Introduction
API keys play a crucial role in enabling applications to access and utilize the functionalities of APIs, which are essential for seamless interactions and data sharing between software applications. These keys serve as exclusive passes that authenticate and authorize applications to tap into the valuable resources provided by APIs.
However, with the increasing importance of APIs comes the heightened risk of breaches and unauthorized access to sensitive data. Therefore, it is vital to manage and restrict API keys effectively to ensure the security and integrity of APIs and applications.
In this article, we will explore different types of API keys, the process of creating an API key, best practices for managing and restricting API keys, and the importance of API keys in applications. We will also discuss best practices for API key security and address common issues and troubleshooting tips when working with API keys. By following these guidelines, you can enhance the efficiency, security, and control of your APIs and applications.
What is an API Key
APIs, or Application Programming Interfaces, serve as the communicative bridge between disparate software applications, allowing them to share data and functionalities efficiently. They are the vital connectors that power the seamless interactions we've come to expect in our web-based activities.
Imagine an API as a bilingual translator, adeptly converting requests between two parties that speak different languages, thus enabling a harmonious exchange of services. They are indispensable in modern software development, so much so that Google has likened them to the 'crown jewel' of the field.
In the realm of web development, API keys are akin to exclusive passes that authenticate and authorize applications to access these valuable APIs. Without these keys, apps would be barred from the wealth of interactions and services APIs provide.
They are not just mere strings of characters but are pivotal to tracking usage and ensuring that only verified applications can tap into the API's resources. Given their importance, it's no surprise that APIs have cemented their role across various industries.
Financial institutions harness them for customer transactions, while healthcare providers use them to safeguard patient data. The API-first strategy underscores this significance, advocating for API quality, security, and performance as the foundation of application development. And as the digital landscape continues to evolve with big data and emerging technologies, the role of APIs only grows more critical, facilitating innovation and collaboration among developers and stakeholders alike. However, with the ascent of APIs comes the heightened risk of breaches, exposing sensitive data to unauthorized access. Such incidents underscore the necessity for robust API security measures, turning the spotlight on the careful management of API keys to prevent such vulnerabilities. As we increasingly rely on APIs, the responsibility to protect them becomes paramount, not just for developers but for the integrity of the digital services that have become integral to our daily lives.
Types of API Keys
APIs, or Application Programming Interfaces, are akin to translators that allow software programs to communicate with one another. They've become essential in modern software development, with Google even hailing them as the "crown jewels."
These interfaces come in various forms, each tailored to specific security and access requirements. Public API keys, for instance, are available for anyone to use, making them ideal for accessing open APIs that don't require user authentication.
On the other hand, private API keys offer a higher security level and are exclusively shared with authorized parties. They are crucial for APIs that demand authentication and restrict access.
For scenarios where access needs to be tailored, limited access API keys come into play, offering specified permissions to certain API parts. Lastly, secret API keys are reserved for the most sensitive interactions, such as financial or personal data transactions, ensuring the utmost security. The choice of API key hinges on the API's specific needs and the desired level of access control. As digital transformation forges ahead, APIs remain a vital part of technology infrastructure across various industries, from finance to healthcare, underpinning the integration of services and data with partners and customers.
How to Create an API Key
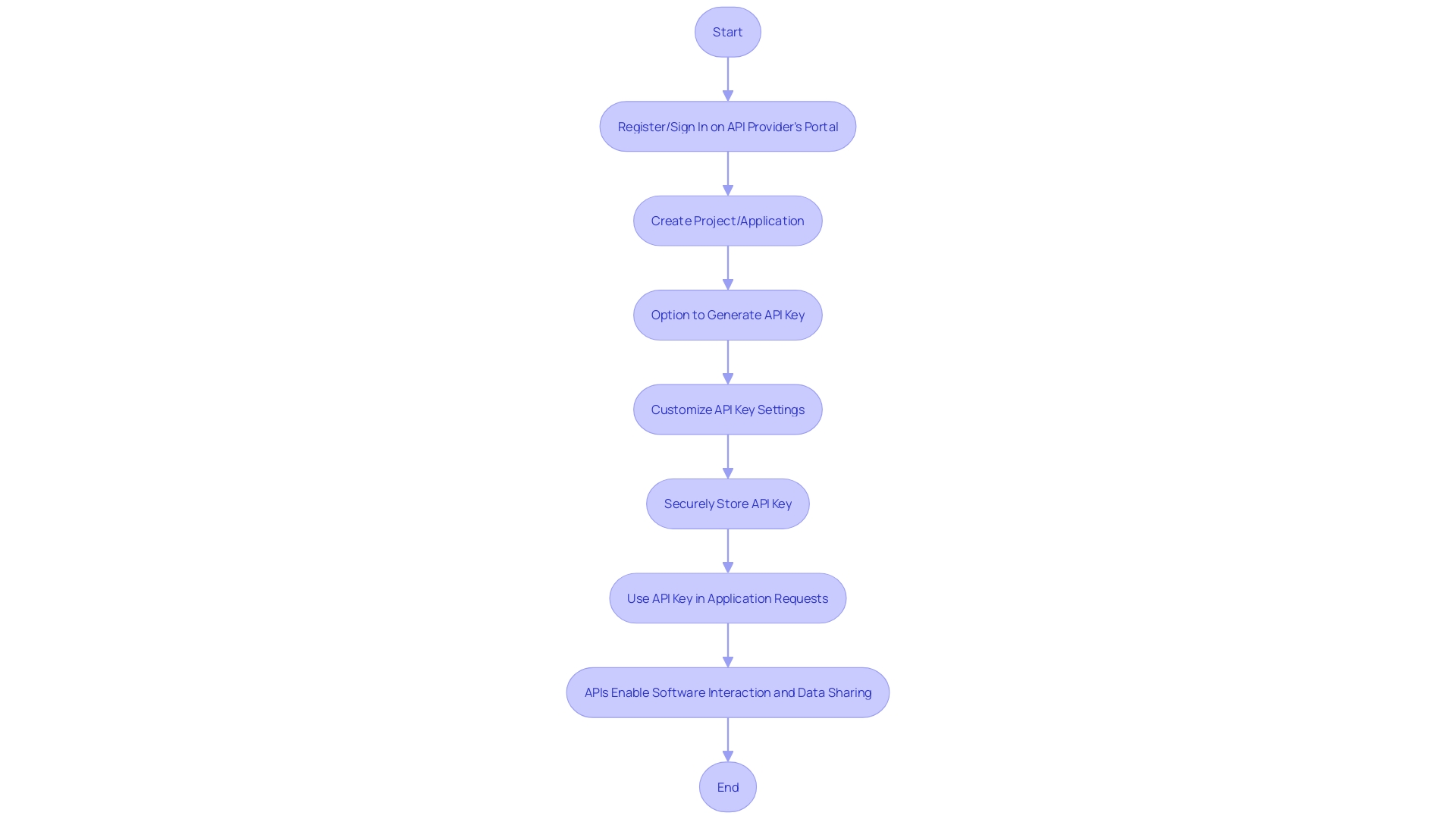
To integrate web services and applications, generating an API key is a fundamental step. Initially, you need to establish your presence on the API provider's portal by registering or signing in.
This gateway into the API's world is where the magic begins. Next, you're prompted to create a project or application, setting the stage for your future development endeavors.
It's within this realm that you'll find the option to generate an API key, a unique identifier that bridges the gap between your application and the API's functionalities. After this key is generated, you're not just left with a string of characters; you have the power to tailor its abilities through various settings, defining access permissions, and setting boundaries with restrictions or expiration dates.
This customization ensures that your API key fits snugly with your application's needs, like a glove. With the key configured, you'll want to store it securely, as it's not just a key but the keeper of your application's access to vast resources and capabilities. Once saved, the API key comes into play in your application by being included in API requests, as per the API documentation. It's a simple yet powerful tool in your arsenal, enabling your software to harness the capabilities of the web services you're tapping into. APIs, after all, are the translators that enable different software to converse, share data, and extend functionality, making them indispensable in the realm of modern software development.
Managing and Restricting API Keys
Proper management and restriction of API keys are essential to ensure the security and integrity of your API and application. Here are some best practices for managing and restricting API keys:1.
Store API Keys Securely: API keys should be stored securely, preferably encrypted, to prevent unauthorized access. Avoid hardcoding API keys directly into your application's code.
- Use Access Control: Implement access control mechanisms to restrict API key usage to authorized applications or users only.
This can be achieved through authentication and authorization techniques such as OAuth or API key whitelisting. 3.
Rotate API Keys Regularly: Regularly rotate API keys to mitigate the risk of compromise. This involves generating new API keys and updating them in your application, while invalidating the old keys.
- Monitor API Key Usage: Monitor and track API key usage to identify any unusual or suspicious activity. This can help detect and prevent unauthorized access or misuse of API keys. 5. Implement Rate Limiting: Set rate limits on API key usage to prevent abuse or excessive requests. This helps ensure fair usage and protects the API from being overwhelmed. By following these best practices, you can effectively manage and restrict API keys, enhancing the security and control of your APIs.
Using API Keys in Applications
API keys serve as secure passports, authorizing applications to interact with APIs and enabling a myriad of functionalities. They are essential in authenticating requests, where developers embed the API key within the request parameters or headers, thus providing a gateway for applications to communicate with APIs.
This authentication is pivotal in accessing restricted resources, ensuring that only authorized entities can tap into specific functionalities of an API. Moreover, API keys are instrumental in tracking and regulating the usage of APIs.
They offer API provides valuable insights into usage patterns and enforce any necessary constraints, preserving the integrity and sustainability of the services provided. Furthermore, in the realm of third-party integrations, API keys are the linchpins that facilitate seamless data exchange and interoperability between disparate systems, enhancing the functionality and value of software ecosystems.
In the context of modern software development, APIs are likened to the crown jewels, as quoted by Google. They function as translators between software programs, allowing them to 'speak' to one another and share services. Embracing an API-first strategy, where APIs are the foundational elements in crafting applications, underscores their importance. This approach ensures that APIs are treated with the attention they deserve, focusing on their quality, security, and performance from the outset. As big data unveils vast amounts of information and new technologies surface, APIs' role becomes increasingly significant, opening doors to innovation and collaboration between developers and stakeholders.
Best Practices for API Key Security
Protecting API keys is paramount for safeguarding your API's integrity and the sensitive data it processes. To enhance API key security, it's essential to adhere to established best practices.
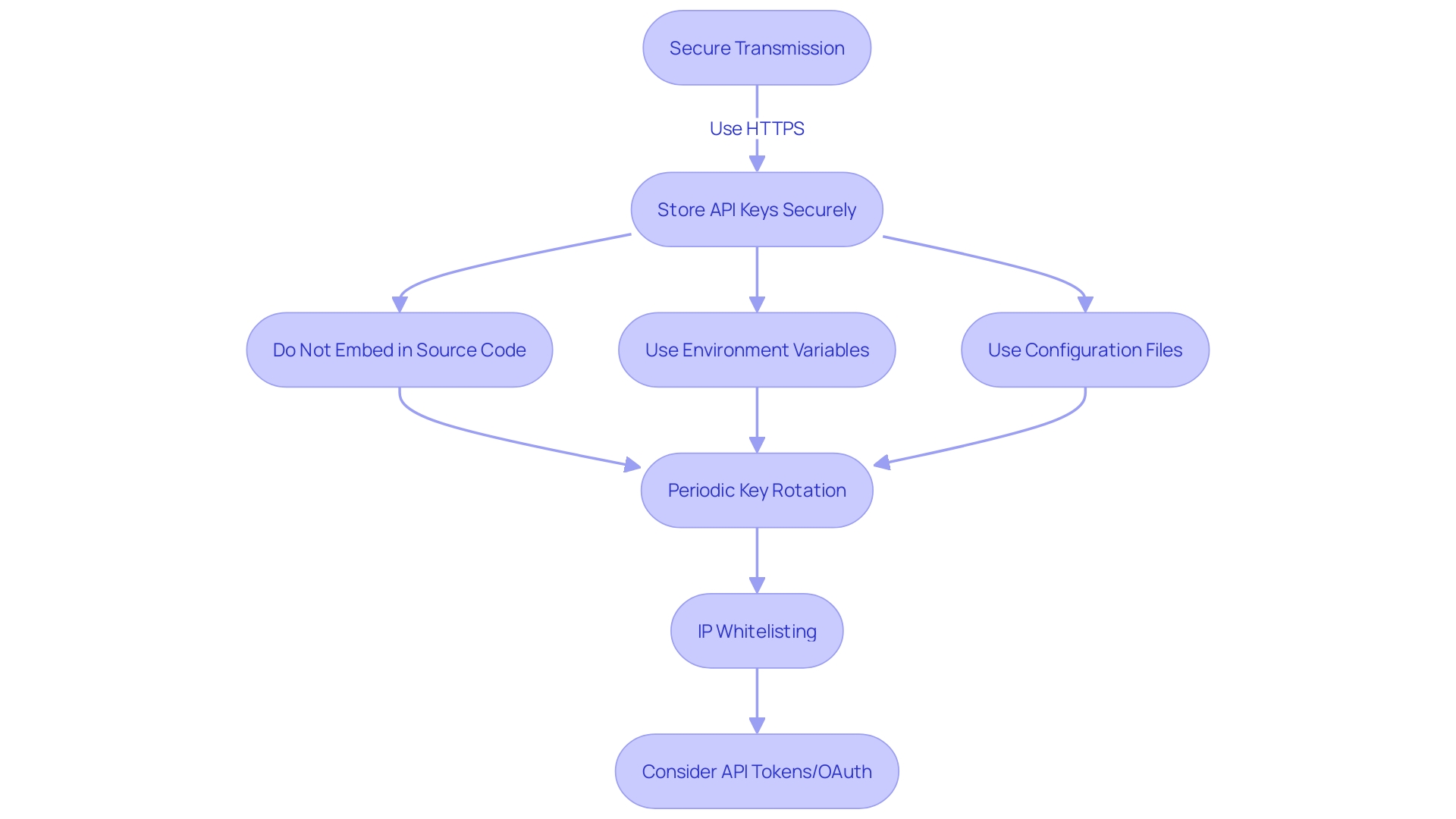
Secure transmission is the first line of defense; therefore, utilize HTTPS (HTTP Secure) to shield API keys during transit, preventing potential eavesdropping or interception by unauthorized parties. To minimize the risk of key exposure, refrain from embedding API keys directly in your application's source code.
Employ environment variables or configuration files as secure repositories for storing and retrieving these keys. Periodic rotation of API keys is a critical strategy for mitigating the risk of key compromise.
This proactive approach entails generating fresh keys, integrating them into your application, and deactivating the previous ones. Augmenting security measures, IP whitelisting restricts API key usage to designated IP addresses or ranges, thereby thwarting access attempts from unverified or dubious sources. For a more robust authentication and authorization framework, consider transitioning to API tokens or OAuth. These alternatives offer refined access control and simplify the revocation process, ensuring more stringent security. Implementing these best practices is a significant step toward reinforcing your API keys' security and shielding your APIs against emerging threats.
Common Issues and Troubleshooting
When integrating API keys into your application, it's crucial to navigate common challenges with precision. Authentication errors often arise when an API key is not correctly authenticated.
To resolve this, meticulously check your API key's configuration and confirm its correct inclusion in API requests. Exceeding the rate limits set by an API provider can lead to errors.
It's imperative to examine the API's documentation to comprehend these limits and modify your application usage to avoid hitting these ceilings. API keys are sometimes time-bound and may expire, necessitating the generation of a new key for continued service.
If access restrictions or errors occur, ensure your API key is endowed with the proper permissions for the resources you're trying to access. Moreover, API providers may revoke keys due to security issues or policy breaches.
In such an event, adhere to the provider's guidelines to restore access or obtain a new key. APIs, serving as conduits between distinct software systems, are governed by a set of rules for data requests and exchanges. They facilitate a myriad of actions, from fetching data from external sources to interfacing with various online services. Selecting the appropriate API is a foundational step and should align with your project's requirements. Whether it's RESTful APIs for straightforward data operations or other types, the choice should be informed by the API's scope and capabilities. For any API key-related difficulties, consult the API provider's extensive documentation or seek out their support team.
Conclusion
In conclusion, API keys are crucial for enabling applications to access and utilize APIs securely. By implementing best practices such as secure storage, access control, key rotation, monitoring, and rate limiting, you can enhance the efficiency and security of your APIs and applications.
APIs play a vital role in modern software development by facilitating seamless data exchange and collaboration. They enable restricted resource access, track usage patterns, and foster innovation among developers.
To protect sensitive data, follow API key security best practices like using HTTPS for secure transmission, avoiding embedding keys in source code, rotating keys regularly, implementing IP whitelisting, and considering alternative authentication methods like API tokens or OAuth. When troubleshooting issues with API keys, ensure correct authentication configuration, stay within rate limits, address key expiration or revocation promptly, and select the appropriate API for your project's needs. In summary, effective management of API keys is essential for maintaining the integrity and security of APIs and applications. By following best practices and addressing common issues proactively, you can maximize efficiency while safeguarding sensitive data.
Take control of your API security with Kodezi CLI!
Frequently Asked Questions
What is an API?
An API, or Application Programming Interface, is like a bridge that allows different software applications to communicate with each other, sharing data and functionalities efficiently. It acts as a translator between two parties that might not speak the same language, enabling them to work together harmoniously.
What is an API Key?
An API key is a unique identifier used to authenticate and authorize an application to access an API. It's like an exclusive pass that grants your application the ability to use the API's services.
Why are API keys important?
API keys are important because they help track and control how the API is used, ensure only verified applications have access, and protect the data and functionality being accessed from unauthorized use.
What are the different types of API keys?
There are several types of API keys: Public API keys (for open APIs without user authentication), Private API keys (for higher security and authorized parties), Limited access API keys (for specified permissions), and Secret API keys (for the most sensitive transactions).
How do you create an API key?
To create an API key, you typically need to: 1. Register or sign in on the API provider's portal. 2. Create a project or application within this portal. 3. Generate the API key from the provided options. 4. Customize the API key settings to fit your needs. 5. Securely store the API key for use in your application.
How should you manage and restrict API keys?
To manage and restrict API keys effectively, follow these best practices: Store them securely and encrypted, use access control mechanisms, rotate them regularly, monitor their usage, and implement rate limiting.
How are API keys used in applications?
API keys are used to authenticate requests to an API. They are included in the parameters or headers of an API request, allowing the application to access restricted resources and functionalities of an API.
What are some best practices for API key security?
Some best practices for API key security include: Use HTTPS to protect keys during transmission, avoid embedding API keys in your source code, store keys in environment variables or configuration files, rotate API keys periodically, use IP whitelisting and consider using API tokens or OAuth for better security.
What common issues might you encounter with API keys?
Common issues with API keys include: Authentication errors if the key is not correctly configured or included in requests, rate limit errors if your application exceeds the number of allowed requests, expiry of keys leading to revoked access, and access restrictions if the key doesn't have the right permissions.
How can you troubleshoot API key issues?
To troubleshoot API key issues: Check the API key's configuration and ensure it's included correctly in requests, review the API's documentation to understand rate limits and adjust your application accordingly, generate a new key if the current one has expired, ensure your API key has the proper permissions for the resources you're accessing, and follow the API provider's guidelines to restore access or obtain a new key if it has been revoked.




