Introduction
API keys serve as essential credentials, similar to a password, authorizing and authenticating access requests to an API. This protective mechanism is crucial, as APIs are at the heart of modern web applications and platforms, where seamless communication between software is a must for operational efficiency.
However, as reliance on APIs has surged, so too has the frequency of security breaches. Unauthorized access to APIs exposes sensitive information, potentially leading to identity theft, financial fraud, and severe repercussions for businesses.
Hence, the fortification of API keys against compromise is paramount in safeguarding digital interactions and maintaining data integrity. In this article, we will explore the importance of API keys, how they work, the different types of API keys, their benefits, common issues, best practices for API key safety, and how to obtain and manage API keys. Understanding the significance of API keys and implementing robust security measures is crucial for protecting applications and preserving the integrity of digital systems.
What is an API Key
API keys serve as essential credentials, similar to a password, authorizing and authenticating access requests to an API. This protective mechanism is crucial, as APIs are at the heart of modern web applications and platforms, where seamless communication between software is a must for operational efficiency.
However, as reliance on APIs has surged, so too has the frequency of security breaches. Unauthorized access to APIs exposes sensitive information, potentially leading to identity theft, financial fraud, and severe repercussions for businesses. Hence, the fortification of API keys against compromise is paramount in safeguarding digital interactions and maintaining data integrity.
How API Keys Work
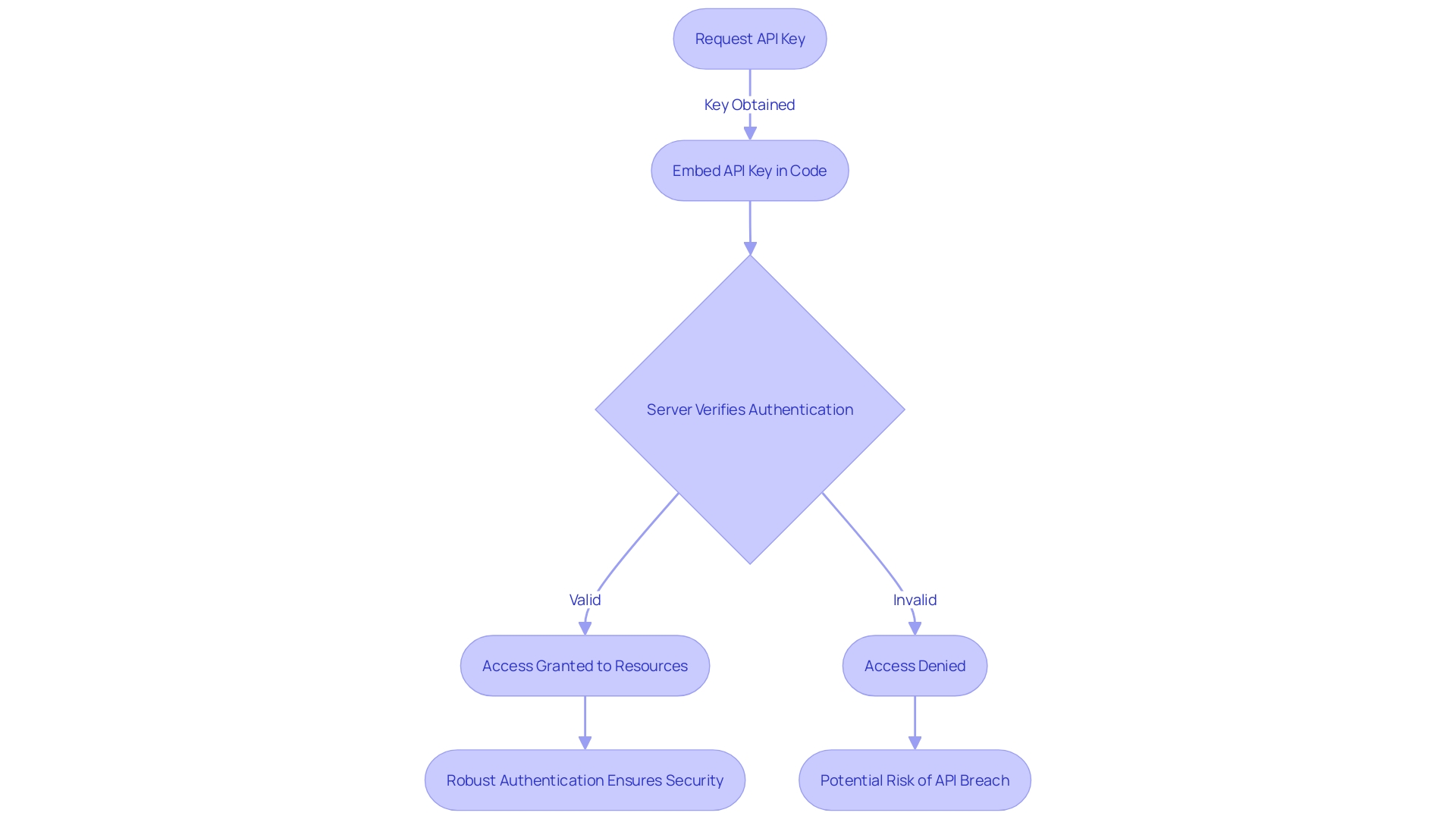
Acquiring and incorporating an API key into web applications has become an essential part of modern software development given the boom in web applications and digital platforms interacting through APIs. When developers obtain these keys, they embed them into the code, which could be within headers, query strings, or the request body, to establish their identity to the API services.
It's like presenting a digital passport that unlocks the functionalities offered by the API. Subsequently, the API server inspects this 'passport'—the API key—to authenticate the request.
Like a meticulous customs officer, the server verifies the key's legitimacy before allowing access, ensuring that only those holding the equivalent of a 'valid ticket' can leverage the API's resources. Yet, this process is not impervious to threats—as the uptick in API breaches painfully illustrates, underscoring the gravity of safeguarding API keys.
These infringements not only undermine the integrity of application ecosystems but can also result in the dissemination of confidential information. APIs sometimes act as gateways to highly sensitive data, which, if compromised, can precipitate identity theft and fraud.
Given these stakes, adopting robust authentication measures—akin to the thorough scrutiny of a passport—is imperative for digital systems. Consider digital certificates—akin to ID cards in the digital realm—as an elevated form of authentication. They bear a digital signature, the technical watermark which attests to their validity, just as physical currencies feature distinct markings to signal their genuineness. Along with this, they hold a public key that corresponds to an exclusive private key, fortifying the notion of identity in cyberspace. Despite their security benefits, digital certificates are seldom leveraged for verifying individuals but are rather utilized in authenticating servers, software, and other digital entities.
Types of API Keys
API keys are essential for the secure and structured interaction between software applications—think of them as unique identifiers that enable applications to converse fluently. As we delve into the diverse types of API keys, it becomes evident that each serves a unique function in the realm of software development.
Public API keys, akin to a business card, are openly circulated for accessing broadly available APIs that don't ask for personal credentials. Conversely, private API keys are akin to the keys to a private vault; they must be kept under wraps as they grant entry to APIs that require precise identification and permissions.
Lastly, limited access API keys are the specialized tools in a developer's toolkit, providing tailored access to certain segments within an API—undeniably beneficial when interfacing with external third-party services. With the tech ecosystem increasingly interlinked, the significance of API management in protecting sensitive data against breaches has never been more critical. Experts urge businesses to fathom the expansive role APIs play and the vital necessity of shielding them to preserve integrity and customer trust.
Benefits of Using API Keys
API keys serve as a fundamental tier of web application security, with rampant digitalization elevating their role to a critical aspect of software development. Firstly, they authenticate users, providing a security layer that ensures only eligible entrants can interact with the desired API. This gated access is pivotal in safeguarding sensitive information, as unauthorized entry to APIs may cascade into breaches—opening the floodgates to sensitive data spills.
Further, API keys empower developers with robust access management tools; they meticulously sculpt user privileges, delineating clear boundaries within the API landscape. This control is vital in an era where selectively reinforcing data vaults is just as important as keeping the information flow agile. Moreover, API keys adeptly administer usage by implementing effective rate limits, acting as gatekeepers to avert system overloads and misuse—maintaining API integrity and resource allocation.
They aren't merely data sentinels; API keys also excel in auditing. They log and scrutinize API interactions, offering invaluable analytics that guide insightful decisions and optimize overall performance. Embedding themselves deeply within the monitoring frameworks, they illuminate patterns of API consumption.
Finally, API keys are the linchpin in assimilating third-party services, creating an interconnected ecosystem. Like a master key unlocking myriad developmental possibilities, API keys facilitate the seamless melding of external functionalities into core platforms. Highly revered in the tech community, APIs, lauded by Google as the 'crown jewel of software development', empower innovators with the versatility to transcend traditional software limitations, ultimately magnifying the canvas for digital progression.
Common Issues with API Keys
Amid the increased integration of web applications, application programming interfaces, or APIs, have become instrumental in software development. They enable different applications to interact seamlessly, emphasizing their critical function in the digital realm. However, their prevalence has also elevated the risk of API breaches, prompting a pressing need for developers to bolster security measures.
When API keys are inadvertently exposed—be it via source code, misconfiguration, or network transmissions—it opens the door for unauthorized entities to infiltrate, potentially unleashing a cascade of unwelcome actions ranging from data theft to full-blown system compromise. Neglecting regular API key rotation is another vulnerability hotspot. Persistent keys become more susceptible to exploitation, underlining why periodic key updates are essential for maintaining a fortified security stance.
Adequate access control is equally essential; without it, the risk of unauthorized breaches creeps higher. Furthermore, the absence of vigilant monitoring of API usage and access patterns makes it significantly more challenging to identify and intercede against emerging security hazards. In the face of API breaches having far-reaching impacts—including exposure of highly sensitive personal and financial data—prioritizing a robust defense protocol for API keys is no longer just recommended, it's a critical component of modern cybersecurity practices.
Best Practices for API Key Safety
Implementing robust security measures to manage API keys is critical in safeguarding web applications against data exposure and breaches. Balance is key, starting with the secure storage of API keys. Rather than embedded in code, keys should be housed in environment variables or secrets management systems that encrypt sensitive information.
Taking it further, access to API keys must be on a need-to-know basis, with a strict permission system in place. Openly sharing keys or allowing them to fall into unauthorized hands is not an option. To further enhance security, rotating API keys can drastically reduce the risk associated with compromised keys.
An automated rotation system ensures that old keys are replaced with new ones at regular intervals without manual intervention, thus maintaining security hygiene. Alongside rotation, transmission of API keys across networks should employ encryption standards such as HTTPS – upholding key confidentiality and integrity. Vigilance through monitoring and logging is paramount.
These systems track API key usage, facilitating the prompt detection of any anomalies, and enable a swift response to any indication of a security incident. Lastly, in case of a breach or when keys are obsolete, a well-defined revocation process is indispensable to prevent misuse, ensuring that compromised or obsolete keys no longer grant access. This multifaceted strategy collectively fortifies the applications against the devastating consequences of API breaches, protecting businesses and their sensitive data from unauthorized access and exploitation.
How to Get an API Key
In the realm of software communication, obtaining access to another system's data hinges on the pivotal step of acquiring an API key. This process commences with a careful selection of an API that dovetails with your project's requirements, from actionable weather forecasts to dynamic financial insights.
Once you've pinpointed the desired API, often necessitating a touchpoint with its developer portal, the subsequent stage involves formalizing your intent through registration, granting you the credentials to partake in a secure data exchange. Proceeding, you will need to delve into the provider's documentation, a treasure trove that will guide you through the creation of your exclusive API key—a digital passport, so to say, that will unlock the troves of data that await you.
With this key in hand, vigilance is paramount; it must be ensconced in a digital vault, sheathed by the best security practices to prevent unauthorized access. The final act of this protocol involves weaving the API key into your application's fabric, ensuring it accompanies each outbound API request. This precise inclusion paves the way for a seamless conversation with outside systems, enabling your software to seek and receive data with the assurance of technical harmony and security.
Managing Access to the API
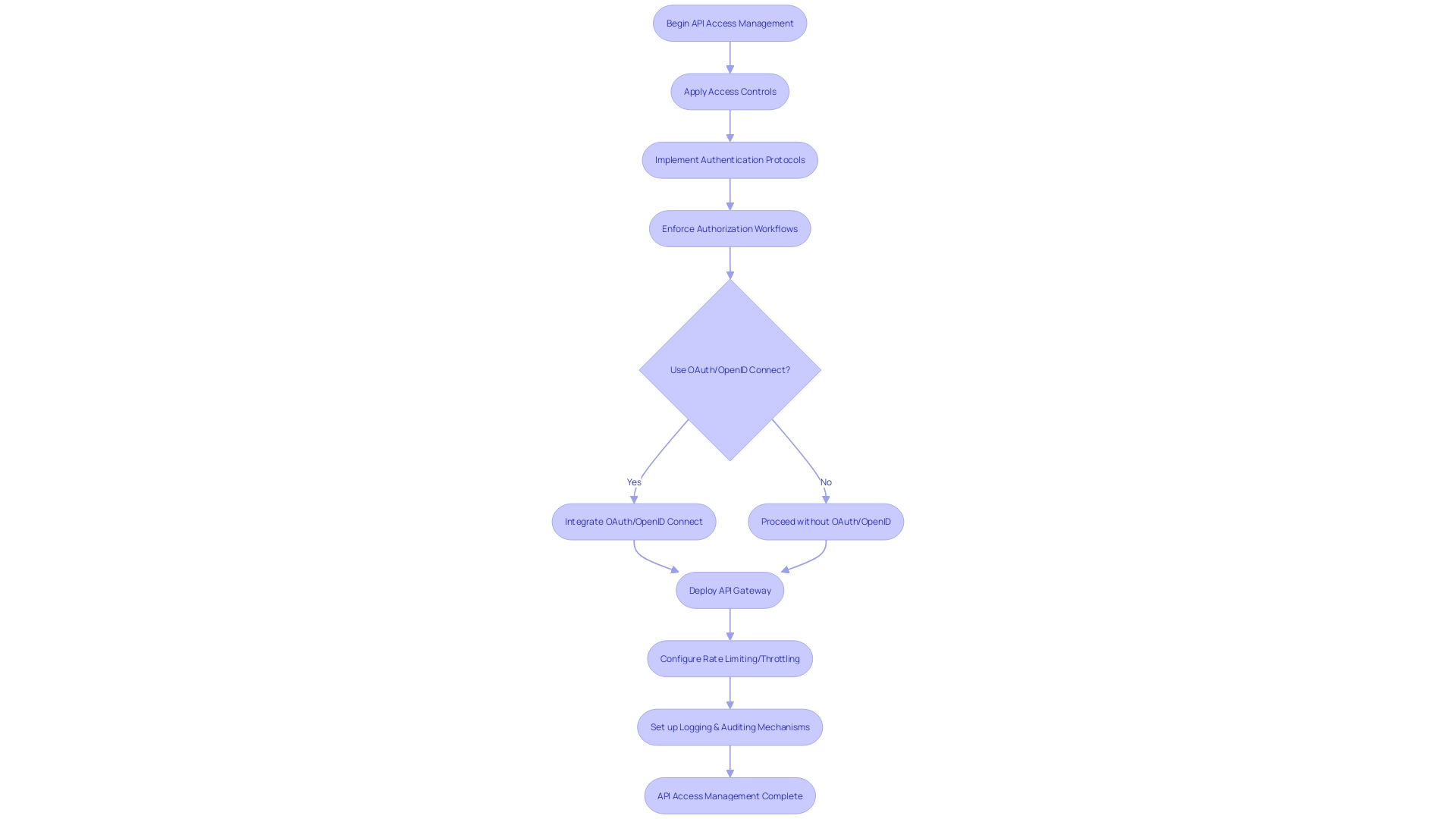
To effectively manage access to APIs and enhance code security, consider the following:1. Access Controls: Implement access control mechanisms to limit access based on user roles, permissions, and scopes. 2.
Authentication and Authorization: Utilize authentication and authorization protocols and frameworks to ensure only authenticated and authorized users can access the API. 3. OAuth and OpenID Connect: Use OAuth and OpenID Connect protocols for secure and standardized authentication and authorization workflows.
- API Gateway: Implement an API gateway to centralize access management, traffic routing, and security policies. 5.
Rate Limiting and Throttling: Implement rate limiting and throttling mechanisms to prevent abuse and ensure fair usage. 6. Logging and Auditing: Implement comprehensive logging and auditing mechanisms to track API activity and detect any suspicious behavior.
API Key Authentication Methods
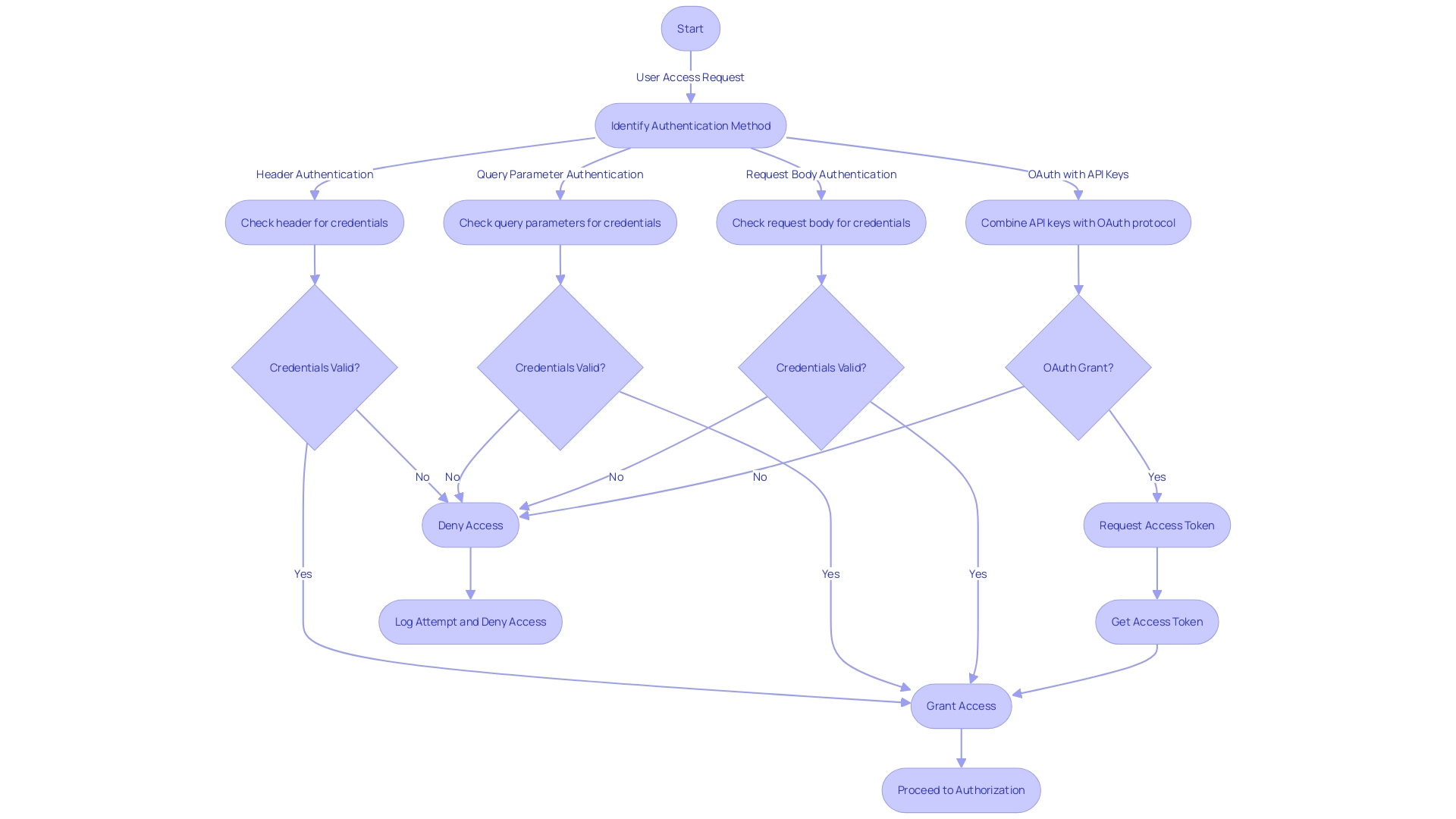
Securing applications against unauthorized access hinges on robust authentication methods. API keys are an excellent tool for this purpose, offering a variety of secure ways to verify identity.
To start, one common method is Header Authentication, where the API key is tucked safely inside the HTTP header of the request, much like a watermark on currency verifies its authenticity. Another option is Query Parameter Authentication, which places the API key in the URL, acting similarly to a passport – over yet secure.
When needed, Request Body Authentication allows the key to be embedded directly within the request body, ensuring the credentials are presented upfront for verification. Additionally, blending API keys with the OAuth protocol fortifies authentication, enhancing security credentials akin to digital certificates with public-private key pairs. It's essential to align the chosen method with API provider guidelines to ensure seamless and secure interactions.
Conclusion
To conclude, API keys are essential credentials that play a crucial role in securing digital interactions and maintaining data integrity. With the increasing reliance on APIs, protecting API keys against compromise is of utmost importance.
API keys serve as authorization and authentication mechanisms for accessing APIs. They ensure seamless communication between software applications, enhancing operational efficiency.
However, unauthorized access to APIs can lead to severe consequences such as identity theft and financial fraud. Different types of API keys cater to specific needs, including public, private, and limited access keys.
Managing API keys is vital for protecting sensitive data and maintaining customer trust. The benefits of using API keys include user authentication, robust access management, usage control through rate limits, and valuable analytics for decision-making.
API keys also facilitate the integration of third-party services, expanding the possibilities for digital progression. However, neglecting to address common issues such as inadvertent exposure and neglecting key rotation can lead to unauthorized breaches.
Implementing best practices such as secure storage, strict access control, and regular key rotation is crucial for API key safety. Managing access to APIs involves implementing access controls, authentication and authorization protocols, and utilizing mechanisms like OAuth and OpenID Connect. Logging and auditing API usage are also essential for detecting suspicious activities. Obtaining and managing API keys require careful selection, registration, and integration into applications. Following recommended authentication methods and securely storing API keys will ensure their effectiveness. Understanding the significance of API keys and implementing robust security measures are vital for protecting applications and maintaining data integrity. By prioritizing API key safety, businesses can maximize efficiency, productivity, and safeguard their digital systems.
Frequently Asked Questions
What is an API Key?
An API key is a credential, similar to a password, that is used to authorize and authenticate access to an API. It acts as a protective mechanism to ensure only authorized users can access the API, which is crucial for the security of web applications and platforms.
How do API keys work?
API keys are embedded into the application code and are used to establish the identity of the application to API services. When a request is made to an API server, the server verifies the API key much like a customs officer would inspect a passport. If the key is valid, access is granted.
Why is it important to protect API keys?
API keys need to be protected because unauthorized access to APIs can lead to security breaches, such as identity theft, financial fraud, and severe business repercussions. Protecting API keys helps maintain data integrity and safeguards digital interactions.
What are the different types of API keys?
There are three main types of API keys: Public API keys, which are used for broadly available APIs; Private API keys, which must be kept secure for APIs requiring precise identification; and Limited access API keys, which grant tailored access to certain parts of an API.
What are the benefits of using API keys?
API keys provide several benefits: They authenticate users, offer robust access management, implement rate limits, facilitate auditing and logging, and enable the integration of third-party services.
What are common issues with API keys?
Common issues include exposure of API keys, failure to regularly rotate API keys, and lack of adequate access controls and monitoring, all of which increase the risk of security threats.
What are the best practices for API key safety?
Best practices for API key safety include secure storage, restricted access, regular rotation, encrypted transmission, vigilant monitoring and logging, and a defined revocation process for compromised keys.
How do you obtain an API key?
To obtain an API key, select an API that meets your needs, register through the developer portal, create your API key following the provider's documentation, securely store the key, and include it in each API request.
How can access to the API be managed effectively?
Effective API access management includes implementing access controls, utilizing authentication protocols, using OAuth and OpenID Connect, employing an API gateway, rate limiting, and comprehensive logging and auditing.
What are the methods for API key authentication?
Common API key authentication methods include Header Authentication, Query Parameter Authentication, Request Body Authentication, and combining API keys with OAuth protocol to enhance security.




