Introduction
Thorough secure code review is essential for safeguarding software integrity and mitigating potential vulnerabilities. This proactive approach not only fortifies security but also aligns with emerging global standards and regulations. Governments and industry leaders are recognizing the critical role of secure coding practices in light of recent reports emphasizing the need for memory-safe programming languages.
However, while many organizations acknowledge the significance of secure coding, the integration of these practices into standardized workflows remains inconsistent. With software supply chains becoming increasingly complex, the risk of introducing vulnerabilities at any stage is heightened. Recent cybersecurity incidents highlight the importance of secure coding and vigilant code reviews in protecting sensitive information.
By analyzing defect trends over time, organizations can gauge progress and identify areas needing improvement. Integrating secure code review into the software development lifecycle (SDLC) brings numerous benefits, including improving code quality, mitigating security risks, educating developers, ensuring compliance, and providing economic advantages. Different types of code reviews, such as static, dynamic, and manual, offer a robust defense against security threats.
The review process must adapt to evolving software development methods, incorporating AI to enhance performance and efficiency. A methodology for conducting secure code reviews involves defining goals, thorough preparation, code inspection, testing security measures, identifying and prioritizing issues, and remediation and verification. Ultimately, secure code review is indispensable for creating efficient, reliable, and secure software in the face of evolving cyber threats.
Why Secure Code Review is Essential
Thorough secure code review is a crucial step in safeguarding the integrity of software. It entails meticulously examining the codebase to unearth and mitigate potential vulnerabilities, effectively barricading it against cyber threats. This proactive approach not only fortifies security but also aligns with emerging global standards and regulations aimed at bolstering software security. In light of a recent White House report emphasizing the need for memory-safe programming languages, it's evident that governments and industry leaders are recognizing the critical role of secure coding practices.
A methodical approach to secure code review begins with a comprehensive understanding of the project's structure and intentions, such as discerning whether the code is original or a modified fork. By employing strategies like breadth-first security research, which targets common vulnerabilities, analysts can rapidly identify and address easily detectable flaws.
Insights from industry experts reveal that while many organizations acknowledge the significance of secure coding, the integration of these practices into formal, standardized workflows remains inconsistent. A study involving 20 companies highlighted an uptick in security prioritization, yet revealed a gap in the full adoption of recommended secure software development techniques.
As software supply chains become increasingly complex, the risk of introducing vulnerabilities at any stage—from development to deployment—is heightened. Recent cybersecurity incidents have underscored the dangers of exposed sensitive information, such as API keys and passwords, emphasizing the importance of secure coding and vigilant code reviews.
It's not just about preventing immediate threats; it's also about understanding and adapting to the evolving landscape of software security. By analyzing defect trends over time, organizations can gauge progress and identify areas needing quality improvement programs. This ongoing vigilance is essential for maintaining robust security in a world that increasingly relies on software for daily operations and critical infrastructures.
Benefits of Integrating Secure Code Review into the SDLC
Embedding secure code review within the SDLC is not simply a best practice; it's a critical defense mechanism against the proliferation of vulnerabilities that can compromise application security. When developers consistently evaluate the code from a security standpoint, they foster a heightened level of security awareness and knowledge. This not only improves code quality but also reduces the likelihood of introducing security flaws that could lead to breaches, thereby strengthening the security posture of your applications.
-
Improving Code Quality: A secure code review process encourages developers to write cleaner, more maintainable code, leading to more reliable applications.
-
Mitigating Security Risks: By catching vulnerabilities early in the development process, the risk associated with security breaches and data exploitation is significantly reduced.
-
Educating Developers: Through the secure code review process, developers become more aware of security best practices, leading to a more informed approach to coding.
-
Ensuring Compliance: Secure code review helps ensure that applications adhere to industry standards and regulations, which is particularly crucial for sectors like banking where M&T Bank, for instance, has set organization-wide Clean Code standards to support software maintainability and performance.
-
Economic Advantages: In an era where the cost of introducing problematic software can be exorbitant, secure code review stands as a cost-effective solution. It minimizes maintenance time and associated costs, which is essential for industries undergoing digital transformation, such as banking, where the adherence to stringent regulatory requirements is non-negotiable.
M&T Bank's initiative to establish Clean Code standards exemplifies the importance of such practices. The drive towards a fully digital customer experience necessitates rapid technology adoption, heightening the need for secure coding to shield highly sensitive data.
Furthermore, the growing emphasis on software quality and security by governments across the globe, as highlighted by recent reports from the White House Office of the National Cyber Director, underscores the urgency of integrating security practices into the SDLC.
Incorporating AI into the SDLC also brings its own challenges and opportunities, necessitating robust policies to manage security and data privacy effectively. Regular security training, as suggested by industry experts, becomes indispensable to ensure that the development team remains vigilant and updated on the latest threats and mitigation strategies.
In conclusion, secure code review is an indispensable element of the SDLC, contributing to the creation of software that is not only efficient and reliable but also secure in the face of evolving cyber threats.
Types of Code Reviews
Code reviews are a critical component in ensuring your software's security and reliability. To stay ahead of potential vulnerabilities, it's essential to use various review methods:
- Static Code Review: Here, tools scrutinize the source code without running it, catching security loopholes and coding mistakes early on.
- Dynamic Code Review: Contrary to static reviews, this method involves executing code to uncover issues that static analysis might miss.
- Manual Code Review: A human reviewer combs through the code, bringing a nuanced perspective that might reveal complex vulnerabilities automated tools could overlook.
Combining these approaches offers a robust defense against a wide array of security threats. As software development evolves, with tools like GitHub Copilot and ChatGPT reshaping how we write code, the review process must also adapt. Traditional methods, while still relevant, are being augmented by AI to enhance performance and efficiency.
Remember that every member of a development team has a role in the review process. Diverse opinions and expectations lead to more thorough reviews, although sensitivity to critique varies among individuals. It's an art as much as a science, and when leveraged fully, reviews can dramatically improve software quality.
Notably, Google's experience emphasizes the effectiveness of focusing on developer ecosystems, incorporating Safe Coding to significantly reduce common defects. Security as Code (Sac) further integrates automated security measures into the development workflow, advocating for early and continuous security considerations.
With these advanced practices, we are at a pivotal moment where new techniques could revolutionize code reviews, as seen in automated program repair. Such advancements may unsettle established researchers but offer exciting opportunities for new talent. Ultimately, the goal is not to eliminate all risks but to understand, manage, and mitigate them strategically, ensuring a resilient codebase for the digital age.
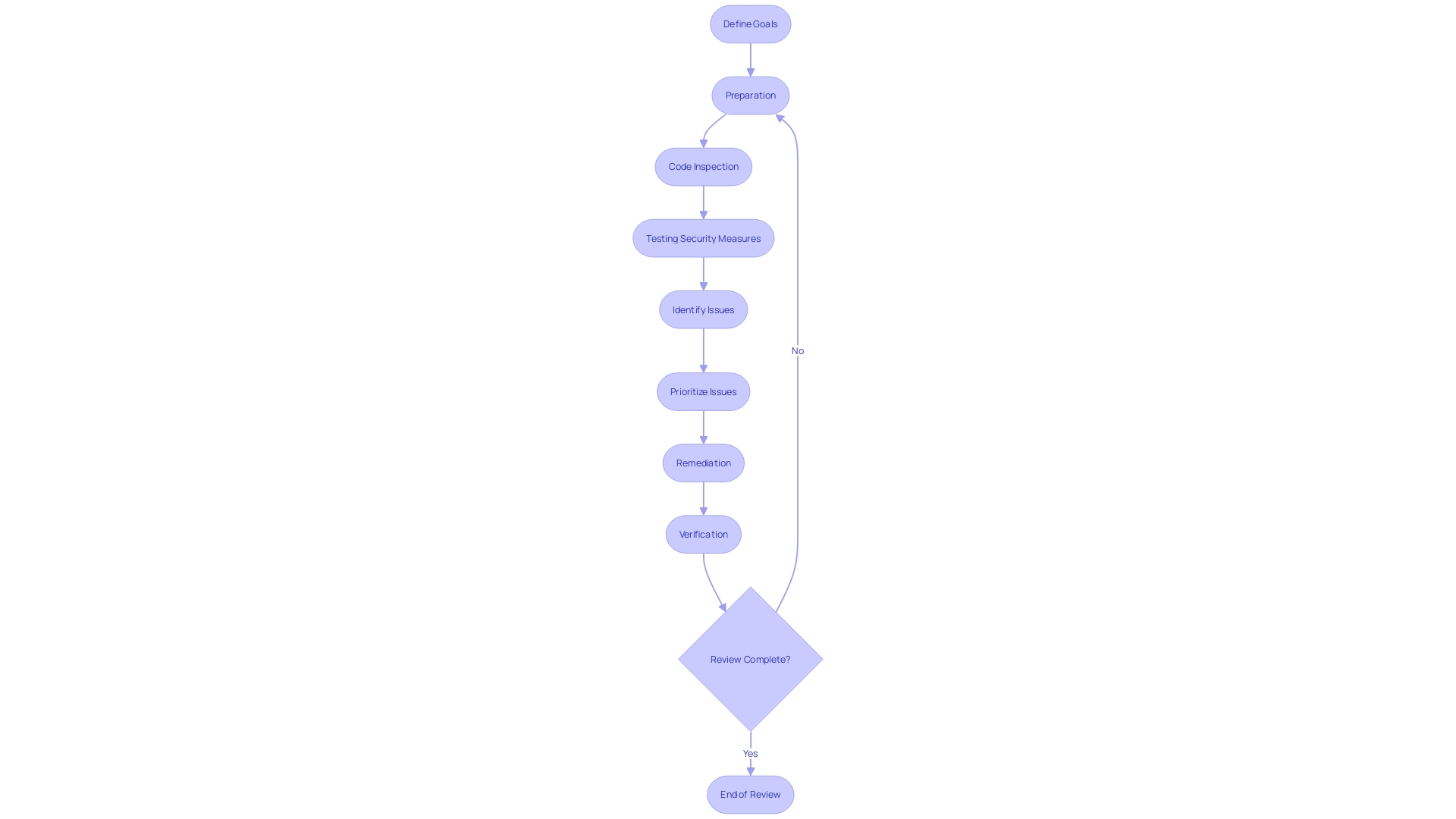
Methodology for Conducting Secure Code Reviews
In the quest for secure coding, effective code review is not just a step; it's a journey with distinct phases. Let's demystify this journey:
-
Define the Goals: Start by pinpointing your objectives. What are the security targets and compliance standards you must hit? M&T Bank's initiative to enforce Clean Code standards is an exemplary case of setting clear goals for software maintainability and security.
-
Prepare Thoroughly: Like any successful mission, preparation is key. Acquire essential documents like design specs and threat models. Grasp the app's architecture - consider the case of analyzing an options-based market; understanding the project's structure is critical.
-
Inspect the Code: Dive into the codebase, keeping an eye out for potential security flaws. Think input validation, authentication errors, or insecure data storage. Tools for static and dynamic analysis are your allies here, as they bolster your vulnerability detection efforts.
-
Test Security Measures: Validate your security controls. Engage in penetration testing, fuzz testing, and more to ensure your defenses hold. Clinton's warning about AI outpacing safeguards serves as a reminder of the imperative for rigorous testing.
-
Identify and Prioritize Issues: Document security issues and prioritize them by their threat level. Offer solid remediation recommendations. Remember, 96% of software has open-source components; vulnerabilities often lurk within these shared pieces.
-
Remediate and Verify: Work in tandem with developers to fix issues and verify corrections. A final review ensures all concerns have been resolved. Following Google's model, focusing on developer ecosystems can drastically reduce defects.
This methodology isn't just about finding problems; it's about fostering an ecosystem where security is integral to the development lifecycle, as suggested by the insights from Google's security engineering team. Incorporate NISTIR 8397's guidelines for a robust approach to developer verification of software. And don't overlook the importance of policies such as Infrastructure as Code (IAC) Scanning, ensuring a secure foundation for your applications.
Conclusion
Thorough secure code review is essential for safeguarding software integrity and mitigating vulnerabilities. Integrating it into the SDLC improves code quality, mitigates security risks, educates developers, ensures compliance, and provides economic advantages.
Different types of code reviews, like static, dynamic, and manual, offer a robust defense against security threats. The review process must adapt to evolving software development methods, incorporating AI for enhanced performance and efficiency.
Embedding secure code review within the SDLC strengthens application security. It aligns with global standards and regulations, emphasizing the urgency of integrating security practices. Governments worldwide emphasize software quality and security.
To stay ahead of vulnerabilities, use various code review methods and leverage diverse opinions. Secure code review is indispensable for creating efficient, reliable, and secure software in the face of evolving cyber threats. It protects sensitive information and strengthens the software's security posture.
In conclusion, secure code review is crucial for software integrity. It improves code quality, mitigates risks, educates developers, ensures compliance, and provides economic advantages. By integrating it into the SDLC and following a comprehensive methodology, organizations can enhance security and protect sensitive information.
Frequently Asked Questions
What is a secure code review?
A secure code review is a detailed examination of the codebase to identify and fix potential vulnerabilities, thereby enhancing the software's security against cyber threats.
Why is secure code review considered essential?
Secure code review is essential because it proactively identifies security vulnerabilities, ensures compliance with global standards and regulations, and aligns with the increasing emphasis on software security by governments and industry leaders.
What are some benefits of integrating secure code review into the Software Development Life Cycle (SDLC)?
Benefits include improved code quality, reduced risk of security breaches, heightened security awareness among developers, compliance with industry standards, and cost-effectiveness by minimizing maintenance time and costs.
How does secure code review contribute to developer education?
It educates developers on security best practices, making them more informed and vigilant about coding securely, which is essential for preventing vulnerabilities.
Can you explain the types of code reviews?
There are several types of code reviews: Static Code Review analyzes source code without executing it to catch early security flaws and coding errors. Dynamic Code Review executes code to identify issues that static reviews might not detect. Manual Code Review involves human reviewers who can identify complex vulnerabilities that automated tools might miss.
What role does AI play in code reviews?
AI is reshaping code review processes by enhancing performance and efficiency, complementing traditional methods with automated program repair, and addressing new challenges and opportunities in managing security.
How should one conduct a secure code review?
Conducting a secure code review involves several steps: Define goals, such as security targets and compliance standards. Prepare by gathering necessary documents and understanding the application's architecture. Inspect the code for potential security issues. Test security measures with penetration testing, fuzz testing, etc. Identify and prioritize documented security issues. Remediate and verify fixes, ensuring all concerns have been addressed.
Why is understanding the project's structure and intentions important in a code review?
Understanding the project's structure and intentions, such as whether the code is original or a modified fork, is important for a methodical approach to security, targeting common vulnerabilities effectively.
What are the economic advantages of secure code review?
The economic advantages include reducing the cost of problematic software by minimizing maintenance time and costs, especially in industries like banking, where compliance with regulatory requirements is crucial.
How does secure code review improve compliance with industry standards and regulations?
Secure code review ensures that applications adhere to industry standards and regulations, which is critical for sectors with stringent requirements, like banking.
What is the impact of secure code review on software quality and security?
Secure code review leads to more reliable applications and reduces the likelihood of security flaws, thereby strengthening the overall security posture against evolving cyber threats.
Can secure code review eliminate all risks?
No, secure code review cannot eliminate all risks, but it aims to understand, manage, and mitigate them strategically, ensuring a resilient codebase suitable for the digital age.




