Introduction
In the digital era, secure coding practices play a crucial role in safeguarding software applications from vulnerabilities and security breaches. Industries like banking are undergoing a massive digital transformation, highlighting the need for robust security measures. M&T Bank, for example, has implemented organization-wide Clean Code standards to ensure the integrity of its software amidst this shift.
Incorporating security from the outset, known as 'Security by Design', is now a fundamental aspect of any development project. DevSecOps, which integrates development, security, and operations, is a modern approach that prioritizes proactive security measures throughout the software development lifecycle. A Secure Software Development Lifecycle (SDLC) ensures that security considerations remain central at all stages of development.
Automation and AI solutions, such as software composition analysis, are indispensable for managing the complexities of modern software supply chains. Cultivating a clean code culture is essential for facilitating smoother reviews and collaborations, especially in remote work settings. With the majority of code being open source, the emphasis on automated security testing is underscored.
Secure coding is not just a technical requirement but a business imperative that demands a comprehensive, culture-driven approach. By embracing risk management, collaborative practices, and advanced tooling, organizations can navigate the intricate landscape of software security and achieve maximum efficiency and productivity.
Importance of Secure Coding Practices
In the digital era, secure coding practices are more than just a set of protocols; they are a critical line of defense in safeguarding software applications from vulnerabilities and potential security breaches. With industries like banking undergoing a massive digital transformation, the stakes have never been higher. Take M&T Bank, for instance, with its pioneering move to institute organization-wide Clean Code standards to maintain the robustness of its software amidst the digital shift.
This reflects the industry's acknowledgment that software is the backbone of modern business operations, and its security is paramount.
Security by Design: Incorporating security from the outset, known as 'Security by Design', is not optional but a fundamental aspect of any development project. Regular risk assessments embedded within the development process can preemptively identify and address vulnerabilities, safeguarding both the product's integrity and the company's resources.
DevSecOps: DevSecOps, the integration of development, security, and operations, epitomizes the modern approach to secure coding. This method champions proactive security measures throughout the software development lifecycle, reinforcing the principle that security is not an afterthought but a cornerstone of software creation.
Secure Software Development Lifecycle (SDLC): A Secure SDLC ensures that security considerations remain central throughout all stages of development. This approach not only enhances safety but fosters a collective security awareness among all stakeholders and aids in the early detection of issues.
Automation and AI in Secure Coding: As the 2024 OSSRA report indicates, with an average of 526 open source components per application, manual security testing is no longer viable. Automated solutions, like software composition analysis (SCA), are indispensable for managing the complexities of modern software supply chains.
Clean Code Culture: Frontend developers, like many working with JavaScript, understand the indispensability of clean code. It's not just about writing code that works but about crafting code that others can comprehend and build upon, facilitating smoother reviews and collaborations, especially when working remotely.
Statistical Insights: With the revelation that 96% of audited codebases contain open source components and the majority of the code being open source, the emphasis on automated security testing is underscored. According to Google's experience, focusing on safe coding practices within developer ecosystems can lead to a significant decrease in common defects.
Secure coding is not just a technical requirement but a business imperative that demands a comprehensive, culture-driven approach encompassing risk management, collaborative practices, and advanced tooling to navigate the intricate landscape of software security.
Overview of the OWASP Secure Coding Practices Quick Reference Guide
The OWASP Secure Coding Practices Quick Reference Guide is an essential toolkit for developers endeavoring to fortify their code against cyber threats. It delineates a comprehensive set of secure coding standards, helping developers preempt security vulnerabilities. Amidst a digital era where organizations like M&T Bank spearhead the adoption of digital banking, safeguarding sensitive customer data against breaches is paramount.
The guide's structure aligns with the necessity to infuse security at each phase of software development, resonating with the DevSecOps philosophy of integrating security from the get-go.
It addresses principal concerns such as security requirement planning, architecting software with security in mind, and fortifying the software against threats. The guide underscores the importance of security in the software lifecycle, echoing the sentiments highlighted by industry experts on the criticality of securing applications—it's not just about securing code, but also the environments and processes that support it.
The guide is also a dynamic resource, reflecting the evolving landscape of cybersecurity threats. As the banking industry grapples with the digital transformation, the guide serves as a beacon, ensuring that the code underpinning crucial financial transactions adheres to the highest security standards. Its best practices are informed by real-world challenges and validated by industry news, such as the OWASP Top 10, which sets the benchmark for secure web application development.
Organizations can leverage this guide to ensure their code is robust and resilient against cyber threats, ultimately supporting operational efficiency and compliance with stringent regulatory requirements. As digital banking continues to advance, the OWASP Secure Coding Practices Quick Reference Guide remains a vital asset for developers and organizations determined to maintain a secure and trustworthy digital presence.
Key Sections of the OWASP Secure Coding Practices Guide
The OWASP Secure Coding Practices Guide is an essential resource for developers to create secure software. It outlines fundamental principles in securing code, including vital topics like input validation, to prevent malicious data from causing harm, and output encoding, to ensure data is safely rendered on the client side. Error handling and logging are also covered, emphasizing the need to manage errors without exposing sensitive information, while maintaining thorough records for tracing and rectification purposes.
Access control and authorization are crucial in defining user permissions and preventing unauthorized access. Cryptographic practices are highlighted to protect data in transit and at rest, ensuring that sensitive information remains confidential and tamper-proof.
For instance, M&T Bank, with its extensive history and commitment to security in the digital banking sphere, employs standards like these to maintain the integrity of their systems amidst the industry's rapid technological advancements. Such stringent measures are necessary to mitigate the risks of severe security breaches and the consequent financial and reputational damage.
In light of recent news, such as Microsoft and Google's initiatives to phase out outdated TLS protocols, the guide's emphasis on adopting modern security measures is more relevant than ever. These industry giants are setting a precedent for enhanced security standards to combat the sophistication of cyber threats.
The guide doesn't just address current security practices but also serves as a touchstone for ongoing education and adaptation. Regular security training, as advocated by cybersecurity experts, is essential for development teams to stay abreast of evolving threats and best practices. It's an investment in proactive defense, shaping a security-conscious culture and equipping teams with the necessary knowledge to navigate the cybersecurity landscape.
Secure Coding Practices Checklist
To fortify software against cyber threats, a secure coding practices checklist is indispensable. This checklist is a strategic framework for developers to scrutinize their code and unearth any underlying security gaps. In the face of the digital revolution within industries like banking, where institutions like M&T Bank are pivoting towards all-digital customer experiences, the importance of secure coding has never been more pronounced.
The necessity to protect sensitive data and transactions demands adherence to stringent security standards to avert potential breaches and the accompanying financial and reputational fallout.
A practical example of implementing secure coding standards comes from NISTIR 8397, which provides a blueprint for building robust software across programming languages. It emphasizes the use of threat modeling adapted to the scale of development, minimizing extraneous alerts and focusing on critical security considerations. For instance, when developing new features, including a security requirements questionnaire in the functional requirements can help pinpoint which parts of the Software Development Life Cycle (SDLC) will be affected.
The recent collaboration between Microsoft and Google to discontinue outdated TLS protocols underscores the industry's commitment to advancing online security standards. Transitioning to TLS 1.2 and 1.3 is a proactive step toward bolstering defenses against evolving cyber threats.
In the spirit of knowledge sharing and actionable advice, here's a compendium of tips to enhance secure coding practices. This cheat sheet should be kept within arm's reach, serving as a constant reminder of the best practices that need to be ingrained in every developer's workflow. For those integrating AI into applications, it's crucial to understand the implications for security and to harness Ai's potential to improve the security posture of applications.
From Google's extensive experience, it's clear that focusing on the developer ecosystem is both practical and effective in significantly reducing common coding defects. This involves not just catching bugs post-development but also instilling Safe Coding principles to preempt potential vulnerabilities. Recent studies have shown that Large Language Models (LLMs) can effectively classify code as secure or insecure, elucidate weaknesses, and suggest remediations, thus enhancing the secure coding process beyond traditional static analysis.
In conclusion, to achieve quality assurance at scale, it is essential to simplify the application of security guidelines for development teams, thus lowering the systemic introduction of defects throughout design, development, and deployment stages.
Software Security Principles Overview
Embedding core security principles into software development is paramount for crafting secure applications. Developers must embrace critical concepts such as the principle of least privilege, which dictates that code should operate with the minimal level of access rights required to perform its function, thereby reducing the potential for misuse or exploitation. Similarly, defense in depth—layering security controls throughout the software—can prevent single points of failure and provide backup measures in case one layer is compromised.
Secure by default is another essential principle, ensuring that software is not vulnerable out of the box and requires explicit action by the user or administrator to reduce its security posture. This approach is vital in an era where digital transformation in sectors like banking is accelerating, and the need for robust security measures has never been greater. For instance, M&T Bank, with its extensive history, has had to adapt to this digital shift by setting organization-wide Clean Code standards to maintain the integrity and performance of its software, reflecting the industry's broader move towards an all-digital customer experience.
The banking industry's pivot to digital platforms has heightened the need for stringent security practices due to the sensitive nature of transactions and data involved. Defects in software can lead to dire consequences, such as security breaches and reputational harm. In response, financial institutions have ramped up efforts to ensure their software meets high-quality standards and remains within regulatory compliance.
The importance of integrating security into every phase of the software development lifecycle (SDLC) cannot be overstated. Implementing security from the outset not only minimizes the potential for vulnerabilities but also reduces the cost and complexity of addressing issues post-deployment.
As we examine the broader tech landscape, it's clear that security concerns are not confined to banking. A report by Silverfort and Osterman Research highlights that 83% of organizations have suffered data breaches due to compromised credentials, underscoring the vulnerability of resources such as command-line tools and legacy systems. Furthermore, the continuous evolution of threats necessitates that developers stay informed and proactive, making security an ongoing priority in the SDLC.
With the rise of AI-generated code and the prevalence of open-source software, the composition of codebases has become increasingly complex. The 2024 OSSRA report reveals that an average application contains 526 open source components, driving home the need for automated security solutions like software composition analysis to manage the scale of potential vulnerabilities. This complexity is a testament to why security must be at the forefront of developers' minds, as manual testing alone is no longer feasible.
In conclusion, adhering to foundational security principles, continuous vigilance, and employing automated tools are essential strategies for developers to enhance the security posture of their applications in a rapidly evolving digital landscape.
Top Secure Coding Best Practices
Adhering to secure coding practices is a cornerstone of developing robust and reliable software. Developers are tasked with fortifying their code against a myriad of security threats, such as typosquatting attacks and malicious packages. Proper input validation stands as the first line of defense, preventing attackers from exploiting your application by inserting harmful data.
Similarly, output encoding is crucial to prevent injection attacks, ensuring that data sent to the browser does not execute as code.
Secure authentication and password management are the gatekeepers of your system, safeguarding user credentials and access. Implementing multi-factor authentication (MFA), as detailed in a security policy analysis by Silverfort, can significantly enhance your security posture. According to a study by Silverfort and Osterman Research, 83% of organizations have suffered data breaches due to compromised credentials, underlining the importance of robust authentication systems.
Sessions are another critical aspect that requires stringent management to prevent unauthorized access. Error handling must be performed with care to avoid leaking sensitive information, while file and database access must be tightly controlled to prevent unauthorized data manipulation.
As the banking industry, exemplified by M&T Bank's digital transformation, increasingly adopts new technologies, the demand for secure coding rises to meet strict regulatory requirements. Security by design, an approach recommended by experts, involves integrating periodic risk assessments to identify and mitigate vulnerabilities early in the development process. This proactive strategy not only enhances product quality but also saves time and resources.
Furthermore, regular security training is essential for a development team to stay ahead of evolving cyber threats. A mix of interactive workshops, online courses, and scenario-based training can foster a proactive security culture. Education is hailed as the best security tool, especially when budget constraints limit the use of expensive security tools.
In conclusion, secure coding is not just about following a checklist; it's about cultivating a culture of security awareness and integrating best practices into every phase of development. By doing so, developers can reduce the risk of security vulnerabilities and protect their software from the ever-present threat landscape.
Security by Design
Embracing security by design is not merely an option but a necessity in today's software development landscape. It requires a fundamental shift in how we perceive security in the development process – as an integral feature, not an afterthought. To achieve this, developers must scrutinize every layer of their project, from its overall structure to its most intricate functions.
An initial step involves determining whether the code is original or a derivative (fork), and if it's the latter, assessing the extent of modifications made to it. This examination is crucial in identifying potential vulnerabilities that could compromise the system.
Closed-source software, by its nature, guards its source code from public access, thereby providing an additional security measure by obscuring potential weaknesses from would-be attackers. However, this approach also means that security relies heavily on the original developers, without the benefit of community auditing that open-source software enjoys. The open-source model, while exposing code to potential threats, also invites a global community of developers and security experts to review and collaboratively address issues, often leading to more robust and trustworthy software.
Moreover, the recognition of security as a paramount feature has been echoed by industry experts who advocate for giving developers the necessary time to construct a secure infrastructure. The Secure by Design principles emphasize this mindset, urging software manufacturers to make a good-faith effort towards integrating security from the ground up and to document their progress transparently.
Recent statistics indicate a collective movement towards these principles, with industry leaders across the globe recognizing the need for a paradigm shift in software development. The expansion of partnership in the white paper on Secure by Design principles showcases the industry's eagerness to engage in this critical conversation. It's clear that the most successful products in the coming years will be those that reject the status quo and weave security into the very fabric of their design.
Against this backdrop, developers are urged to not only keep abreast of the latest vulnerabilities but also to embrace practices that systematically incorporate security considerations into the development lifecycle. This means analyzing trends, understanding the implications of security defects, and generalizing remedies to bolster the security posture of software applications. With these practices in place, developers can proactively prevent system failures, compromises, and data leaks, thereby safeguarding their customers and their reputation.
Password Management and Authentication
Strong password policies, multi-factor authentication (MFA), and secure storage practices are crucial in fortifying the security of user accounts and thwarting unauthorized access. Non-stop dogwear, a dog equipment retailer, once had employees sharing credentials, leading to security vulnerabilities. To scale their global business securely, adopting stringent password management was pivotal.
Similarly, a financial services company faced the complexity of ensuring data remained within Canada while supporting a remote workforce, making robust credential management a necessity.
Understanding the significance of secure authentication is the first step. It's the cornerstone of protecting sensitive information and maintaining the trustworthiness of organizations. Hashing passwords, as opposed to storing them in plain text, is one best practice that enhances security by making it computationally impractical to derive the original password from the hash.
News reports highlight the dire consequences of inadequate authentication measures, such as the potential for hackers to exploit Active Directory accounts for social engineering attacks. With 83% of global organizations suffering data breaches due to compromised credentials, the integration of password managers is no longer optional but a critical component of cybersecurity infrastructure.
Firewalls play a defensive role in network security, but they're not sufficient on their own. Password managers can be integrated at every level to create a more robust barrier against cyber threats. This is particularly important for small and medium-sized businesses (SMBs), 67% of which admit to lacking in-house expertise to manage data breaches.
In light of the staggering 236.1 million ransomware attacks reported in the first half of 2022, proactive measures are essential.
Beyond the practical benefits of password managers, they also promote efficiency. Consider the quote from Jeff Marmins, CEO of SolarQuote, who emphasizes the dual advantages of enhanced security and improved workflow efficiency. As we secure our digital identities, remembering the lessons from the past, when physical locks and keys were sufficient, is critical.
Today's landscape demands more sophisticated solutions to verify identities over the internet and protect against the ever-evolving cyber threats.
Access Control and Authorization
Access controls are integral components of web applications, ensuring that only authorized users have the ability to interact with sensitive resources and execute specific operations. Practices such as role-based access control (RBAC), the principle of least privilege, and secure session management are pivotal in safeguarding these digital environments. RBAC, for instance, enables a granular approach to permissions, allowing users to access only what they need based on their role, which is pivotal in scenarios ranging from e-commerce to complex platforms like Reddit's advertising system, where swift and accurate authorization checks are indispensable.
When implementing access control, it's essential to consider where permissions are evaluated—be it at the frontend, backend, or database level—to prevent unauthorized actions, such as a regular user modifying content they can only read. With tools like Silverfort's platform, authentication requests, including those from legacy systems, are scrutinized for potential risks, thereby enforcing multi-factor authentication when necessary. In fact, a report by Silverfort and Osterman Research highlighted that 83% of global organizations have suffered data breaches due to compromised credentials, underscoring the importance of robust access control measures.
Furthermore, the intersection of application and authorization data is a critical point to consider. As an application scales, the overlap between data used for the application's core functions and that used for authorization decisions increases, demanding constant evaluation and adjustment. Inevitably, improper access control, which encompasses authentication, authorization, and auditing, leads to vulnerabilities that can be exploited, allowing unauthorized access.
Adequate training, policy development, and auditing are essential to ensure that access control measures are effectively implemented and maintained, as suggested by insights from ASIS research and security consultants. To remain effective, these systems must evolve with the organization's needs and technological advancements.
Error Handling and Logging
To build software that not only functions well but also provides a seamless experience for users, it's crucial to have effective error handling and logging practices in place. These practices are not just about fixing problems; they're about anticipating and preparing for potential issues to streamline the user's journey. Properly managed error handling ensures that when an application encounters an unexpected scenario, it responds in a way that maintains user confidence and facilitates quick resolution.
When considering error handling, it's essential to design software with the user in mind. Users expect to interact with applications smoothly and without interruption. Any hiccup in the process can be frustrating and detracts from the overall experience.
Therefore, error messages should be clear, informative, and guide the user towards the next steps, rather than leaving them confused or concerned about the integrity of their transaction.
Logging is another critical component of a well-oiled software machine. It's not just about recording what happened; it's about understanding the context of operations within the application. This understanding is pivotal when you're in the thick of troubleshooting.
Effective logging practices involve capturing detailed information that pinpoints where something went awry, without exposing sensitive user data. Each log entry should be considered carefully—asking whether the information logged could inadvertently reveal user details or compromise security is a necessary step in safeguarding privacy.
Moreover, security-related events must be logged with particular care. As the adage goes, 'you can't improve what you can't measure.' Logging security events allows for a clear assessment of an application's security posture, and aids in the quick identification and patching of vulnerabilities.
It's a proactive approach that can prevent issues from escalating into serious threats.
In this digital era, where software applications are integral to our daily lives, the significance of robust error handling and secure logging mechanisms cannot be overstated. They are the underpinnings of trustworthy software that not only performs its intended functions reliably but also respects and protects the user's data and experience.
System Configuration and Patch Management
Understanding and implementing secure system configuration play a pivotal role in fortifying software applications against cyber threats. A robust approach involves starting with secure defaults, which means setting the highest security settings by default. This is a foundational step in reducing the attack surface of your application.
Moreover, it's crucial to disable services that are not required for your application's functionality. Every unnecessary service running on a system can act as a potential entry point for attackers, hence minimizing these is a proactive security measure.
Regular patching cannot be overstressed. The significance lies in the fact that as vulnerabilities are discovered, patches are developed to fix them. Ignoring patch updates is akin to leaving your doors unlocked in a high-crime area; it's an open invitation for an attack.
The varying states of software flaws—from unaffected to exploited—highlight the dynamic nature of vulnerabilities. Keeping software up-to-date ensures that known vulnerabilities are addressed, significantly reducing the risk of exploitation.
For instance, the recent updates in Spring Boot, where a discrepancy in the spring.jms.listener.concurrency property behavior was corrected, exemplify the kind of attention to detail required in patch management. This sort of vigilance is necessary to maintain the integrity and security of software applications.
While the internet and technology have evolved at a breakneck pace since the creation of ARPANET in 1969, the principles of secure system configuration and patch management have remained fundamentally unchanged. These practices are as relevant today as they were decades ago, even as we've transitioned from mainframes to cloud computing. The evolution of computer security has been significant, yet the core requirement for proper system configuration and diligent patch management persists as a cornerstone of cybersecurity.
Threat Modeling and Risk Assessment
Understanding and mitigating security threats is a critical component of the software development lifecycle. Through threat modeling and risk assessment, developers can preemptively identify potential security threats and evaluate the risks associated with them. This proactive approach enables developers to prioritize security measures and judiciously allocate resources to fortify the application against attacks.
Threat modeling begins with a comprehensive understanding of potential vulnerabilities, such as those found in SQL, which is commonly used for managing data in relational databases. SQL injections, for example, are a type of security threat where attackers exploit vulnerabilities to execute malicious SQL statements. By recognizing such vulnerabilities early in the development process, teams can implement robust validation processes to prevent security breaches.
Real-world case studies, like the analysis of Moodle—a widely used learning management system—not only highlight the complexity of software systems but also underscore the surprising security implications that can arise, such as authorized users inadvertently having the ability to execute Cross-Site Scripting attacks.
Incorporating threat modeling into the development process is not just about identifying potential risks; it's about integrating security considerations from the outset. Architectural Decision Records (ADRs) can be instrumental in documenting security decisions within an agile framework, ensuring that threat modeling aligns with the rapid pace of development. Whether it's through the implementation of STRIDE—a methodology for identifying security threats—or the use of checklists and continual learning, the focus remains on embedding security into the fabric of the development process.
The Security Development Lifecycle (SDL) approach, adopted by many global corporations, emphasizes the importance of defining security and privacy requirements at the beginning of product development. These requirements evolve as the product matures, necessitating the continual adaptation of threat models to address both existing and emergent risks.
Supporting this approach, NISTIR 8397 provides valuable guidelines for building secure software and illustrates how threat modeling can be scaled to align with development needs while minimizing irrelevant information. For agile teams, incorporating security considerations into the feature development process through a security requirements questionnaire can streamline the SDL and ensure that threat modeling remains relevant to the changes being introduced.
In sum, threat modeling and risk assessment are not just steps in the development cycle—they are integral practices that underpin the creation of secure, resilient software products in an ever-evolving threat landscape.
Cryptographic Practices
Protecting digital assets through robust cryptographic practices is essential, especially in sectors where sensitive data is prevalent, like banking and healthcare. Implementing effective cryptographic measures is not just about using strong encryption algorithms; it also involves meticulous key management and the generation of secure random numbers. Doing so ensures that data remains confidential, its integrity is preserved, and its authenticity is verifiable.
Proper encryption renders sensitive data unreadable to unauthorized individuals, converting plaintext into ciphertext. The decision to encrypt data should be deliberate, taking into account the nature of the data and the potential risks involved. For example, password storage typically avoids encryption, as the goal is not to recover the original text but to verify identity securely.
Key management is another critical aspect. It's the process of handling cryptographic keys throughout their lifecycle, ensuring they're generated, distributed, stored, rotated, and destroyed securely. Secure key management prevents unauthorized access and maintains the strength of the cryptographic system.
Furthermore, secure random number generation underpins many cryptographic processes. Random numbers are used in key generation, nonces, and other cryptographic primitives. Inadequate randomness can weaken cryptographic systems, making them vulnerable to attack.
In the ever-evolving landscape of cybersecurity, it's also vital to stay ahead of emerging threats. Post-quantum cryptography is gaining attention as quantum computing advances, posing a risk to current encryption methods. By proactively adopting cryptographic best practices, developers can fortify their applications against both current and future threats.
Ultimately, the goal is to reduce the cognitive load for those interacting with your systems. The cleaner your code and documentation, the easier it is for team members to understand and implement these cryptographic standards effectively, enhancing the security posture of your software. This is particularly relevant in high-stakes environments where data breaches can have severe consequences, underscoring the importance of vigilance and continuous improvement in cryptographic practices.
Input Validation and Output Encoding
Ensuring the security of web applications requires robust input validation and output encoding to guard against threats like cross-site scripting (XSS) and SQL injection. Input validation acts as the first line of defense, scrutinizing user-provided data to prevent malicious code from entering the system. For instance, in our analysis of Moodle, a prevalent learning management system, we observed that all variables in the validation process are replaced with the number 1.0, and the formula is converted to lowercase with spaces removed, highlighting the importance of thorough input sanitization.
Output encoding, on the other hand, ensures that any data rendered in the browser is treated as displayable text, not executable code, thus neutralizing potential XSS attacks. Highlighting the significance of this approach, Google's latest security insights emphasize the need for ongoing research and application of practical techniques to fortify systems against such vulnerabilities.
Recent advancements have shown that large language models can now accurately classify code as secure or insecure and suggest improvements, promising a more streamlined secure coding process. This is a crucial development, as security scans often lead to a rush of last-minute fixes. With these models, developers are equipped with tools that can preemptively identify and rectify security flaws.
In the context of Node.js applications, the industry is moving towards a simplified and condensed set of best practices. These include detailed explanations of attacks and prevention strategies tailored to Node.js, such as avoiding typosquatting attacks and malicious packages.
Understanding and preventing vulnerabilities like those found in smart contracts, where attackers exploit numerical operations to manipulate critical values, is also essential. The OWASP Smart Contract Top 10 provides insights into the top vulnerabilities within Web3 development, serving as a vital reference for security teams.
In essence, developers must remain vigilant and proactive, employing both traditional techniques and innovative tools to ensure the security and integrity of their applications. As we continue to learn from real-world vulnerabilities, it's clear that collaboration among application security engineers, researchers, and developers is key to safeguarding our digital landscape.
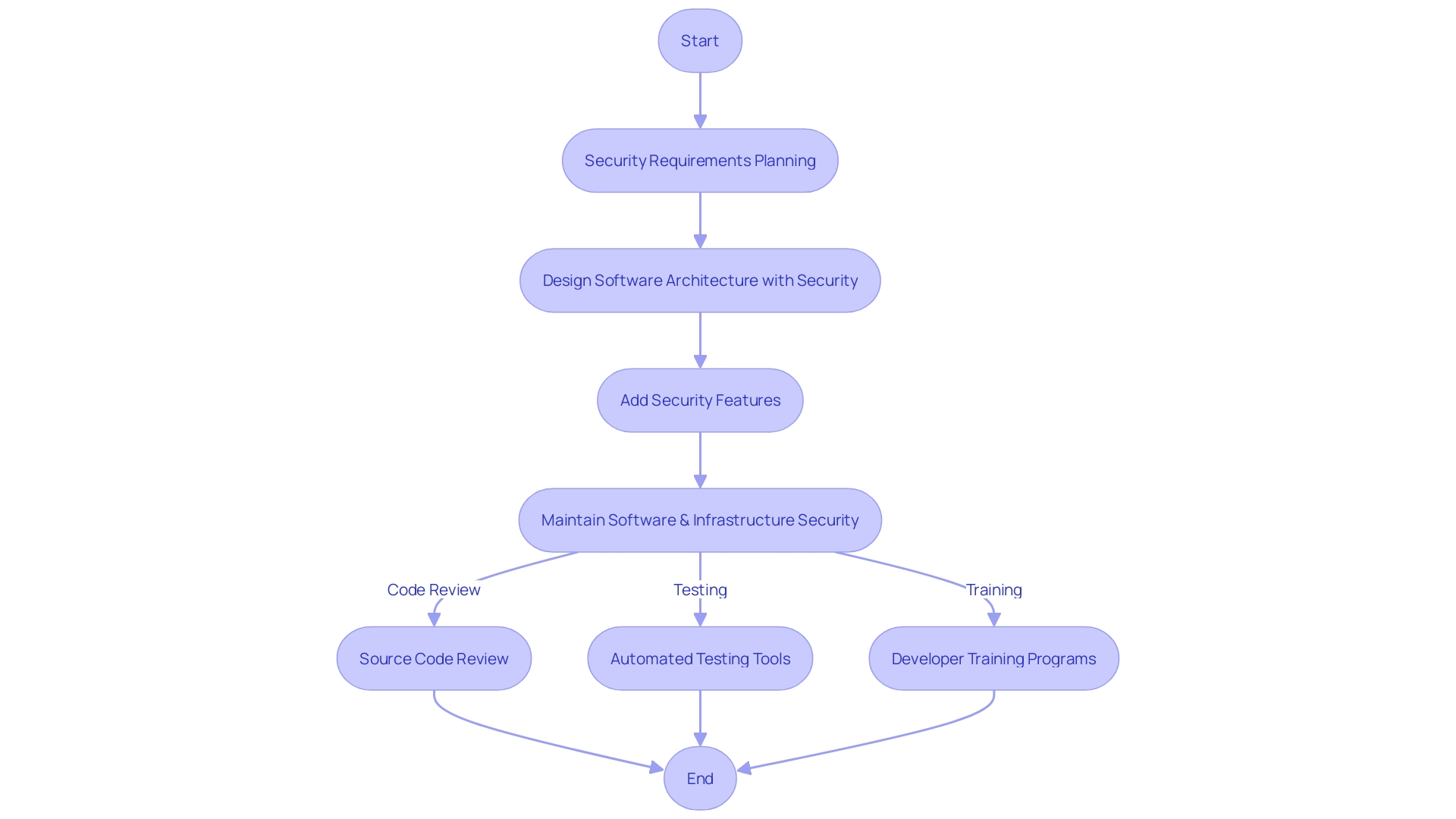
Implementing Secure Coding Standards in Your Organization
Upholding secure coding standards is essential for maintaining the integrity of software applications. To effectively embed these standards within an organization, a multifaceted approach is necessary. This involves the adoption of code reviews, automated testing tools, and comprehensive developer training programs.
Take, for instance, M&T Bank, a longstanding institution in the banking sector. They faced the formidable task of instituting Clean Code standards across their development teams. In an industry where the stakes for security are exceptionally high, and the cost of software vulnerabilities can be devastating, M&T Bank's initiative serves as a case study for the necessity of robust coding practices.
Regular security training is the foundation of a security-aware development team. Cybersecurity threats are constantly evolving, and ongoing training helps developers stay abreast of the latest threats and mitigation strategies. This investment in knowledge not only builds a proactive security culture but also is crucial for the maintainability and performance of software.
Security as Code (SaC) is also a pivotal practice, integrating security into every phase of the development process. By defining security policies, tests, and scans as code, these measures become an automated part of the software development lifecycle (SDLC), aligning with the principles of DevSecOps. This shift-left approach ensures security considerations are made early and consistently throughout the SDLC.
The importance of these practices is underscored by the impending EU's Cyber Resilience Act and the efforts of the Eclipse Foundation and the Apache Foundation to establish security standards. They recognize the vital role of open source software and the need for comprehensive documentation and alignment of security practices.
As noted by industry experts, the quality of code is directly linked to security. With the prevalence of open source software in today's software infrastructure, it's crucial that security standards include both open source and proprietary software development.
In conclusion, establishing and reinforcing secure coding standards is not merely about adhering to best practices; it's about safeguarding the reputation, financial stability, and trustworthiness of an organization in the digital age.
Resources and Tools for Secure Coding
A wealth of tools and resources are available to developers to bolster their secure coding practices. The Open Web Application Security Project (OWASP) offers comprehensive secure coding resources that serve as a vital reference. Additionally, developers can turn to security testing frameworks to detect vulnerabilities early in the development process.
Established organizations provide secure coding guidelines which act as a roadmap to writing safer code. Moreover, code analysis tools can scrutinize code for potential security flaws. Utilizing these assets not only enriches developers' security knowledge but also streamlines the coding process, making it more secure and efficient.
Embracing secure coding practices is essential in sectors where security is paramount, such as the banking industry. Historical examples like M&T Bank, with its long-standing reputation and commitment to digital transformation, have set organization-wide Clean Code standards. These standards are critical in maintaining software maintainability and performance while ensuring efficiency, reliability, and security.
In the face of escalating cyber threats, regular security training for development teams is indispensable. It keeps the team abreast of the latest threats and best practices necessary for a proactive security culture. Effective training can range from interactive workshops to online courses and scenario-based exercises.
Security in software development is not just a feature; it is a foundational principle. Every engineer shares the responsibility of prioritizing security to prevent unauthorized access to systems and data. Challenges like securely storing essential user data within a browser highlight the intricacies involved in secure coding practices.
The recent 2024 OSSRA report underscores the criticality of visibility into open source components within your code, emphasizing the creation and maintenance of a Software Bill of Materials (SBOM). Keeping open source components updated is as crucial as maintaining proprietary code. Furthermore, consolidating and correlating results from different security tests is a significant concern for security and DevOps teams, which can lead to delays in addressing critical vulnerabilities.
The banking industry, heavily reliant on digital platforms, serves as a prime example of the importance of secure coding practices in safeguarding sensitive data and transactions.
Conclusion
In conclusion, secure coding practices are crucial for safeguarding software applications from vulnerabilities and security breaches. Incorporating security from the outset, known as 'Security by Design', is fundamental in any development project. DevSecOps prioritizes proactive security measures throughout the software development lifecycle, while a Secure Software Development Lifecycle (SDLC) ensures that security considerations remain central at all stages.
Automation and AI solutions, like software composition analysis, are indispensable for managing the complexities of modern software supply chains. Cultivating a clean code culture facilitates smoother collaborations, especially in remote work settings. Secure coding is not just a technical requirement but a business imperative that demands a comprehensive, culture-driven approach.
By embracing risk management, collaborative practices, and advanced tooling, organizations can navigate the intricate landscape of software security and achieve maximum efficiency and productivity.
To achieve these goals, organizations can leverage Kodezi. It provides a comprehensive set of tools and resources to support secure coding practices. By following secure coding practices and utilizing Kodezi, organizations can enhance the security posture of their software applications, reduce the risk of vulnerabilities, and ensure the trustworthiness of their digital presence.
By integrating Kodezi into their development processes, organizations can create a culture of security awareness and adherence to best practices. This investment in secure coding practices not only protects sensitive data and mitigates the risks of security breaches but also contributes to the maintainability and performance of software.
In the face of escalating cyber threats and the increasing complexity of software supply chains, it is crucial for organizations to prioritize security throughout the software development lifecycle. By doing so, they can protect their reputation, financial stability, and the sensitive data of their customers. By embracing secure coding practices and leveraging tools like Kodezi, organizations can achieve maximum efficiency and productivity in software development while maintaining the integrity and security of their software applications.
Frequently Asked Questions
What are secure coding practices?
Secure coding practices are a set of protocols and principles that developers follow to protect software applications from vulnerabilities and security breaches.
Why is secure coding important in industries like banking?
In industries like banking that are undergoing digital transformation, secure coding is critical to protect sensitive customer data and maintain trust in digital platforms.
What is 'Security by Design'?
'Security by Design' is an approach where security is integrated from the beginning of the software development process, rather than being added as an afterthought, to preemptively identify and mitigate vulnerabilities.
What does DevSecOps stand for?
DevSecOps stands for the integration of development, security, and operations, emphasizing proactive security measures throughout the software development lifecycle.
How does automation and AI contribute to secure coding?
Automation and AI help manage the complexities of modern software supply chains and can classify code as secure or insecure, suggest fixes, and streamline the secure coding process.
What is the Clean Code Culture?
Clean Code Culture refers to the practice of writing code that is easy to understand and maintain, facilitating smoother reviews and collaboration, especially in remote work environments.
What statistical insights highlight the need for secure coding practices?
Insights reveal that 96% of audited codebases contain open source components, indicating a high reliance on automated security testing, and adopting safe coding practices can significantly decrease common defects.
What is the OWASP Secure Coding Practices Quick Reference Guide?
The OWASP Guide provides developers with a comprehensive set of secure coding standards to help preempt security vulnerabilities in their code.
What are key sections in the OWASP Secure Coding Practices Guide?
Key sections include input validation, output encoding, error handling and logging, access control, cryptographic practices, and more.
What is a Secure Software Development Lifecycle (SDLC)?
A Secure SDLC is a framework that ensures security considerations are central throughout all stages of software development.
What are some core security principles in software development?
Core security principles include the principle of least privilege, defense in depth, and secure by default, all aimed at reducing the risk of misuse or exploitation.
What is the importance of password management and authentication?
Strong password policies and authentication practices are vital for protecting user accounts, preventing unauthorized access, and maintaining organizational trustworthiness.
What is the role of access control and authorization in web applications?
Access control ensures that only authorized users can interact with sensitive resources and execute specific operations, thus preventing unauthorized actions.
Why is error handling and logging important in software development?
Effective error handling and logging are essential for maintaining user confidence, facilitating resolution of issues, and preventing security threats.
What is system configuration and patch management?
Secure system configuration involves setting secure defaults and disabling unnecessary services, while patch management ensures that known vulnerabilities are addressed through regular updates.
What is threat modeling and risk assessment?
Threat modeling and risk assessment involve identifying potential security threats and evaluating associated risks to prioritize security measures and strengthen the application's defense.
Why are cryptographic practices necessary?
Cryptographic practices protect sensitive data by ensuring confidentiality, integrity, and authenticity through encryption, key management, and secure random number generation.
How do input validation and output encoding contribute to security?
Input validation prevents malicious data from entering the system, while output encoding ensures that data is safely rendered in the browser, protecting against XSS and SQL injection attacks.
How can an organization implement secure coding standards?
Organizations can implement secure coding standards through code reviews, automated testing tools, developer training programs, and by integrating security into every phase of the SDLC.




