Overview
In today's digital landscape, developers face significant challenges in ensuring software security. The article outlines four effective strategies for software security analysis:
- Threat modeling
- Static evaluation
- Dynamic evaluation
- Code reviews
- Penetration testing
These methodologies are crucial for identifying vulnerabilities and improving code quality. Furthermore, they ensure compliance by providing structured approaches to proactively address security risks. By implementing these strategies, developers can enhance the overall protection of their software applications, ultimately leading to greater peace of mind and improved productivity.
Introduction
In an age where digital threats loom larger than ever, the significance of software security analysis has reached unprecedented heights. As organizations increasingly depend on technology, the vulnerabilities within software systems can result in severe outcomes, including data breaches and financial losses. With scams surging by 400% since early 2020, the urgency for robust security measures has never been more evident.
This article explores the essential processes of software security analysis, emphasizing effective methodologies, the role of automation tools, and the necessity of continuous monitoring. By adopting these practices, developers not only safeguard sensitive information but also elevate the overall quality and reliability of their software, paving the way for a more secure digital landscape.
Understand Software Security Analysis and Its Importance
Software security analysis is a vital process that evaluates software systems to identify and mitigate potential vulnerabilities. The significance of this method cannot be overstated; vulnerabilities can lead to data breaches, erode user trust, and result in substantial financial losses. Since March 2020, scams have surged by 400%, emphasizing the urgent need for robust protective measures. By prioritizing software security analysis, developers can adopt secure coding practices and seamlessly integrate protection into the software development lifecycle. This proactive approach not only safeguards sensitive information but also enhances the overall quality and reliability of software products. A case study involving HD Supply illustrates the importance of governance, risk, and compliance (GRC) in aligning protective strategies with regulatory requirements and best practices. As Corey Reed, Senior Director of Information Protection, points out, effective GRC frameworks are essential for organizations navigating the complex protective landscape.
Furthermore, recent statistics reveal that 43% of spoofing attacks impersonated Microsoft, showcasing the sophisticated tactics employed by cybercriminals. With 3.5 million unfilled cybersecurity positions worldwide in 2023, the demand for skilled professionals in this field is more urgent than ever. By implementing program protection evaluation, development teams can not only secure their applications but also contribute to a more secure digital environment, ultimately fostering business success.
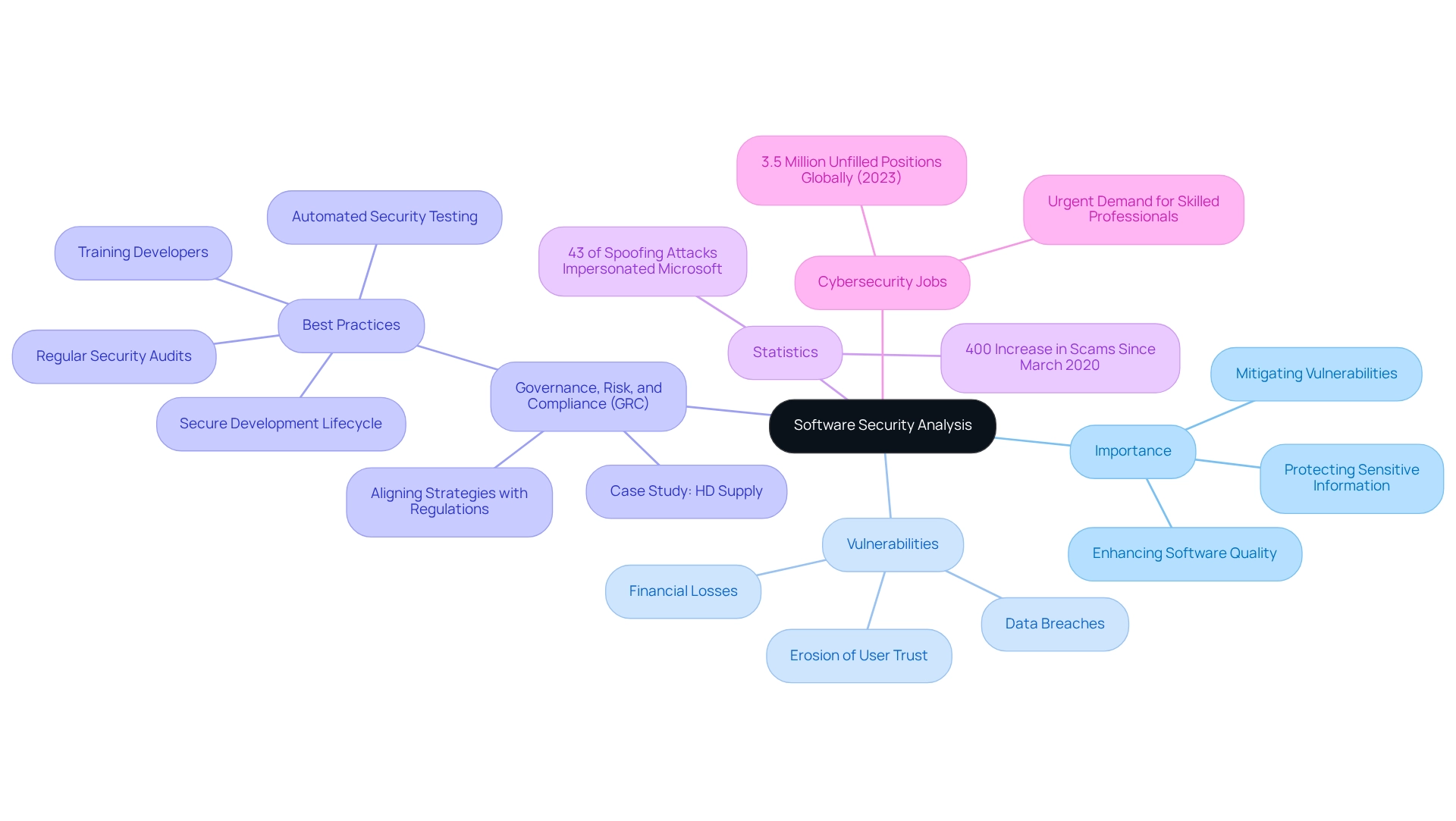
Implement Effective Methodologies for Software Security Analysis
In the realm of software development, coding challenges can often impede progress. To perform efficient software security analysis, developers should apply several key methodologies that not only address these challenges but also enhance overall security.
- Threat Modeling is a crucial first step. This involves identifying potential threats to the software and assessing their impact and likelihood. By prioritizing risk in software security analysis, teams can allocate resources more effectively. Recent insights indicate that organizations adopting threat modeling practices have seen significant improvements in early issue detection, minimizing wasted engineering time.
- Furthermore, employing Static and Dynamic Evaluation is essential. Static evaluation tools inspect code for vulnerabilities without executing it, while dynamic evaluation tools assess the software in an active state. Both approaches provide distinct perspectives on protection, with static evaluation focusing on code structure and dynamic assessment examining runtime behavior. Statistics indicate that incorporating software security analysis into the development workflow can improve automated code reviews, resulting in more secure applications. Kodezi's automated code debugging feature enhances these analyses by enabling developers to swiftly detect and address codebase problems, ensuring adherence to the latest safety best practices and coding standards.
- In addition, Code Reviews play a vital role. Regular peer evaluations of code are crucial for identifying vulnerabilities and ensuring compliance with safe coding standards. This cooperative method not only enhances code quality but also cultivates a culture of safety within the team, emphasizing the significance of collective accountability in preserving system integrity. Kodezi enhances this process by providing detailed insights into code issues, enabling rapid resolution and performance optimization.
- Lastly, Penetration Testing is an invaluable practice. Simulating attacks on the application helps identify vulnerabilities that could be exploited by malicious actors. This practical approach offers a real-world viewpoint on vulnerabilities, enabling teams to tackle problems proactively through software security analysis. By embracing these methodologies, along with tools like Kodezi that support automated testing and code improvement, developers can create a robust framework for efficient software security analysis to identify and resolve vulnerabilities. This ultimately leads to an improved overall protection stance of their applications, fostering a safer development environment.
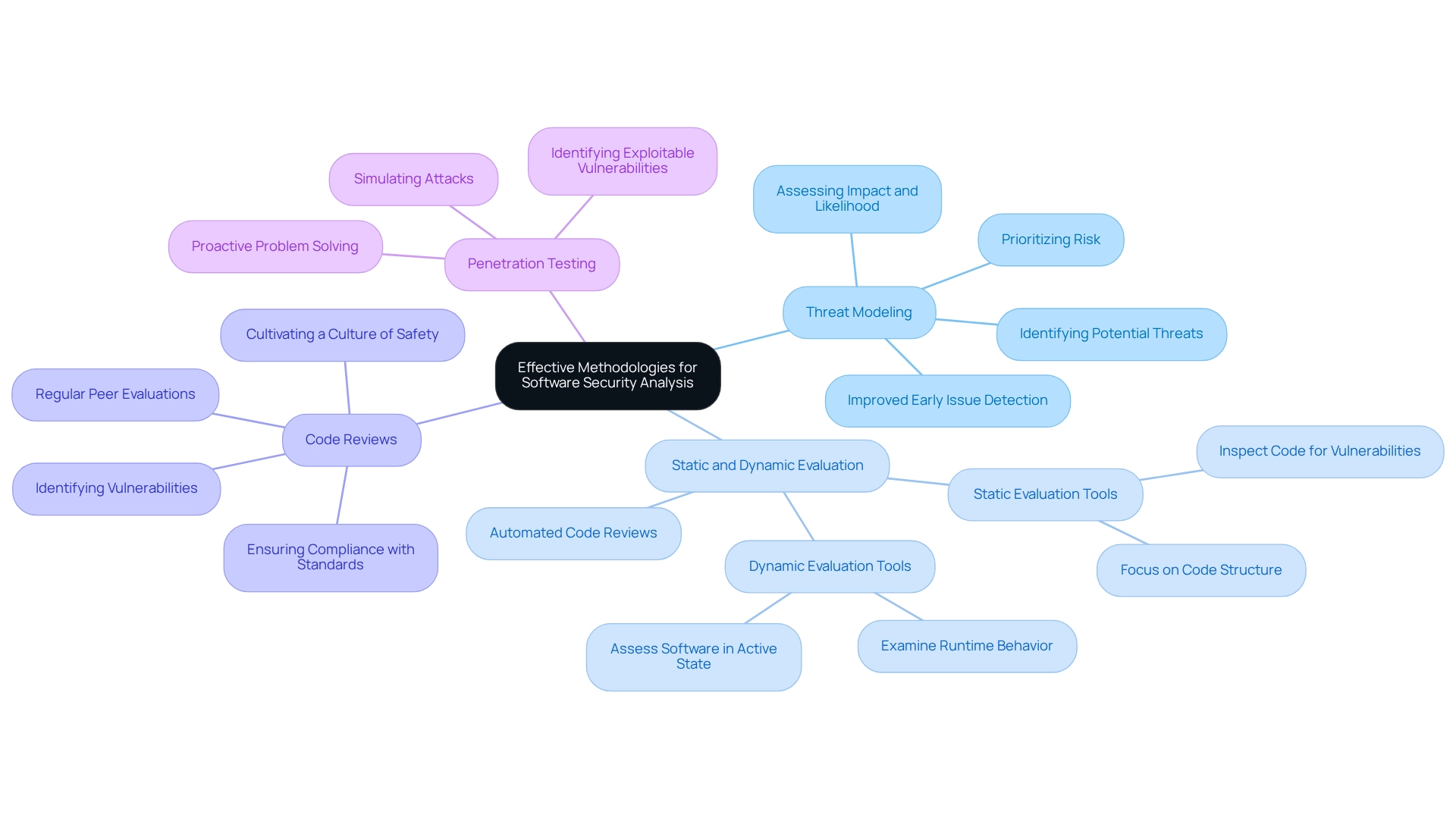
Leverage Automation Tools for Enhanced Security Analysis
In today's rapidly evolving software landscape, developers face significant challenges in performing software security analysis to ensure the security of their code. Automation tools are essential for enhancing software security analysis by effectively addressing these challenges.
Identifying Vulnerabilities: Tools such as Snyk and Veracode automatically examine codebases for known vulnerabilities, providing prompt feedback to developers regarding potential threats. This proactive approach is crucial, especially considering that unpatched vulnerabilities were involved in 60% of data breaches, underscoring the need for timely remediation.
Continuous Integration/Continuous Deployment (CI/CD): By incorporating protective tools into CI/CD pipelines, developers can enable automatic checks throughout the development lifecycle. This integration helps catch issues early, significantly reducing the risk of vulnerabilities making it into production. Kodezi enhances this process with its CLI, allowing for seamless integration and automated code debugging, which helps maintain code quality and resolve issues rapidly.
Reporting and Analytics: Automation tools generate detailed reports on vulnerabilities, enabling teams to track weaknesses over time and evaluate the effectiveness of their protective measures. Kodezi's automated debugging feature provides insights into codebase issues, offering detailed explanations that facilitate understanding and efficient problem resolution.
Compliance Checks: These tools also facilitate automated compliance assessments against industry standards, ensuring that applications adhere to necessary regulations and optimal practices. With 83% of IT SME professionals requiring multi-factor authentication, compliance automation becomes increasingly important. Kodezi ensures that codebases comply with the most recent safety guidelines and coding standards, further supporting compliance initiatives, while facilitating software security analysis. By utilizing automation tools like Kodezi, developers can simplify their software security analysis procedures, reduce manual effort, and significantly improve overall application protection. As the cybersecurity market is projected to reach $212 billion by the end of 2025, adopting such tools will be critical for organizations aiming to safeguard their digital assets.
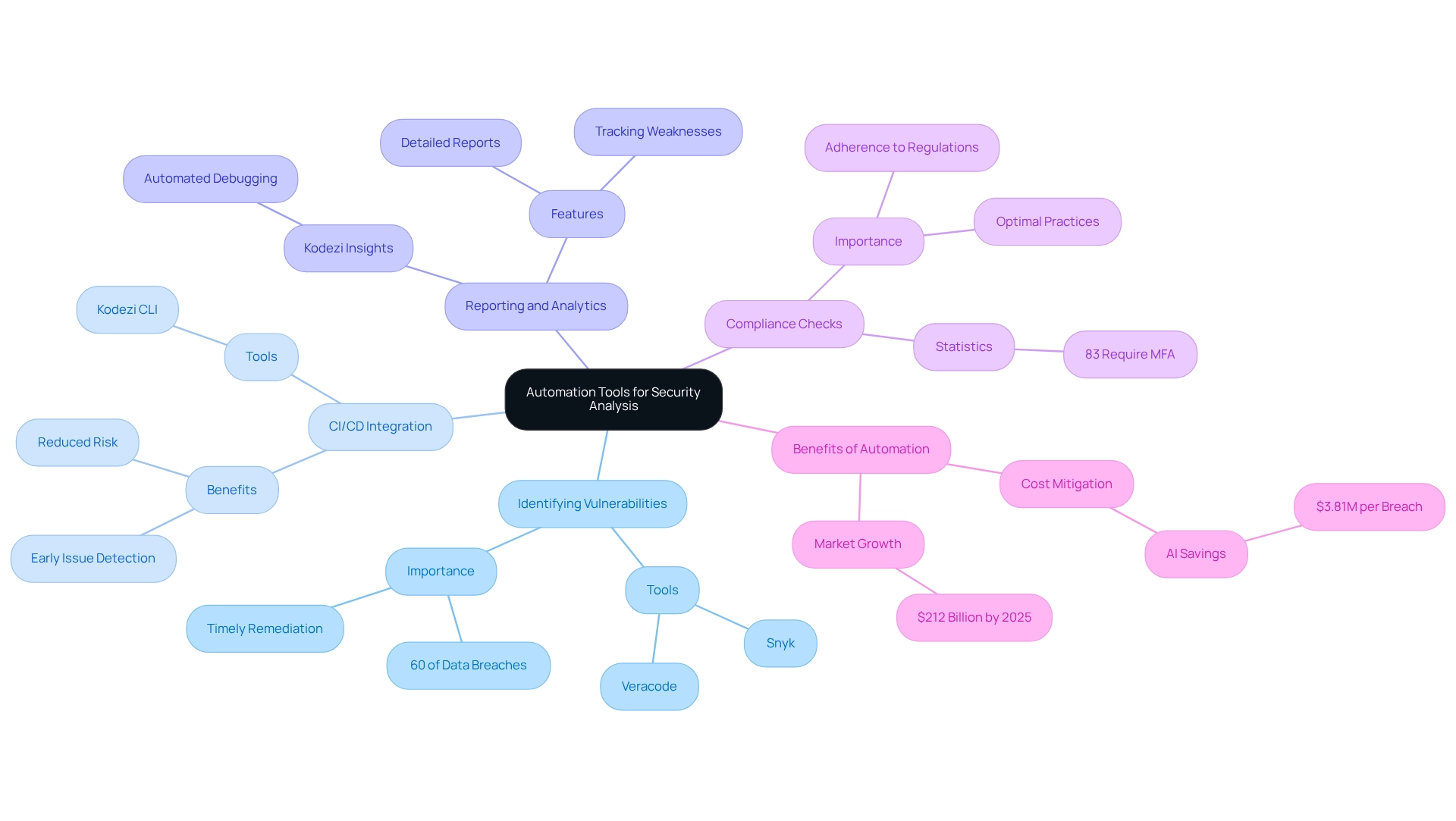
Adopt Continuous Monitoring and Improvement Practices
To ensure ongoing software protection, developers face significant challenges that require proactive strategies in software security analysis. Continuous monitoring and enhancement methods are essential in software security analysis to address these challenges effectively.
- Routine Security Assessments: Regular evaluations of the codebase and safety protocols through software security analysis are crucial for identifying areas for improvement and ensuring compliance with safety standards. Implementing tools for real-time monitoring of applications is a crucial aspect of software security analysis, allowing teams to detect suspicious activities and respond promptly to potential threats.
- Feedback Loops: Establishing feedback systems enables developers to report concerns and share insights regarding vulnerabilities encountered in production environments.
- Training and Awareness: Regular training sessions for development teams on the latest security threats and best practices foster a culture of security awareness within the organization.
By committing to continuous monitoring and improvement, development teams can adapt to the evolving security landscape and maintain high standards of software security analysis.
Conclusion
In today’s digital landscape, the significance of software security analysis is paramount. As organizations confront escalating threats, the implementation of robust security measures is crucial for safeguarding sensitive information and preserving user trust. Effective methodologies, including threat modeling, static and dynamic analysis, code reviews, and penetration testing, empower developers to proactively identify and mitigate vulnerabilities before they result in substantial breaches or financial setbacks.
Furthermore, automation tools are integral to enhancing security analysis processes. By incorporating tools like Snyk and Veracode into development workflows, teams can swiftly identify vulnerabilities, perform compliance checks, and generate insightful reports. This integration ensures that security remains a priority throughout the software lifecycle. The adoption of Continuous Integration and Continuous Deployment (CI/CD) practices further strengthens these initiatives, facilitating early detection and remediation of potential risks.
In addition, continuous monitoring and improvement are essential for adapting to the ever-evolving threat landscape. Regular security audits, real-time monitoring, and ongoing training for development teams cultivate a culture of security awareness, enabling organizations to respond promptly to emerging threats. By committing to these practices, developers not only bolster the security of their applications but also contribute to a safer digital environment for all. Ultimately, prioritizing software security analysis transcends mere compliance; it embodies a commitment to resilience and the safeguarding of technology's future.
Frequently Asked Questions
What is software security analysis?
Software security analysis is a process that evaluates software systems to identify and mitigate potential vulnerabilities, ensuring the protection of sensitive information and enhancing software quality.
Why is software security analysis important?
It is crucial because vulnerabilities can lead to data breaches, erode user trust, and result in significant financial losses. The surge in scams by 400% since March 2020 highlights the urgent need for robust protective measures.
How can developers implement software security analysis?
Developers can adopt secure coding practices and integrate protection into the software development lifecycle to prioritize software security analysis.
What role does governance, risk, and compliance (GRC) play in software security?
GRC is essential for aligning protective strategies with regulatory requirements and best practices, helping organizations navigate the complex protective landscape.
What statistics illustrate the current cybersecurity threat landscape?
Recent statistics show that 43% of spoofing attacks impersonated Microsoft, indicating the sophisticated tactics used by cybercriminals.
What is the current demand for cybersecurity professionals?
As of 2023, there are 3.5 million unfilled cybersecurity positions worldwide, highlighting the urgent need for skilled professionals in the field.
How does program protection evaluation contribute to cybersecurity?
By implementing program protection evaluation, development teams can secure their applications and contribute to a more secure digital environment, fostering business success.




