Introduction
In today's digital landscape, secure coding practices are crucial for creating software that can withstand security threats and deliver on its promise of reliability and trustworthiness. This article explores the importance of secure coding practices and the benefits of using the Kodezi platform to achieve maximum efficiency and productivity. By adhering to secure coding practices, developers can lay down a solid foundation for software security and create an environment that supports the writing of safe and reliable code.
The article also highlights the significance of continuous education and training to stay ahead of the evolving cybersecurity landscape. Additionally, it discusses the concept of the Secure Software Development Lifecycle (SDLC) and the importance of managing and protecting secrets and open-source components. Overall, the article emphasizes the need for a strategic approach to secure coding to produce reliable and resilient software in today's digital age.
Importance of Secure Coding Practices
Adhering to secure coding practices is crucial for crafting programs that withstand security threats. Such practices are not only about mitigating risks; they're about ensuring the program delivers on its promise of reliability and trustworthiness. From the beginning, developers who incorporate these practices establish a strong basis for software protection.
M&T Bank's dedication to Clean Code standards throughout its extensive development team exemplifies the significance of coding with utmost safety in an industry where digital transformation is crucial. Their approach echoes the need for banking organizations to maintain code quality and compliance amidst the pressures of technological evolution and safety demands.
Google's experiences also highlight the significance of a developer-friendly ecosystem, which, when optimized, can substantially reduce common coding errors. This speaks to the broader theme of secure coding: it's not just about preventing bugs, but creating an environment that supports developers in writing safe and reliable code.
Supporting this environment requires continuous education. Regular training is crucial as it ensures developers stay ahead of the evolving landscape in cybersecurity. Interactive workshops, online courses, and scenario-based training can all contribute to a proactive security culture.
When talking about the principles of coding with high-level of protection, it's crucial to examine the idea of the Software Development Lifecycle (SDLC). Incorporating security-focused practices throughout the SDLC leads to products that can be trusted, where concerns are detected early, and all stakeholders maintain a focus on security.
A pressing concern for developers is managing and protecting secrets, like API keys and credentials. With most software containing a significant portion of open-source components, the risks of vulnerabilities from these sources cannot be overlooked. Developers must be vigilant in safeguarding these secrets to prevent devastating data breaches and business disruptions.
Analyzing defect patterns and their evolution over time is another aspect of coding strategy. This analysis helps identify which organizations are improving and which need to enhance their quality programs. Applying general remedies to these patterns can lead to a more protected coding landscape.
As the industry continues to wrestle with the challenge of coding with high levels of protection, it is evident that a combination of training, integration throughout the lifecycle, and diligent management of confidential information and elements is necessary to generate dependable and enduring applications. The path toward coding with safety measures is intricate, but with a strategic approach, it is attainable.
NIST Secure Software Development Framework (SSDF) Overview
The National Institute of Standards and Technology (NIST) has developed the Secure Software Development Framework (SSDF) to guide organizations through the complexities of creating secure applications. This framework underscores the importance of integrating safety from the initial planning phase throughout the entire software maintenance process. By highlighting a proactive approach on safety measures and promoting ongoing improvement, the SSDF aims to create a thorough and resilient growth process.
M&T Bank, an influential entity in the US banking industry, acknowledged the importance of incorporating such protection principles into its development culture. With the digital banking landscape evolving rapidly, the bank addressed the need for strong protection and compliance standards to safeguard sensitive data and transactions. M&T Bank's move towards establishing Clean Code standards across its organization reflects a commitment to maintaining program quality and adhering to strict regulatory demands.
The SSDF is a component of a wider initiative to address cyber threats presented to critical infrastructure, with guidance on principles such as requirements planning for safeguarding, architecture design for secure systems, and ongoing maintenance of protection. Recent updates to the framework have highlighted the significance of managing open source components and bills of materials (SBOM), aiming to enhance cybersecurity across organizations and their supply chains. These endeavors address a rise in cyber assaults, especially those exploiting supply chain vulnerabilities of programs, emphasizing the need for all-encompassing protective measures.
As the industry moves towards the principles of designing with security in mind, manufacturers of software are urged to take ownership of customer security outcomes, practice radical transparency, and showcase leadership. The updated guidance, co-authored by ten US and international partners and expanded with input from eight more countries and organizations, stands as a testament to the global commitment to software protection.
Integrating the principles of the SSDF into the lifecycle of creating digital solutions is vital in the current era, where safeguarding information is of utmost importance. With comprehensive instructions on requirement definition for safety, threat modeling, and best practices for protected evolution, organizations like M&T Bank can effectively reduce risks and ensure the integrity of their digital products.
Prepare the Organization for Secure Software Development
Recognizing the significance of a secure development environment is crucial in today's digital landscape. This is exemplified by M&T Bank, a long-standing institution that has faced the challenges of digital transformation head-on. They acknowledged the necessity for a strong culture of protection, which resulted in the implementation of Clean Code standards throughout the organization. This initiative supports maintainability and performance, crucial for protecting sensitive data and financial transactions.
To replicate such effective approaches, companies must begin by explicitly defining safety and privacy requirements, taking into account data types, known threats, and regulatory standards. This is where the Security Development Lifecycle (SDL) becomes instrumental. It ensures that all personnel involved in program creation, from employees to contractors, are well-versed in cybersecurity basics and secure development practices. Consistent training and the incorporation of AI in testing further strengthen the framework.
As highlighted in a three-part series on cyber threats, it's crucial to plan protection needs, design architecture with safety in mind, and maintain the integrity of both applications and infrastructure. With changing consumer habits fueling rapid technological adoption, the banking industry exemplifies the urgency of such measures. Neglecting to handle concerns regarding safety can result in substantial financial losses and damage to one's reputation.
Recent news has highlighted the complexities of the software supply chain, which includes everything from development environments to third-party dependencies. Cybersecurity incidents in 2023 have underscored the repercussions of exposed sensitive information, such as API keys and passwords. Consequently, organizations are giving more importance to safeguarding, as demonstrated by Microsoft's company-wide focus on protection as a fundamental concern.
Industry analysis has revealed an increasing emphasis on safeguard measures among organizations. While theoretical techniques for creating reliable programs are implemented in real-world scenarios, they are frequently not integrated into official procedures. This gap presents an opportunity for future research to refine the application of these methods in real-world scenarios. In general, establishing a culture that gives importance to protection is an essential measure in generating reliable programs, with education, policy formation, and cooperation playing crucial roles.
Define Security Requirements for Software Development
When talking about the establishment of coding standards that ensure safety, it's crucial to acknowledge that protection needs are essential to the development of strong software. For instance, M&T Bank, a commercial bank with a rich history, encountered the necessity to adjust its protective measures in view of the digital revolution engulfing the banking sector. This transformation has brought about not only new customer experiences but also the highest safety expectations and stringent regulatory demands to safeguard sensitive data and transactions.
The objectives for a software project should encompass important areas such as authentication, authorization, data protection, input validation, and secure communication. For instance, in designing a self-parking car application, risk assessments begin by identifying components that the app would interact with, raising questions about risk and responsibility. Similarly, with the Bureau of Industry and Security's initiative on AI, developers must meet reporting requirements that assure the cybersecurity resilience of AI technologies.
The approach to defining and implementing protection needs must be proactive and inclusive. Examining historical patterns reveals that the prioritization of system design frequently overlooks the aspect of safeguarding, resulting in possible system malfunctions, data breaches, and repercussions for customers. Efficient protection integrates the detection of patterns and their evolution over time, allowing companies to progress and establish quality improvement programs. A shift in focus from fixing individual defects to preventing classes of defects is crucial. This mindset is echoed by the experience at Google, where a focus on safe coding within the developer ecosystem has led to a dramatic reduction in common classes of defects.
In summary, establishing comprehensive protection guidelines is not only about complying with current demands but also about anticipating upcoming obstacles and guaranteeing that applications can withstand evolving dangers, thereby preserving customer confidence and the stability of crucial IT infrastructure.
Implement Roles and Responsibilities
The basis of safeguarding the creation process lies in defining and communicating specific roles and responsibilities. For instance, the process can be compared to the meticulous planning and execution that went into the Hoover Dam project, where every task and responsibility was clearly assigned to ensure the successful completion of one of the largest concrete structures of its era. Likewise, in the realm of software creation, it is vital to assign specialized individuals or teams to oversee particular safeguarding responsibilities. These tasks range from conducting code reviews and vulnerability assessments to orchestrating incident responses. Implementing this organized strategy guarantees that protective measures are consistently merged and executed effectively throughout the entire process of software creation.
Considering the observations from the National Cybersecurity Education Colloquium, it becomes clear that the incorporation of protection in the growth procedure should not be discretionary but a fundamental component. This aligns with the assertion from a workshop at the colloquium which discussed the importance of integrating safety into computer science curriculums as a fundamental discipline, rather than considering it as an optional subject.
As the information protection landscape reaches a critical point, emphasized by a discussion organized by Adrian Sanabria, Principal Researcher at the Defenders Initiative, the accessible budgets and resources present a favorable moment to strengthen the protective measures within workflow progress. This is especially pertinent given the increasing autonomy developers have historically enjoyed, which, while conducive to innovation, also introduces vulnerabilities to cyber threats.
In the spirit of the Security Development Lifecycle (SDL) approach, which is endorsed by numerous global corporations, it is imperative that everyone involved in application developmentbe it employees, contractors, or other relevant personnelâreceives comprehensive training in cybersecurity basics and secure development practices. This involves the utilization of artificial intelligence in testing applications, thereby promoting a culture of safety that spans throughout the organization.
Ultimately, the goal is to emulate Google's approach of focusing on developer ecosystems, which has proven to be both practical and effective. It results in a significant decrease in common types of defects across manifold applications developed by a vast number of developers. By highlighting the importance of secure coding to avoid glitches, the frequency of implementation-level defects can be significantly diminished, thereby improving the overall resilience and dependability of the program.
Implement Supporting Toolchains
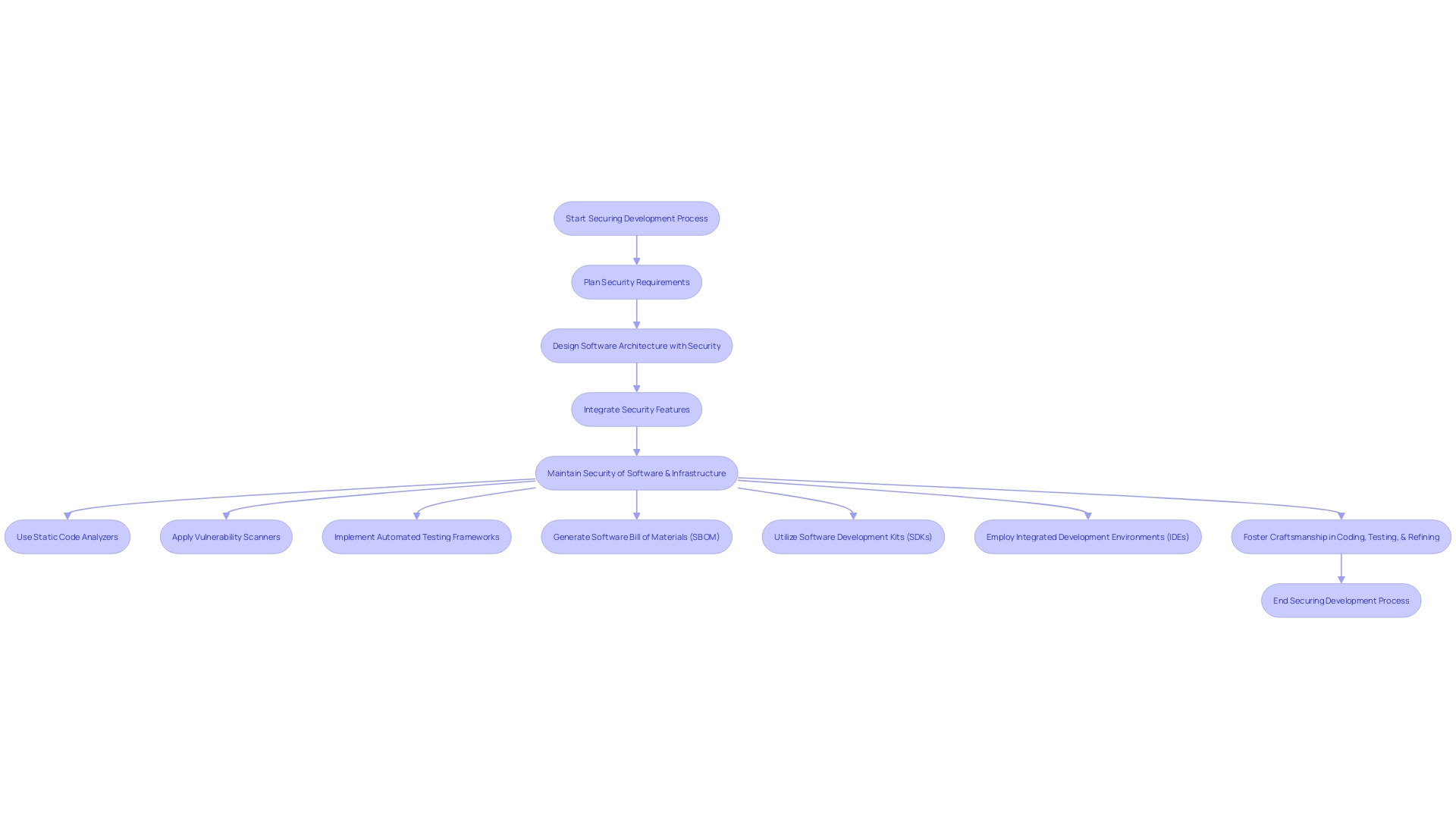
Incorporating toolchains such as static code analyzers, vulnerability scanners, and automated testing frameworks is essential for securing the development process. These tools enable the early detection of flaws, vulnerabilities, and weaknesses, allowing developers to promptly address issues, thus reducing the risk of breaches.
Toolchains enable the crafting of safe, reliable code, which is the cornerstone of robust security. Google's experiences show that a strategic focus on developer ecosystems can significantly decrease common defect rates, demonstrating the effectiveness of preventing bugs through safe coding practices.
The recent ESF report underscores the urgency of addressing software supply chain vulnerabilities by advocating for the consumption and management of software bills of materials (SBOM). This approach, highlighted by industry leaders like BlackBerry, aligns with best practices and principles to enhance cybersecurity across organizations and their supply chains.
Furthermore, implementing Software Development Kits (SDKs) and Integrated Development Environments (IDEs) can streamline the process, providing APIs, code libraries, and comprehensive documentation. These tools are instrumental in creating a centralized development workspace, thereby augmenting productivity and reducing the potential for coding errors.
As we develop applications, it's essential to embrace the spirit of craftsmanship, as mentioned by industry professionals. This involves a hands-on effort in coding, testing, and refining, with a dedication to excellence that reflects in the security and quality of the final product.
Ultimately, the combination of these tools and practices establishes a strong framework for developers, enabling them to build high-quality programs that withstand the evolving challenges of cybersecurity threats.
Produce Well-Secured Software
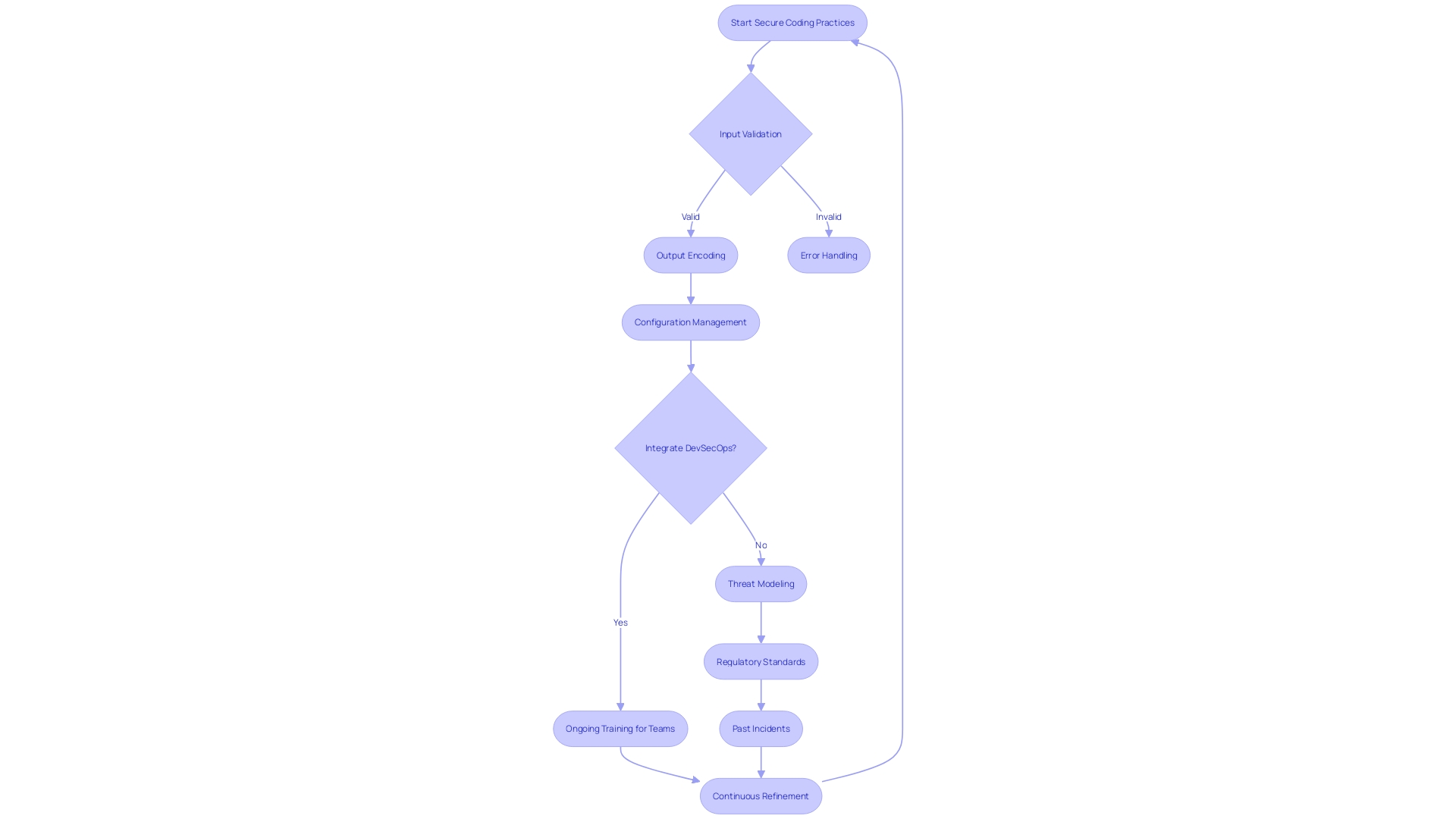
To construct software that stands strong against cyber threats, developers must embrace coding practices that prioritize safety and adhere to the highest standards of the industry. This encompasses a holistic approach, such as ensuring rigorous input validation to prevent SQL injection, implementing output encoding to thwart cross-site scripting, and establishing meticulous error handling and configuration management to avoid authentication bypass risks.
Case studies from leading financial institutions like M&T Bank, with its rich history of over 165 years, illustrate the critical need for such measures. As the banking sector evolves with digital advancements, ensuring the utmost protection and regulatory compliance becomes paramount to safeguard sensitive data and transactions. M&T Bank's embrace of Clean Code standards among its teams highlights the significance of secure coding for operational efficiency and program performance.
Including methodologies such as DevSecOps, which integrates protection into every stage of software advancement, is crucial. This method not just promotes a atmosphere of collective accountability but also utilizes automation and AI to uphold safety at the speed of progress.
Furthermore, ongoing training in safeguarding for development teams is a cornerstone for maintaining a robust posture. By staying updated with the latest threats and best practices, teams can cultivate a proactive protection culture, as suggested by cybersecurity experts.
Statistics from the 2024 Open Source Security and Risk Analysis (OSSRA) report emphasize the widespread use of open source, with an average of 526 open source components per application. This highlights the importance of automated testing tools like Software Composition Analysis (SCA) to handle the intricacies of contemporary development.
These practices are part of a broader, disciplined process anchored in the Security Development Lifecycle (SDL), which focuses on the evolution of protection and privacy requirements alongside the dynamic threat landscape. Secure coding is an iterative process, with continuous refinement based on threat modeling, regulatory standards, and lessons from past incidents.
Design Software to Meet Security Requirements and Mitigate Security Risks
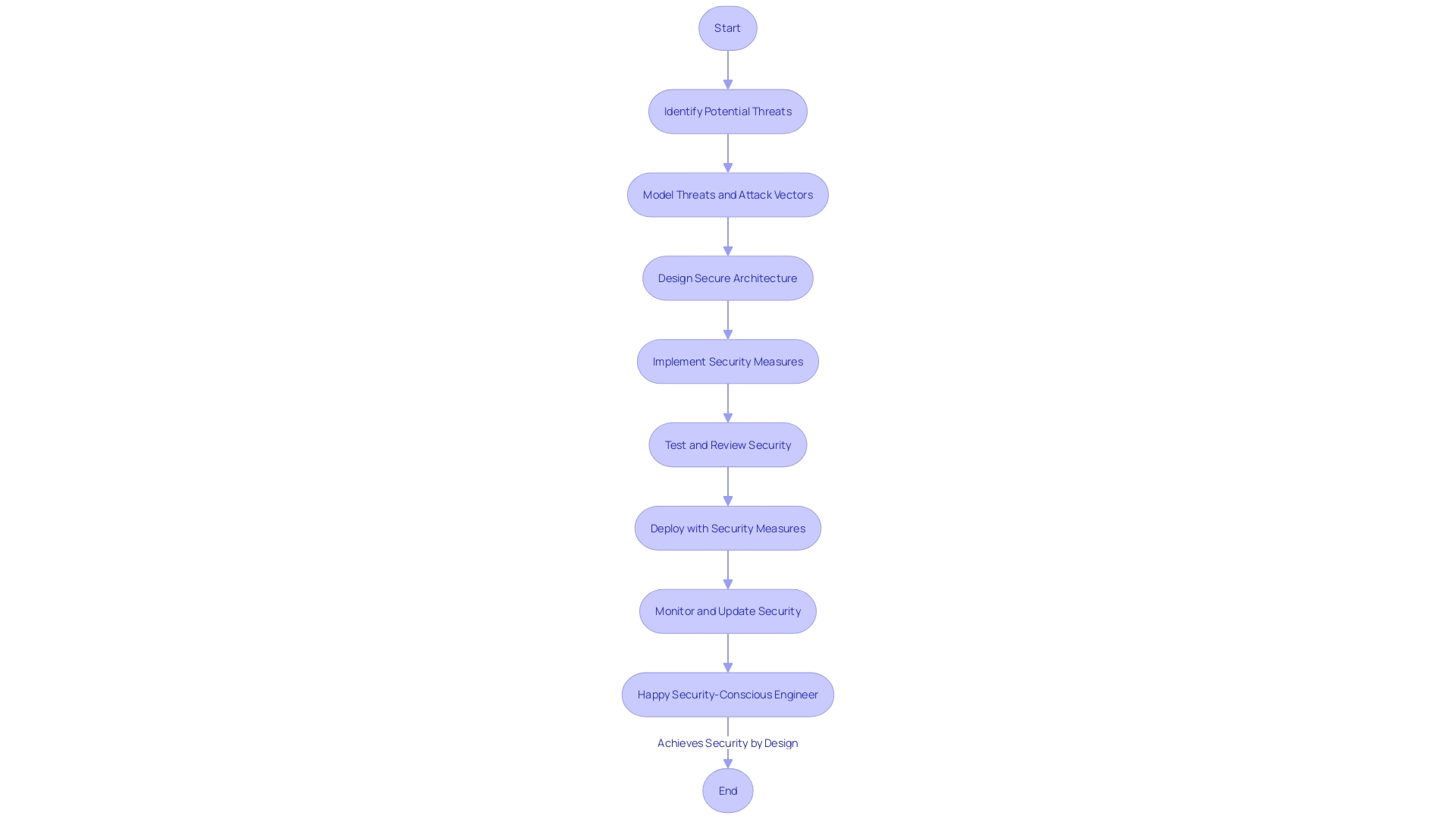
Incorporating safety concerns into the creation of programs is more than a recommended approach—it's an essential in today's digital environment. Threat modeling and the identification of potential attack vectors are foundational steps in creating architectures that can withstand and counteract cyber threats effectively. The focus on security from the beginning sets the stage for more resilient programs, able to protect against and reduce the impact of security breaches.
Recent events have emphasized the vulnerability of critical systems, especially those relying on open-source programs, which often originates from the combined efforts of unpaid programmers, some of whom work in obscurity. These systems form the backbone of various sectors including banking, aviation, and defense, making them prime targets for attackers. Such incidents demonstrate the essential requirement for a security-focused approach in development of programs.
The emphasis on ensuring the safety of software design is echoed by industry movements and expert recommendations, which underscore the risks of relegating security as an afterthought. Ignoring safety during the design phase can result in serious outcomes such as system failures, data breaches, and other compromises that ultimately affect customers and businesses. Additionally, implementing protective measures after the deployment can be expensive and may require significant alterations to the application's structure.
To address these challenges, there is an increasing agreement on the significance of a Software Bill of Materials (SBOM) and the examination of AI coding tools to manage the risks introduced by third-party code. High-profile cybersecurity incidents in 2023 have been linked to exposed sensitive information, such as API keys and passwords, emphasizing the need for stringent safeguarding of such 'secrets.'
Considering these advancements, companies in the technology industry are recommended to examine defect patterns and trends over a period of time, with the goal of proactively detecting and resolving vulnerabilities. By embracing Secure by Design principles and engaging in ongoing quality improvement programs, the industry can work towards a more secure future for applications.
Review the Software Design to Verify Compliance with Security Requirements
Maintaining adherence to strict safety measures is not a singular occurrence but a continuous undertaking crucial to protecting digital assets and customer confidence. Regular assessments of software design, including code and architectural reviews as well as audits, are indispensable tools in this endeavor. By adopting a proactive and continuous review strategy, organizations are better equipped to detect and rectify deviations from protocols before they escalate into vulnerabilities.
Recent industry trends highlight a change in the responsibility for safeguarding from users to manufacturers, reflecting safety evolutions in the automotive industry. Producers are encouraged to give importance to safety as a fundamental element of design, as mentioned in the revised document emphasizing principles for protected applications. This change in thinking is highlighted by initiatives like the Secure by Design Pledge from the Cybersecurity and Infrastructure Security Agency (CISA), which has gained commitments from over 150 technology companies to improve product safety.
The importance of this proactive stance is further validated by studies showing that maintenance and enhancement stages of software life cycles are fraught with complexity and resource consumption. In reaction, influential thinkers have promoted a 'secure-by-design' structure that incorporates safety into every level of product creation, thus decreasing the possibility of vulnerabilities after deployment.
Moreover, an emphasis on coding practices that prioritize safety can greatly reduce the occurrence of typical vulnerabilities. By highlighting the importance of coding safely and providing resources that simplify the process of creating strong code, organizations can assist developers in producing more resilient code, ultimately resulting in a decrease in defects related to security as time progresses.
In brief, a thorough approach to software safety that involves ongoing assessment, a transfer in accountability towards manufacturers, and the implementation of secure coding practices is vital for preserving the integrity and protection of digital products throughout their lifespan.
Respond to Vulnerabilities Throughout the Software Lifecycle
M&T Bank, with its significant legacy and workforce, faced the challenges of digital transformation head-on by setting stringent Clean Code standards for their software development. In an industry where digital customer experiences are paramount, the pressure to adopt new technologies comes with a heavy responsibility to ensure safety and compliance. Software issues are not just costly, but pose substantial business risks, including security breaches and reputational harm. Addressing vulnerabilities swiftly is not only a best practice but a necessity; it's about reducing risk through patching systems, as commonly recognized within the industry. Weaknesses manifest in different statesâfrom those not impacting the program to those actively exploitedâand comprehending each state is crucial for efficient incident response.
Root cause mapping, as updated by the CWE Program, enhances this approach by identifying the fundamental causes of vulnerabilities, enabling both industry and government bodies to target their investments in cybersecurity more effectively. It's a process that can lead companies to understand patterns and trends in defects, allowing them to make informed decisions about initiating quality improvement programs. This proactive approach to software safety is vital for preserving the integrity and protection of the program throughout its entire lifecycle, from design and creation to deployment and beyond.
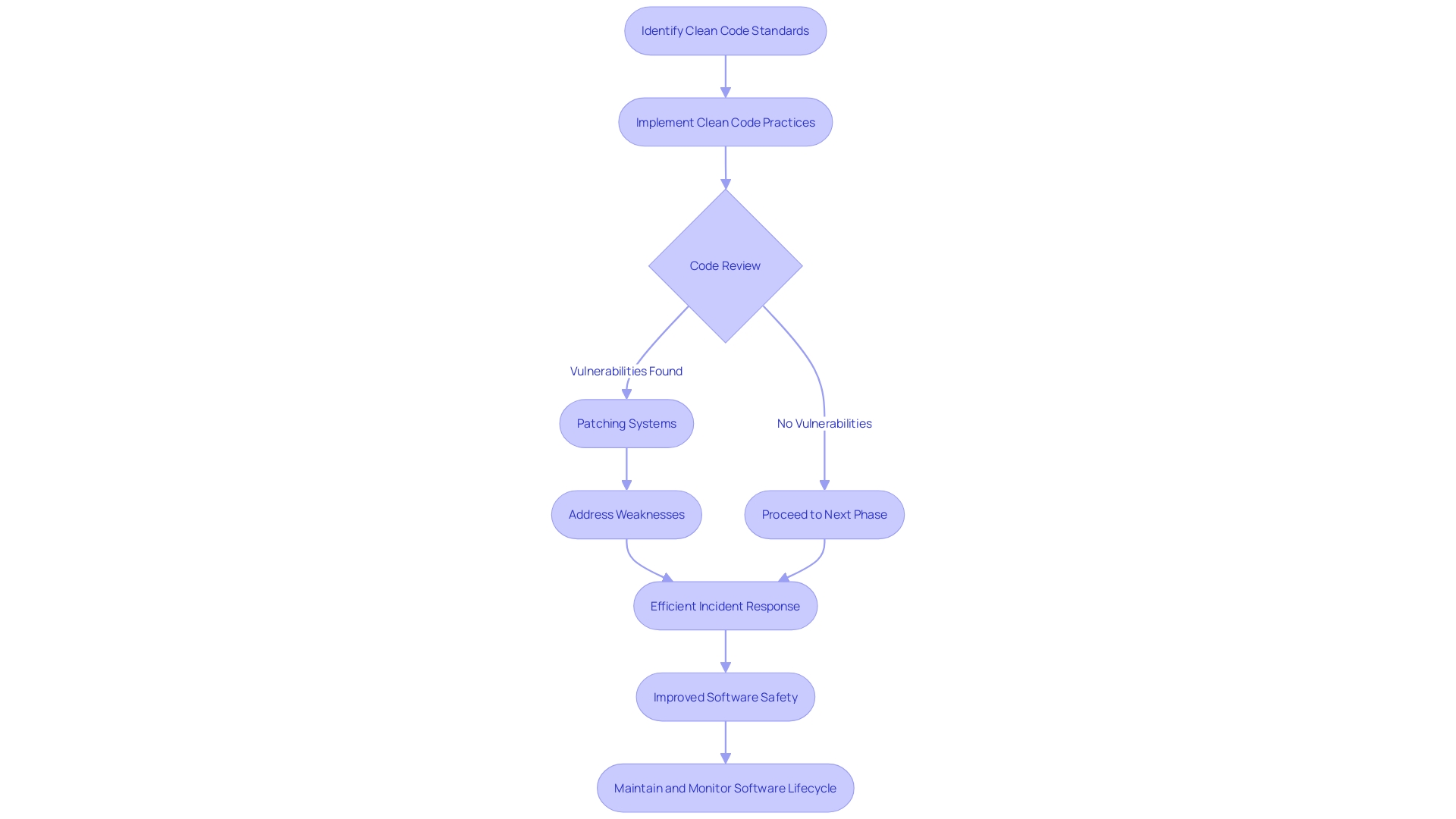
Key Practices and Tasks in the SSDF
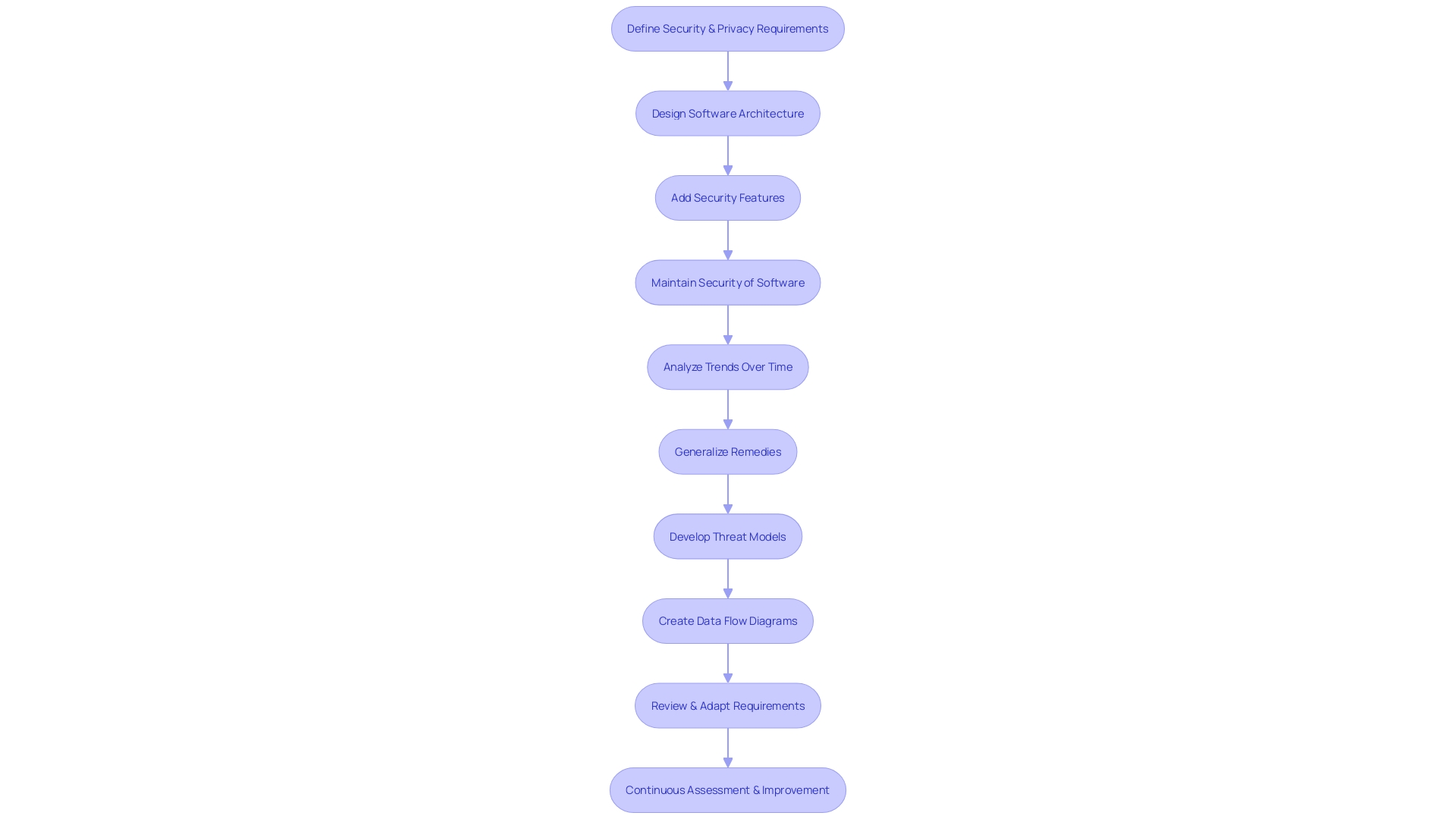
The Secure Software Development Framework (SSDF) by the National Institute of Standards and Technology is a crucial blueprint for integrating safety into the creation of software from the ground up. It highlights the significance of incorporating safety measures at the beginning of the development process, promoting a 'Shift Left' strategy where precautionary measures are not an afterthought but are integrated right from the initiation of the project. This implies planning for protection, designing with safety in mind, and continuously updating protective measures throughout the lifecycle of the program.
M&T Bank, a steadfast presence in the banking sector, encountered the challenge of digitization and the necessity for rigorous protection measures head-on by embracing Clean Code standards. This effort not just strengthened their protection against cyber dangers but also optimized their development procedures to guarantee efficient, dependable, and secure programs.
As technology becomes more and more essential to the functioning of organizations, the need for a proactive approach to safeguarding becomes evident. With the banking industry as a prime example, we see the costly risks of safety lapsesâcatastrophic breaches, financial loss, and reputational harm. Hence, the latest industry best practices now mandate a comprehensive approach to safeguarding programs, which includes overseeing open source components and maintaining software inventories (SBOM) to ensure transparency and maintain control over program integrity.
Organizations must not only embrace these practices but also participate in regular training to keep pace with the evolving landscape of cyber threats. By doing so, they can detect patterns of defects, analyze trends, and implement quality improvement programs where necessary. The joint endeavor among teams and the dedication to ongoing enhancement are crucial for upholding the integrity of both the application and the system it operates on.
In summary, the inclusion of protection into every stage of software creation is now a requirement but a requirement, as emphasized by the SSDF and demonstrated in the preemptive actions taken by prominent financial institutions like M&T Bank.
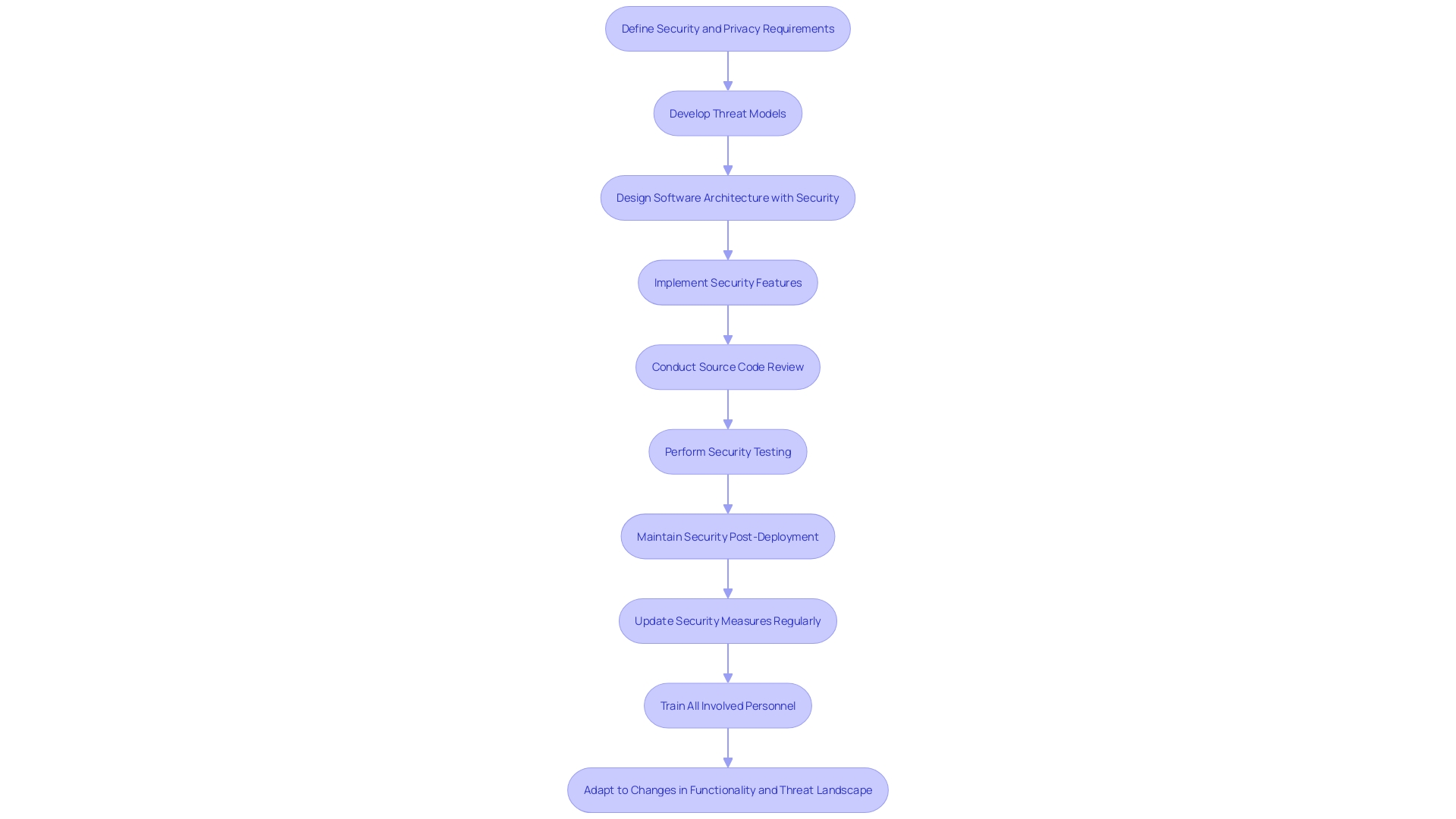
Benefits and Implementation of the SSDF
The incorporation of the National Institute of Standards and Technology's Secure Software Development Framework (SSDF) into an organization's practices is a crucial step in strengthening its applications against cyber threats. This framework provides a thorough approach to integrating protection into the development lifecycle, from the beginning to deployment. By implementing the SSDF, organizations can significantly curtail the likelihood of vulnerabilities, bolster their protection stance, and solidify the trust of their clientele.
Key practices within the SSDF include establishing requirements planning focused on ensuring the safety of the system, architecting software with a core focus on protection, incorporating features that enhance system safety, and ensuring continuous protection of software and infrastructure. These practices are critical, as evidenced by M& T Bank's initiative to uphold Clean Code standards amidst the banking sector's digital shift, where secure and compliant code is non-negotiable due to sensitive data and stringent regulatory demands.
Embracing these guidelines is not a one-time event but a continual process. Regular training is crucial to uphold a team's expertise in the most recent cybersecurity threats and mitigation tactics. Such training can take various forms, from interactive workshops to online courses and scenario-based exercises, laying the groundwork for a robust security-aware culture within the organization.
The updated SSDF also highlights the significance of software manufacturers taking ownership of customer safety outcomes, advocating for radical transparency and accountability, and leadership driving these principles from the top. This dedication to 'Secure by Design' is essential, as it cultivates trust among customers and partners, which is particularly vital in sectors where protection is of utmost importance, like banking and finance.
Backing this dedication, the recent report from the US Office of the National Cyber Director reinforces the importance of proactive measures, including the decrease of potential breach surfaces through design strategies that reduce memory safety vulnerabilities. This proactive stance on software security is further validated by the inclusion of eight additional countries and international organizations in the white paper on secure software development practices, highlighting a global consensus on the urgency of software security.

Conclusion
Secure coding practices are crucial for creating reliable and trustworthy software. The article emphasizes the importance of continuous education and training to stay ahead of evolving cybersecurity threats. It also highlights the significance of the Secure Software Development Lifecycle (SDLC) and managing secrets and open-source components.
Implementing secure coding practices and adhering to industry standards is crucial for building software that can withstand cyber threats. Leading financial institutions like M&T Bank have adopted Clean Code standards to prioritize security and compliance.
The article emphasizes integrating security into every phase of software development, from design to review. Implementing supporting toolchains, such as static code analyzers and vulnerability scanners, is essential for early identification and rectification of security flaws.
The article concludes by highlighting the benefits and implementation of the National Institute of Standards and Technology's Secure Software Development Framework (SSDF). Implementing the SSDF enables organizations to enhance their security stance and build trust with clients.
In summary, secure coding practices and the use of Kodezi are essential for creating reliable and resilient software. By following a strategic approach to secure coding, developers can mitigate cybersecurity risks and build software that meets the highest standards of security and trust.
Boost your software's security and trust with Kodezi's secure coding practices. Try Kodezi today!
Frequently Asked Questions
What are secure coding practices?
Secure coding practices involve methodologies and techniques that developers use to write code that is protected against vulnerabilities and security threats. This ensures the software is reliable and trustworthy.
Why is secure coding important for organizations like M&T Bank?
For organizations such as M&T Bank, secure coding is critical to maintaining code quality and compliance, especially in industries like banking where digital transformation and protection of sensitive data are paramount.
How does Google's developer-friendly ecosystem contribute to secure coding?
Google's developer-friendly ecosystem helps reduce common coding errors by creating an environment that supports developers in writing safe and reliable code, thus contributing to the broader theme of secure coding.
Why is continuous education important in secure coding?
Continuous education is vital as it ensures that developers stay informed about the evolving landscape of cybersecurity, enabling them to use the latest best practices and protect against new threats.
What is the Software Development Lifecycle (SDLC) and its role in secure coding?
The SDLC is a process that incorporates security-focused practices throughout the stages of software development, resulting in products that can be trusted and have security concerns addressed early.
What is the importance of managing and protecting secrets like API keys in software development?
Protecting secrets such as API keys and credentials is crucial to prevent data breaches and business disruptions, especially since most software contains open-source components that may have vulnerabilities.
How do defect pattern analyses contribute to secure coding?
Analyzing defect patterns over time helps organizations identify areas for improvement in their quality programs and apply general remedies to create a more protected coding landscape.
What is the NIST Secure Software Development Framework (SSDF)?
The SSDF, developed by the National Institute of Standards and Technology, guides organizations in creating secure applications by integrating safety from the initial planning phase throughout the entire software maintenance process.
How does the SSDF address software supply chain vulnerabilities?
The SSDF provides guidance on managing open source components and software bills of materials (SBOM) to enhance cybersecurity across organizations and their supply chains, addressing the rise in cyberattacks.
What is the Security Development Lifecycle (SDL)?
The SDL is a process that ensures all personnel involved in software creation are educated in cybersecurity basics and secure development practices, thus fostering a strong culture of protection.
What recent cybersecurity incidents have highlighted the need for secure coding practices?
Incidents in 2023 have showcased the consequences of exposed sensitive information, stressing the importance of secure coding practices to safeguard against such vulnerabilities.
Why is defining security requirements for software development essential?
Defining security requirements is a proactive step in ensuring that software is designed to meet the highest safety expectations and regulatory demands, protecting sensitive data and transactions.
What roles and responsibilities must be defined in secure software development?
It's important to assign specialized roles for conducting code reviews, vulnerability assessments, and incident responses to ensure that protective measures are effectively integrated into the software development process.
How do supporting toolchains aid in secure coding?
Tools like static code analyzers, vulnerability scanners, and automated testing frameworks help in early detection of issues and enable developers to write safer, more reliable code.
What is the purpose of the SSDF and how does it benefit organizations?
The SSDF aims to create a thorough and resilient development process that minimizes vulnerabilities and enhances security. Organizations that implement the SSDF can bolster their defense against cyber threats and strengthen customer trust.




