Introduction
The concept of secure coding is not just a best practice, but a critical component in crafting resilient and trustworthy software applications. It serves as a vital defense against an array of vulnerabilities and potential cyber-attacks. M&T Bank, a seasoned institution in the financial sector, exemplifies this through its adoption of Clean Code standards, recognizing the inherent risks and astronomical costs associated with deploying software that fails to meet stringent security benchmarks.
With banking's digital evolution, steering through a landscape fraught with security perils and regulatory demands, M&T Bank's initiative underscores the gravity of establishing and maintaining high-quality coding practices. In the context of modern software development, understanding the anatomy of your software is paramount. This includes the originality of the code, whether it's a fork and if so, the nature of the alterations.
Furthermore, the software supply chain, which encompasses everything from the developer's IDE to the OS on which the software operates, is riddled with potential vulnerabilities that can be exploited maliciously.
Why Secure Coding is Essential
The concept of secure coding is not just a best practice, but a critical component in crafting resilient and trustworthy software applications. It serves as a vital defense against an array of vulnerabilities and potential cyber-attacks. M&T Bank, a seasoned institution in the financial sector, exemplifies this through its adoption of Clean Code standards, recognizing the inherent risks and astronomical costs associated with deploying software that fails to meet stringent security benchmarks.
With banking's digital evolution, steering through a landscape fraught with security perils and regulatory demands, M&T Bank's initiative underscores the gravity of establishing and maintaining high-quality coding practices.
In the context of modern software development, understanding the anatomy of your software is paramount. This includes the originality of the code, whether it's a fork and if so, the nature of the alterations. Furthermore, the software supply chain, which encompasses everything from the developer's IDE to the OS on which the software operates, is riddled with potential vulnerabilities that can be exploited maliciously.
The security incidents of 2023, where critical secrets were exposed in plain text, serve as a stark reminder of the perils lurking within the software supply chain. To battle these threats, the industry is gravitating towards the concept of a software Bill of Materials (BOM), offering transparency and tracking of all components that constitute a piece of software.
In terms of security measures, the Security Development Lifecycle (SDL) approach has been widely championed by major corporations. It mandates that all personnel involved in software creation, from full-time employees to contractors, are well-versed in cyber security fundamentals and secure development practices. This begins with defining precise security and privacy requirements that evolve with the product's lifecycle, influenced by the type of data processed, known threats, and regulatory standards.
Threat models are pivotal in this process, highlighting potential risks through data flow diagrams which depict the interactions of data types and protocols.
The necessity of a Software Bill of Materials (SBOM) for managing the software supply chain has never been more evident. With the rise of AI-generated code and the ubiquity of open source components, it's crucial to have a comprehensive understanding of the contents within your code. The 2024 OSSRA report highlights that a staggering 96% of commercial software contains open source elements, with an average of 526 components per application.
This reinforces the essential role of automated security testing, as manual efforts become unfeasible at scale.
Google's experience in reinforcing developer ecosystems shows that focusing on Safe Coding can dramatically decrease common defects across numerous applications. This strategy is two-pronged: preventing bugs through safe coding patterns and automated solutions like software composition analysis (SCA), which scrutinize open source components within your code for vulnerabilities, licensing issues, and code quality risks.
Key Principles of Secure Coding
Adhering to OWASP's secure coding principles is not just a technical requirement but a strategic imperative, especially in industries dealing with sensitive data, such as banking. For instance, M&T Bank, with its considerable legacy and expansive digital footprint, must mitigate risks associated with software vulnerabilities to protect customer data and maintain trust. Secure coding practices, such as input validation, applying the principle of least privilege, and ensuring systems fail securely, are essential to their digital strategy.
They are part of a broader culture of security by design, where security is not a bolt-on feature but an integrated aspect of the software development lifecycle. This approach is supported by evidence, such as a guide on high-priority cyber threats, which emphasizes the importance of incorporating security requirements from the early stages of planning and design to maintenance. Moreover, regular security training is highlighted as a cornerstone of a security-aware culture, with a focus on continuous education to keep pace with evolving cybersecurity threats.
Incorporating these practices allows organizations like M&T Bank to not only avoid the high costs associated with security breaches but also to build a foundation of secure operations that reinforces their market position in a competitive and rapidly changing industry.
Secure Defaults and Least Privilege
To enhance software security, it's crucial to establish secure defaults and adhere to the principle of least privilege. Secure defaults ensure that only the safest settings are enabled without user intervention, reducing the risk of exploitation. For instance, consider a scenario where individuals wish to compare salaries without disclosing exact figures.
A parallel in software would be ensuring no backdoor in the code compromises data confidentiality.
Additionally, applying the principle of least privilege is akin to assigning a trusted person to handle sensitive salary data; it ensures users have the minimum access required, minimizing the security breach impact. With cyber threats constantly evolving, regular security training becomes indispensable, empowering teams to stay ahead of vulnerabilities.
SQL vulnerabilities serve as a pertinent example, highlighting the need for developers to understand and safeguard against such weaknesses. Effective security measures also include continuous scrutiny and management of machine identities and secrets within the code. A proactive approach involves detecting long-lived secrets and ensuring their secure management through centralized systems.
Statistics highlight that organizations are increasingly prioritizing software security. Although secure coding practices from literature are applied in practice, there's room for improvement in formalizing these into standardized processes. Embracing secure coding practices and integrating them into the development workflow is fundamental to building robust, secure applications in today's digital landscape.
Defense in Depth and Fail Securely
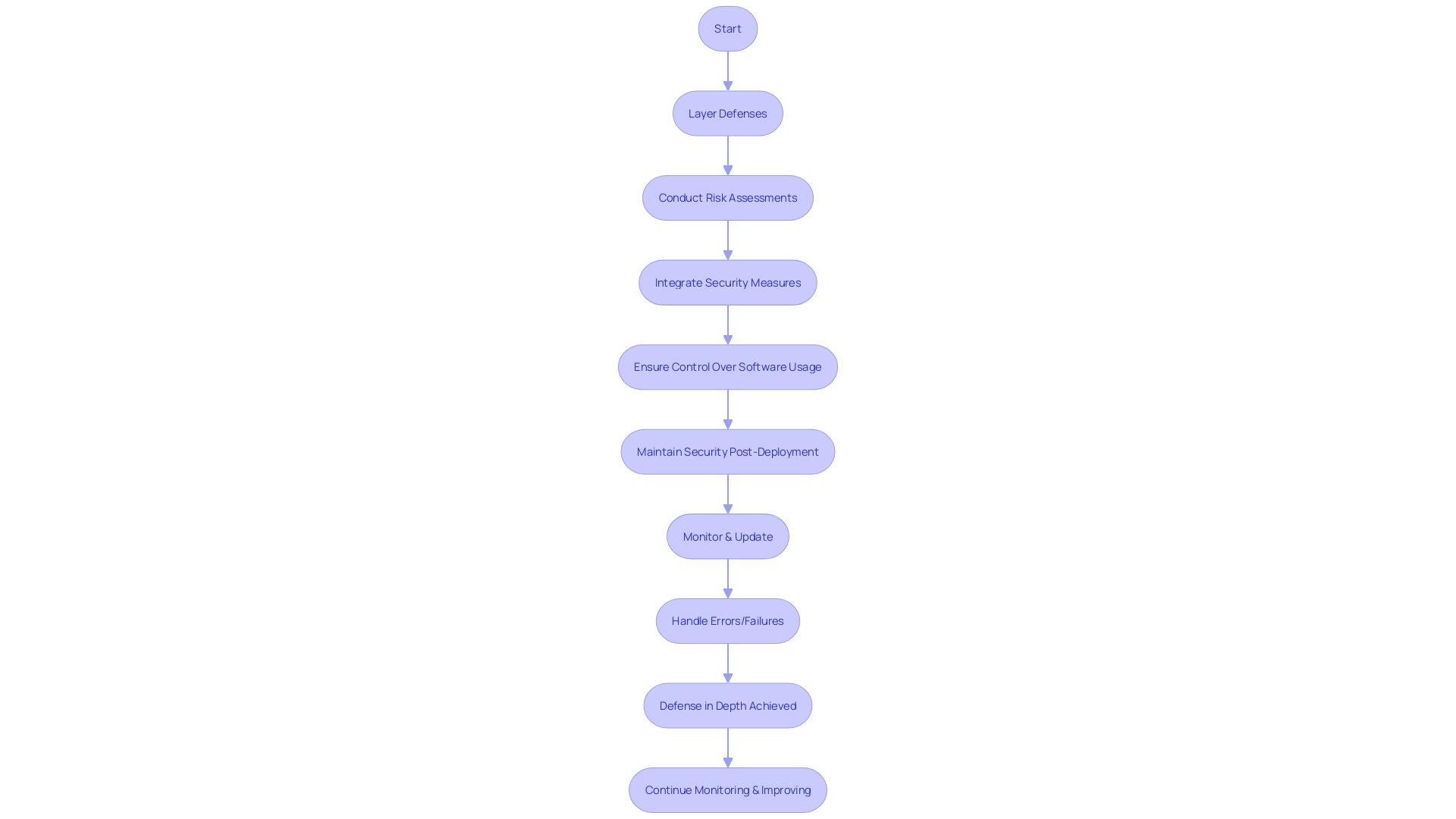
The principle of defense in depth is akin to fortifying a castle with multiple layers of defense, not just a single drawbridge. It is the practice of layering defenses to protect software against a variety of threats. By examining the structure of projects and understanding their components—whether original code or modified forks—one can better secure the software supply chain.
The recent emphasis on securing these chains, as seen in significant cybersecurity incidents where exposed secrets caused havoc, underpins the importance of this multi-tiered approach.
Furthermore, implementing a 'fail securely' strategy ensures that, in the event of an error or failure, the system does not compromise sensitive information. This idea is central to creating resilient software that maintains security even when things go wrong. As the adoption of OAuth demonstrates, ease of implementation does not guarantee simplicity behind the scenes; a robust authorization protocol is complex and full of nuances that must be secured at each layer.
Considering the closed-source software's approach to security—where code confidentiality makes it tougher for attackers to exploit vulnerabilities—highlights the need for control over who can use your software. This control is a part of the defense in depth, ensuring that security isn't just an afterthought but is designed into the very fabric of your software from the beginning. As advocated by experts in the field, integrating risk assessments throughout the development process not only enhances product quality but also saves time and resources by addressing issues early on.
These strategies, when combined, form a comprehensive framework for secure coding practices that stand up to the multifaceted nature of today's cybersecurity challenges.
Secure by Design
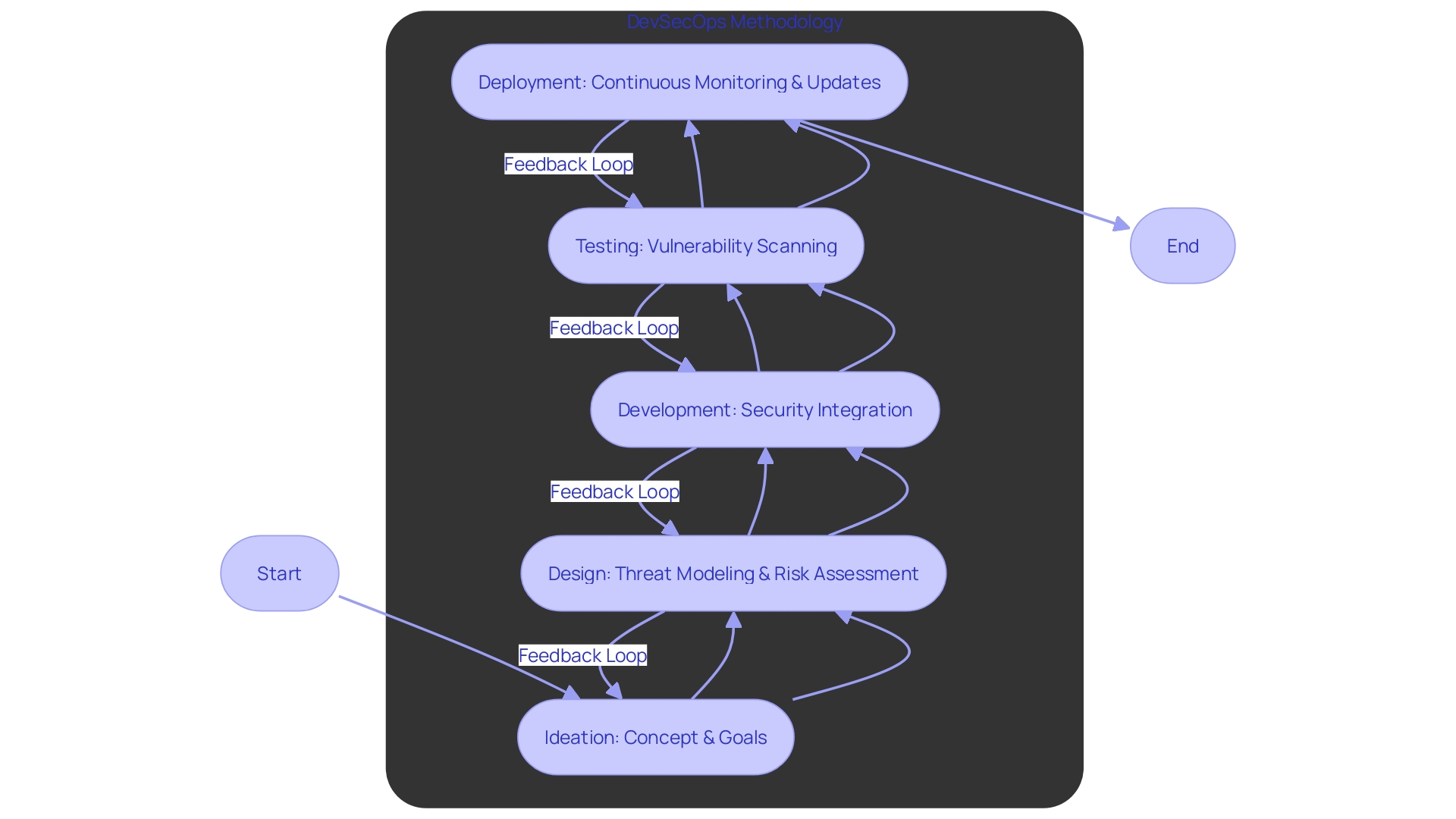
The concept of 'Secure by Design' is revolutionizing the way we approach software development. By embedding security measures at every stage of the software development lifecycle, from conception to deployment, we ensure that our applications are not just functional but robustly secure. A key aspect of this approach is threat modeling and risk assessment, which allows us to proactively identify and mitigate potential security threats.
A recent whitepaper, co-sealed by ten U.S. and international partners, has become a pivotal guide in this field. It emphasizes the importance of secure by design principles and provides actionable insights for both procuring organizations and software manufacturers. This collaborative effort, which now includes feedback from eight additional countries and international organizations, marks a significant industry shift towards prioritizing security.
The whitepaper acts as more than a mere checklist; it's a comprehensive guide that assists organizations in making informed, risk-based decisions tailored to their unique operational contexts. It underscores that while not all practices may be applicable to every organization, understanding the intent behind each principle is crucial.
In the realm of software supply chains, where everything from the developer's IDE to the operating system on which software runs can introduce vulnerabilities, the whitepaper's principles are especially relevant. Recent cybersecurity incidents have highlighted the dangers of exposed secrets, such as API keys and passwords, which can compromise the entire 'corporate kingdom.'
To address these challenges, DevSecOps—a methodology that integrates security practices throughout the software development lifecycle—has emerged as a leading solution. By 'shifting security left', or integrating security measures as early as possible, DevSecOps ensures that security is a foundational element of the development process. This not only facilitates early vulnerability detection but also helps organizations meet regulatory obligations more efficiently.
Moreover, DevSecOps requires a cultural shift towards shared responsibility and collaboration across development, security, and operations teams. The right tools, technologies, and the smart application of automation and AI are instrumental in securing applications at the pace of development.
The whitepaper has been met with a wave of constructive feedback, indicating a readiness within the industry to transition the responsibility for security. This feedback has highlighted the success of companies that have embraced secure by design principles, with evidence presented in the form of artifacts—a collection of which can tell a compelling story about a company's commitment to security.
Finally, Google's experience has shown that focusing on the developer ecosystem can lead to a significant reduction in common security defects. This involves not only preventing bugs through safe coding but also addressing systemic issues within the developer ecosystem that contribute to the introduction of defects. By adopting these secure by design practices, organizations can enhance their security posture, thereby delivering more secure and resilient applications.
Common Security Threats and Vulnerabilities
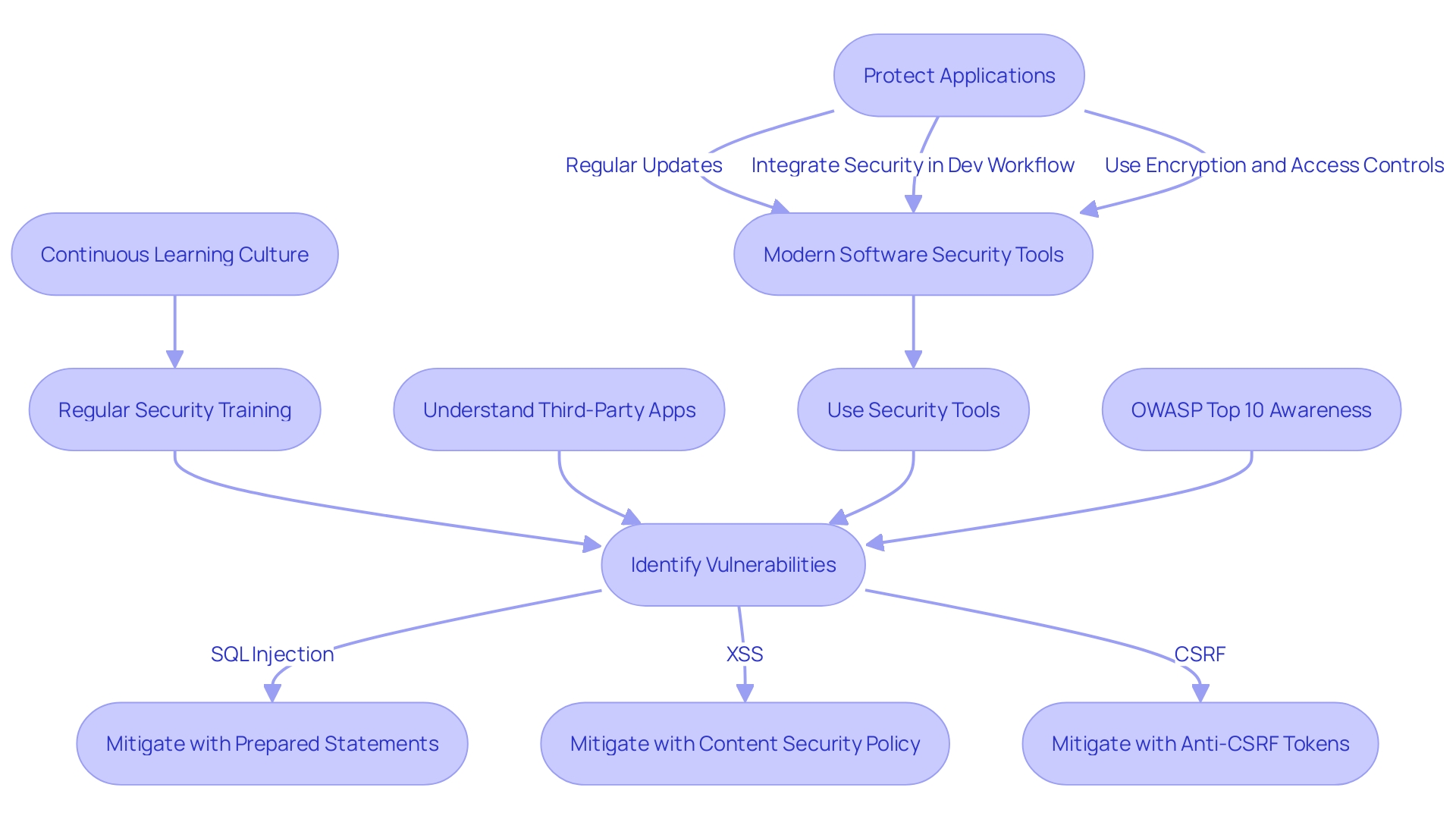
Developers must stay vigilant against security threats, such as SQL injection, XSS, and CSRF, which can jeopardize application security. For example, during a penetration test on Moodle, a widely-used LMS, it was found that users with the 'trainer' role could execute XSS attacks. This highlights the complex nature of modern web applications and the intricate vulnerabilities that can arise, even by design.
Injections and Broken Access Control (BAC) are among the top security vulnerabilities. Injections occur when unauthorized commands are executed, like in the courtroom analogy where 'Bob' manipulated the system to escape. BAC issues arise when users gain improper access to data, which can be as granular as a single field in a database.
Emphasizing regular security training can help teams keep up with evolving cybersecurity threats. Interactive workshops and scenario-based training are effective means to instill a proactive security culture. As per a security expert's analysis, identifying and generalizing remedies for classes of defects can lead to broader improvements in software security.
Moreover, it's crucial to understand the behavior of third-party apps and open-source code in your digital supply chain, establishing what 'normal' behavior looks like and being alerted to deviations, as demonstrated by the Log4J vulnerability incident.
Ultimately, the future of securing modern software lies in continuous vigilance, adaptation, and education. Tools and technologies that integrate with development workflows and manage sensitive data are essential to protect applications from breaches.
Best Practices for Secure Coding
Implementing secure coding practices is not just a technical necessity; it's an integral part of safeguarding the digital landscape of industries such as banking. Take M&T Bank for example, a long-standing institution that has embraced digital transformation to meet the demands of today's technology-driven world. In doing so, they have set a precedence in maintaining stringent security standards to protect sensitive data and transactions.
To avoid catastrophic breaches and financial repercussions, they've implemented Clean Code standards, ensuring their software not only meets quality benchmarks but remains within compliance.
Secure coding practices encompass numerous facets, from input validation and sanitization to authentication protocols. For instance, a robust authentication system, like the one implemented by Silverfort, can analyze access requests' risks and enforce Multi-Factor Authentication (MFA) even on legacy protocols, thereby strengthening security postures. This is critical, considering a report by Silverfort and Osterman Research indicating 83% of organizations have faced breaches due to compromised credentials.
Furthermore, when exploring Node.js applications, it's crucial to understand the specific threats such as typosquatting attacks and malicious packages. Documenting these attacks in plain language and supplementing them with code examples can significantly aid developers in recognizing and mitigating such threats.
The commitment to these practices is evident in the broader software industry's pledge to CISA's goals, aiming for enhanced security across enterprise software products. Software manufacturers are encouraged to document their progress towards these goals transparently, thus contributing to a culture of security that benefits all.
In conclusion, embracing a culture of secure development is not just about deploying tools but about fostering an environment where security is an integral part of the development process. As one security expert puts it, "The best application security tool is education." This sentiment is echoed in the industry-wide move towards prioritizing security, from planning and design to maintenance and documentation, as outlined in CISA's three-part series on cybersecurity threats.
Incorporating these secure coding practices is essential for the creation of robust and trustworthy software, ensuring that organizations like M&T Bank can continue to innovate while safeguarding their customer's data and maintaining their reputations in an ever-evolving digital economy.
Conducting Secure Code Reviews
Secure code review is a pivotal element in the software development life cycle, specifically for industries like banking, where the stakes are exceptionally high. Take M&T Bank for instance, a venerable institution with a 165-year legacy, which recognized the necessity of integrating Clean Code standards to maintain their software's performance and reliability. As they navigate the digital transformation, they are acutely aware that any software issue could result in severe security breaches and financial repercussions.
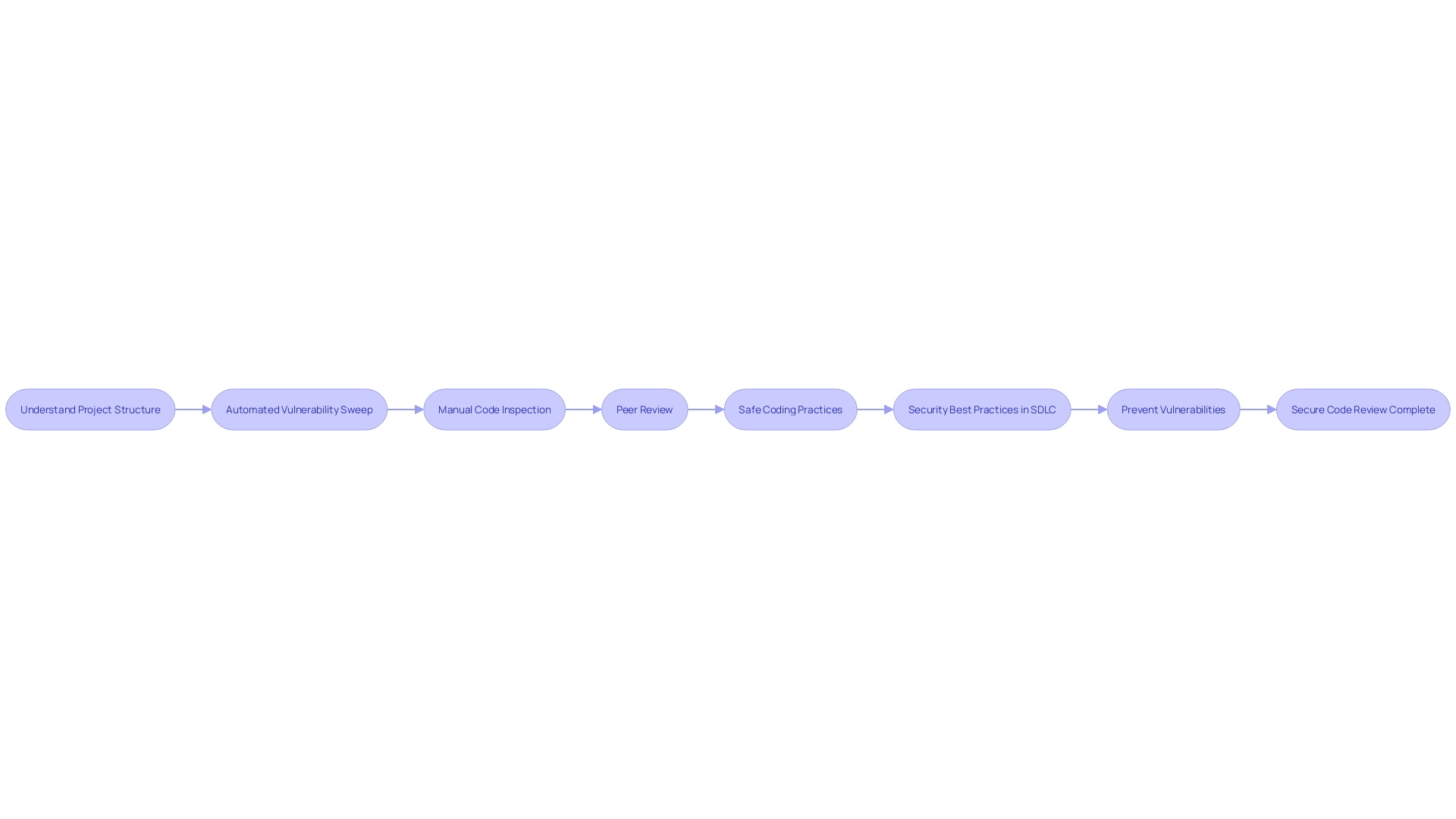
The process of secure code review involves meticulous analysis of the code to identify potential vulnerabilities. It starts with understanding the project's structure, whether the code is original or a modified fork, and the primary functions users will engage with. Automated tools are indispensable in this phase, providing an initial sweep for common vulnerabilities.
However, manual code inspections are equally crucial; they delve deeper into complex issues that automated tools might overlook.
Peer reviews play an important role as well, fostering collaboration and knowledge sharing, which is vital for maintaining high security standards. In the words of an industry expert, 'Preventing bugs through Safe Coding' is essential, as it is far more effective to prevent vulnerabilities than to fix them post-development.
Statistics have revealed that the reuse of vulnerable code, such as insecure third-party libraries, significantly contributes to security risks. Hence, the emphasis on thorough code reviews is not just about finding errors but also about adhering to security best practices throughout the software development life cycle (SDLC).
In conclusion, security should never be an afterthought in software development; it must be embedded from the very beginning. The importance of secure coding practices is underscored by the potential dire consequences of neglect, ranging from data breaches to operational disruptions. By committing to secure code reviews, organizations can fortify their applications against the ever-evolving cyber threats, safeguarding their customer trust and business integrity.
Addressing Challenges and Solutions
As developers weave the fabric of digital transformation within the banking industry, they face a myriad of challenges that can compromise the security of highly sensitive data and transactions. The case of M&T Bank serves as a quintessential example; despite its storied history and robust workforce, the bank had to contend with the daunting task of implementing organization-wide Clean Code standards to sustain its software's maintainability and performance.
Integrating security into the software development life cycle is not a mere compliance checkbox but a strategic investment. Security by design is a philosophy where security is not an afterthought but a fundamental, integral part of the development process. Periodic risk assessments are crucial in identifying and addressing vulnerabilities early on, preventing them from becoming deep-rooted in the codebase.
This practice not only enhances the product's quality but also saves time and resources.
In an all-digital customer experience landscape, the adoption of new technologies brings heightened security requirements. SpyAgent Android malware, for instance, demonstrates the innovative ways threat actors can exploit vulnerabilities, such as stealing recovery phrases from images on mobile devices. This highlights the importance of encrypting sensitive data even in areas often overlooked, such as image security.
Moreover, open-source components dominate modern software, with 96% of all software containing them. While these components accelerate development, they also introduce vulnerabilities that necessitate constant vigilance and refactoring by developers. Organizations and developers must ensure that the code is not only functional but also secure from the start, avoiding the costly process of addressing vulnerabilities after deployment.
Security training is paramount, as cybersecurity threats are in constant flux. Regular, up-to-date training equips development teams with the knowledge to combat new threats and reinforces a security-first culture. Interactive workshops, online courses, and scenario-based training can be employed to keep the knowledge fresh and relevant.
To this end, the security landscape demands a vigilant, educated approach to software development. The journey of M&T Bank showcases the necessity of establishing Clean Code standards, while the dynamic nature of cybersecurity underscores the importance of security by design. Developers must embrace regular security training as a critical component of their professional development to ensure the creation of secure, reliable software that stands the test of time and cyber threats.
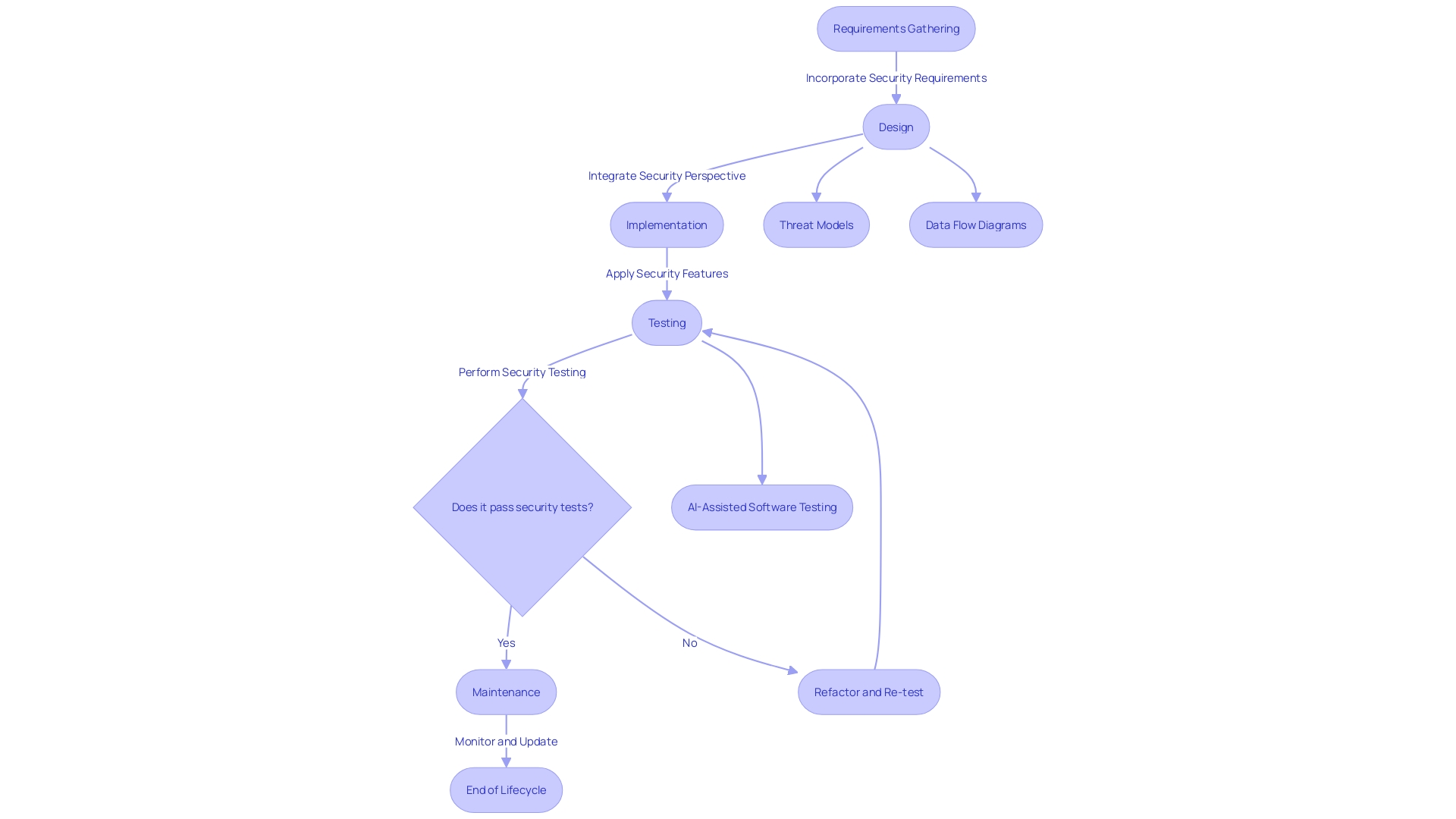
Implementing a Secure Software Development Lifecycle
To ensure the integrity of the software they produce, developers must embed security measures throughout the development lifecycle. Each phase—requirements gathering, design, implementation, testing, and maintenance—must be approached with a security-first mindset. For instance, banking giant M&T Bank, with its extensive history and workforce, faced the challenge of adapting to the digital landscape while upholding stringent security and regulatory standards.
They tackled this by setting organization-wide Clean Code standards to maintain their software's performance and security.
The secure SDLC is a dynamic process. Initially, it involves defining precise security and privacy requirements, considering the data type, existing threats, and compliance needs. As software evolves, so do these requirements, necessitating regular updates to threat models and data flow diagrams to accurately represent system interactions and potential vulnerabilities.
In practice, this approach is exemplified by the Security Development Lifecycle (SDL), which promotes continuous cybersecurity training for all involved in the development process, integrating AI-assisted software testing. Such proactive measures are part of the 'Shift Left' strategy, which advocates for introducing security early in the development process, thereby preventing costly and time-consuming issues later on.
Statistically, these practices are crucial. Research indicates a significant decrease in common defects within companies that employ secure coding practices, underscoring the importance of preventing bugs through safe coding and regular security training. To equip software engineers with the necessary tools for security, automation and training are key, fostering a culture where security is owned by the developers themselves.
This not only enhances the security posture but also aligns with the DevSecOps philosophy of incorporating security as a fundamental aspect of the software development process.
Establishing Secure Coding Standards and Training
Adopting secure coding standards and prioritizing developer education is essential for sustaining robust cybersecurity measures. These steps ensure that the code produced is not only functional but also resilient against threats, aligning with best practices that are widely recognized in the industry. As technology continues to permeate every facet of our lives, from digital banking to connected devices, the necessity of adopting secure coding practices has never been more pronounced.
For instance, M&T Bank, with its commendable history in banking, has undertaken a significant digital transformation, recognizing that their software must uphold stringent quality and security standards to maintain trust and efficiency. Their initiative to standardize Clean Code practices across their development teams exemplifies a proactive approach to minimizing risks and maintaining software integrity.
Moreover, Google's experience demonstrates that focusing on developer ecosystems yields tangible results in reducing common defects. Emphasizing safe coding prevents bugs that could lead to security vulnerabilities, especially in large, complex codebases where the margin for error is slim.
In light of these real-world examples, the cybersecurity landscape presents us with sobering statistics: only 4% of organizations feel fully confident in their defense against cyberattacks. With a global cybersecurity workforce of approximately 4.7 million professionals and a median annual pay for information security analysts at $102,600 in 2021, it's evident that the industry recognizes the value and necessity of skilled security personnel.
Consequently, the need for secure coding is underscored by the White House Office of the National Cyber Director, advocating for the adoption of memory-safe programming languages. Additionally, the National Cybersecurity Education Colloquium has highlighted the urgency of integrating security knowledge into computer science curricula as a foundational, not elective, skill.
In summary, secure coding is not merely a technical requirement but a strategic imperative. It stands at the confluence of development, operations, and security, and its importance is amplified as we navigate an increasingly digital and interconnected world. The development of secure software begins with clear, evolving security and privacy requirements, informed by threat models and best practices, ultimately shaping a resilient digital infrastructure.
Conclusion
Secure coding is crucial for developing resilient and trustworthy software applications. M&T Bank's adoption of Clean Code standards highlights the recognition of risks and costs associated with insecure software. Understanding the software's anatomy and vulnerabilities in the supply chain is essential.
The Security Development Lifecycle (SDL) approach, precise security requirements, and threat models are vital for secure development. Implementing secure defaults, least privilege, and fail-secure strategies create robust software even in the face of errors.
"Secure by Design" revolutionizes software development by embedding security at every stage. Thorough code reviews, including automated tools and manual inspections, identify vulnerabilities. Embracing a secure development culture ensures security is integral.
Developers face challenges in securing sensitive data and transactions. Regular security training, understanding specific threats, and managing open-source components are crucial. Embedding security throughout the development lifecycle maintains software integrity.
Adopting secure coding standards and prioritizing developer education is key. Focusing on developer ecosystems and safe coding reduces common defects. Skilled security personnel and integrating security knowledge into curricula are vital.
In summary, secure coding is a strategic imperative. M&T Bank's adoption of Clean Code and commitment to secure practices exemplify risk mitigation. Embracing secure coding, thorough reviews, and a security culture create trustworthy software.
Regular training and vulnerability management protect data. Adopting coding standards and education enhance cybersecurity.
Frequently Asked Questions
What is secure coding and why is it important?
Secure coding is the practice of writing software with a focus on protecting the integrity, confidentiality, and availability of the data and systems that the software interacts with. It's important because it helps prevent vulnerabilities and cyber-attacks, ensuring trustworthy and resilient software applications.
How does M&T Bank illustrate the importance of secure coding?
M&T Bank, a financial institution with a significant digital presence, has adopted Clean Code standards to address the risks and costs associated with security breaches. Their initiative highlights the importance of secure coding in maintaining high-quality and secure coding practices in the banking industry.
What are some key components of a software supply chain that can introduce vulnerabilities?
Key components include the developer's Integrated Development Environment (IDE), the operating system (OS) on which the software operates, and the originality or modifications of the code (forks). These can all be potential sources of vulnerabilities that may be exploited maliciously.
What is a software Bill of Materials (BOM) and why is it useful?
A software Bill of Materials (BOM) is a comprehensive list of all components that make up a piece of software. It offers transparency and helps track these components, which is particularly important for managing vulnerabilities in the software supply chain.
What is the Security Development Lifecycle (SDL) and its role in secure coding?
The Security Development Lifecycle (SDL) is an approach that incorporates security measures throughout the software development process. It requires that all personnel involved in software creation are knowledgeable in cybersecurity fundamentals and secure development practices, starting with defining security and privacy requirements for the product.
What are some examples of secure coding principles?
Secure coding principles include input validation, applying the principle of least privilege, ensuring systems fail securely, and establishing secure defaults. These practices help mitigate risks and protect customer data, which is especially critical in sensitive industries like banking.
What does it mean for a system to 'fail securely'?
Failing securely means that when a system encounters an error or failure, it does so in a way that does not compromise sensitive information. The system should maintain security and data integrity, even in the event of unexpected issues.
How does Secure by Design enhance software development?
Secure by Design integrates security measures at every stage of the software development lifecycle, from planning to deployment. It involves threat modeling, risk assessment, and embedding security into the design and architecture of the software, ensuring that applications are secure from the outset.
Why is regular security training for developers important?
Regular security training is important because cybersecurity threats constantly change and evolve. Training keeps development teams informed about the latest threats and reinforces a proactive security culture, which is crucial for maintaining secure coding practices.
What are common security threats and vulnerabilities in software development?
Common security threats include SQL injection, XSS (Cross-Site Scripting), CSRF (Cross-Site Request Forgery), and Broken Access Control. These vulnerabilities can jeopardize the security of applications and need to be addressed through vigilant coding practices and regular security reviews.
What is the purpose of secure code reviews?
The purpose of secure code reviews is to meticulously analyze code to identify potential vulnerabilities before they can be exploited. It involves automated tools and manual inspections to scrutinize the code for common and complex issues, and is an integral part of maintaining high security standards throughout the software development lifecycle.
How does implementing a Secure Software Development Lifecycle (SDLC) help developers?
Implementing a Secure SDLC ensures that security measures are embedded throughout the development process, from requirement gathering to maintenance. It promotes a security-first mindset, which helps prevent vulnerabilities and enhances the overall security of the software produced.
What strategic steps have M&T Bank taken for secure coding?
M&T Bank has undertaken standardizing Clean Code practices across their development teams as part of their digital transformation. This involves prioritizing security in their coding standards to minimize risks and maintain the integrity and performance of their software.




