Introduction
In today's digital landscape, secure coding practices are not just a choice, but a necessity. The consequences of security breaches can be disastrous, making it crucial for developers to fortify software applications against prevalent threats. The banking sector, for example, has taken proactive steps to enhance software maintainability and security by implementing Clean Code standards.
Similarly, the recent near-miss cyberattack on critical infrastructure highlights the universal need for robust coding practices. To achieve maximum efficiency and productivity, developers must prioritize consistent security training, understanding of evolving threats, and the implementation of security-focused development cultures. Furthermore, automated security testing becomes indispensable, considering that most commercial software contains open source components.
By adopting a security-first mindset and focusing on safe coding practices, developers can ensure the integrity of their software and protect sensitive data. It is clear that secure coding is not just about following guidelines; it requires integrating security into the very fabric of the application. With the right practices, developers can create software that is not only functional but fortified against the ever-evolving landscape of cyber threats.
Importance of Secure Coding Practices
Adopting coding practices that prioritize protection is not just a matter of preference but an essential requirement in the modern digital environment where breaches can have catastrophic outcomes. Developers have the power to strengthen applications against prevalent threats like injection attacks and XSS by adhering to comprehensive secure coding guidelines. The banking sector is a prime example, as seen with M&T Bank's initiative to establish Clean Code standards to enhance program maintainability and security. Similarly, the recent near-miss cyberattack on critical infrastructure, relying on open-source programs, underscores the universal need for robust coding practices. Microsoft's adoption of post-quantum cryptographic algorithms, like ML-KEM, marks a proactive step in future-proofing applications against quantum attacks. Consistent training, understanding of evolving threats, and implementation of development cultures focused on protection are pivotal. With 96% of commercial applications containing open source components, and the average application comprising 526 such components, automated security testing becomes indispensable. Google's experience illustrates that a developer ecosystem-centric approach can significantly reduce common defects, emphasizing the importance of Safe Coding to prevent bugs at scale. Collectively, these measures shape a security-first mindset, ensuring the software's integrity and the protection of sensitive data.
Key Principles of Secure Coding
Secure coding is akin to a fortress in the digital world, where each line of code can either be a robust defense or a breach waiting to happen. At the core of coding lie foundational principles such as meticulous input validation to prevent unauthorized data from sneaking through, rigorous output encoding to shield against data corruption, stringent authentication and authorization protocols ensuring only verified users gain access, astute error handling to avoid data leaks, and robust encryption to safeguard data in transit and at rest. Not only do these practices shrink the attack surface, but they also fortify the application against untrusted inputs, a critical step in erecting a resilient digital edifice.
When we consider the tale of M&T Bank, a venerable institution with over a century and a half of history, the stakes of secure coding climb higher. As they navigate the high seas of digital transformation, where consumer demands and technological breakthroughs steer the ship, they understand that any application vulnerability is an iceberg that could sink the enterprise. By embedding Clean Code standards within its culture, M&T Bank strives to keep its software fleet sailing smoothly, minimizing maintenance and guarding against the tempests of cyber threats and stringent regulations.
In a recent series of industry discussions, a trio of development culture components emerged as critical: ownership of protection outcomes, transparent accountability, and leadership advocacy. These pillars resonate with the insights shared by global experts who have coalesced around the whitepaper on Design principles, highlighting the consensus on the urgency of coding practices.
As we analyze the anatomy of an application that ensures safety, we must remember that security is not simply an afterthought but an essential part of the design. This perspective is echoed by the collective wisdom of those who have shaped the development landscape of reliable programs, emphasizing the need for a cultural shift towards security—a shift that is both a protective measure and a competitive advantage, as outlined by the international guidance on manufacturing dependable software.
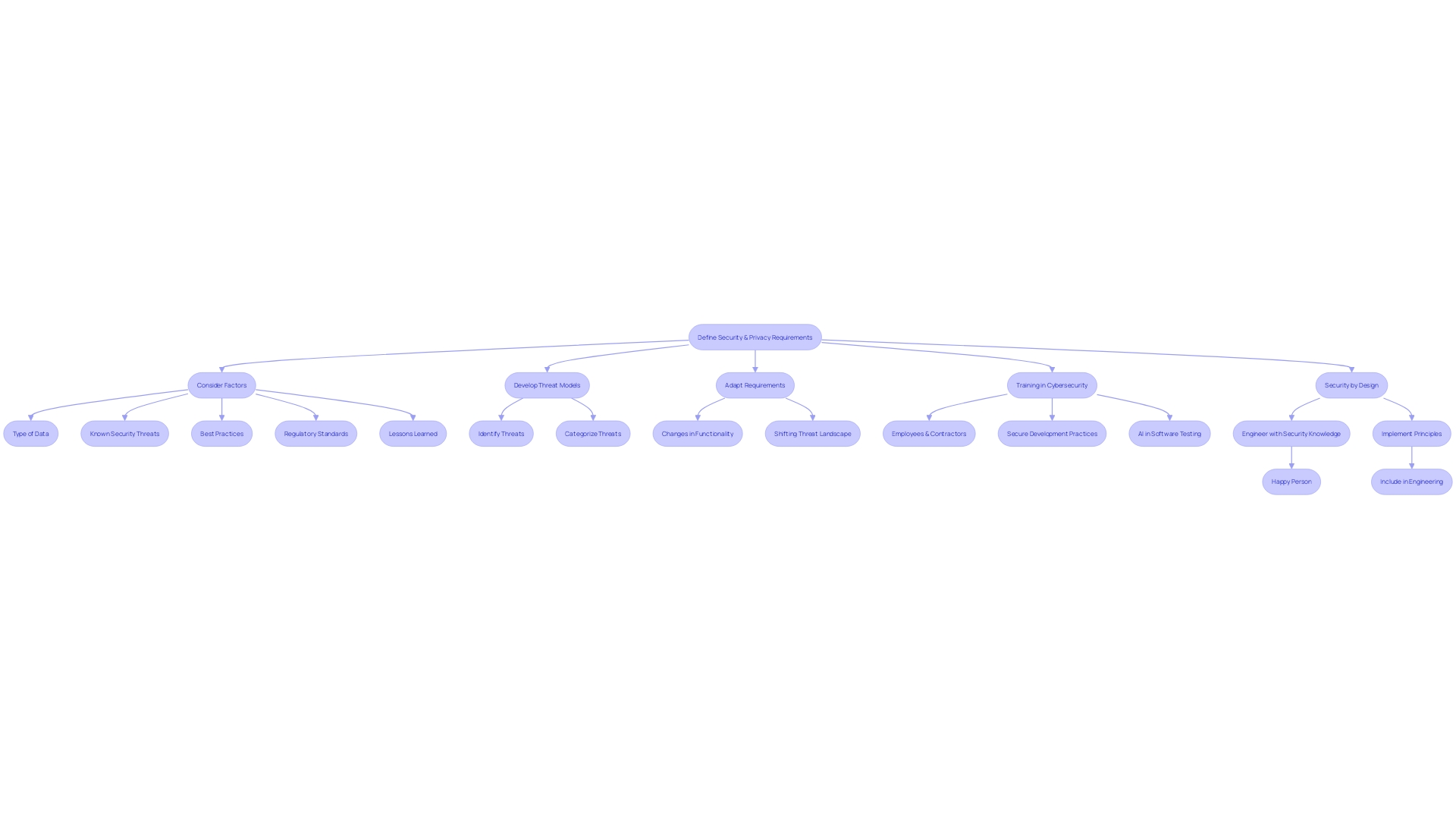
Secure Coding Standards and Guidelines
Following secure coding standards is crucial for development, especially in industries like banking where the stakes are extremely high. M&T Bank serves as a prime example of an organization that has embraced this philosophy. With over 21,000 employees and a 165-year legacy, they understand that the digital landscape is evolving rapidly, necessitating strong measures to protect sensitive data. This comprehension prompted them to execute Clean Code principles throughout the organization to improve program maintainability and performance while reducing risks linked to application vulnerabilities.
The concept of Secure by Design, reaffirmed by feedback from international partners on a recent whitepaper, is integral to these standards. It stipulates that principles of safeguarding should be embedded in the development process from the beginning. The Secure by Design approach is backed by proof, or artifacts, that show a dedication to ensuring safety throughout the application lifecycle—from planning and design to testing and maintenance. This collection of artifacts tells a story of dedication to security that is increasingly demanded by programs consumers.
It is evident that the conventional approach of implementing applications and dealing with weaknesses in subsequent updates is outdated. In today's environment, attackers are skilled at exploiting any vulnerabilities from the moment the program is released. The Secure Software Development Life Cycle (SDLC) incorporates protection into every phase of development, guaranteeing that the final product not only fulfills user requirements and quality standards but also withstands common vulnerabilities. With the rise of these stringent expectations for safety, the industry is urged to take a proactive stance in demonstrating their commitment to secure practices, thereby protecting themselves from the dire consequences of breaches.
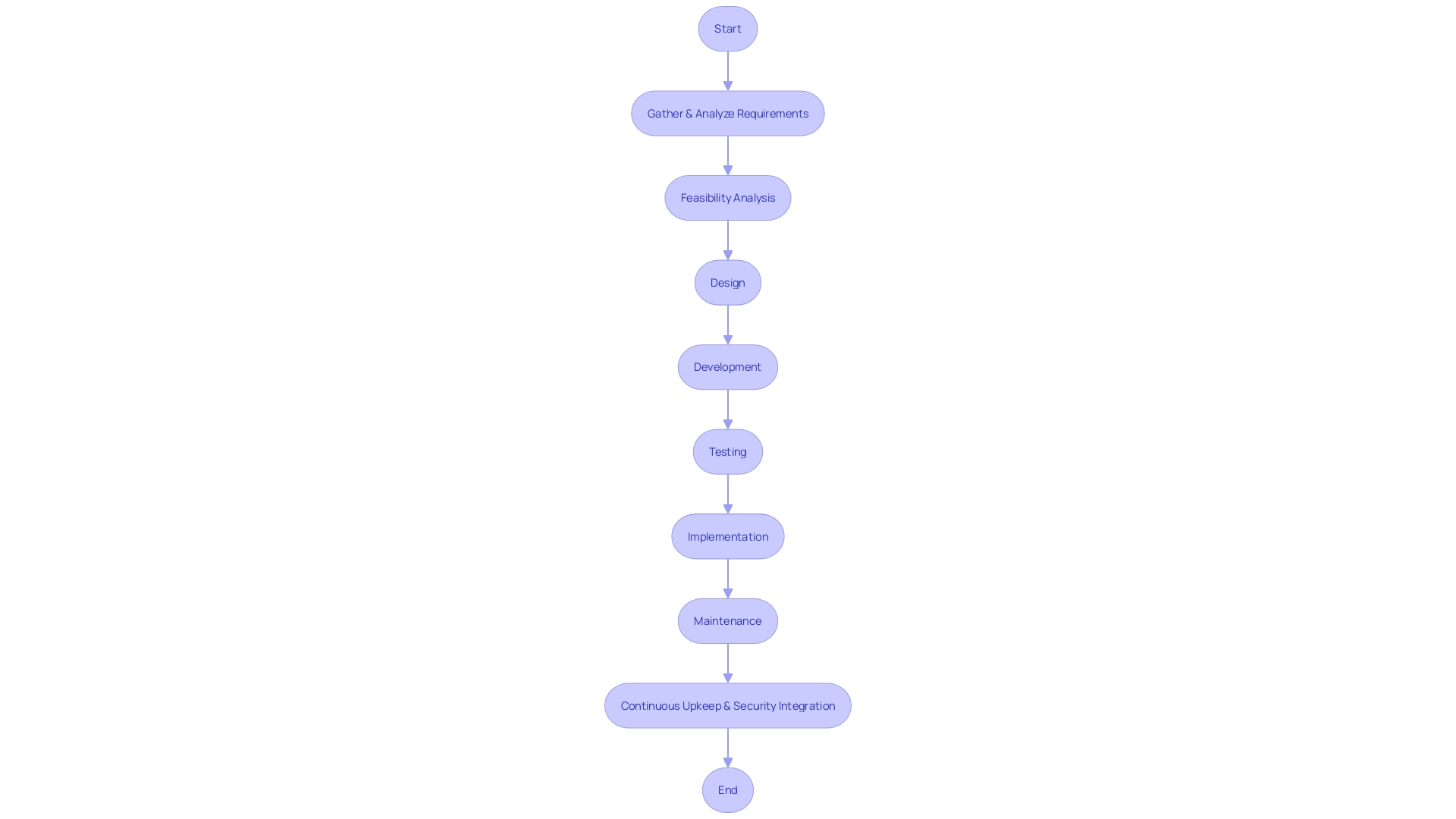
Secure Development Life Cycle (SDLC)
Incorporating protection into the development process is not only about completing a checklist of prerequisites; it's about infusing protection into every aspect of the application's essence. The Secure Development Life Cycle (SDLC) encapsulates this principle by integrating protective measures throughout the creation process of a program, starting from the initial idea to the deployment and continuous upkeep of the end result.
With the growing intricacy and interconnection of contemporary systems, safeguarding can no more be an optional addition or a final item on a checklist. Case in point: M&T Bank, with over a century and a half of history, faced the digital transformation of the banking industry head-on. They implemented Clean Code standards across their development teams to ensure that every line of code contributed to the protection and reliability of their systems, crucial for safeguarding sensitive financial data.
Security concerns are no longer hypotheticals but real-world challenges that impact the integrity of businesses and the trust of customers. For example, Ai's introduction into the SDLC poses both opportunities and risks. Ensuring that AI tools are used responsibly and securely is paramount. As development continues to evolve with new updates like Matter 1.2, enhancing device interoperability and protection, developers must remain vigilant.
The creation of protected computer programs starts with a comprehensive comprehension of its safety and confidentiality demands, which are influenced by the kind of information processed, recognized risks, and regulatory criteria. The creation of threat models and data flow diagrams during the early phases of development is essential for visualizing and mitigating potential risks. As demonstrated by Google's experience, emphasizing developer ecosystems and advocating for Safe Coding practices can result in a significant reduction in typical vulnerabilities.
In summary, the SDLC is a strategic method that guarantees safety is not an afterthought but a crucial element of software development, essential for the product's triumph and the organization's standing.
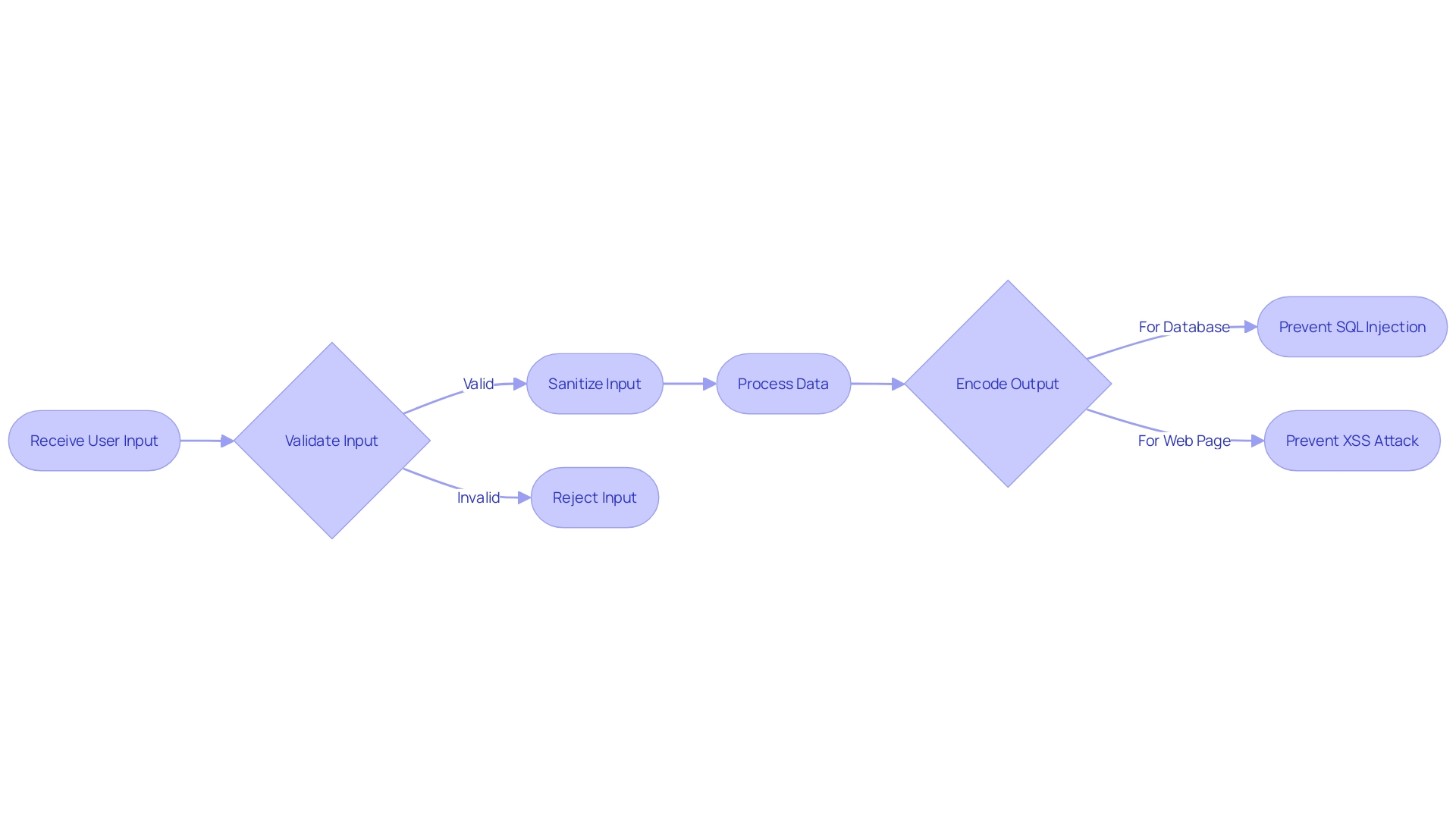
Input Validation and Output Encoding
Validating user input is not just about maintaining application functionality; it's a crucial defense against attacks. This process involves scrutinizing the data users enter into a system, ensuring it adheres to expected formats and ranges, and is of the correct data type. But it's more than just checking boxes; input validation must be robust, as it serves as the first line of defense against cunning threats like SQL injection and cross-site scripting (XSS) attacks. Sanitization plays a pivotal role here, removing any elements that could be used maliciously.
On the flip side, output encoding is equally vital. It's about ensuring that when data is echoed back to the browser or saved, it's done so safely to prevent any embedded malicious scripts from executing. This is a key tactic in thwarting XSS attacks, which can compromise an entire application.
In the real world, consider the example of Moodle, a widely-used learning management system. During a penetration test, it was discovered that users with certain roles could execute XSS attacks. This highlights the importance of steadfast input validation and output encoding in complex systems. Furthermore, with the introduction of post-quantum cryptography demonstrated by Microsoft's inclusion of the ML-KEM algorithm in its cryptographic library, SymCrypt, the focus on protection is stronger than ever.
To enhance protection further, developers can gain knowledge from case studies and expert insights. For instance, application security engineer Andreas Bergman emphasizes the significance of input validation and data sanitization in Python development. Tanya Janca, an authority in the field, also stresses the importance of secure coding practices. From implementing stringent checks to prevent PHP comment inclusion in inputs, to automating software testing and generating 'testing bots' that continuously assess software, these practices are crucial.
Despite the increasing focus on security, research involving 20 companies reveals a gap in integrating these techniques into standardized processes. This calls for more extensive research and a push towards formalizing coding guidelines as a standard development practice.
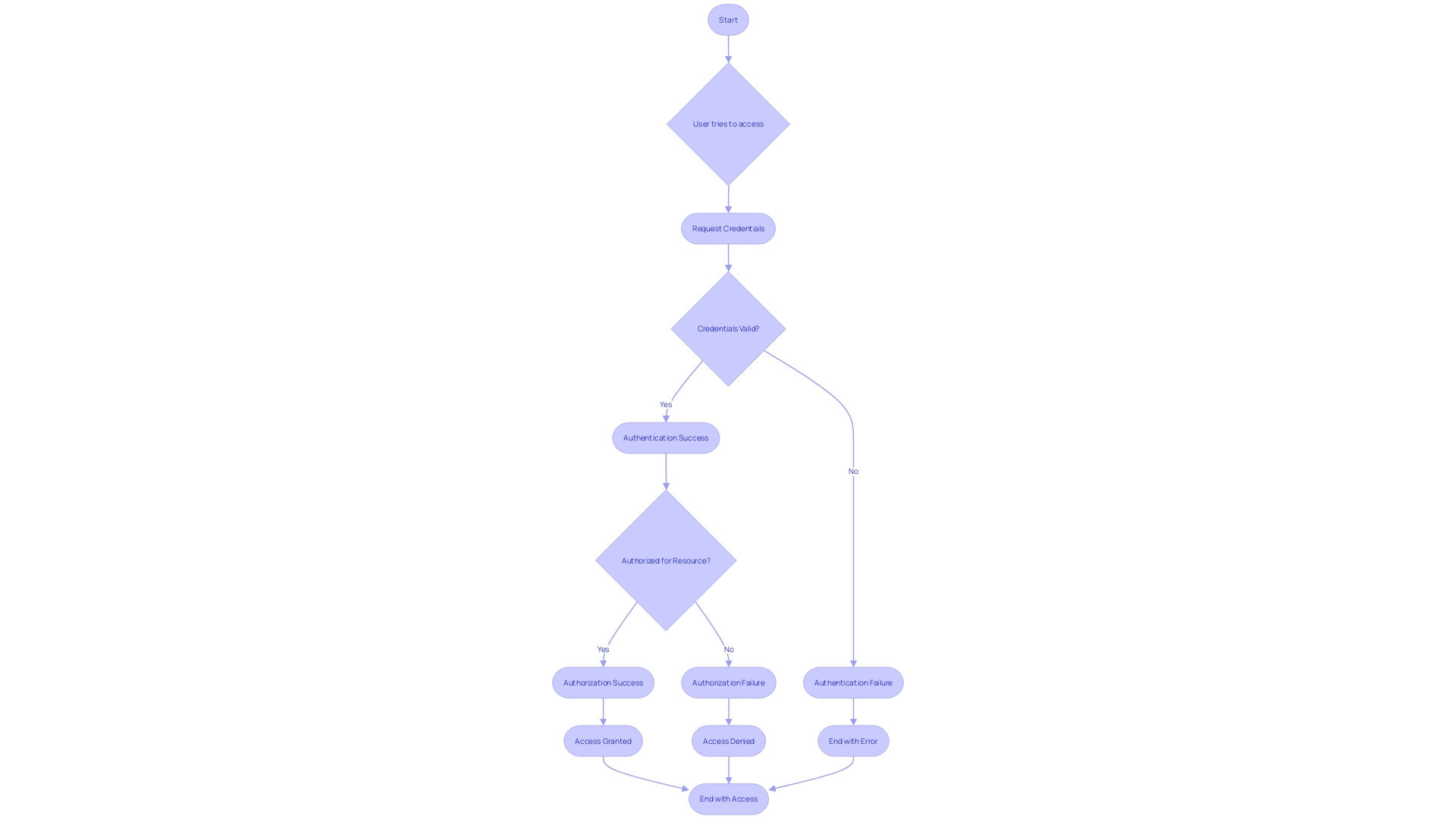
Authentication and Authorization
Mastering the principles of coding, such as authentication and authorization, is fundamental to protecting web applications. Authentication acts as the digital 'gatekeeper,' verifying a user's identity and ensuring that only those with legitimate credentials gain access. Authorization goes a step further, defining the scope of access for these authenticated users, thereby safeguarding sensitive data from unwarranted alterations or disclosures.
Consider the example of a reputable institution like M&T Bank, which has embraced Clean Code standards across its organization. By maintaining strict measures to safeguard vast amounts of sensitive data, they directly confront the challenges of digital transformation. This is indicative of the broader industry trend, where businesses strive to offer user experiences that are both seamless and secure across various platforms.
In addition, the implementation of protocols like OAuth showcases the industry's dedication to strong practices. Despite its outward simplicity, OAuth's underlying complexity provides a comprehensive solution for user authentication and authorization, which has been widely adopted by major web services.
Considering the latest advancements, we observe the launch of Matter 1.2 by the Connectivity Standards Alliance, which introduces new devices with improved safety measures, emphasizing the continuous progression in the field of cybersecurity. This is a testament to the industry's dedication to advancing secure access to systems and data.
In this digital era where protection takes precedence, the distinction between authentication and authorization becomes more pronounced. Authentication is the initial step, asking "Who are you?" and requiring credentials for verification. Authorization follows, determining what an authenticated user can access and interact with. By emphasizing these elements, we not only enhance protection but also enable a smooth user experience.
Through careful analysis, we've observed trends in defect patterns and their evolution over time, which inform us about the progress of software companies in improving protection. Instead of addressing individual defects, there's a shift towards preventing entire classes of vulnerabilities, thereby transferring the responsibility of security from developers to systemic solutions. Such an approach has been proven effective, as demonstrated by reductions in common defect rates across numerous applications, per Google's experience.
In essence, the interaction of authentication and authorization forms the foundation of coding. By implementing these mechanisms diligently, developers can significantly mitigate unauthorized access and maintain the integrity of sensitive data.
Error Handling and Logging
Robust error handling and error logging are critical pillars of secure coding practices. When errors occur, they need to be captured and managed strategically to prevent leakage of sensitive data to potential attackers. A solid error logging protocol is indispensable, serving as a valuable tool for detecting and investigating security-related incidents. By improving error handling procedures and logging practices, developers can quickly identify and fix vulnerabilities, thereby strengthening the resilience of their applications.
With the advent of new programming paradigms, such as the Practical Type System (PTS), developers are exploring innovative approaches to error handling. However, it's common to see a preference for coding along "the happy path," neglecting the less appealing but crucial task of error management. In the context of this changing environment, it's crucial to remember two straightforward but impactful guidelines: every log entry should be examined for its potential to reveal sensitive information, and developers should consistently question the necessity and implications of each piece of logged data.
Recent insights from industry leaders highlight the importance of fostering a security-centric development culture. Education is promoted as the most effective tool for enhancing application protection, particularly when resources are limited. A change in culture can result in improved outcomes, reducing dependence on expensive tools. This perspective is echoed in discussions around programming language safety, emphasizing the need for languages and their libraries to offer static and dynamic guarantees, such as type and memory safety, to make programs both secure and safe.
Empirical data from Google's experience indicates that focusing on developer ecosystems can lead to a significant reduction in common defects across numerous applications. Safe coding practices, aimed at preventing bugs, are a cornerstone of this approach. Through the analysis of trends over time, we can obtain insights into which companies are advancing in software protection and which ones need to start quality enhancement initiatives. Addressing classes of vulnerabilities rather than isolated issues allows developers to shift the responsibility of safeguarding from the least capable to the most equipped, asking, 'How can I prevent all similar vulnerabilities?' instead of "How can I fix this one defect?"
Data Protection and Encryption
Secure coding is not just a practice but a necessity, particularly in domains where data protection is paramount, such as the banking industry. Encryption is one of the foundations of data protection, safeguarding sensitive information both when stored and while being sent. Utilizing encryption means that even if data falls into the wrong hands, it remains indecipherable without the corresponding decryption key. For instance, M& T Bank, with its rich history and dedication to innovation, has confronted the task of digital transformation directly by implementing Clean Code standards throughout the organization, emphasizing the significance of upholding high protection and quality in software development.
End-to-End Encryption (E2EE) stands out as a powerful method for securing communication channels, ensuring that only the intended recipients can access and decipher the transmitted data. This approach is crucial for preventing unauthorized access, be it from cybercriminals, service providers, or any other potential interlopers. Alongside encryption, robust key management practices are essential to preserve the confidentiality and integrity of encryption keys. As the cybersecurity field keeps growing, with a workforce of around 4.7 million experts and median yearly compensation for information protection analysts at $102,600 in 2021, the commitment to secure coding measures, such as encryption and key management, becomes even more vital. This investment is necessary to navigate the evolving challenges and dynamic growth of the cybersecurity landscape and to ensure that organizations can confidently protect against cyber attacks.
Code Review and Testing
The strength of an application's protection depends heavily on thorough code reviews and rigorous testing. Code reviews are thorough evaluations aimed at detecting vulnerabilities and coding mistakes. Meanwhile, testing includes performing different tests such as unit, integration, and penetration tests to reveal possible weaknesses in the system.
According to experts in the field, having a well-defined strategy is essential when investigating issues related to the escalation of privileges. It's important to recognize the boundaries of privilege and concentrate on areas that are less examined for weaknesses, such as DBus interfaces on Linux systems. Insights from application safety engineers highlight the significance of comprehending underlying reasons for weaknesses to devise precautionary measures efficiently.
Furthermore, the most recent adjustments to the Common Vulnerability Scoring System (CVSS) highlight the importance of a nuanced assessment of weaknesses. With the implementation of extra metrics and a fresh terminology, organizations can now more effectively prioritize their responses to threats.
Real-world incidents, like the exploitation of the PaperCut vulnerability, exemplify the substantial consequences of breaches, impacting tens of thousands of organizations worldwide. These occurrences emphasize the necessity for all-encompassing protective measures integrated throughout the development lifecycle (SDL).
The Security Development Lifecycle (SDL) method is exemplary of this integrated approach, mandating cybersecurity training and secure development practices for all involved in software creation. Embracing the 'Shift Left' paradigm ensures that safety becomes a cornerstone of the development process from the outset, helping to identify and rectify issues early on.
Veracode's data analysis from millions of application scans reveals a persistent deployment of applications riddled with vulnerabilities. This reinforces the crucial requirement for organizations to embrace development practices with a focus on safeguarding, particularly in light of the continuously rising expenses linked to breaches.
Overall, developers improve application safety by incorporating regular code reviews and thorough testing into the initial phases of the development process. This proactive approach not only strengthens the final product against vulnerabilities but also aligns with the evolving safety landscape and business priorities that demand swift and reliable flow management.
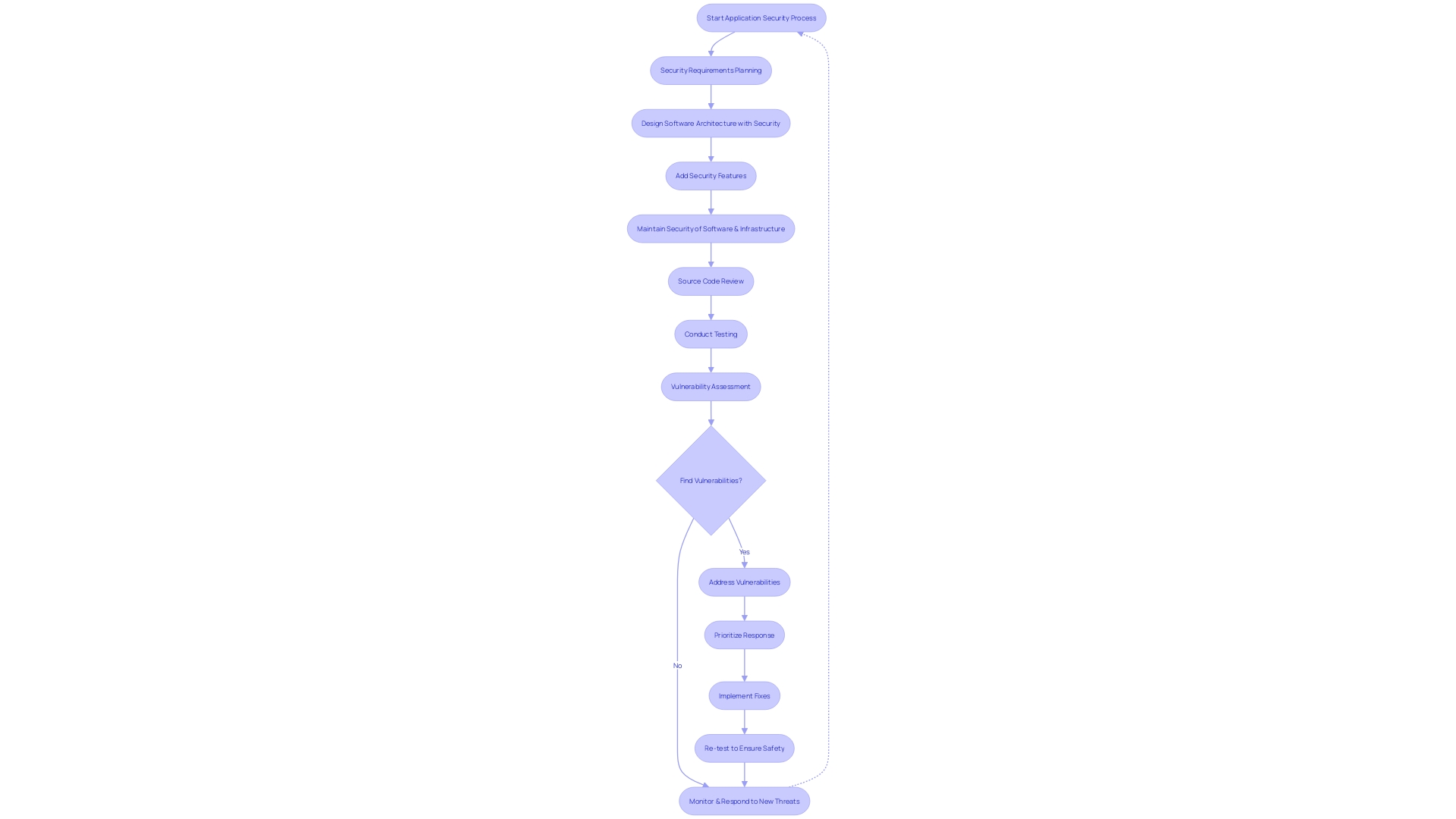
Vulnerability Management and Scanning
Maintaining the soundness of an application throughout its lifecycle is a multi-faceted challenge that involves a continuous dedication to safeguarding practices. One of the cornerstones of a secure application is the process of risk management and scanning. This is not merely a one-time event but an ongoing cycle of identifying potential threats within the codebase and the underlying infrastructure. It requires a strategic approach, starting with defining the 'privilege boundaries'—the critical points where unauthorized access could potentially be gained. For example, in the context of a Linux system like Ubuntu, security experts might focus on areas like DBus, a client/server-based remote procedure call (RPC) framework, rather than immediately targeting more obvious and often scrutinized elements like setuid binaries or file permissions.
The true skill of managing vulnerabilities lies in the prioritization and resolution of these weaknesses. This may involve patching, implementing code fixes, or other corrective actions. The key is not only to discover weaknesses, but to address them in a manner that is consistent with the organization's risk tolerance and operational needs. A statement from an industry specialist highlights the significance of this approach: 'The management of weaknesses is a methodical procedure aimed at decreasing an organization's susceptibility to threats by identifying, evaluating, and mitigating vulnerabilities.'
Nevertheless, the cyber threat landscape is constantly changing, with daily announcements of new weaknesses. Traditional models of 'annual penetration tests' or 'quarterly security scans' are no longer sufficient. Continuous scanning for vulnerabilities, with its round-the-clock monitoring and automated processes, is becoming essential, particularly for agile SaaS businesses, online retailers, and entities in highly-regulated industries such as healthcare and financial services. This shift is not just about ticking a compliance box; it's about truly securing digital assets against the next potential breach. The news reflects a stark reality: semi-regular scanning does not equate to proper vulnerability management.
The influence of engineering protection extends beyond safeguarding applications; it's about preserving the business's integrity and maintaining customer trust. As companies rely more and more on technology for operations, data storage, and customer engagement, the protection implemented at each stage of the Software Development Life Cycle (SDLC) becomes crucial. The repercussions of disregarding software safety are severe, including monetary losses, operational disruptions, and damage to reputation.
To address the overwhelming amount of data generated by advanced scanning tools, teams are looking for methods to consolidate and connect findings, emphasizing the requirement for effective management processes. This is reflected by statistics which show that organizations often take weeks, if not months, to fix identified critical weaknesses. An approach that prioritizes the integration of protective measures early in the SDLC, is advocated as best practice to not only identify but also remediate vulnerabilities more efficiently and cost-effectively. The message is clear: proactive identification and remediation of security risks are not optional but essential for ensuring the ongoing security and success of an application.
Secure Coding Training and Education
To construct resilient and protected applications, developer education in coding practices that ensure safety is crucial. This education encompasses a robust curriculum that should include crucial topics such as input validation, output encoding, and authentication, as well as language-specific secure coding practices. For instance, M&T Bank, with its extensive background and forward-thinking management, acknowledged the significance of Clean Code standards to uphold maintainability and performance. This is particularly relevant in industries like banking, where digital transformation introduces both new technologies and strict protection requirements.
A comprehensive training program also addresses authorization, error handling, and data protection. This is crucial because, as observed in the banking industry, software weaknesses can lead to serious outcomes, such as breaches and harm to reputation. For instance, SQL, a common database language, requires developers to perform functions securely to prevent vulnerabilities and attacks.
Recent talks at the National Cybersecurity Education Colloquium have emphasized the reality that protection is frequently regarded as an optional course in computer science curriculums, rather than as an essential skill. This approach risks leaving new developers unprepared for the challenges they will face in the industry. It is a call to action for technology companies, indicating the importance of incorporating safety into the developer's fundamental education.
The industry's dedication to safe coding is emphasized by feedback received on a white paper jointly endorsed by ten U.S. and international partners, which indicates that the most impactful practices for developing programs are those that integrate protection through design. By learning from patterns of defects and understanding how they change over time, developers can shift from fixing individual defects to preventing entire classes of vulnerabilities. This approach is akin to the aviation industry, where systemic analysis of incidents leads to comprehensive improvements across training and design.
In brief, coding training equips developers with the knowledge to create software that is not only functional but also protected from inception, minimizing maintenance time and costs while ensuring efficiency, reliability, and safety.
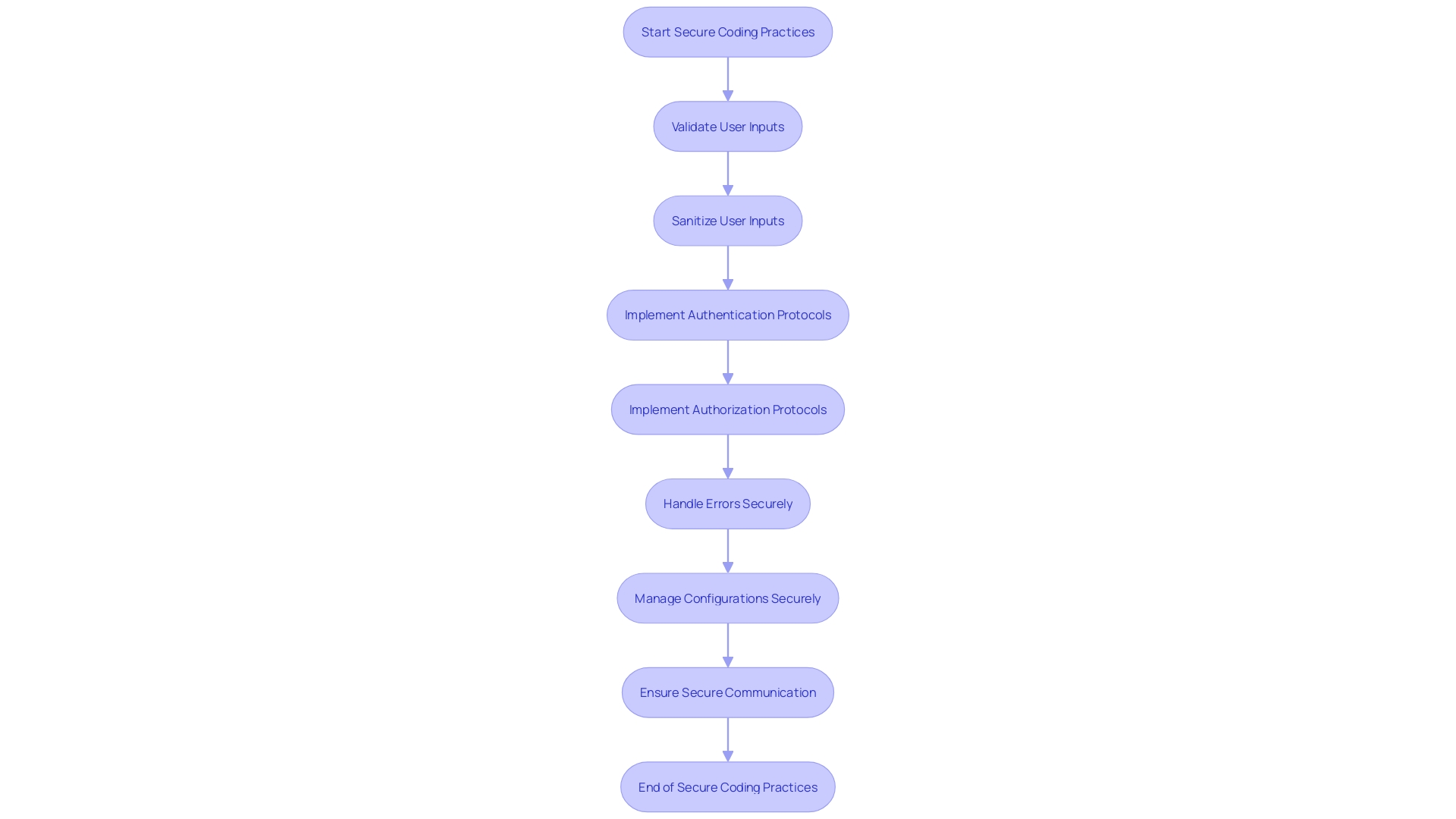
Best Practices for Secure Coding
Secure coding is not just about following a set of guidelines; it's about integrating security into the DNA of your application. Best practices start with adhering to secure coding standards that are tailored to the programming language in use. This means not just validating input rigorously but also encoding output to shut down potential vulnerabilities. Effective authentication and authorization are your gatekeepers, controlling who gets access to what within your application.
One cannot overlook the necessity of robust error handling and logging. These practices are crucial for identifying and addressing incidents promptly. When it comes to sensitive data, encryption and secure key management practices are the shields that protect this valuable information.
Peer reviews and comprehensive testing are not just a formality; they are a developer's best defense, uncovering safety issues that automated tools might miss. A proactive vulnerability management process, including regular scanning and patching, is a testament to a developer's dedication to safeguarding.
Education is key. Providing developers with the understanding of secure coding practices is as crucial as any tool in the development lifecycle. It's about building a culture of security awareness.
Consider M&T Bank's initiative to establish Clean Code standards across its development team. This effort is not merely about compliance; it's about safeguarding against the risks associated with digital transformation in the banking industry. It's about upholding the trust that millions of customers place in their financial institutions every day.
Secure coding is a continuous journey, one that requires vigilance, dedication, and a willingness to adapt. With the right practices, developers can create software that's not just functional but fortified against the ever-evolving landscape of cyber threats.
Conclusion
In conclusion, secure coding practices are crucial in today's digital landscape to protect software applications from threats and security breaches. By prioritizing consistent security training, understanding evolving threats, and implementing security-focused development cultures, developers can ensure the integrity of their software and protect sensitive data.
The adoption of Clean Code standards by M&T Bank exemplifies the proactive steps taken to enhance software maintainability and security in the banking sector. Furthermore, the recent near-miss cyberattack on critical infrastructure highlights the universal need for robust coding practices.
Integrating security into every aspect of the application is essential, as demonstrated by the Secure Development Life Cycle (SDLC). Authentication and authorization form the foundation of secure coding, while encryption safeguards data both at rest and during transmission.
Regular code reviews, comprehensive testing, and continuous vulnerability management are crucial for identifying and addressing security vulnerabilities. Education in secure coding practices equips developers with the knowledge to prioritize security from the start.
By following best practices such as adhering to secure coding standards, implementing robust error handling and logging, and prioritizing encryption and key management, developers can create software that is fortified against evolving cyber threats.
Secure coding is a continuous journey that requires vigilance, dedication, and adaptation. By embracing secure coding, developers can protect their applications, maintain customer trust, and ensure the ongoing security and success of their software.
Frequently Asked Questions
Why is secure coding important in today's digital environment?
Secure coding is essential because breaches can lead to catastrophic outcomes. By adopting protective coding practices, developers can safeguard applications against prevalent threats like injection attacks and cross-site scripting (XSS).
What are some key principles of secure coding?
Key principles include: Input Validation, Output Encoding, Authentication and Authorization, Error Handling, and Encryption.
Can you provide an example of a company implementing secure coding standards?
M&T Bank has established Clean Code standards to enhance software security and maintainability, reflecting the bank's commitment to protecting sensitive customer data.
What is the Secure Software Development Life Cycle (SDLC)?
The Secure SDLC integrates security measures throughout the development process, from planning to maintenance, ensuring that security is a fundamental aspect, not an afterthought.
What role does training play in secure coding?
Consistent training is vital for developers to stay informed about evolving threats and to understand secure coding practices. This education fosters a culture of security awareness within organizations.
How prevalent is open-source software in applications?
Research indicates that 96% of commercial applications contain open-source components, with the average application including about 526 such components, highlighting the need for automated security testing.
What proactive measures are companies taking against cyber threats?
Companies like Microsoft are adopting post-quantum cryptographic algorithms to protect against future quantum attacks, while many organizations are implementing regular code reviews and comprehensive testing to identify and address vulnerabilities early.
What are the risks of neglecting secure coding practices?
Neglecting secure coding can lead to severe consequences, including data breaches, financial losses, operational disruptions, and damage to a company's reputation.
How can developers reduce vulnerabilities in their applications?
Developers can reduce vulnerabilities by implementing robust input validation and output encoding, ensuring rigorous authentication and authorization protocols, regularly conducting code reviews and comprehensive testing, and focusing on continuous vulnerability management and proactive remediation.
Why is a cultural shift towards security necessary in software development?
A cultural shift towards security integrates protective measures into the development process, which is crucial for maintaining software integrity and protecting sensitive data in an increasingly complex digital landscape.




