevent vulnerabilities related to deserialization?
To mitigate vulnerabilities, developers should use safer alternatives like JSON or XML for serialization, which offer better control over data integrity and authenticity.
What is the significance of a Software Bill of Materials (SBOM) and automated testing?
With a high percentage of codebases containing open-source components, an SBOM is crucial for tracking these components. Automated testing, such as software composition analysis (SCA), is essential for quickly identifying vulnerabilities and ensuring the safety of these components.
What best practices should developers follow for secure password storage?
Developers should use strong hashing algorithms like bcrypt or Argon2, implement unique salts for each user's credentials, and enforce robust password policies to ensure secure storage of login credentials.
How does access control enhance the security of Java applications?
Access control ensures that sensitive resources are accessible only to authorized individuals. Implementing systems like Attribute-Based Access Control (ABAC) allows for more precise management of access rights compared to Role-Based Access Control (RBAC).
What is the principle of least privilege and why is it essential?
The principle of least privilege restricts users' permissions to only what is necessary for their roles, significantly reducing the risk of breaches and limiting the attack surface.
Why is regular maintenance of third-party libraries important?
Regularly updating and patching third-party libraries ensures that applications benefit from the latest security enhancements and bug fixes, protecting against vulnerabilities.
What are some key secure coding practices for Java developers?
Key practices include robust input validation, output encoding, secure session management, and prudent error handling. Following guidelines from the Open Web Application Security Project (OWASP) can also help developers navigate secure coding.
How can ongoing education contribute to security-conscious development teams?
Regular training and education keep development teams informed about evolving cybersecurity threats and best practices, fostering a proactive security culture within organizations.
What tools can assist in managing open source dependencies?
Tools like Maven and Gradle can streamline the process of updating dependencies, ensuring that developers can efficiently manage their libraries and frameworks while maintaining security standards.




