Overview
The article highlights the significant challenges developers face in coding, particularly regarding security vulnerabilities. It presents four strategies for effectively integrating security analysis software into the software development lifecycle (SDLC). By embedding security practices early in development, utilizing automated tools for continuous assessment, training development teams, and establishing clear protocols, developers can enhance overall code security and significantly reduce vulnerabilities.
Furthermore, Kodezi addresses these challenges by providing specific features that streamline the integration of security analysis. The platform not only improves productivity but also enhances code quality. By using Kodezi, developers can ensure that their coding practices are more secure and efficient.
In addition, the benefits of employing Kodezi are clear:
- Improved productivity
- Enhanced code quality
- A more secure development process
This makes it an invaluable tool for developers looking to strengthen their coding practices.
Are you ready to explore the tools available on Kodezi? By leveraging these strategies and features, you can take significant steps toward a more secure and efficient coding environment.
Introduction
In an age where software development faces significant challenges, the importance of security analysis software cannot be overstated. As organizations navigate an ever-evolving threat landscape, robust tools to identify vulnerabilities and ensure compliance have become essential. Did you know that 50% of internal application vulnerabilities are classified as high or critical risks? This statistic underscores the urgency for proactive security measures.
By integrating security analysis into the development lifecycle and leveraging automated tools, companies not only mitigate risks but also enhance code quality and maintain user trust. This article explores how Kodezi addresses these challenges, empowering development teams to fortify their applications against potential breaches and ensuring a secure, resilient software environment.
Understand Security Analysis Software and Its Importance
In today's software development landscape, security analysis software is indispensable for developers facing numerous coding challenges. These tools play a vital role in detecting weaknesses, ensuring compliance, and maintaining code integrity. By identifying potential vulnerabilities early in the development lifecycle, developers can avoid costly breaches and protect user trust. Notably, recent statistics reveal that 50% of internal application vulnerabilities are classified as high or critical risks, underscoring the pressing need for effective protective measures. Furthermore, the average cost of a data breach has surged by $137,000 due to the rise in remote work, making proactive safety evaluations even more essential.
When evaluating protection software, it’s crucial to prioritize features such as:
- Both static and dynamic examination capabilities
- Seamless integration with CI/CD pipelines
- Comprehensive reporting functionalities
For instance, organizations with compromised cloud accounts can face an annual average loss of $6.2 million, with 86% of them reporting significant financial setbacks from breaches. This stark reality emphasizes the importance of implementing robust access controls and protective measures, and by leveraging security analysis software such as Kodezi, development teams can proactively address safety concerns. Kodezi offers automated debugging that not only identifies and resolves issues within the codebase but also enhances quality and ensures compliance with the latest safety best practices. It effectively tackles performance bottlenecks, detects vulnerabilities, adds exception handling, and improves code formatting in just seconds. This proactive approach empowers teams to mitigate vulnerabilities and develop more secure applications, and as the software development landscape evolves, the integration of security analysis software remains a fundamental aspect of successful and secure coding practices. Are you ready to explore the tools available on the Kodezi platform and elevate your coding standards?
Implement Best Practices for Effective Security Analysis
To implement effective protection analysis, organizations should adopt the following best practices:
- Conduct Regular Risk Evaluations: Regular assessments are essential to identify weaknesses and ensure adherence to safety standards. Statistics indicate that companies perform network vulnerability scans on a weekly, monthly, quarterly, biannual, or annual basis, underscoring the necessity of these evaluations.
- Integrate Protection into Development Processes: By embedding protective practices within the software development lifecycle (SDLC), organizations can catch issues early. Effective integration has shown that organizations can significantly reduce the average duration to identify a breach from weeks to days, thereby improving their defensive posture through the use of security analysis software. Utilizing automated protection evaluation tools, such as Kodezi, enhances the detection of weaknesses and minimizes manual errors. Kodezi's AI-driven features allow for automatic code correction, bug evaluation, and the creation of comments on code. This not only enhances efficiency but also ensures that vulnerabilities are identified in real-time, facilitating quicker remediation. Furthermore, Kodezi supports over 30 programming languages and is compatible with Visual Studio Code, making it a versatile choice for developers.
- Train Development Teams: Ongoing training for developers on safe coding practices and the use of protection analysis tools is crucial. Continuous education enables teams to proactively identify and address safety concerns.
- Establish Clear Protocols: Developing and documenting protocols for responding to identified vulnerabilities ensures a swift and effective response. Consistently assessing automated policies improves resilience against new threats, making it essential for organizations to remain vigilant in their protective measures.
Integrate Security Analysis into the Software Development Lifecycle
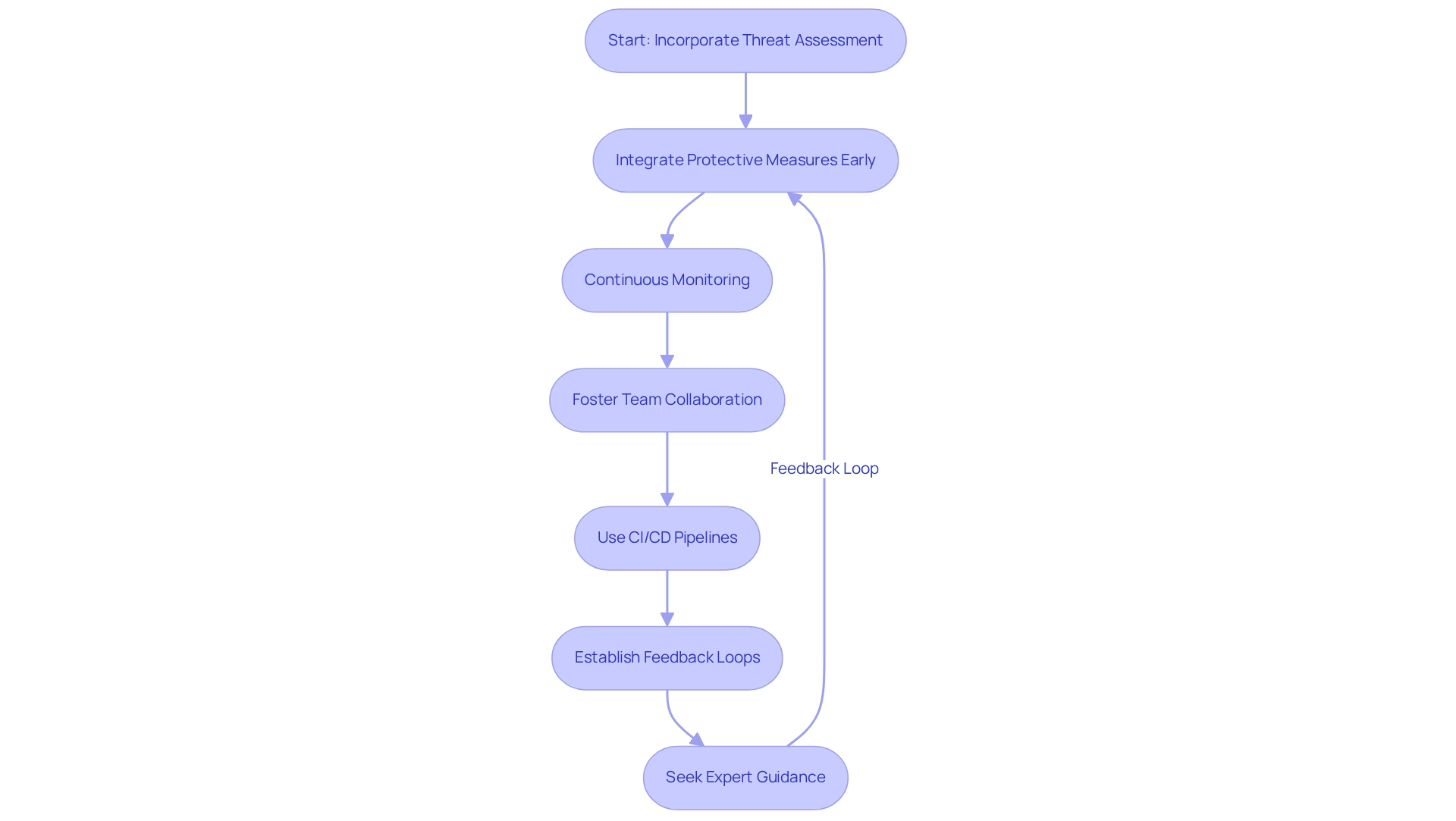
Incorporating threat assessment into the software development lifecycle (SDLC) is essential for enhancing software protection and resilience. By starting to include protective measures early in the development process, beginning from the requirements phase, teams can proactively identify potential weaknesses before they become embedded in the code. Continuous monitoring throughout the development lifecycle enables teams to recognize and address vulnerabilities in real-time, ensuring that protection is maintained as the code evolves.
Furthermore, fostering collaboration among development, safety, and operations teams is crucial. When safety considerations are integrated into every decision, organizations can cultivate a culture of shared responsibility for protection. The use of CI/CD pipelines is another key strategy; by integrating safety analysis tools into these pipelines, organizations can automate safety checks, ensuring that code is secure before deployment. This significantly reduces the risk of vulnerabilities in production environments. In fact, 96% of organizations reported that they would benefit from automating safety and compliance processes.
In addition, establishing feedback loops to learn from incidents is vital. Continuous enhancement of protection methods allows teams to adapt and refine their strategies based on real-world experiences. A case study on the advantages of DevSecOps implementation revealed that 54% of participants cited improved protection, quality, and resilience as their primary motivations for adopting these practices. By implementing these strategies, organizations can effectively integrate risk analysis and security analysis software into their SDLC, thereby addressing the skill gap in protection and enhancing their overall software safety posture. Seeking expert guidance in executing a Secure Software Development Lifecycle (SSDLC) can further strengthen these efforts, ensuring that organizations are well-equipped to navigate the complexities of software protection.
Leverage Automation to Enhance Code Security
To effectively improve program protection through automation, consider the following strategies: Many developers face significant challenges in ensuring code security, which can be addressed by using security analysis software amid rapid development cycles.
- Automated Code Evaluations offer a solution. Incorporate security analysis software like Kodezi that performs automatic assessments of software for vulnerabilities during the development lifecycle. Kodezi's AI-assisted development tool not only identifies and fixes codebase issues but also provides detailed explanations of what went wrong and how to resolve it. While security analysis software can significantly enhance the detection of potential vulnerabilities through automated evaluations, it is important to note that they should not substitute human supervision, as emphasized in recent studies.
- Continuous Integration and Deployment (CI/CD) is another critical strategy. Utilize CI/CD tools along with security analysis software to automate testing for vulnerabilities, ensuring that every code modification undergoes rigorous assessments. Kodezi integrates seamlessly into CI/CD workflows, enhancing the overall effectiveness of the testing process by providing rapid issue resolution and performance optimization.
- Furthermore, consider Protection Orchestration. Utilize protection orchestration tools to automate incident response and streamline operations. This integration of security analysis software enables a more unified protection strategy, which decreases response times and enhances the overall defense posture.
- In addition, Regular Updates and Patching are essential. Use security analysis software to automate the updating of dependencies and the patching of known vulnerabilities. Kodezi guarantees that your codebase adheres to the most recent protection best practices and coding standards, enhancing this proactive approach even further.
- Integrate AI and Machine Learning to further bolster your defenses. Utilize AI-powered tools such as Kodezi to examine programming patterns and identify anomalies, thus improving the ability to recognize potential vulnerabilities. Expert opinions suggest that these technologies can complement automated reviews, providing deeper insights into code behavior and vulnerabilities.
By implementing these strategies, organizations can significantly bolster their code security practices with the help of security analysis software. This ensures a robust defense against vulnerabilities while maintaining high productivity levels. Are you ready to explore the tools available on the Kodezi platform to enhance your coding practices?
Conclusion
In today’s rapidly evolving software landscape, the need for robust security analysis software is not merely a necessity; it is a critical component of effective development practices. The alarming statistics regarding internal application vulnerabilities underscore the urgency for organizations to adopt proactive security measures. By integrating tools like Kodezi into the development lifecycle, companies can effectively identify and mitigate risks early, while also enhancing the overall quality of their code.
Adopting best practices such as:
- Regular security assessments
- Embedding security within software development processes
- Leveraging automation
are essential steps for organizations striving to maintain a robust security posture. Furthermore, continuous training for development teams and the establishment of clear protocols for addressing vulnerabilities solidify these efforts. This ensures that security becomes a shared responsibility across all levels of the organization.
As the threat landscape continues to evolve, integrating security analysis into the software development lifecycle remains paramount. Organizations that prioritize security through the use of effective tools and practices not only protect their applications but also build trust with users. Ultimately, this leads to a more resilient software environment. The time to act is now; embracing these strategies will pave the way for a secure and trustworthy digital future.
Frequently Asked Questions
Why is security analysis software important for developers?
Security analysis software is essential for developers as it helps detect weaknesses, ensures compliance, and maintains code integrity. By identifying potential vulnerabilities early in the development lifecycle, it allows developers to avoid costly breaches and protect user trust.
What are the statistics related to internal application vulnerabilities?
Recent statistics indicate that 50% of internal application vulnerabilities are classified as high or critical risks, highlighting the urgent need for effective protective measures.
How has the cost of data breaches changed recently?
The average cost of a data breach has increased by $137,000, largely due to the rise in remote work, making proactive safety evaluations more critical than ever.
What features should be prioritized when evaluating security analysis software?
Key features to prioritize include both static and dynamic examination capabilities, seamless integration with CI/CD pipelines, and comprehensive reporting functionalities.
What are the financial implications of compromised cloud accounts?
Organizations with compromised cloud accounts can face an annual average loss of $6.2 million, with 86% reporting significant financial setbacks from breaches.
How does Kodezi enhance the software development process?
Kodezi enhances the development process by offering automated debugging that identifies and resolves issues within the codebase, improves quality, and ensures compliance with safety best practices. It also tackles performance bottlenecks, detects vulnerabilities, adds exception handling, and improves code formatting quickly.
What is the overall impact of integrating security analysis software in coding practices?
Integrating security analysis software is fundamental for successful and secure coding practices, empowering development teams to proactively address safety concerns and develop more secure applications.




