Introduction
In the digital landscape, API keys serve as crucial tools for secure communication and access management. They act as unique identifiers, allowing verified developers to interact with APIs and ensuring the integrity of the system. However, the rise in API breaches highlights the need for robust security measures.
Recent statistics reveal that 78% of cybersecurity teams have encountered API-related security incidents, emphasizing the importance of API key protection. In this article, we will explore the significance of API keys, how they work, different types of API keys, and best practices for their usage. We will also discuss the process of obtaining an API key and the security considerations associated with them.
By understanding and implementing proper API key management, developers can enhance the security and efficiency of their applications in the ever-evolving digital landscape.
What is an API Key?
In the digital landscape, an API key is more than just a unique identifier; it's the linchpin of security and access management. This small piece of digital data is a critical component of API documentation, acting as both a gatekeeper and facilitator, ensuring that only verified developers can make requests and interact with an API's functionalities.
As we navigate through the complexities of modern technologies like Kubernetes, the importance of robust authentication mechanisms comes to the forefront. Traditional methods often fall short in the face of sophisticated cyber threats, underscoring the need for advanced solutions such as API gateways integrated with LDAP Single Sign-On. These gateways do not simply act as connectors between various services; they are the vanguards of security, providing a buffer against password leaks, unauthorized access, and potential attacks, while simultaneously streamlining system management and enhancing user experience.
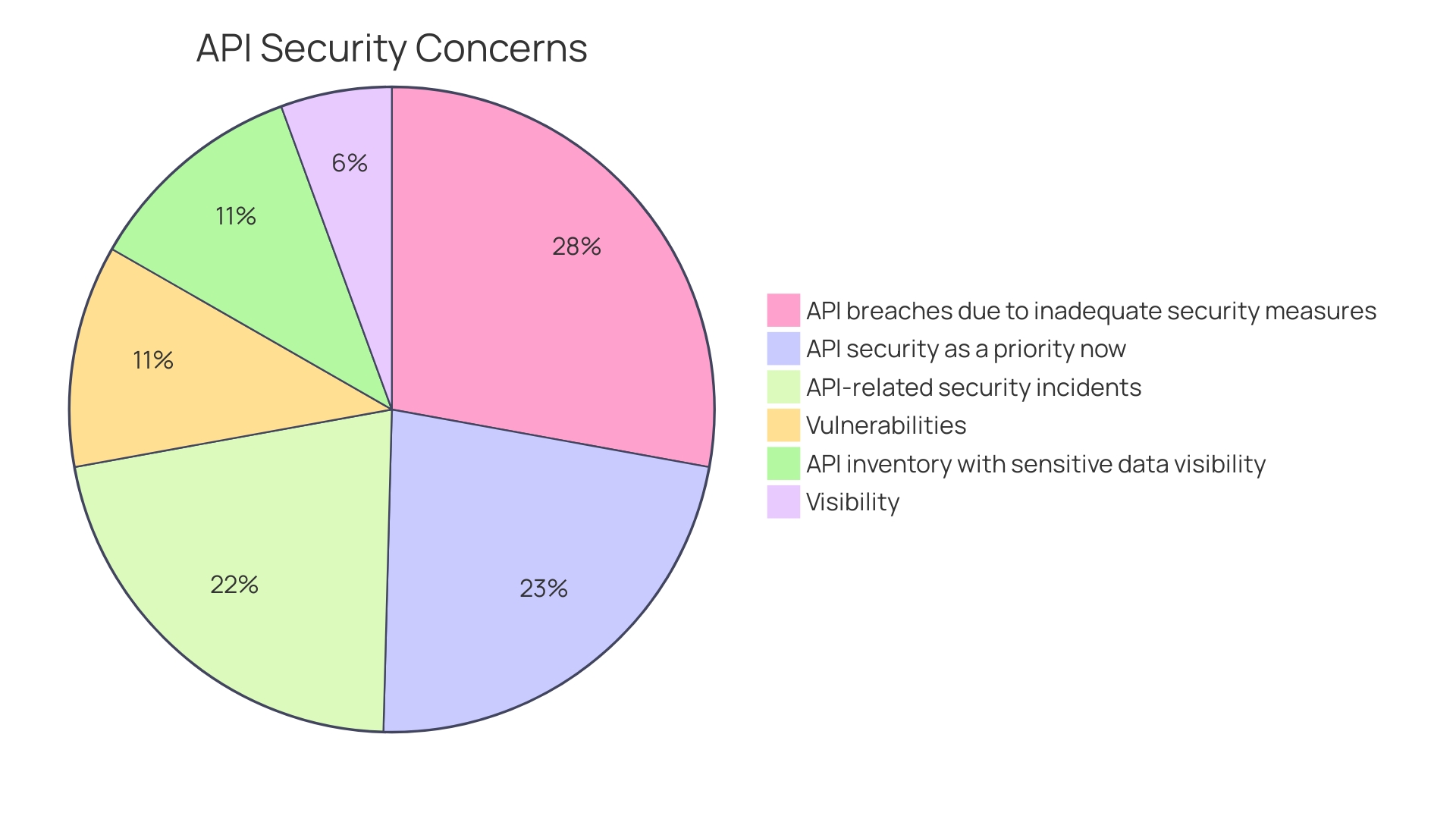
The evidence of the necessity for secure API practices is starkly highlighted by the alarming statistics that reveal a staggering 78% of cybersecurity teams have encountered API-related security incidents in the past year. Furthermore, while a significant portion of organizations maintain full inventories of APIs, only 40% have the means to track those that handle sensitive data. This gap in visibility has made API security a top priority, now more than ever.
The value of clear, comprehensive API documentation cannot be overstated. It serves as a roadmap, detailing essential information including endpoints, methods, and parameters. This clarity is not just a matter of convenience, but a cornerstone of security.
As APIs continue to underpin the seamless functionality of the digital world, their documentation stands as a testament to an organization's commitment to safeguarding its systems and users.
To paint a picture of the API's purpose and benefits, documentation must address the pressing question of what unique value the API offers. It is the narrative that connects a developer to the API's capabilities, highlighting the resolution to a market need that the product promises. It's about ensuring that from the very first encounter, developers are not only informed but also engaged and equipped to integrate the API into their own digital ecosystems.
The gravitas of these considerations is further underscored by the discovery of over 18,000 exposed API secrets during a recent security sweep of URLs, with 41% posing high financial risks. Such findings emphasize the critical need for stringent security measures and the pivotal role of API keys in fortifying the digital domain against ever-evolving cyber threats.
How API Keys Work
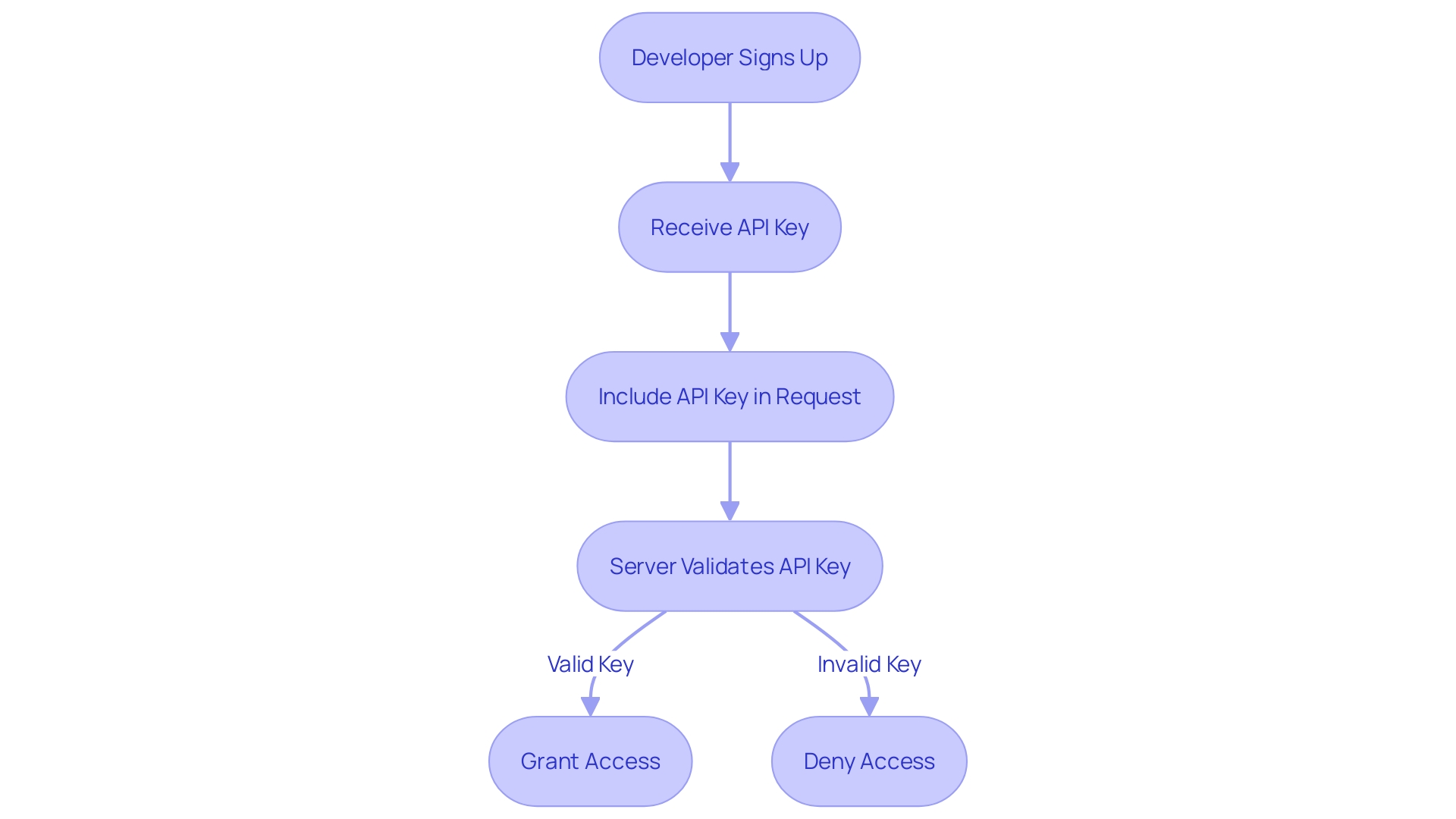
API keys are indispensable tools in the realm of software development, offering a streamlined and secure method for applications to interact with APIs. To illustrate, consider a developer using the Razorpay API without the need for an SDK. They must first sign up for a merchant account, after which an API key is provided.
This key must be included in every request to the API. Upon receipt, the server validates the key and determines the level of access granted. This critical step is what ensures only authorized users can engage with the API services, thereby safeguarding the API's resources and maintaining the integrity of the system.
With the API's role as a bridge between different software components, its security becomes paramount, especially in light of reports that 78% of cybersecurity teams have encountered API-related security incidents within a year. Proper authentication, as emphasized in the practices of TotalEnergies Digital Factory and modern API gateways, is not just about verifying identity, but also about managing access and defending against sophisticated cyber threats. In this context, API keys are not just identifiers but are part of a more comprehensive security strategy aimed at protecting sensitive data from unauthorized access and potential breaches.
Types of API Keys
API keys and tokens are often confused, but they serve distinct purposes and have different attributes. API keys are unique identifiers used to authenticate a user or application, allowing them to access specific functionalities or data from an API. They are generally static, created once, often through a user interface, and can remain valid until they are manually rotated or configured to expire after a set period.
On the other hand, tokens represent a user session or specific privileges and are used by individual users for a limited time. They are dynamically generated and can vary with each user session or transaction. Tokens are more about representing user states and permissions, while API keys are about secure identification and access.
Understanding these differences is crucial, especially in the context of API security. With the increasing prevalence of APIs in software development and the surge in API breaches, distinguishing between API keys and tokens becomes essential. Unauthorized access to APIs, especially those containing sensitive data, can lead to severe consequences such as data theft or fraud.
To mitigate these risks, it is important to manage API keys and tokens securely. For instance, public API keys, which are used for accessing public data and typically do not require authentication, must be handled differently from private API keys, which provide access to restricted or sensitive data and are obtained through a registration or approval process.
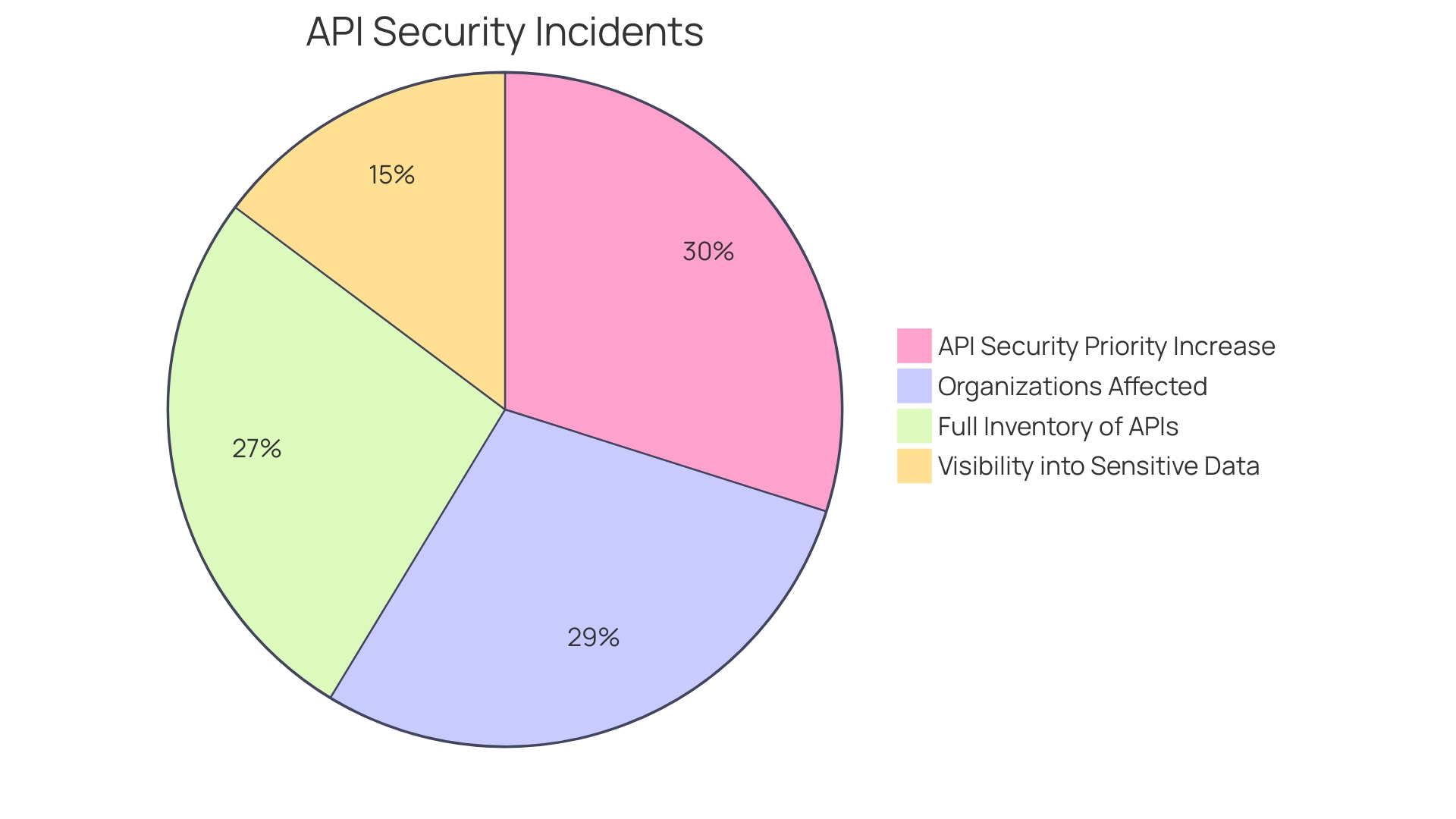
Recent reports indicate that a staggering 78% of cybersecurity teams have encountered an API-related security incident in the past year. Moreover, even though 72% of organizations maintain a full inventory of APIs, only 40% have visibility into which ones return sensitive data. Consequently, the importance of API security has been propelled to the forefront, with 81% of respondents to a cybersecurity survey stating it has become a greater priority over the last 12 months.
In essence, APIs function as an interface between different software applications, akin to how an ATM provides an interface between customers and their bank. Just like the ATM's screen and buttons allow for transactions, APIs enable software interactions that are pivotal for the functionalities we often take for granted in our daily digital experiences.
Why Are API Keys Important?
API keys serve as both a unique identifier and a secret token for authentication, playing an essential role in safeguarding an API from unauthorized access. By implementing API keys, service providers can meticulously monitor who is using their API, ensuring that only legitimate developers and applications have access. This level of control is critical for preventing misuse and potentially malicious activities that could compromise sensitive data.
Here's an example of an API key: eyJhbGciOiJSUzI1NiIsImtpZCI6ImVlODk1OWMzYzFhMDdlMTBlZGJjMDE3NWI2ZmZmN2I1ZGYyOTBiZTIiLCJ0eXAiOiJKV1QifQ.eyJzY29wZSI6.... When decoded, it reveals vital details such as the issuer and the specific API endpoint it's authorized for, further strengthening security by restricting access to intended purposes only.
The significance of API keys is underscored by the alarming rise in API breaches, as reported in recent news. Sensitive data exposure through such breaches can lead to identity theft or fraudulent activities. In response, organizations are prioritizing API security more than ever, with 81% acknowledging its increasing importance over the past year.
In terms of real-world application, developers are encouraged to handle API keys with utmost care. For instance, when updating an App.TSX file in a React project to make requests, the API key should not be hardcoded but stored as an environment variable and excluded from version control to prevent accidental exposure.
Additionally, a robust API security protocol is incomplete without proper training for an organization's employees. This approach is crucial for defending against threats and ensuring that APIs, which are integral to the digital infrastructure and often handle personal information such as contact details and financial data, remain secure.
Recent statistics reflect the critical nature of API security, with 93% of organizations acknowledging the relevance and necessity of APIs. This affirmation is coupled with the integration of APIs and microservices, which 97% agree complement each other, leading to enhanced performance and customer satisfaction.
Overall, effective API key management and security practices are not just technical requirements but form a core part of an organization's defense strategy against data breaches and unauthorized access, thereby preserving the integrity of digital services and user trust.
How to Obtain an API Key
To harness the power of APIs, developers must navigate the initial hurdle of acquiring an API key. This key serves as a unique identifier and an essential component for ensuring secure communication between software applications. The process begins with developers registering on the provider's platform, a step that may entail sharing information and consenting to the provider's terms of service.
Upon successful registration, developers gain access to the provider's portal or API management system, where they can generate their API key. This key is then tethered to the developer's account, enabling them to authenticate their access to the API and manage their requests.
The significance of this process cannot be overstated in the context of modern software development, where APIs are integral to the creation of robust and versatile applications. As Google aptly describes, APIs are the 'crown jewels' of software development, facilitating a seamless exchange between disparate systems and unlocking the potential for greater innovation.
However, the rise in API adoption brings with it an increased risk of security breaches. Reports indicate that a staggering 78% of cybersecurity teams have encountered API-related incidents within the past year. This underscores the imperative for developers to not only secure their API keys but also to remain vigilant about the data their APIs access and exchange.
In a digital environment where APIs are increasingly critical yet susceptible to threats, the onus is on developers to ensure that their integration into applications is executed with precision and protected with robust security measures. Through this meticulous approach, developers can leverage APIs to expand their capabilities and, perhaps, even explore new avenues for generating income through their technical expertise.
Best Practices for Using API Keys
- Protect API keys as if they are personal credentials, ensuring they are never exposed to unauthorized entities. Use system-assigned identities for automated tasks, as demonstrated in the creation of an App Service in Bicep code, which uses the principal ID of the managed identity.
- Regularly rotate API keys to reduce the risk of compromised access, much like changing passwords periodically for security. Remember that deleting code or editing Git history is not enough if keys are exposed; they must be actively managed and reissued.
- Limit the number of requests an entity can make using rate limiting to prevent overuse and potential abuse, similar to how you would manage traffic flow to maintain order.
- Conduct ongoing surveillance of API key activity, akin to monitoring a security feed, to promptly detect and address any abnormal or suspicious patterns that emerge.
- Decommission any API keys that are obsolete or have been jeopardized to prevent them from becoming a liability, as KAYAK did by moving away from passwords to more secure authentication methods with the Credential Manager API and RxJava.
Security Considerations for API Keys
APIs are the backbone of modern software development, enabling applications to interact seamlessly. However, the increased use of APIs has coincided with a surge in security breaches. These breaches can have dire consequences, such as unauthorized access to sensitive data, which can lead to fraudulent activities or identity theft.
Protecting API keys is paramount to safeguarding the security of an API. Encryption is essential when storing or transmitting API keys to prevent them from being intercepted by malicious actors. Secure protocols, notably HTTPS, are critical for API communication, ensuring that data in transit is encrypted and secure from eavesdropping or man-in-the-middle attacks.
Authentication and authorization mechanisms must be robust to verify and define user access, preventing unauthorized use of API functions. Access controls and precise permission settings can significantly limit the reach of API keys, reducing the risk of extensive damage should a breach occur. Additionally, regular audits and monitoring of API key usage can quickly detect and mitigate unauthorized or abnormal activities.
For example, a widely-used open-source library, hosting over 500,000 AI models and datasets, underscores the potential disaster of compromised API security. The repository's API, which allows for the integration of models and management of repositories, became a target for hackers. Following the breach disclosure, the organization and its users implemented swift countermeasures to prevent further damage.
Recent research highlights that 78% of cybersecurity teams have faced an API-related incident in the past year. Despite 72% of organizations maintaining a full inventory of APIs, only 40% have visibility into those that return sensitive data. Consequently, 81% of organizations now prioritize API security more than they did a year ago.
API documentation is likened to a user manual, guiding developers on how to effectively leverage the API. Clarity in documentation, particularly for error codes and statuses, fosters better understanding and troubleshooting capabilities for developers. For instance, the Infobip API reference provides links to commonly misunderstood concepts, aiding developers, especially beginners, in overcoming learning barriers.
In conclusion, vigilance in API security is not merely a precaution but a necessity. As digital infrastructures continue to rely on APIs, the implementation of robust security protocols and monitoring practices is non-negotiable to protect sensitive data and maintain the integrity of digital systems.
Common Uses of API Keys
API keys serve as critical instruments for developers, enabling a multitude of functionalities essential for modern software. They play a pivotal role in integrating third-party services, allowing applications to extend their capabilities by leveraging external APIs. For instance, they can authenticate user actions, manage access permissions, and track API usage to ensure secure and efficient operations.
To illustrate, consider a JSON Web Token (JWT), which encapsulates key details like the issuing authority, the intended API endpoint, and the token's validity period. An example JWT might look like this: eyJhbGciOiJSUzI1NiIsImtpZCI6... and upon decoding, it reveals a payload with crucial information such as the scope and expiration time.
In practice, the implementation of API keys is straightforward yet secure. For example, in a React project, developers can store the API gateway URL in an environment variable within a .env.local file, which is excluded from version control for security purposes. Subsequently, they can update components like App.TSX to fetch data from an API endpoint, thereby integrating the API's functionality into the application with a simple button click.
However, the ubiquity of APIs has also attracted the attention of cybercriminals, leading to an increase in API-related security incidents. A staggering 78% of cybersecurity teams have experienced an API security breach in the past year, according to a recent report. This highlights the critical need for robust API security measures, with only 40% of organizations having visibility into which APIs return sensitive data.
With APIs becoming increasingly integral to digital transformation, their importance is undeniable. They are the communicative bridge between different software components, likened to an ATM interface for banks or Google's 'crown jewel of software development.' As modern software relies heavily on the interconnectivity APIs provide, it's essential for developers to ensure their APIs are both functional and secure.
Statistics reinforce this importance, with research showing that 93% of organizations recognize APIs as crucial to their operations. Moreover, 97% of respondents acknowledge the complementary nature of APIs and microservices, suggesting that integrated approaches can lead to improved customer satisfaction and productivity.
Overall, API keys not only facilitate the expansion of application features but also underscore the significance of security and strategic integration in the digital landscape.
Troubleshooting Common Issues with API Keys
- When an API key becomes invalid or expires, developers should verify the key's status in their account settings and regenerate a new key if required.
- To tackle rate limiting issues, consider optimizing request patterns or discussing a limit increase with the API provider, as demonstrated by the 429 Too Many Requests error encountered due to breaching the 100 requests per minute limit in a real-world case.
- In the event of unauthorized access, immediate revocation of the compromised API key and a thorough security investigation are crucial.
- Integration difficulties might necessitate a review of the current implementation and seeking guidance from API documentation or support forums.
Resolving these issues is pivotal for the seamless operation of applications dependent on API keys.
References/Citations
Understanding and securing API keys is crucial for safeguarding the digital infrastructure of any software utilizing APIs. API keys are akin to secret passphrases that grant access to API functions, and they need to be protected just as diligently as one would guard the keys to a treasure chest.
To illustrate the importance of robust API key security, consider the case of an open-source library with over half a million AI models and datasets. A security breach in such a repository could have dire consequences, potentially allowing malicious actors to manipulate models and undermine the integrity of countless downloads. This scenario underscores the necessity of implementing stringent security measures and constantly reviewing API key usage to prevent unauthorized access.
Comprehending the mechanics of API keys involves understanding JSON Web Tokens (JWT), which are a secure method of representing claims between two parties. JWT consists of three parts: a header specifying the token type and signing algorithm, a payload containing the claims and additional data, and a signature to ensure the token's integrity. Grasping these fundamentals is essential for developers to securely manage authentication processes.
It is equally important for developers to familiarize themselves with tools like Postman, which function as the Swiss Army knives of API development, providing a platform for building, testing, and sharing APIs. Mastery of such tools, coupled with an in-depth understanding of API keys, can greatly enhance the security and efficiency of any development environment.
As we delve into the realm of APIs, remember that these interfaces are the lifeblood of modern software, enabling seamless interactions between applications. They are the unsung heroes of the tech world, much like translators facilitating dialogue between two distinct languages. With APIs' growing significance in fostering innovation and collaboration across industries, safeguarding API keys is not just a technical necessity but a foundational aspect of sustaining the digital ecosystem.
Conclusion
API keys are crucial for secure communication and access management in the digital landscape. They serve as unique identifiers, ensuring that only verified developers can interact with APIs and maintain system integrity. However, the rise in API breaches highlights the need for robust security measures.
Recent statistics reveal that 78% of cybersecurity teams have encountered API-related security incidents, emphasizing the importance of API key protection. To mitigate risks, it is crucial to distinguish between API keys and tokens, manage them securely, and implement best practices.
API keys streamline and secure interactions between applications and APIs. They authenticate users, manage access permissions, and protect sensitive data. Best practices include protecting API keys as personal credentials, regularly rotating them, and limiting the number of requests.
The significance of API keys is further underscored by the alarming rise in API breaches. Encryption and secure protocols are essential for protecting API keys from unauthorized access. Robust authentication, authorization mechanisms, and ongoing monitoring help detect and address abnormal activities.
Obtaining an API key involves registering on the provider's platform and generating a key tied to the developer's account. This process ensures secure communication between software applications and enables developers to leverage the power of APIs.
API keys play a critical role in modern software development, facilitating the integration of third-party services, authenticating user actions, and tracking API usage. As APIs become integral to digital transformation, prioritizing their security and strategic integration is vital.
In conclusion, effective API key management and security practices are fundamental for protecting sensitive data, maintaining system integrity, and enhancing application efficiency. By implementing proper API key protection and following best practices, developers can ensure secure and efficient operations in the dynamic digital landscape.
Frequently Asked Questions
What is an API Key?
An API key is a unique identifier that acts as both a gatekeeper and facilitator for accessing an API's functionalities, ensuring that only verified developers can make requests.
How do API Keys work?
API keys authenticate and grant access to an API, determining the level of access for each request. They ensure that only authorized users can engage with the API services, protecting the API's resources.
What are the different types of API Keys?
API keys are static and unique identifiers for user or application authentication. Tokens, on the other hand, are dynamic, represent user sessions or privileges, and are used for a limited time.
Why are API Keys important?
API keys are crucial for monitoring API usage and preventing misuse. They authenticate legitimate developers and applications, helping to safeguard sensitive data from unauthorized access.
How can I obtain an API Key?
Obtaining an API key involves registering on the provider's platform and generating the key through their portal or API management system.
What are the best practices for using API Keys?
Best practices include treating API keys as personal credentials, regularly rotating them, using rate limiting, monitoring key activity, and decommissioning compromised keys.
What are the security considerations for API Keys?
Encryption of API keys during storage and transmission is essential, as well as implementing HTTPS for secure communication. Robust authentication, access controls, and regular monitoring are necessary to prevent breaches.
What are the common uses for API Keys?
API keys enable integrating third-party services, authenticating user actions, managing access permissions, and tracking API usage for secure and efficient operations.
How do I troubleshoot common issues with API Keys?
Common troubleshooting steps include verifying the key's status and regenerating it if necessary, optimizing request patterns to handle rate limiting, revoking compromised keys, and reviewing implementation against API documentation.
Why has API security become a greater priority in recent times?
With a surge in API-related security incidents and breaches, organizations recognize the need to protect sensitive data and maintain the integrity of digital systems, making API security a top concern.
What is the significance of API documentation?
API documentation is a roadmap that details endpoints, methods, and parameters, providing clarity and security, and ensuring developers are informed and engaged.
How can API Keys be compromised?
API keys can be compromised through unauthorized access, password leaks, attacks, or inadvertent exposure in code repositories, leading to potential data breaches or fraud.
What should I do if my API Key is exposed?
If an API key is exposed, it should be immediately revoked and replaced, and a security audit should be conducted to assess the impact and prevent further unauthorized access.




