Introduction
Safeguarding code and ensuring code security is crucial for developers to protect software and data from intrusions. In this article, we will explore various aspects of code security and delve into the best practices and strategies for achieving and maintaining it.
From integrating security into the development lifecycle to implementing robust authentication and authorization systems, securing data inputs and outputs, managing application secrets, conducting regular code audits and vulnerability scans, to handling security incidents and patch management, we will cover it all. By implementing these measures and adopting a proactive approach to code security, developers can ensure the integrity and safety of their codebase, enhancing overall product quality and mitigating risks. So let's dive in and discover how to fortify your code and protect it from potential vulnerabilities and cyber threats.
Understanding Code Security
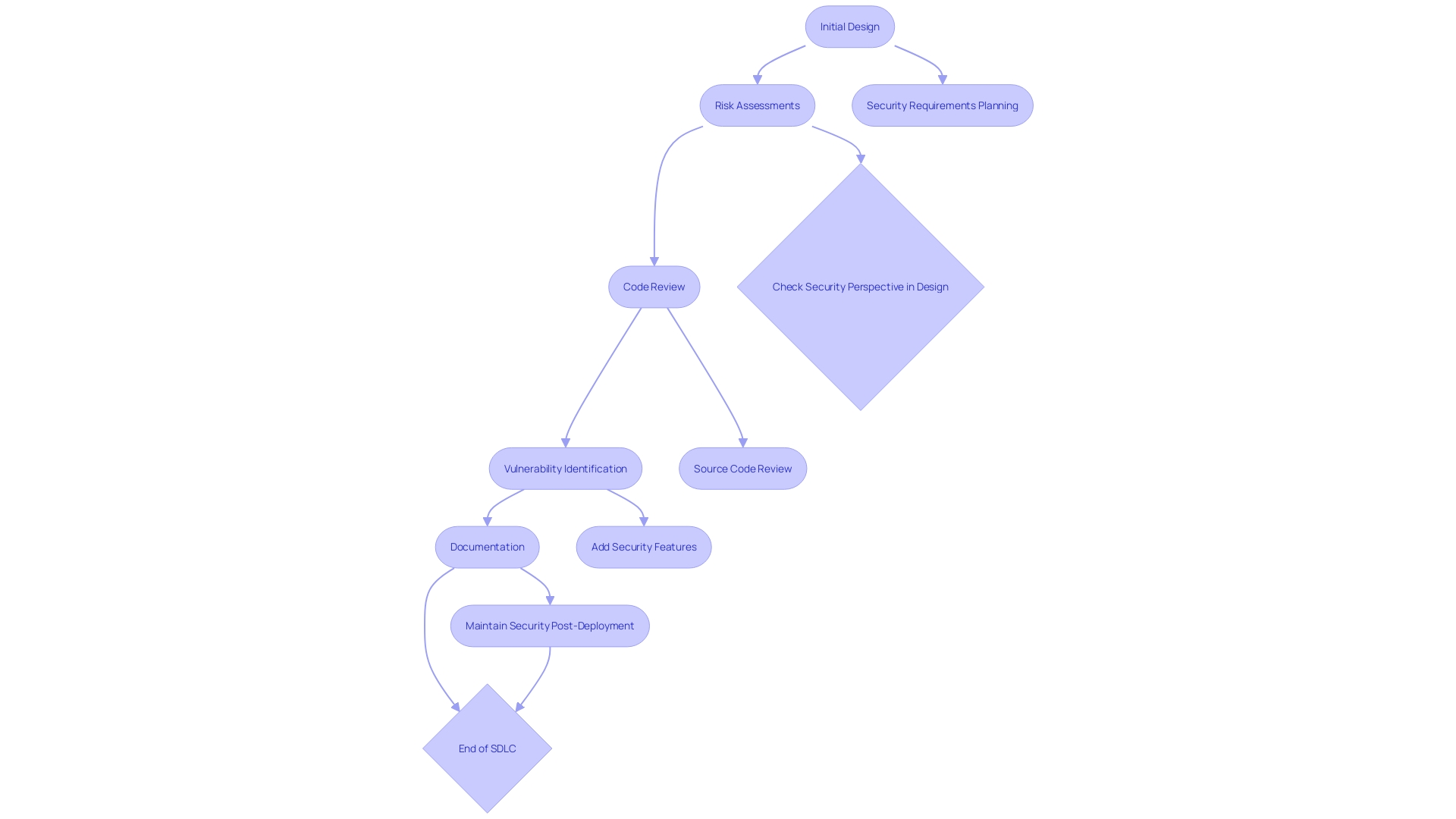
Safeguarding code is paramount for developers to shield software from intrusions and safeguard data. It is imperative to integrate security into every stage of development, starting from the initial design.
Rather than making it a lower priority, embed security considerations deeply into the project, be it for utility applications or the next innovative tech marvel. Periodically performing risk assessments during the development cycle can preemptively identify vulnerabilities, significantly enhancing product quality while saving time and resources by addressing these issues early.
Especially today, when software vulnerabilities can have profound impact, understanding the project structure is vital. Assess if the codebase is unique or a derivative, and if it's a fork, identify changes made and the primary functions exposed to users.
By documenting and educating on the types of potential security attacks, such as typosquatting or the inclusion of malicious packages, developers can proactively protect their code. A poignant insight on the state of software security highlights the urgency to address the complexities of code and its dependencies. Resorting to external libraries indiscriminately not only bulks up the code but also amplifies the risk of introducing vulnerabilities from unchecked sources. Therefore, a meticulous approach to code quality and dependency management is essential for maintaining a high standard of code security.
Implementing Authentication and Authorization
A core tenet of digital security lies in distinguishing who can enter your systems and what they can do upon entry, these principles are known as authentication and authorization. Security must be interwoven from the outset of software development, a practice commonly referred to as 'Security by Design'.
As elucidated by cybersecurity experts, authentication is the initial checkpoint where a system verifies a user's identity, immediately pivotal upon attempted access. Authorization follows, dictating their permissible actions.
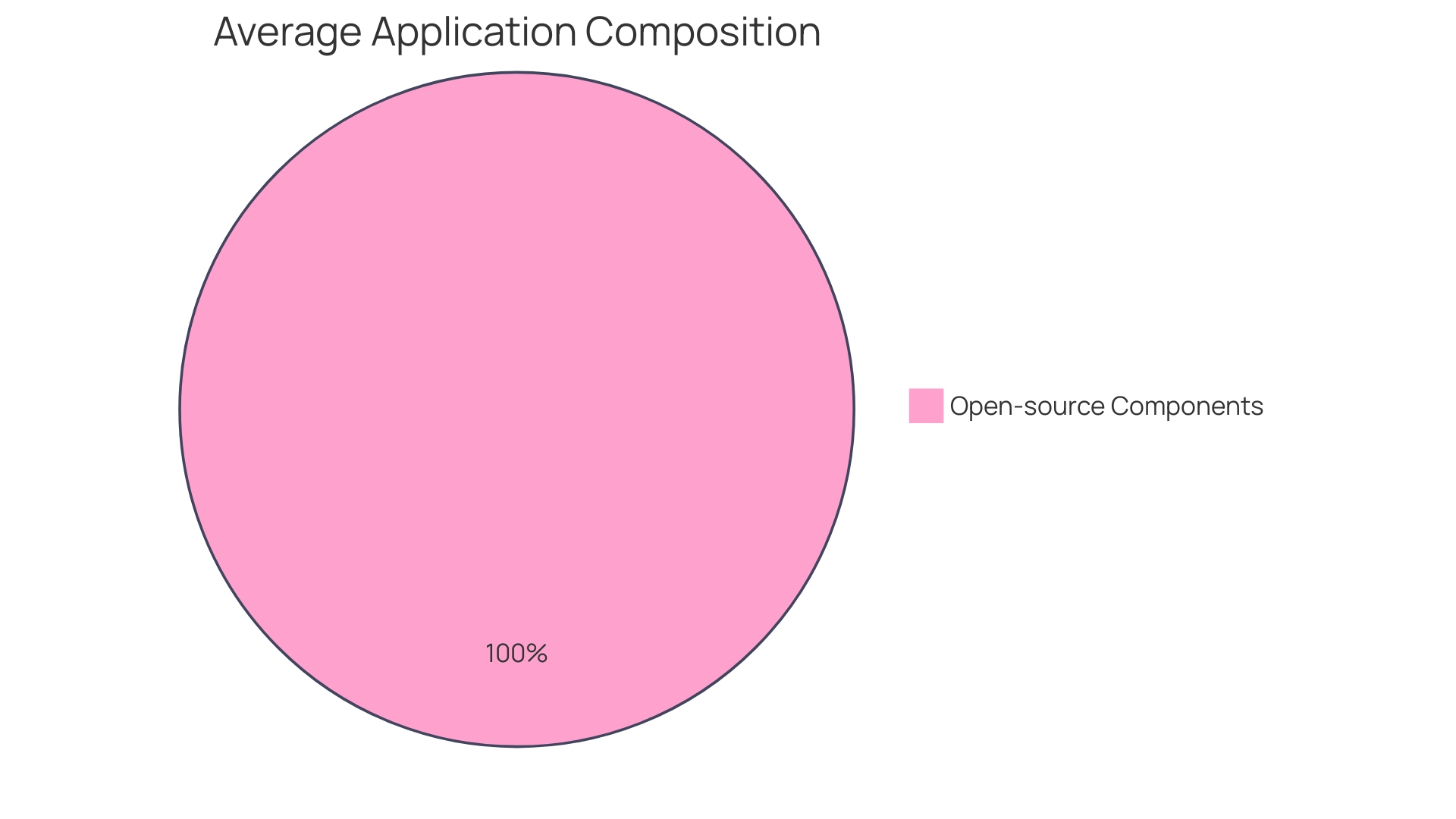
Consider that the OSSRA report of 2024 emphasized, 96% of audited commercial software incorporated open source components, with the average application containing 526 such components. This statistic underscores the complexity of today's software supply chains and highlights the irreplaceable role of automated security solutions. With the increasing integration of AI-generated code into the development process, a comprehensive understanding of the components within your code, including potential vulnerabilities, becomes an imperative. By implementing robust authentication, you can assure that only those who are verified can view or interact with sensitive aspects of your system, while authorization ensures they can only operate within their defined scope.
Securing Data Inputs and Outputs
Understanding the nuances of securing data handling in code is critical for safeguarding against cyber threats. Attacks like SQL injection and cross-site scripting prey upon weak input and output data validation. To combat these, advanced approaches and security best practices must be employed.
For instance, automated security testing has proven indispensable in a landscape where the average application contains 526 open-source components, as per the 2024 Open Source Security and Risk Analysis report. Automated solutions like software composition analysis (SCA) streamline the identification of vulnerabilities across these multiple components, which would be unmanageable manually. Moreover, these tools assist in revealing any open-source licenses, code quality, and security gaps, addressing 96% of commercial software that includes open-source content.
By exemplifying best practices with practical code snippets, developers gain a clearer comprehension of secure coding. AI-assisted applications upraise these practices, offering insights on how to shield against more sophisticated cyber-attacks like typosquatting and malicious packages. The adoption of a Software Bill of Materials (SBOM) emerges as a crucial step for maintaining software supply chain integrity.
SBOM fosters complete transparency of components and their security statuses, pivotal for preventing incidents that arise from exposed secrets such as API keys, often found in plain text within the code. As we move forward, remember the words of a cybersecurity expert: "The best application security tool is education". Investing in knowledge not only reinforces the defenses but also propels the development of secure applications tailored to your organization's specific needs, ultimately bolstering the overall code security.
Managing Application Secrets
Securing application secrets is crucial in maintaining the integrity and safety of any codebase. As such, API keys, passwords, and tokens must be given the same rigorous protection as the rest of the application. It's not just about having robust security measures; it's about integrating these measures throughout the development lifecycle as advocated by the DevSecOps community.
This way, security is not an afterthought but a preemptive strike against potential misuse and unauthorized access. By utilizing secure storage solutions that include encryption and controlled access, we create a fortress around these critical data points. Enforcing these best practices casts a broad safety net, ensuring that every angle from which a breach could occur is being surveilled and secured.
Regular Code Audits and Vulnerability Scans
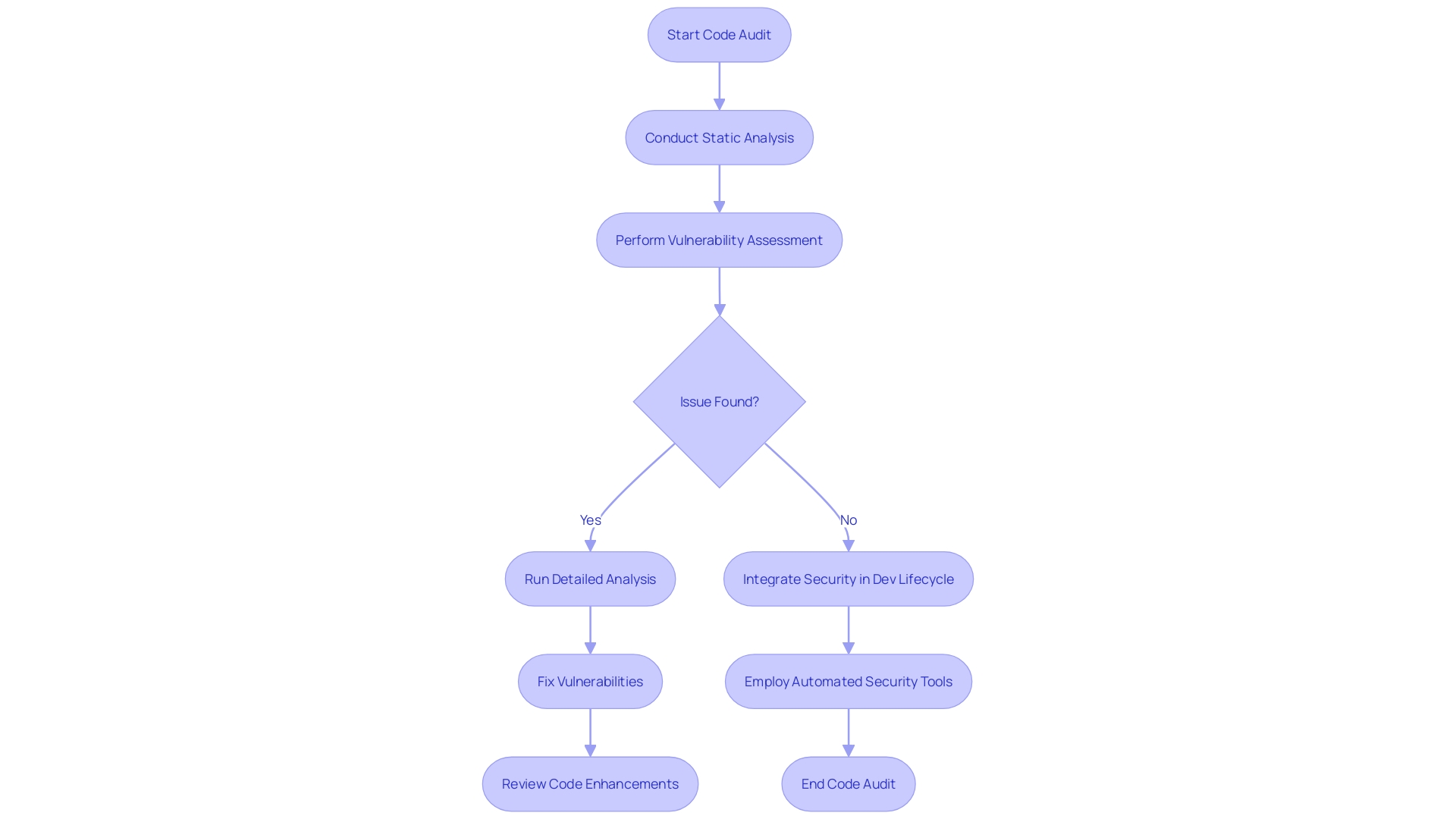
Uncovering the unseen, as demonstrated by our colleague Maarten Boone's experience with the Dutch Electoral Council, underscores the criticality of regular code audits and vulnerability scans. In the realm of software development, the commitment to secure, dependable coding is unwavering. Rigorous code examination through static analysis and vulnerability assessments is an indispensable tactic, identifying weaknesses before they escalate into severe threats.
This practice ensures that every line of code contributes to a stronger, impenetrable digital infrastructure. The integration of security early in the development lifecycle and steadfast code review cultivates a proactive environment for quality and safety. From scrutinizing the originality of code in forks to understanding the intricacies of smart contracts, every step fortifies the code's resilience.
Employing automated tools bolsters this process by catching the glaring issues that human auditors might overlook. In an industry teeming with complex web applications, security is paramount. Web scanners emerge as not just a shield but a strategic asset, sharpening a developer's edge in the competitive landscape.
They play a vital role in sealing fissures that might be exploited, mirroring the intricate duties entrusted to web developers. Moreover, quality audits delve beyond superficial analysis, dispensing comprehensive insights into the code's structure and fortitude, pinpointing whether vulnerabilities have been addressed. Thus, navigating the intricate web of software security demands vigilance and an unwavering commitment to these diligent practices of code review and vulnerability scanning.
Handling Security Incidents and Patch Management
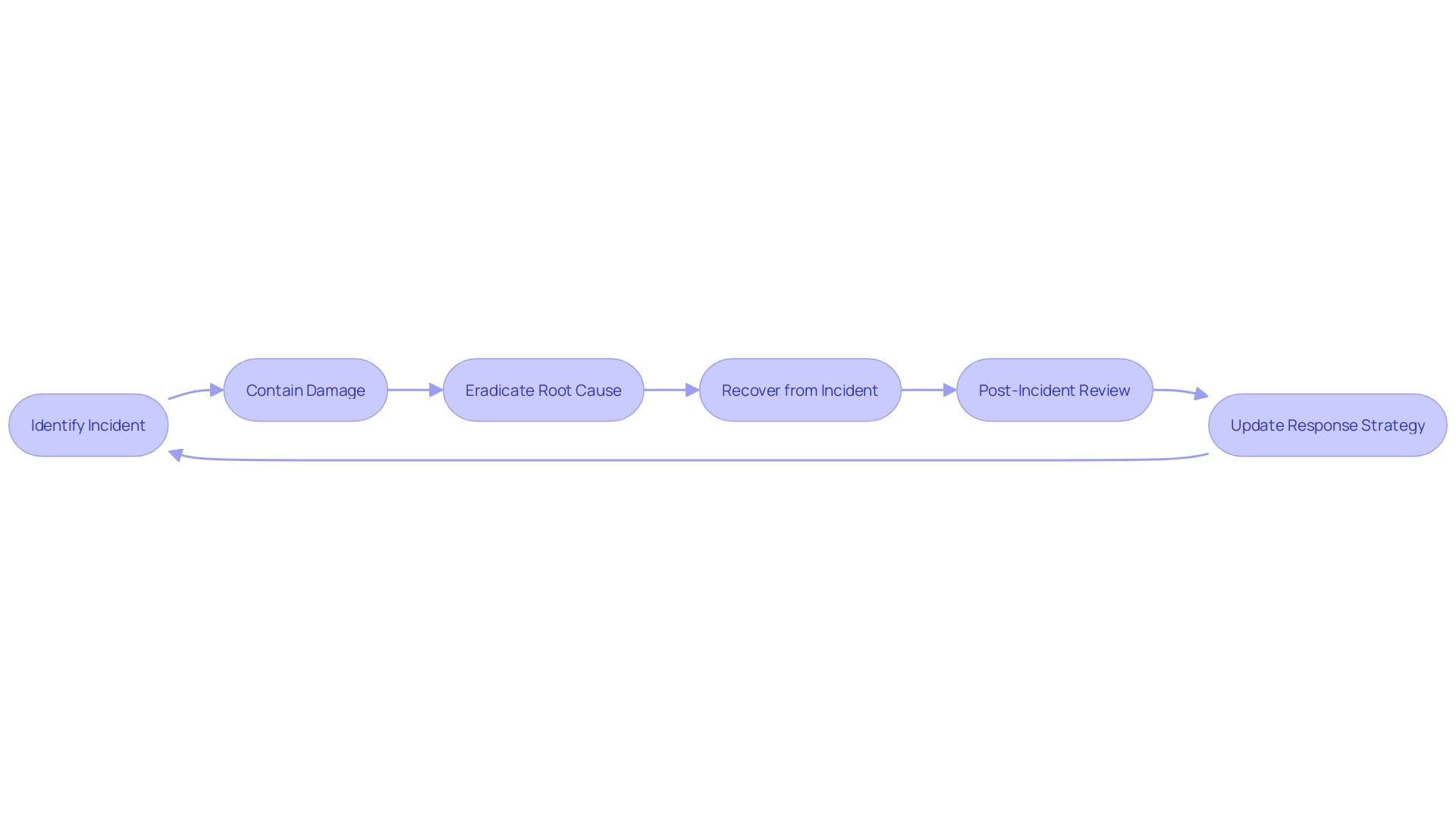
Incident response (IR) is an organized approach to addressing and managing the aftermath of a security breach or cyberattack, also known as an incident. The objective is to handle the situation in a way that limits damage and reduces recovery time and costs. An effective incident response plan includes a set of predetermined instructions that help identify, respond to, and recover from network security incidents.
These plans involve various actions ranging from technical IT solutions to business continuity measures, aiming to quickly identify incidents, contain the damage, and eradicate the root cause. Since the inception of Computer Emergency Response Teams (Certs) in the 1980s, IR has evolved from rudimentary measures to complex strategies incorporating a variety of domains like human resources, legal affairs, and public relations. The sophistication of these plans is evident in their ability to encompass not only IT or security considerations but also the welfare of personnel, legal compliances, financial integrity, and the organization's reputation.
A successful IR strategy isn't just about the technology or the process; it encompasses the entire organizational fabric, ensuring that all stakeholders are prepared to act effectively in times of crisis. As such, the BCM (Business Continuity Management) process begins with a comprehensive risk assessment, balancing an organization's objectives against potential impacts to personnel, operations, and reputation. Rigorous and regular reviews, along with the incorporation of new threats and lessons from past incidents, ensure that the IR plan evolves to meet the challenges of a dynamic security landscape.
Conclusion
In conclusion, safeguarding code and ensuring code security is crucial for developers. By integrating security into every stage of development, developers can preemptively identify vulnerabilities, enhance product quality, and save time and resources. Implementing robust authentication and authorization systems ensures secure access while managing application secrets protects critical data points.
Regular code audits and vulnerability scans fortify code resilience. Effective incident response and patch management strategies mitigate damage from security breaches. By adopting a proactive approach to code security, developers enhance overall product quality and protect against vulnerabilities and cyber threats.
Frequently Asked Questions
What is the importance of integrating security into the development process?
Integrating security from the initial design stage throughout the entire development process is crucial to protect software from intrusions and safeguard data, preemptively identifying and addressing vulnerabilities.
How can developers proactively protect their code against security attacks?
Developers can protect their code by understanding their project structure, documenting potential security attacks like typosquatting and malicious packages, and being cautious with the use of external libraries to avoid introducing vulnerabilities.
What are authentication and authorization in the context of digital security?
Authentication is the process of verifying a user's identity when they attempt to access a system, while authorization defines what actions the authenticated user is allowed to perform within that system.
How prevalent is the use of open-source components in commercial software?
According to the OSSRA report of 2024, 96% of audited commercial software incorporates open-source components, with the average application containing 526 such components, highlighting the complexity of software supply chains.
Why are automated security solutions important in software development?
Automated security solutions, such as software composition analysis (SCA), are important because they can efficiently identify vulnerabilities across numerous components and help manage open-source licenses, code quality, and security gaps.
What is a Software Bill of Materials (SBOM) and why is it important?
A Software Bill of Materials (SBOM) is a comprehensive list of components, along with their security statuses, used in software development. It is important for maintaining software supply chain integrity and preventing incidents stemming from exposed secrets in the code.
How should application secrets like API keys and passwords be managed?
Application secrets should be protected with secure storage solutions that include encryption and controlled access, integrated throughout the development lifecycle to prevent misuse and unauthorized access.
What role do regular code audits and vulnerability scans play in software development?
Regular code audits and vulnerability scans are essential for identifying weaknesses in code before they become severe threats. They contribute to a stronger digital infrastructure and are supported by automated tools and detailed quality audits.
What is incident response (IR) and why is it important?
Incident response (IR) is an organized approach to manage the aftermath of a security breach or cyberattack. It involves a set of instructions to identify, respond to, and recover from incidents, aimed at limiting damage and reducing recovery time and costs.
How has the approach to incident response evolved since the 1980s?
Since the inception of Computer Emergency Response Teams (CERTs) in the 1980s, incident response has evolved to incorporate complex strategies that address not only IT and security but also human resources, legal affairs, public relations, and the welfare of personnel and the organization's reputation.




