Overview
SAST scanning, or Static Application Security Testing, is a proactive method that analyzes source code for vulnerabilities without executing the program, allowing developers to identify and rectify security issues early in the software development lifecycle. The article emphasizes that this early detection significantly reduces remediation costs and enhances overall application security, particularly as the demand for secure mobile applications rises in the face of increasing cyber threats.
Introduction
In an increasingly interconnected digital landscape, the security of applications has never been more critical. As organizations strive to protect their software from vulnerabilities, Static Application Security Testing (SAST) emerges as a powerful ally in the quest for robust application security. By examining code at rest, SAST empowers developers to identify and rectify potential security flaws before they can be exploited, ultimately streamlining the development process and enhancing overall security.
With the rapid growth of mobile applications and the pressing need for compliance in various industries, understanding the intricacies of SAST becomes essential. This article delves into the purpose, benefits, and future of SAST, highlighting its role in fostering collaboration, ensuring compliance, and integrating seamlessly into modern development practices.
As the landscape of application security continues to evolve, embracing SAST can significantly bolster an organization's defense against emerging threats.
Understanding Static Application Security Testing (SAST)
What is SAST scanning? It signifies an essential white-box testing approach that examines source code, bytecode, or binary code for possible weaknesses without requiring program execution. To understand what is SAST scanning, it's important to note that these tools evaluate the code in its static state to effectively pinpoint a broad spectrum of vulnerabilities, including:
- Coding errors
- Insecure coding practices
- Compliance violations
This proactive strategy allows developers to rectify vulnerabilities early in the software development lifecycle (SDLC), significantly mitigating the risk of exploitation in production environments.
Highlighting early detection not only simplifies the development process but also strengthens the application against future threats, thereby improving overall efficiency and protection. Considering that the demand for mobile application security is expected to rise at a CAGR of 26% due to heightened internet usage and BYOD policies, understanding what is SAST scanning and its significance in incorporating static application security testing becomes even more evident. Furthermore, with North America holding the largest share in the Application Security Market, the significance of static application security testing within this landscape is underscored.
When choosing a static analysis service provider, organizations should take into account factors such as:
- Technology stack support
- Scalability
- Reporting capabilities
- Customer assistance
As emphasized in recent case studies, to ensure the effectiveness and reliability of the selected resources.
The Purpose and Benefits of SAST in Application Security
What is SAST scanning aims to uncover vulnerabilities within the code before an application goes live. The key benefits of implementing SAST are manifold, and tools like Kodezi can play a crucial role in maximizing these advantages:
-
Early Detection: SAST facilitates the identification of security issues during the development phase, significantly reducing remediation costs and time. With Kodezi’s AI-supported development resource, programmers can automatically examine and rectify code, guaranteeing that weaknesses are addressed early. Research has demonstrated that early weakness detection can result in a cost reduction of up to 30% compared to late-stage fixes.
-
Comprehensive Coverage: Open-source tools like SonarQube and Semgrep support a wide range of programming languages and can swiftly analyze extensive codebases. Similarly, Kodezi supports over 30 languages, optimizing and correcting code effectively, which is crucial for understanding what is SAST scanning and ensuring thorough examination of every line for potential vulnerabilities. This comprehensive approach assists organizations in upholding a high standard of protection throughout their applications.
-
Integration into CI/CD Pipelines: Static Application Security Testing effortlessly merges into Continuous Integration/Continuous Deployment processes, facilitating automated safety checks that align with agile development practices. Kodezi's capabilities can further enhance this integration by providing real-time bug analysis, making safety a continuous consideration rather than an afterthought.
-
Compliance Assurance: Many industries face stringent compliance requirements, and static application security testing plays a pivotal role in helping organizations meet these regulations. Kodezi can contribute by flagging non-compliant coding practices, enhancing safety posture, and supporting regulatory compliance. Case studies, including the one named 'Benefits of Implementing SAST,' illustrate how tools like Kodezi can improve overall defense stance within software development processes.
-
Enhanced Collaboration: By promoting better code readability and organization, static analysis fosters improved collaboration among developers. Kodezi’s automatic commenting and optimization features create a collaborative environment, crucial for maintaining secure coding practices across teams. As one industry leader pointed out,
With the tool’s guardrails, you gain assurance that best practices are consistently adhered to.
However, it is important to recognize some limitations of static application testing, including the potential to overlook configuration-related vulnerabilities and challenges with dynamically generated code. Furthermore, with advancements in Interactive Application Security Testing (IAST), which merges static application security testing and DAST methodologies, organizations can now identify issues during operation while simultaneously evaluating code. This dual strategy is particularly effective in QA environments with automated functional tests, which raises the question of what is SAST scanning, making tools like Kodezi an essential part of modern application protection.
Additionally, Kodezi offers both free and paid plans depending on your usage, making it accessible for various users.
SAST vs. Other Testing Methods: Understanding the Differences
Static Application Security Testing is often compared to Dynamic Application Security Testing (DAST), with each fulfilling unique functions in the application security landscape. The main distinctions can be summarized as follows:
- Timing: Static analysis is performed during the coding phase, allowing for early identification of weaknesses, whereas dynamic analysis occurs during the testing phase, evaluating applications in an operational state.
- Approach: Static analysis investigates the source code directly, utilizing lexical analysis and rule-based pattern matching to detect possible weaknesses without running the code. In contrast, DAST simulates real-world attacks on the live application, focusing on runtime vulnerabilities.
- Scope: The static analysis technique possesses the capability to uncover a wider array of vulnerabilities, including those stemming from coding practices and architectural flaws. DAST, however, focuses on runtime issues such as authentication, session management, and other operational concerns.
Both methodologies are integral to a well-rounded protection strategy. Organizations should schedule regular SAST scans to understand what is SAST scanning, which is essential for maintaining a secure codebase and ensuring ongoing adherence to safety standards. The integration of automated code debugging tools like Kodezi enhances this process, allowing teams to instantly identify and fix codebase issues.
Kodezi offers thorough explanations for swift issue resolution, optimizes performance, identifies vulnerabilities, adds exception handling, improves code formatting, and enforces coding standards, ultimately supporting agile development practices. This is especially advantageous for tackling weaknesses detected through static and dynamic analysis tools, such as enhancing authentication methods and overseeing session protection.
As Cisco observes,
Due to our resolution of an average of 715 billion DNS requests each day, we encounter more data protection threats, more malware, and more cyberattacks than any other protection provider.
Moreover, the Hybrid Application Testing (HAST) approach integrates static and dynamic analysis methodologies, offering a thorough solution for detecting and addressing application vulnerabilities. While requiring more time and budget, HAST is optimal for designing secure applications. Employing static and dynamic analysis together, along with automated debugging resources, enables organizations to create a more extensive defense against emerging security threats, guaranteeing that applications remain secure throughout their lifecycle.
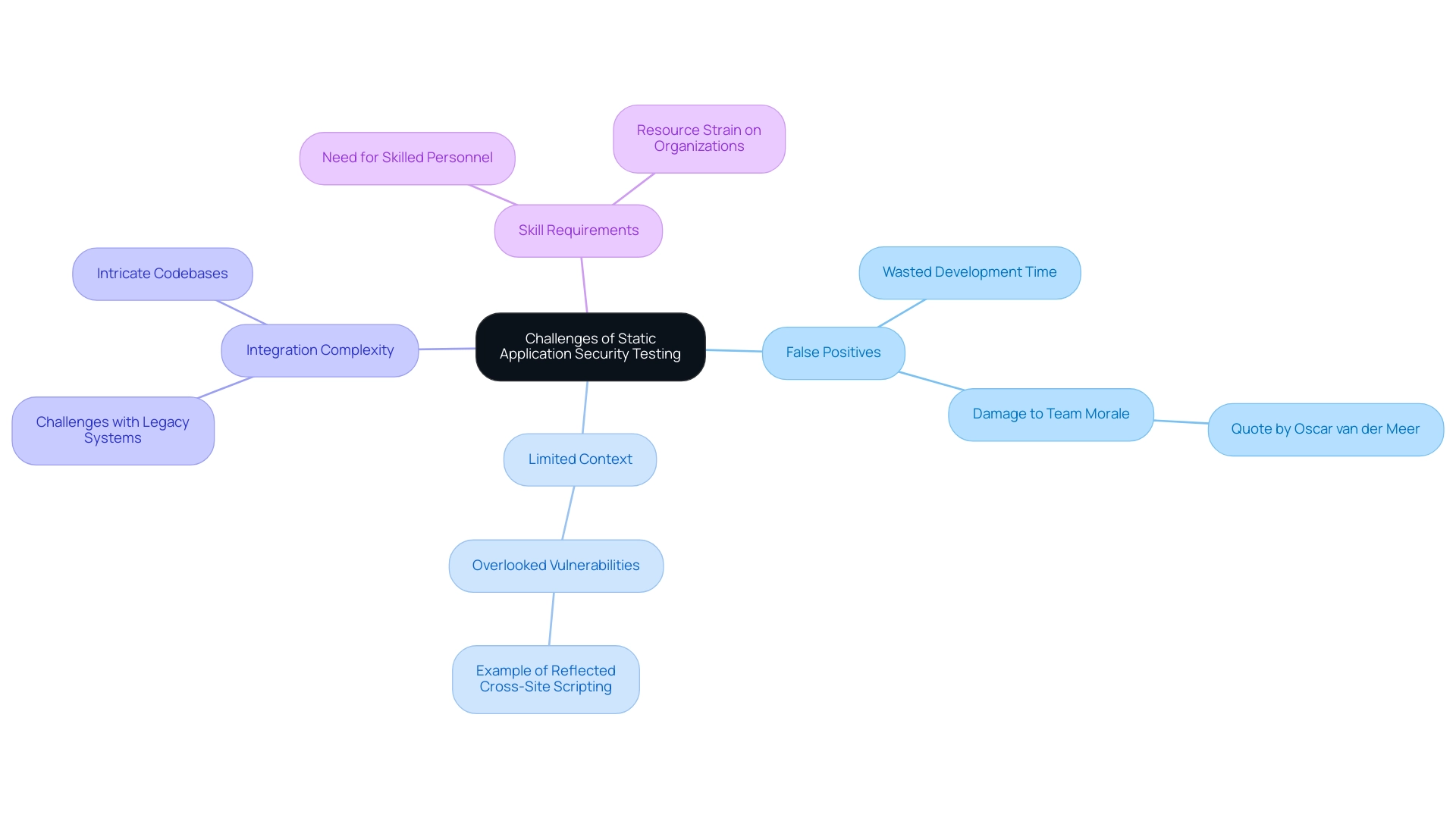
Challenges and Limitations of Static Application Security Testing
While Static Application Security Testing provides significant benefits, it is essential for developers to recognize its limitations:
- False Positives: Static analysis tools often produce false positives, which can lead to unnecessary remediation efforts. As Oscar van der Meer points out, > False positives waste valuable dev time and damage team morale <. This not only drains resources but can also hinder productivity.
- Limited Context: By examining code independently, static analysis tools may overlook weaknesses that only emerge during execution or in particular operational settings, resulting in gaps in security coverage. For instance, a refined rule for reflected cross-site scripting weaknesses specifies that a data flow from HTTP to a print operation writing HTML is a flaw if the data is not properly managed, showcasing a specific example of what static analysis tools might overlook.
- Complexity of Integration: Incorporating security analysis tools into existing workflows can present challenges, particularly within legacy systems or intricate codebases, complicating the implementation process.
- Skill Requirements: The effective utilization of static application security testing necessitates skilled personnel capable of interpreting results and prioritizing vulnerabilities accurately, which can be a resource strain for many organizations.
Moreover, the financial implications of not addressing these limitations can be significant; two-thirds of decision-makers who’ve seen their firms breached six or more times reported that total breach costs have exceeded $2 million. By understanding these challenges, organizations can better navigate the implementation of static application security testing, ensuring they maximize its advantages while mitigating potential drawbacks. Additionally, exploring alternative solutions such as Runtime Security, which embeds trust boundaries throughout the software stack, can help organizations manage false positives and reduce backlogs, ultimately safeguarding applications from development to production.
The Future of SAST: Trends and Innovations
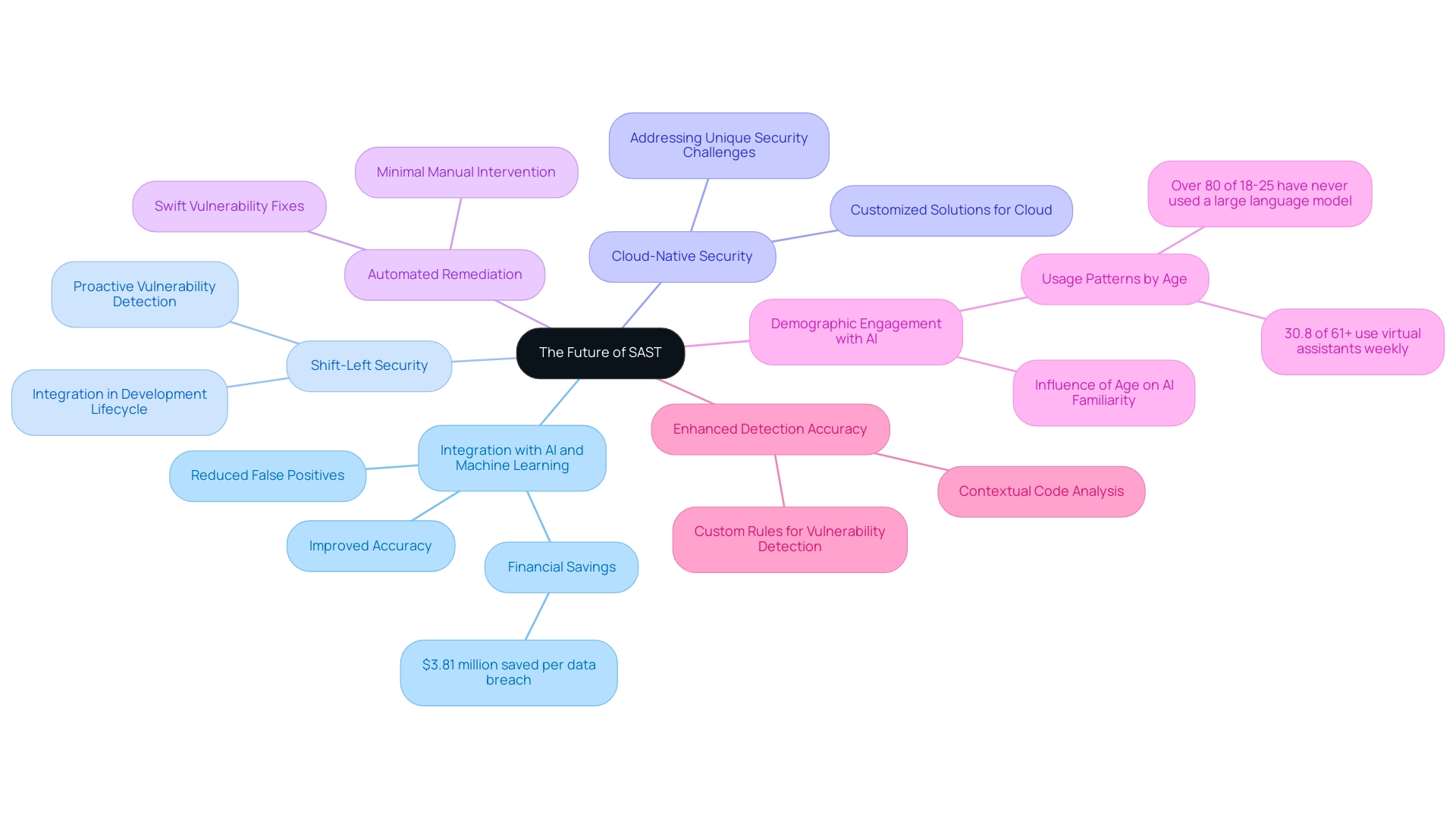
The future of Static Application Security Testing (SAST) is being revolutionized by several pivotal trends and innovations that promise to enhance both security measures and operational efficiency:
- Integration with AI and Machine Learning: The infusion of AI and machine learning into static application security testing tools is expected to significantly elevate accuracy and efficiency. By reducing false positives and improving detection rates, organizations can allocate resources more effectively and focus on genuine threats. Significantly, artificial intelligence can save organizations up to $3.81 million per data breach, emphasizing the financial benefits of incorporating AI into protective measures.
- Shift-Left Security: As more organizations adopt DevSecOps practices, static application testing is becoming a vital part of the development lifecycle, highlighting protection from the initial phases of software creation. This proactive method aids in recognizing weaknesses sooner, reducing potential risks prior to deployment.
- Cloud-Native Security: The rise of cloud-native applications presents distinct security challenges, encouraging static analysis solutions to adjust accordingly. These instruments are developing to provide customized solutions that tackle the intricacies of safeguarding cloud settings, ensuring strong defense against weaknesses inherent in these systems.
- Automated Remediation: Looking ahead, upcoming software solutions are likely to incorporate automated remediation features. This capability will empower developers to swiftly rectify identified vulnerabilities with minimal manual intervention, thereby accelerating the development cycle and enhancing security responsiveness.
- Demographic Engagement with AI: Understanding the demographics of AI users can also inform the adoption of AI in security applications. For instance, the case study titled "AI Demographics by Age" reveals that 30.8% of individuals aged 61+ use virtual assistants weekly, while over 80% of those aged 18-25 have never used a large language model. This information can assist organizations customize their security analysis resources to better engage various user groups.
- Enhanced Detection Accuracy: Tools like Semgrep's AI assistant enhance detection accuracy by analyzing the context of surrounding code and creating custom rules for improved vulnerability detection. This example illustrates how AI can directly enhance the effectiveness of static application security testing tools.
By staying abreast of these trends and integrating these insights, organizations can effectively leverage the concept of what is SAST scanning, fortifying their application security posture while optimizing productivity and resource allocation.
Conclusion
Embracing Static Application Security Testing (SAST) is a strategic move for organizations aiming to enhance their application security. By conducting thorough examinations of code at rest, SAST empowers developers to identify and address vulnerabilities early in the software development lifecycle, significantly reducing the risk of exploitation in production environments. The proactive nature of SAST not only streamlines the development process but also fortifies applications against emerging threats, making it an indispensable tool in modern software development.
The benefits of SAST are extensive, ranging from early detection of vulnerabilities to seamless integration into CI/CD pipelines. Tools like Kodezi exemplify how organizations can maximize these advantages, offering comprehensive coverage across various programming languages while ensuring compliance with stringent industry regulations. Furthermore, the collaborative environment fostered by SAST enhances code readability and organization, promoting best practices among development teams.
While challenges such as false positives and integration complexities exist, understanding and addressing these limitations can lead to improved outcomes. The future of SAST is bright, driven by innovations in AI, machine learning, and automated remediation, all of which promise to elevate the efficiency and accuracy of security measures. By harnessing these advancements, organizations can not only protect their applications but also optimize their development processes, ensuring a robust defense against the ever-evolving landscape of cyber threats.
Frequently Asked Questions
What is SAST scanning?
SAST scanning, or Static Application Security Testing, is a white-box testing approach that examines source code, bytecode, or binary code for vulnerabilities without executing the program. It evaluates code in its static state to identify issues such as coding errors, insecure coding practices, and compliance violations.
What are the benefits of SAST scanning?
The benefits of SAST scanning include early detection of security issues during the development phase, comprehensive coverage of various programming languages, seamless integration into CI/CD pipelines, assurance of compliance with industry regulations, and enhanced collaboration among developers.
How does SAST scanning help with early detection?
SAST scanning allows for the identification of security issues early in the software development lifecycle, significantly reducing remediation costs and time. Research shows that early detection can lead to cost reductions of up to 30% compared to fixing issues later in the process.
What tools support SAST scanning?
Tools like Kodezi, SonarQube, and Semgrep support SAST scanning. Kodezi, for example, can automatically examine and rectify code across over 30 programming languages, ensuring thorough analysis for vulnerabilities.
How does SAST integrate into CI/CD pipelines?
SAST scanning can be easily integrated into Continuous Integration/Continuous Deployment (CI/CD) processes, allowing for automated safety checks that align with agile development practices. This integration helps maintain a continuous focus on security throughout the development lifecycle.
Why is compliance important in SAST scanning?
Compliance is crucial as many industries face strict regulations. SAST scanning helps organizations meet these requirements by flagging non-compliant coding practices, thereby enhancing their security posture and supporting regulatory compliance efforts.
How does SAST scanning enhance collaboration among developers?
SAST scanning promotes better code readability and organization, which fosters improved collaboration among developers. Tools like Kodezi enhance this by providing automatic commenting and optimization features, ensuring that secure coding practices are consistently followed.
What are some limitations of SAST scanning?
Some limitations of SAST scanning include the potential to overlook configuration-related vulnerabilities and challenges associated with dynamically generated code. Additionally, advancements in Interactive Application Security Testing (IAST) may complement SAST by identifying issues during operation.
What is the expected market trend for mobile application security?
The demand for mobile application security is expected to rise at a compound annual growth rate (CAGR) of 26% due to increased internet usage and Bring Your Own Device (BYOD) policies.
What factors should organizations consider when choosing a static analysis service provider?
Organizations should consider factors such as technology stack support, scalability, reporting capabilities, and customer assistance when selecting a static analysis service provider to ensure effectiveness and reliability.




