Overview
Joomla security vulnerabilities pose significant risks, such as unauthorized access and data breaches. Developers must recognize and tackle these weaknesses to safeguard their applications. Among the various vulnerabilities are:
- Cross-Site Scripting
- SQL Injection
These vulnerabilities can severely compromise security. Furthermore, implementing best practices and utilizing automated tools is essential for enhancing security measures and protecting against potential threats. By addressing these vulnerabilities proactively, developers can ensure a more secure environment for their users.
Introduction
In the digital age, where data breaches and cyber threats are increasingly prevalent, the security of content management systems like Joomla warrants serious attention. As one of the most widely used platforms for website development, Joomla faces vulnerabilities that can jeopardize sensitive information and erode user trust.
Have you considered the potential risks lurking within your Joomla site? Understanding these security threats is essential for developers and site administrators alike, as the repercussions of ignoring them can be dire, ranging from unauthorized access to a complete site takeover.
This article explores the landscape of Joomla security, shedding light on:
- Common vulnerabilities
- Best practices for safeguarding your site
- The vital tools that can bolster security management
Ensuring that Joomla sites remain resilient against ever-evolving threats.
Explore Joomla Security Vulnerabilities: Importance and Impact
Joomla, a widely used content management system, faces significant risks due to joomla security vulnerability that developers must acknowledge. The presence of a joomla security vulnerability can lead to severe repercussions, such as unauthorized access to sensitive data, website defacement, and even total site takeover. Understanding the implications of these weaknesses is vital for developers, enabling them to prioritize security within their development processes. The fallout from a data breach can be catastrophic, affecting not only the functionality of the website but also its reputation and user trust. Therefore, identifying and addressing the joomla security vulnerability is essential for ensuring a secure and reliable platform.
As we look toward 2025, the security landscape for this platform is becoming increasingly intricate, particularly with the introduction of headless setups that present new challenges for API endpoints and data exchange. Implementing routine backups and maintaining vigilant oversight for unusual behavior are crucial strategies for safeguarding web platforms, as emphasized by industry experts.
A well-documented case study on incident response planning underscores the necessity of having a robust strategy in place for website management. Key elements include:
- Incident identification
- Communication strategies
These are critical for minimizing damage and downtime during a breach. Additionally, aligning protection strategies with broader business objectives is crucial for preserving brand reputation and maintaining customer confidence.
Expert insights stress the importance of utilizing protective extensions to limit unsuccessful login attempts, thereby reducing the risk of brute-force attacks. As the platform evolves, developers must prioritize addressing the joomla security vulnerability to ensure the integrity and reliability of their sites, making proactive measures not merely advisable but essential.
Identify Common Joomla Vulnerabilities: Types and Examples
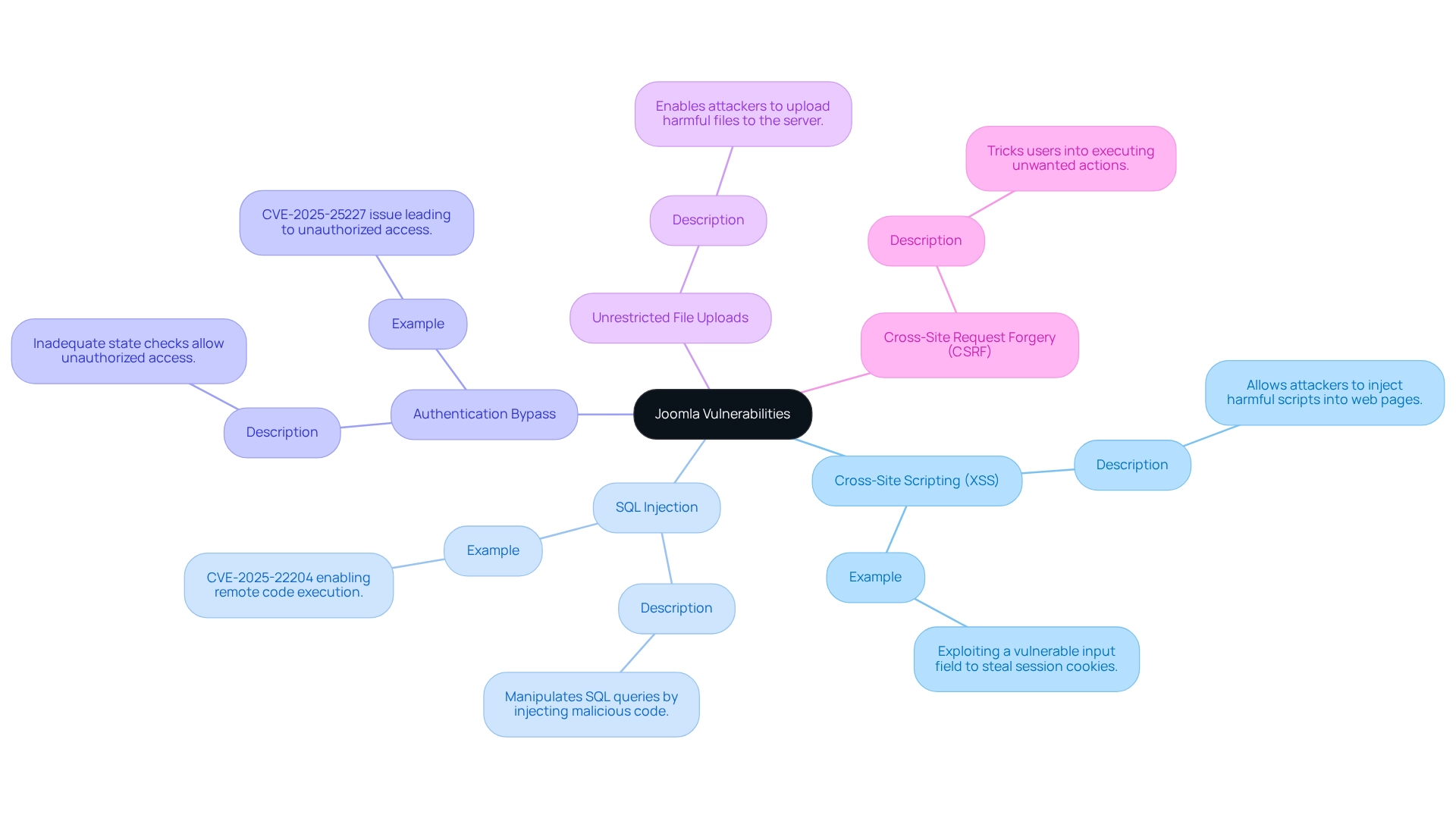
Common Joomla security vulnerabilities present significant challenges for developers, underscoring the need for awareness and proactive measures against Joomla security vulnerability.
- Cross-Site Scripting (XSS) is a prevalent weakness that allows attackers to inject harmful scripts into web pages accessed by unsuspecting users. For instance, an attacker might exploit a vulnerable input field to execute scripts designed to steal session cookies, compromising user security.
- SQL Injection is another critical vulnerability, where attackers can manipulate SQL queries by injecting malicious code, potentially gaining unauthorized access to sensitive databases. A notable example is CVE-2025-22204, which enables remote code execution due to improper control of code generation.
- Authentication Bypass occurs when inadequate state checks allow unauthorized individuals to circumvent two-factor authentication, as seen in the CVE-2025-25227 issue. This vulnerability can lead to unauthorized access to sensitive sections of the platform, jeopardizing user data.
- Unrestricted File Uploads pose a significant risk, enabling attackers to upload harmful files to the server, which can then be executed to compromise the platform's integrity.
- Lastly, Cross-Site Request Forgery (CSRF) can trick users into executing unwanted actions on a web application where they are authenticated, potentially resulting in unauthorized transactions.
Understanding these Joomla security vulnerabilities is crucial for developers aiming to secure their Joomla applications effectively.
Implement Security Measures: Best Practices for Joomla Protection
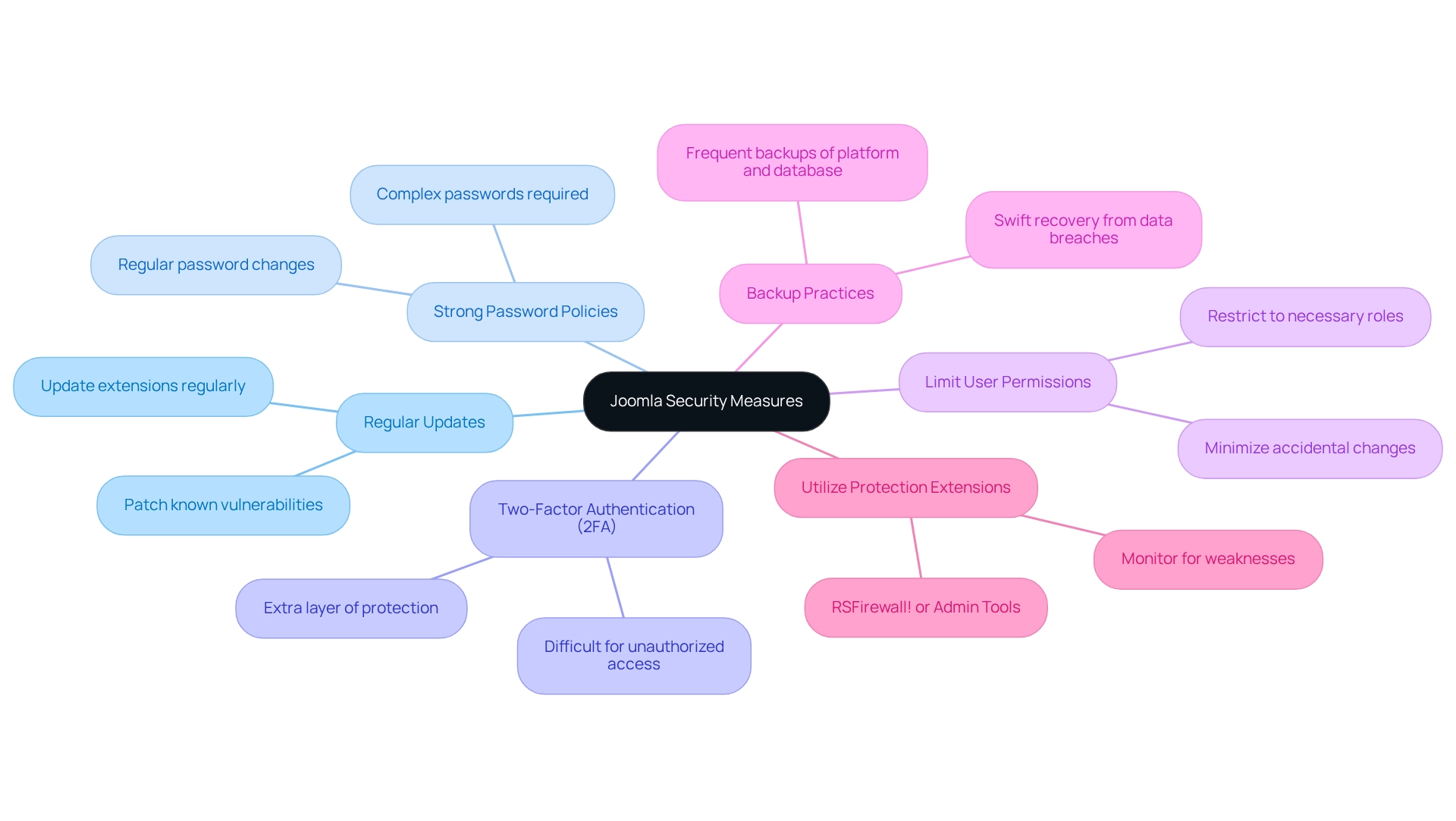
To safeguard your Joomla site effectively, it is essential to adopt several best practices.
- Regular Updates: Keeping Joomla and its extensions updated to the latest versions is crucial. This practice ensures that any known Joomla security vulnerabilities are patched promptly, thereby enhancing your site's security.
- Strong Password Policies: Implementing strong password requirements for all user accounts, including administrators, is vital. Passwords should be complex and changed regularly to prevent unauthorized access.
- Two-Factor Authentication (2FA): Activating 2FA adds an extra layer of protection. This measure makes it significantly more difficult for unauthorized individuals to gain access to your site.
- Limit User Permissions: Restricting user permissions to only what is necessary for their role is a prudent step. This approach minimizes the risk of accidental or malicious changes that could compromise your site’s integrity.
To protect against a Joomla security vulnerability, it is critical to frequently back up your Joomla platform and database. This ensures that you can recover swiftly in the event of a data breach, minimizing potential downtime.
- Utilize Protection Extensions: Considering the use of protection extensions, such as RSFirewall! or Admin Tools, can significantly enhance your site's security features. These tools help monitor for weaknesses and bolster your overall protection strategy.
Utilize Automated Tools: Enhancing Joomla Security Management
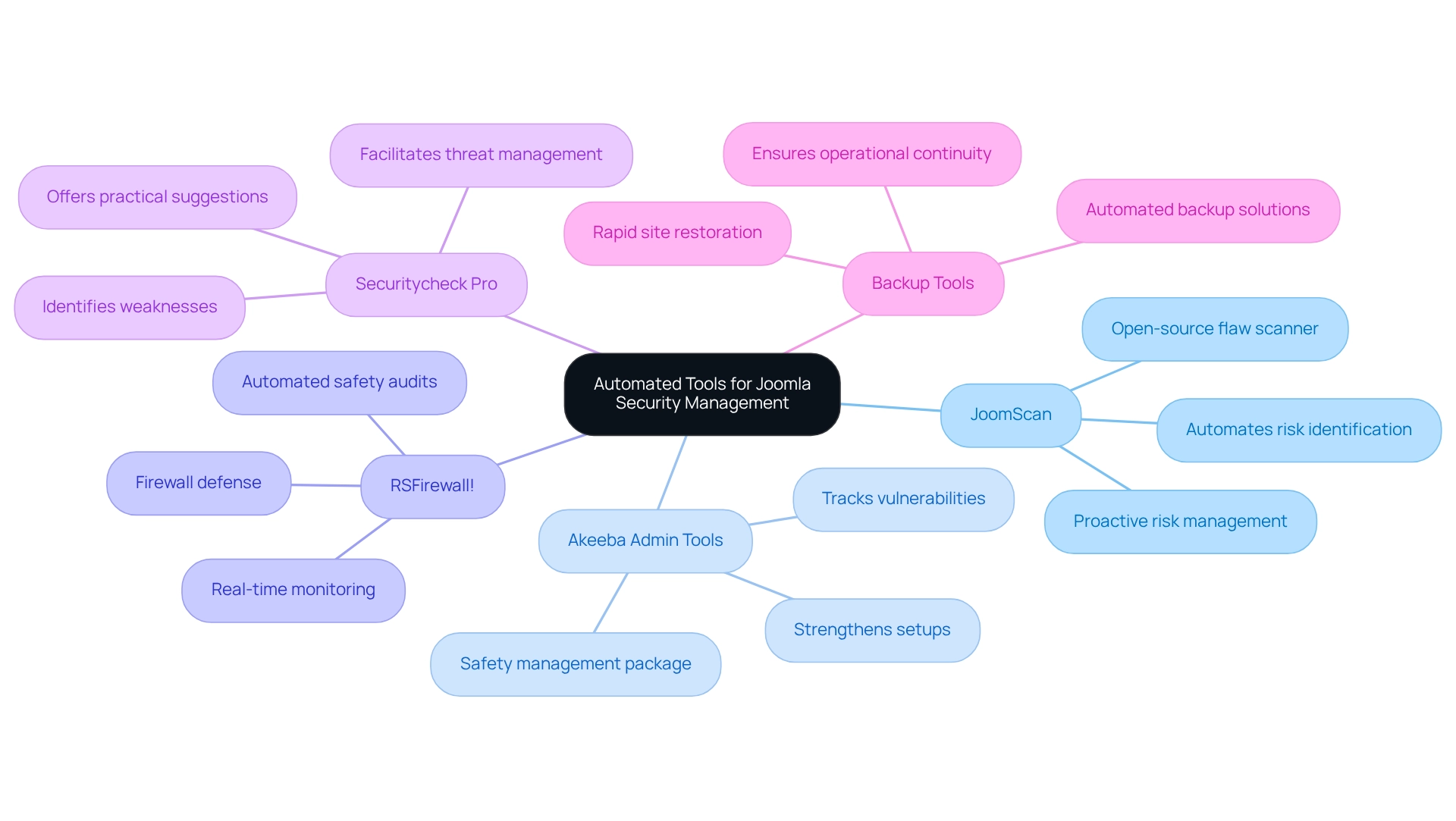
Automated tools significantly enhance platform management by providing essential features that sustain a safe environment. Consider the following top recommended tools:
- JoomScan: This open-source flaw scanner automates the identification of common risks within CMS installations, making it an essential tool for proactive risk management.
- Akeeba Admin Tools: A comprehensive package designed for safety management, Akeeba Admin Tools offers functions for strengthening setups and tracking vulnerabilities, ensuring continuous defense against threats.
- RSFirewall!: Renowned for its robust capabilities, RSFirewall! provides real-time monitoring, firewall defense, and automated safety audits, effectively safeguarding your platform from potential attacks.
- Securitycheck Pro: This tool identifies weaknesses and offers practical suggestions to enhance the protective stance of your web application, facilitating the management of potential threats.
- Backup Tools: Automated backup solutions, such as Akeeba Backup, are crucial for ensuring rapid restoration of your site in the event of an incident, offering peace of mind and operational continuity.
In 2023, the Mod Einsatz Stats Project reported a total of 52 vulnerabilities classified by type, including SQL Injection and XSS. This underscores the importance of utilizing these automated tools to effectively mitigate risks. Expert insights suggest that while the CMS is often perceived as more reliable than WordPress initially, as noted by the ScalaHosting team, the application of these tools is vital for maintaining that security over time. The current usage rates of JoomScan in installations reflect its increasing significance in the security landscape, demonstrating its effectiveness in enhancing security management. For a complete list of Joomla vulnerabilities, refer to the CVE details site.
Conclusion
In the ever-evolving landscape of digital security, safeguarding Joomla sites from vulnerabilities is paramount. Understanding common security threats such as Cross-Site Scripting (XSS), SQL Injection, and Authentication Bypass is critical, as these can lead to unauthorized access and significant damage. By recognizing these vulnerabilities, developers can prioritize security measures that protect sensitive data and maintain user trust.
Implementing best practices is essential for fortifying Joomla sites. Regular updates, strong password policies, and two-factor authentication serve as foundational steps in creating a robust defense against potential breaches. Furthermore, limiting user permissions and utilizing security extensions can enhance protection, ensuring that only authorized individuals have access to critical areas of the site.
Automated tools play a vital role in ongoing security management, providing essential resources for detecting vulnerabilities and managing risks. Tools like JoomScan, Akeeba Admin Tools, and RSFirewall! empower site administrators to maintain a secure environment through proactive monitoring and swift action against threats. As the Joomla platform continues to grow, leveraging these tools becomes indispensable for effective security management.
Ultimately, the responsibility for Joomla security lies with developers and site administrators. By staying informed about vulnerabilities, implementing best practices, and utilizing automated tools, the integrity and reliability of Joomla sites can be preserved. The commitment to a secure digital environment not only protects sensitive information but also fosters user confidence, ensuring that Joomla remains a trusted platform for website development.
Frequently Asked Questions
What are Joomla security vulnerabilities?
Joomla security vulnerabilities are weaknesses within the Joomla content management system that can lead to unauthorized access to sensitive data, website defacement, or total site takeover.
Why is it important for developers to address Joomla security vulnerabilities?
Addressing these vulnerabilities is crucial for developers to prioritize security, prevent data breaches, and protect the functionality, reputation, and user trust associated with their websites.
What are the potential consequences of a data breach in Joomla?
The fallout from a data breach can be catastrophic, affecting website functionality, damaging its reputation, and eroding user trust.
How is the security landscape for Joomla changing as we approach 2025?
The security landscape is becoming increasingly complex, particularly with the introduction of headless setups that create new challenges for API endpoints and data exchange.
What strategies are suggested for safeguarding Joomla web platforms?
Suggested strategies include implementing routine backups and maintaining vigilant oversight for unusual behavior.
What are the key elements of an incident response plan for Joomla?
Key elements include incident identification and communication strategies, which are critical for minimizing damage and downtime during a breach.
How can protection strategies align with business objectives?
Aligning protection strategies with broader business objectives is important for preserving brand reputation and maintaining customer confidence.
What measures can be taken to reduce the risk of brute-force attacks in Joomla?
Utilizing protective extensions to limit unsuccessful login attempts is recommended to reduce the risk of brute-force attacks.
Why is it essential for developers to prioritize addressing Joomla security vulnerabilities?
It is essential to ensure the integrity and reliability of their sites, making proactive measures necessary to safeguard against potential security threats.




