Introduction
Are you looking to maximize efficiency and productivity in your workflow? Look no further than Kodezi. With its cutting-edge features and intuitive interface, Kodezi is designed to streamline your coding process and deliver results like never before.
Whether you're a seasoned developer or just starting out, Kodezi's powerful tools and comprehensive resources will equip you with everything you need to succeed. Say goodbye to wasted time and hello to seamless development with Kodezi.
What is an API Key?
An API key serves as a compact, unique identifier critical for securing an API, much like a nuanced digital keycard for software interactions. To illustrate, the TotalEnergies Digital Factory (TDF) and its sprawling team of developers underscores its reliance on API keys, unanimous in their view that such security measures are indispensable for fostering effortless collaboration. These keys are the gateway to an array of digital solutions, streamlining TotalEnergies' expansive operations across practically 130 countries.
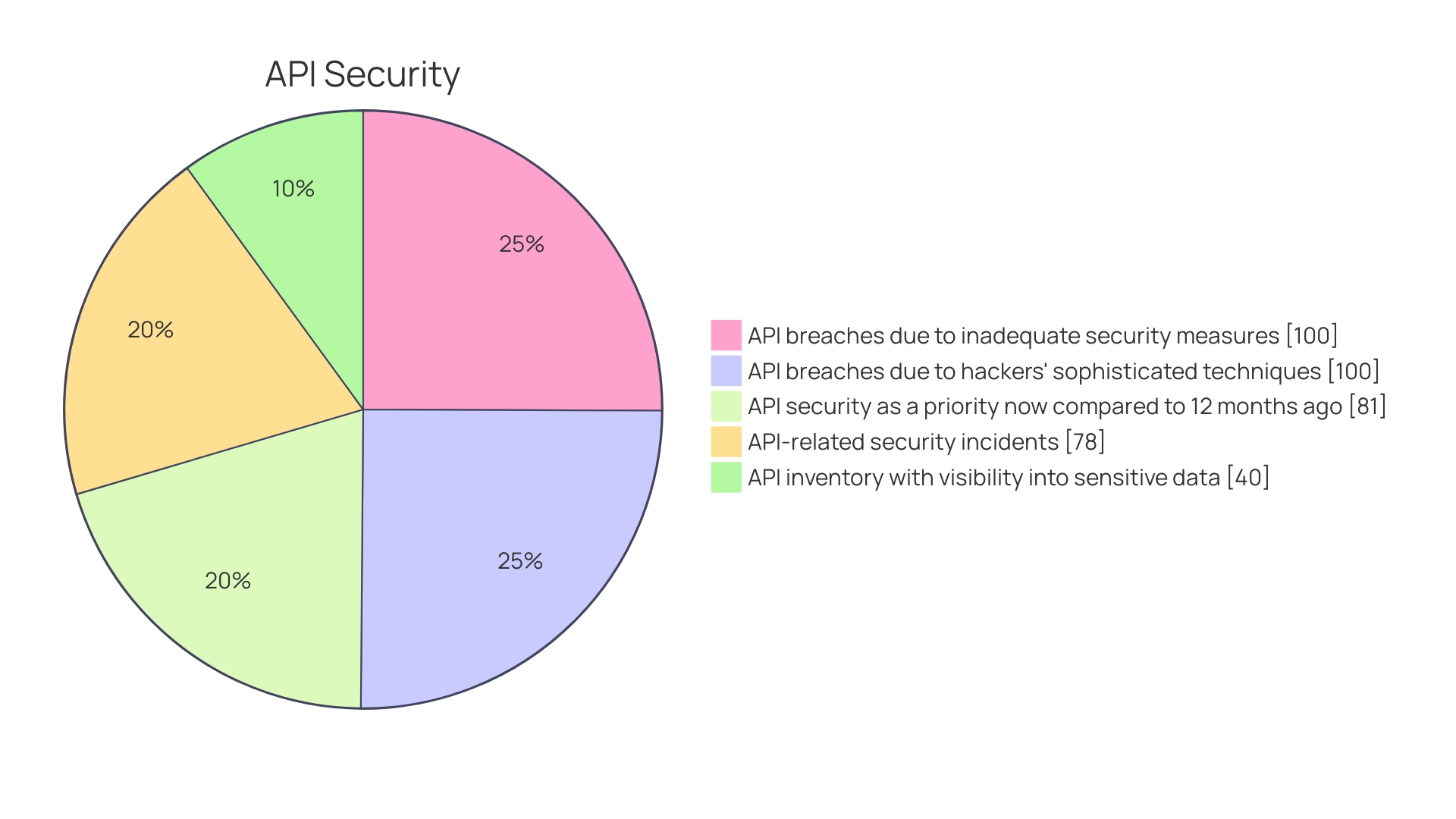
At the heart of this ecosystem lies the API gateway, integrated with LDAP Single Sign-On, exemplifying its significant role in bolstering the security and management of enterprise information systems. These gateways provide a fortified entry point, maintaining robust security standards amidst the increasing prevalence of API breaches, a pressing concern detailed in numerous reports. Highlighting this urgency, a staggering 78% of cybersecurity teams have encountered API-targeted cyber attacks within the past year, prompting a more focused attention on API security.
Through judicious management of API keys, TDF ensures the safe handling of sensitive data against unauthorized access—a practice echoed across the industry as cybersecurity professionals aim to shield essential information from vulnerabilities. This digital diligence is about protecting what's beyond the API: the people and their well-being, in line with the values espoused by TotalEnergies.
Why Do You Need an API Key?
The importance and function of API keys are multifaceted, integrating critical elements such as authentication, rate-limiting, usage tracking, and security into a system designed to enhance control and protect valuable data. Authentication via API keys acts as a gateway, ensuring that only validated users have the ability to interact with the API, thus upholding system integrity.
API keys also play an instrumental role in rate-limiting, a measure necessary to maintain the API's stability and availability by restricting the quantity of requests a user or service can make in a given timeframe. This serves to ward off potential misuse and evenly distributes the service capacity.
Moreover, usage tracking provided by API keys offers visibility for providers to effectively supervise how the API is utilized, shedding light on usage patterns, optimizing resource management, and facilitating the early detection of irregularities or anomalous behavior.
Lastly, API keys add a robust layer to security defenses, shielding actual API credentials from exposure and mitigating the risk of unauthorized access. This has become vital in an era where digital platforms are ubiquitous, emphasized by the online collaboration tool Trello's data leak example, underscoring the consequences of exposed sensitive information.
As the digital landscape evolves, the necessity to secure APIs against emerging threats is paramount. Adoption of best practices and learning from real-world scenarios—like the misuse of a unified search function due to lacking rate limiting—can guide the development and implementation of more secure APIs. Protecting data integrity is not only urgent but necessary, as highlighted by recent statistics indicating a high volume of API-related security incidents within the last year.
As evidenced by the evolving nature of cyber threats, securing APIs continues to be a critical priority for safeguarding sensitive information and maintaining trust in digital ecosystems.
How to Obtain an API Key
Accessing the world's news has never been easier thanks to the free news API key offered by Newsdata.io. It provides a gateway to a treasure trove of articles from across the globe, boasting coverage of 154 countries and 81 languages. With more than 100,000,000 news articles available, dated from 2018 onwards, harvested from over 50,000 sources, the platform serves as an indispensable resource for anyone interested in real-time news data.
If you're eager to delve into this vast news repository, here's how to embark on your journey:
- Sign Up for an Account: Begin by registering for a free trial account on Newsdata.io to explore their services. Whether you're a journalist, researcher, or developer, signing up is your first step towards accessing comprehensive news data.
- Generate Your API Key: Once registered, tap on the “Get API Key” option on the website. This key is your pass to fetch news from the platform, so keep it confidential.
- Customize Access: You'll have the opportunity to tailor your API key's access permissions, harmonizing it with your specific needs. This ensures that you get exactly what you need from the service, without unnecessary breadth that can complicate usage.
- Secure Your Key: Given the critical incidents of API breaches reported — such as the unauthorized request to increase Simple Email Service (SES) sending limits in a high-profile AWS incident — safeguarding your API key is paramount. To prevent misuse, refrain from embedding the key in your codebase. Instead, use environment variables or secure storage solutions, ensuring that no unauthorized entity gains access to this sensitive information.
By following this structured approach, you can seamlessly integrate a constant stream of global news into your applications, whilst maintaining stringent security protocols.
How to Use an API Key
Integrating an API into your applications entails several cornerstone steps, each critical for a successful and secure interaction. Beginning with the essential inclusion of the API key in your code, the key performs as an access pass, enabling you to exchange information with the API. Insertion of the key can assume various forms such as headers, query parameters, or within the request body.
Following this, you transition to crafting API requests using your chosen programming language. Responsibilities at this stage include detailing endpoints and specifying parameters necessary for the information you seek.
Subsequent to dispatching the request, your application awaits and then processes the API's response. Parsing the incoming data is crucial, as is the management of any potential errors or exceptions. APIs, serving as the backbone for web and mobile apps, are gateways to the digital realm where speed, flexibility, and scalability reign.
However, as much as APIs expedite the development process and enhance the interplay between various digital services, they also attract security risks due to their internet exposure. In fact, research has underscored the paramount importance of APIs, with a staggering 93% of organizations recognizing them as indispensable. Still, with acknowledgement also comes responsibility; 86% of those surveyed recognized the siloed nature of operations without APIs.
And it's this inherent connectivity that necessitates robust security protocols and vigilant monitoring.
The narrative of unified search aptly illustrates the double-edged nature of API ease of use. Designed for quick and straightforward searches, it serves as a testament to performance and user convenience. Yet, the simplicity that endears it to users also drew misuse, necessitating the implementation of rate limits to counteract abuse.
Such is the paradox of API design: the quest for user-friendliness must be balanced with the imperatives of security.
Roblox's venture into real-time language moderation via AI technologies exemplifies the innovative paths companies are threading to tackle challenges in the dynamic user-generated content landscape. Similarly, Akamai's amalgamation of Noname and Akamai API securities demonstrates a swift response to the burgeoning API landscape, ensuring robust protections in an age where digital interactions are fundamentally API-driven.
The salience of these examples underscores that, whether for search functionality on a homepage or the immersive 3D experiences on platforms like Roblox, meticulous API design paired with sound security measures is a topic of paramount discourse among development communities. It's a conversation where views on the API revolution's impact on innovation skew to the affirmative, punctuated by the surging growth trajectory and the synergy between APIs and microservices leading to an ensemble of benefits such as heightened customer satisfaction and productivity leaps.
Best Practices for API Key Safety
Securing your API keys is paramount in safeguarding your applications from unauthorized access and potential threats. By adhering to strategic practices, you can significantly enhance API security. Firstly, access to API keys should be stringently limited, with entry only available to personnel or applications that have an explicit need.
Highlighting the potential dangers, recent security breach studies indicate that 60% of surveyed organizations experienced at least one incident in the past two years.
Next, consider a regular rotation schedule for API keys, particularly after any suspicion of compromise. This policy aligns with lessons learned from an evasion of a catastrophic situation at a repository with over half a million AI models, where swift action was necessary after a disclosure.
Moreover, it's crucial to encrypt sensitive API keys and to use secure transmission methods such as HTTPS. The Traceable and Ponemon Institute report underscores this need, pointing to the alarming rate of breaches resulting from inadequate API security measures.
Hardcoding of API keys poses a high risk and should be avoided entirely. Implement secure storage solutions or environment variables instead to manage your keys. As the digital infrastructure depends heavily on APIs, understanding their structure, security attributes, and associating them with corporate policies is essential for a strong security posture, as emphasized by experts who advise defining what 'good' API standards mean to a business.
Common Issues with API Keys
API keys serve as a passport for accessing various web services, but handling them carelessly can lead to severe complications, from service disruptions to security vulnerabilities. For example, if an API key is inadvertently leaked, as evidenced by OpenWeatherMap's process requiring verification upon receiving your key, unauthorized users could exploit sensitive data. The consequences can range from identity theft to financial fraud, underscoring the necessity for robust security measures.
Proper management of API keys is crucial, especially as the number of keys increases with project complexity. Tools and strategies must be in place for organizing and monitoring these keys to prevent them from becoming unmanageable or falling into the wrong hands. The case study of KAYAK illustrates how the integration of Credential Manager API and RxJava on Android improves security.
A shift away from passwords, which can be easily compromised, towards more secure authentication methods is vital, as underscored by KAYAK's Chief Scientist, Matthias Keller.
Moreover, API keys may be revoked without warning, hence the importance of having backup plans. Our exploration of the Pied Piper Todo Management System (PPTMS), a hypothetical todo service, highlights the necessity of proper permissions and practices for changing or rotating API keys when needed. The responses to an incident of leaked API keys illustrate why simply deleting the exposed key or editing the Git history isn't enough to rectify the situation—prompt action is required.
Lastly, rate limiting is a practical approach to managing the flow of requests to your API, ensuring that your service remains available and the user experience isn't compromised. In the early days of APIs, this wasn't a typical consideration, but now it's paramount for maintaining functionality without overwhelming your service, as echoed in discussions around the evolution of front and backend development.
The statistics from a comprehensive cybersecurity report suggest that 78% of security teams have encountered an API-related incident in the past year. With only 40% of those teams able to monitor sensitive data exposure, it's clear that vigilance and proactive management are more important than ever. The reported 18,000 exposed API secrets highlight the extent of the security risks and the critical need for robust key management practices.
Conclusion
In conclusion, API keys are crucial for secure and controlled interactions with APIs. They serve as a gateway, ensuring system integrity and protecting valuable data. API keys enable rate-limiting, usage tracking, and add a robust layer of security.
To obtain an API key, sign up for an account, generate a unique key with customized permissions, and securely store it. This allows seamless integration of global news or any desired API data into applications with stringent security protocols.
When using an API key, include it in the code, craft API requests, and process the API's response. Robust security protocols and vigilant monitoring are necessary to mitigate risks associated with APIs.
Best practices for API key safety include limiting access, regularly rotating keys, encrypting them, and using secure transmission methods. Avoid hardcoding keys and understand API structure and security attributes.
Common issues with API keys highlight the importance of proper management and organization. Secure authentication methods, backup plans for revoked keys, and rate limiting help maintain service availability and protect sensitive data.
In summary, API keys are essential in maximizing security and efficiency when using APIs. By following best practices and implementing robust security measures, applications can benefit from the power and convenience of APIs while safeguarding valuable data and maintaining trust in digital ecosystems.
Get started with Kodezi and secure your API interactions today!




