Introduction
In an era where the prevalence of web applications and software systems is on the rise, the safeguarding of API keys has become paramount. These keys act as strongholds, regulating access to specific data and functionalities.
However, with the increasing number of API infringements and unauthorized data access, the need for efficient API key management is more important than ever. In this article, we will explore the benefits of using Kodezi, an AI-powered development platform, to enhance the security of API keys.
With industry-standard encryption and robust security measures, Kodezi ensures that your code remains fully protected. We will also delve into best practices for generating and managing API keys, as well as troubleshooting common key-related issues.
By implementing these strategies, developers can create a secure environment, protect sensitive information, and mitigate potential damages from cyber incidents. Furthermore, we will discuss the significance of monitoring and auditing API key usage to identify any abnormal patterns or unauthorized access attempts. Lastly, we will highlight the advanced API key management techniques offered by Kodezi, such as multi-factor authentication and encryption, that can significantly enhance code security. With Kodezi's commitment to privacy and security, developers can have peace of mind knowing that their API keys and the data they unlock are in safe hands.
Understanding API Keys and Their Importance
The expansion of web applications as digital cornerstones has put APIs in the spotlight, with their ability to connect diverse software systems becoming increasingly more common. Yet, this prevalence brings about significant security concerns, especially around API keys.
These keys are essential, acting as strongholds by regulating who gets entry to specific data and functionalities. In an era where API infringements are surging, resulting in unauthorized data access and serious repercussions like identity theft and financial fraud, the mastery of API key management is not merely a technicality but an absolute necessity for the protection of our digital domain.
Enhancing the security of these keys has become paramount and Kodezi offers a robust solution. As an AI-powered development platform, Kodezi ensures your code remains shielded with industry-standard 256-bit AES encryption, never storing your data but fully encrypting it. Additionally, with SOC 2 Type II compliance and SSL encryption for data in transit, Kodezi provides a secure environment for analyzing and debugging code. Kodezi's commitment to maintaining the highest level of security for your digital infrastructure is unwavering, making it an indispensable tool in the battle against API vulnerabilities and ensuring that your digital keys only open doors for the right reasons.
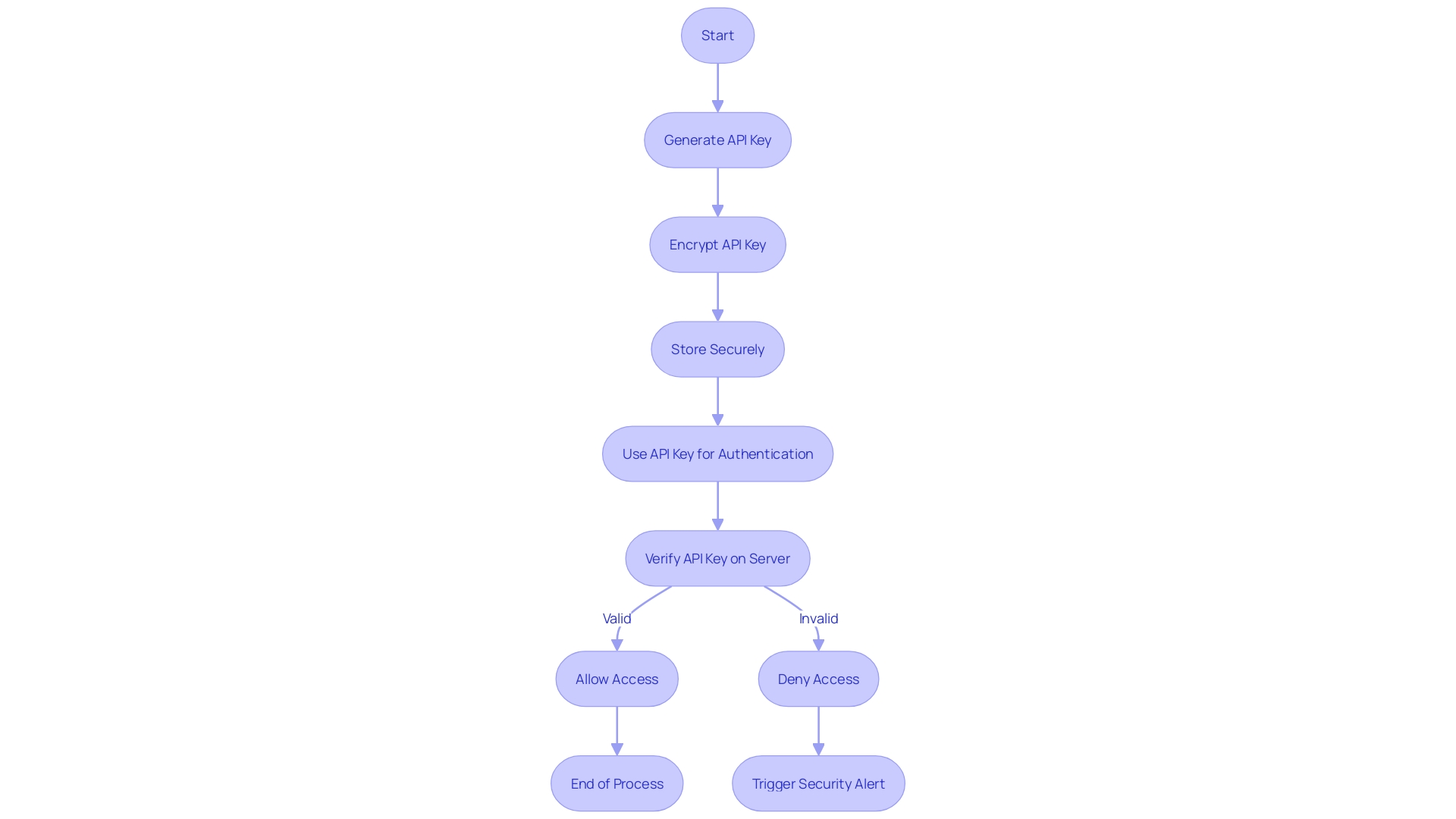
How to Generate API Keys
Understanding how to create API keys is crucial for safeguarding your applications. With the surge in web applications and interconnectivity, ensuring that API keys are robust is not just good practice; it's critical to preventing breaches that could result in the exposure of sensitive data.
To fortify your code against unauthorized access, a multifaceted approach is necessary. Strong encryption must be the cornerstone of your strategy.
Utilize advanced algorithms to ensure that your API keys remain impenetrable. Beyond encryption, the safekeeping of these keys is paramount.
This means avoiding common pitfalls like hard-coding them into your source code or leaving them in plain text files. Instead, you should invest in secure storage solutions. Key rotation is another key element in maintaining API security over time. It acts as a failsafe, ensuring that even if a key does get compromised, its window of usage—and consequential damage—is limited. By incorporating these methods into your development process, you create a secure environment that keeps the integrity of your APIs intact, and ultimately, protects the precious data they govern.
Managing API Keys
In the digital age, the prominence of application programming interfaces (APIs) stands out as a testament to their crucial role in enabling software interactions. Yet, with rising popularity comes the escalation of API breaches—incidents where unauthorized figures exploit APIs to access sensitive information.
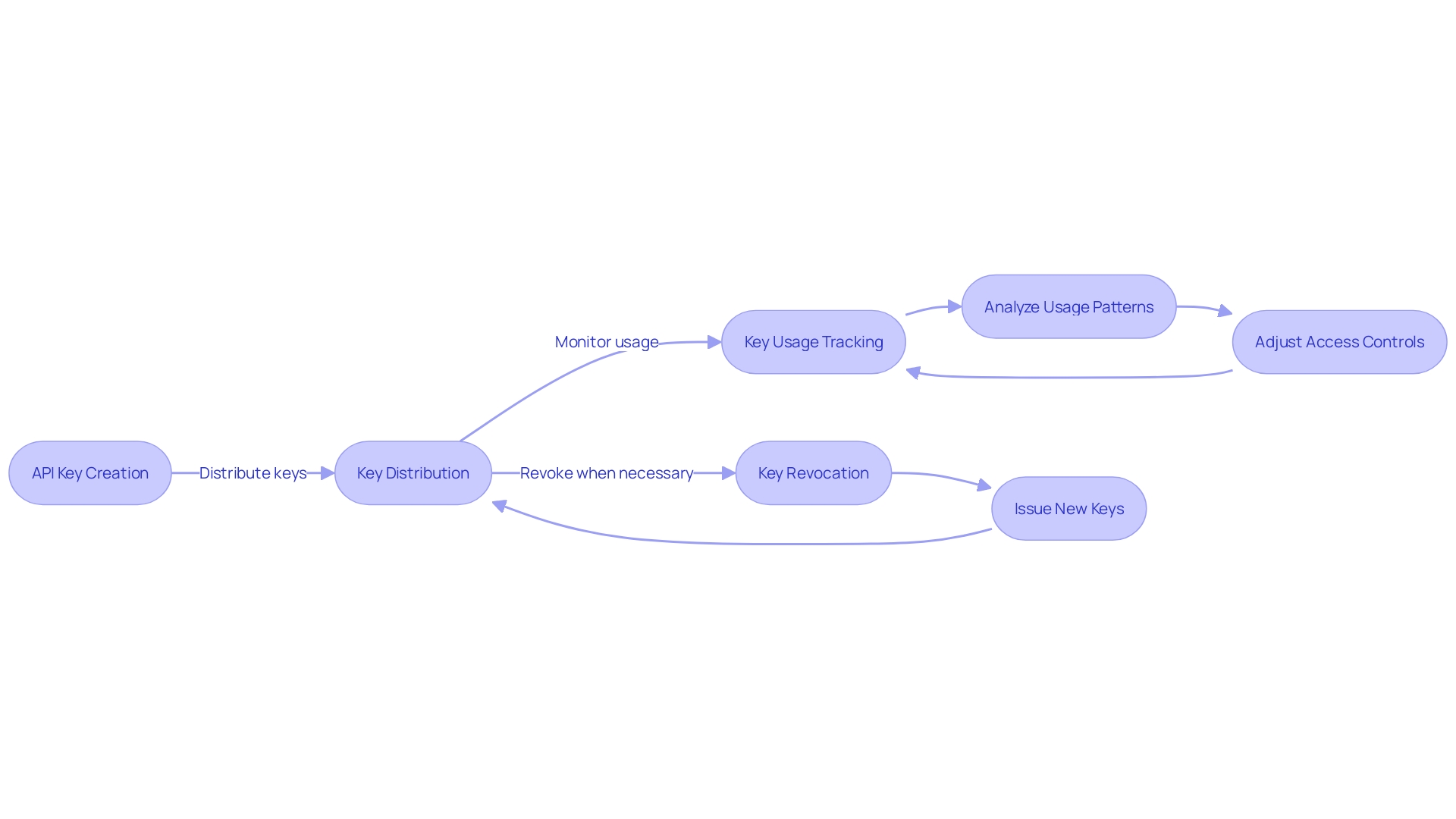
Effective API key management emerges as an indispensable defense against these breaches. It involves strategies to safeguard the unique keys that grant access to an API's functions.
Fundamental to this safeguarding is the meticulous distribution of API keys, ensuring that keys are only in trusted hands. Equally critical is the capacity to revoke keys swiftly when they are compromised or no longer needed. Tracking key usage is another pillar to consider, providing transparency over who is using the keys and for what purpose. Diligently monitoring and controlling API key access can act as a robust barrier against unauthorized use, curtailing the risk of data exposure and mitigating potential damages from cyber-incidents.
Best Practices for API Key Security
As web applications and digital platforms proliferate, application programming interfaces (APIs) have become fundamental to software development, enabling seamless communication between applications. However, their widespread use has ushered in an era marked by a surge in API security breaches. The ramifications of such breaches are profound, often leading to the exposure of sensitive data, which, if compromised, can result in identity theft or fraudulent activities.
In response to these looming threats, adhering to API key security best practices is not just recommended but vital for developers aiming to secure their codebases. To mitigate unauthorized access and potential data breaches, certain strategies are paramount. Tokenization, an effective security measure, helps in replacing sensitive data with unique identification symbols, rendering it indecipherable outside of the secured platform.
Meanwhile, role-based access control (RBAC) ensures that only authorized personnel with clearly defined permissions can access certain API functions, thereby minimizing the potential for misuse or unauthorized entry. Additionally, defining API key scopes to limit access to specific areas within an API can significantly constrict the avenues for exploitation. Investing in these API key security methodologies creates a robust foundation for generating secure applications, shielding them from the escalating dangers of API breaches and protecting the cherished trust of users and businesses alike.
Troubleshooting API Key Issues
API keys are essential for secure communication between applications. They're used so frequently in today’s digital landscape that they've become a prime target for malicious entities. Given their importance and ubiquity, it's crucial for developers to have strategies in place to resolve key-related issues swiftly, preventing unauthorized access and data exposure.
Issues like authentication errors, key expiration, and misconfigured permissions are common stumbling blocks that can lead to far-reaching impacts if not resolved promptly. By adeptly handling these situations, developers can shield APIs—which often contain sensitive personal or financial information—from vulnerabilities, maintaining the integrity of the software and the privacy of end-users. To safeguard against the tangible risks of API breaches, such as identity theft and fraudulent activities, developers must be skilled in troubleshooting and neutralizing API key vulnerabilities, thereby fortifying their applications' defense against potential cyber threats.
Monitoring and Auditing API Key Usage
To safeguard the security of a codebase, it's critical to implement stringent monitoring and auditing measures for API key usage. Tools designed to monitor API key usage are not only about tracking what keys exist but also examining APIs’ action logs meticulously to detect any abnormal patterns or unauthorized access attempts.
Regular security audits, including reviews of API key access patterns, play a crucial role in preemptively identifying potential vulnerabilities. Vigilant oversight and immediate action upon detecting irregularities help uphold the code's integrity, reducing the risk of security breaches. It's imperative for developers to be proactive in these efforts to maintain the highest standard of code security and manage vulnerabilities effectively.
Enhancing Code Security with Advanced API Key Management Techniques
API keys are the gatekeepers to our digital products, and robust security is not just a bonus; it's a necessity. With the increase in digital threats, especially concerning APIs, stepping up your security game is a must. One essential rule of thumb is to beef up your API key management.
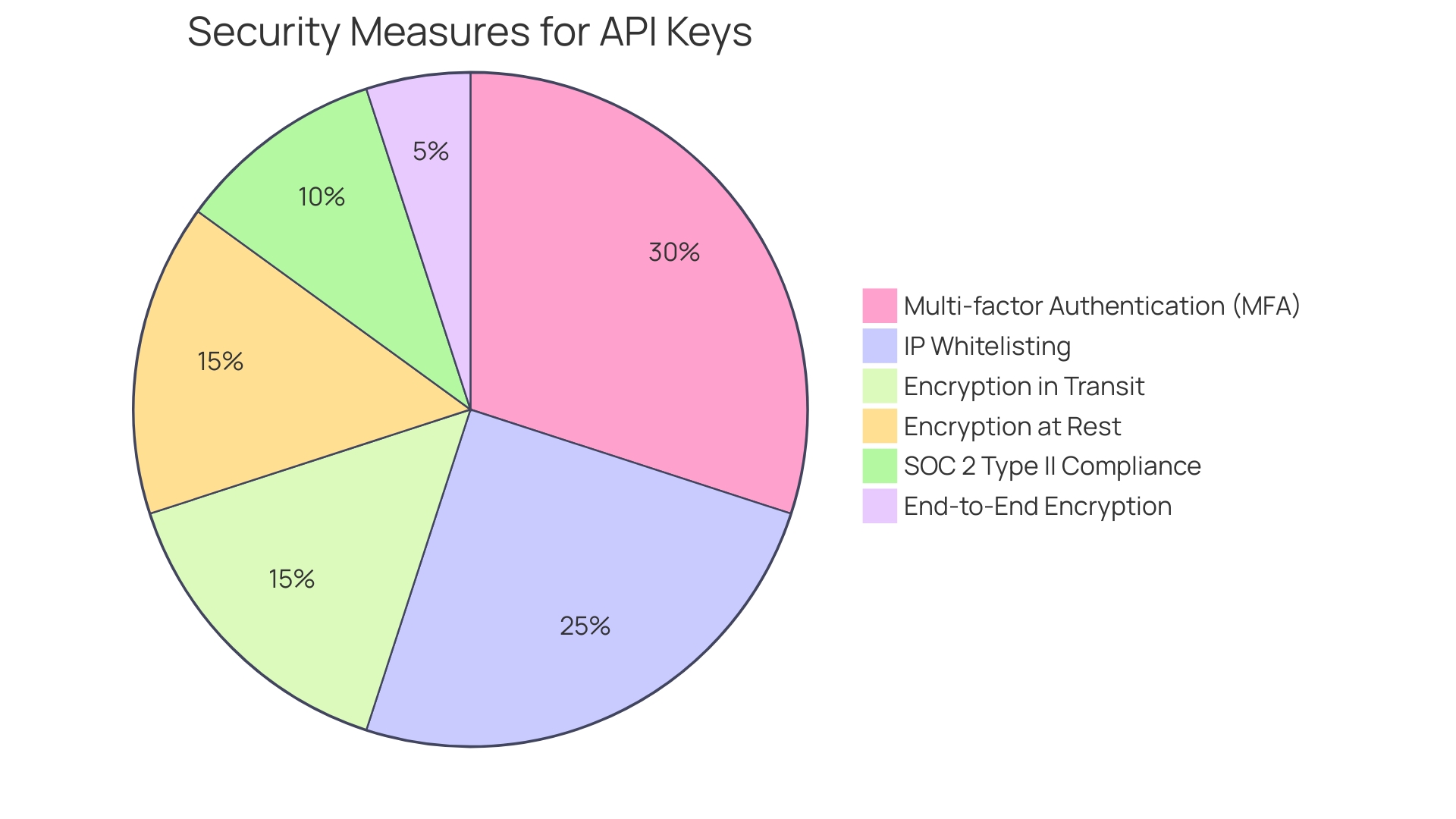
Introducing multi-factor authentication (MFA) is more than just a trend; it's an added security checkpoint that makes unauthorized access exponentially harder. This, coupled with IP whitelisting, puts you in control, only allowing signals from trusted sources to pass through your digital domain—it's like having a personalized firewall. And let's talk about encryption—this isn't just spiraling jargon, it's the cornerstone of securing data as it travels across the web (transit) and while it's not actively being used (at rest).
It's what keeps your sensitive data locked away from prying eyes. Now, with Kodezi, there's no compromise on security. Kodezi brings to the table top-of-the-line 256-bit AES encryption and SSL encryption for data during transit.
That's akin to layering your data in armor, both when it's stored and when it's traveling through the digital realm. And let's not forget Soc 2 Type II compliance—this isn't just a badge, it's a commitment to rigorous standards. Kodezi's unwavering stance on privacy and security extends beyond the nuances of encryption; it reflects through their no-data-storage policy and their proprietary models designed in-house.
It guarantees that your code is never stored and fully secured, ensuring peace of mind for developers, teams, and anyone taking their code security seriously. To top it all off, Kodezi offers end-to-end encryption, fortifying your code from unintended breaches. This is where efficiency meets security head-on, ensuring that your API keys, and the data they unlock, remain in safe hands.
Conclusion
In conclusion, safeguarding API keys is crucial in the current era of web applications. Kodezi, an AI-powered development platform, offers robust security measures like encryption and compliance standards to protect code and data.
Implementing best practices such as strong encryption, secure storage, and key rotation helps create a secure environment. Efficient API key management, including careful distribution, swift revocation, and tracking of key usage, is essential to prevent unauthorized access.
Adhering to API key security best practices, like tokenization and role-based access control, enhances code security. Monitoring and auditing API key usage help identify vulnerabilities and maintain code integrity.
With Kodezi's commitment to privacy and security, developers can trust that their API keys and data are safe. The platform's advanced techniques, like multi-factor authentication and encryption, prioritize security without compromising efficiency. By implementing these strategies and leveraging Kodezi's capabilities, developers can protect sensitive information, mitigate cyber risks, and create a secure environment. In summary, with Kodezi, developers can enhance code security, safeguard valuable data, and mitigate potential damages from cyber incidents. By following best practices and utilizing the platform's advanced features, developers can ensure that their API keys remain secure and their applications are protected.
Protect your API keys and data with Kodezi's robust security measures!
Frequently Asked Questions
What are API keys and why are they important?
API keys are unique identifiers used to authenticate and regulate access to specific data and functionalities provided by an API. They are important because they help maintain the security of web applications by controlling who can access sensitive information, thereby protecting against unauthorized data access and potential identity theft or financial fraud.
How does Kodezi enhance the security of API keys?
Kodezi enhances API key security through several methods, including industry-standard 256-bit AES encryption to protect your code, SSL encryption for data in transit, and a strict policy of not storing user data. With SOC 2 Type II compliance, Kodezi provides a secure environment for code analysis and debugging.
What are some best practices for generating secure API keys?
Best practices for generating secure API keys include using strong encryption algorithms to ensure keys remain secure, avoiding hard-coding keys into source code, investing in secure storage solutions, and implementing key rotation to limit the window of usage if a key becomes compromised.
Why is effective API key management important?
Effective API key management is critical for defending against API breaches, where unauthorized entities exploit APIs to access sensitive information. It involves strategies to safeguard API keys, meticulous distribution, swift revocation when compromised, and tracking key usage to provide transparency and control access, thus reducing the risk of data exposure.
What security methodologies can be used to protect API keys?
Security methodologies to protect API keys include tokenization, which replaces sensitive data with unique identification symbols, role-based access control (RBAC) to ensure only authorized personnel can access certain API functions, and defining API key scopes to limit access to specific areas within an API.
What common issues can arise with API keys?
Common issues with API keys include authentication errors, key expiration, and misconfigured permissions. These can lead to vulnerabilities in the software and potential data exposure if not promptly resolved.
How should developers monitor and audit API key usage?
Developers should implement stringent monitoring and auditing measures for API key usage, such as tracking existing keys, examining APIs’ action logs for abnormal patterns or unauthorized access attempts, and regularly conducting security audits to identify potential vulnerabilities.
What advanced management techniques can enhance code security for APIs?
Advanced API key management techniques that can enhance code security include multi-factor authentication (MFA), IP whitelisting to allow access only from trusted sources, and encryption of data both in transit and at rest. Kodezi supports these techniques by providing 256-bit AES encryption, SSL encryption for data in transit, and SOC 2 Type II compliance to ensure high security standards.




