Overview
Best practices for secure code analysis include systematic strategies that prioritize safety throughout the software development lifecycle, such as utilizing checklists like the OWASP Top Ten and leveraging automated tools for vulnerability detection. The article emphasizes that these practices not only enhance code quality and maintainability but also significantly reduce the risk of security breaches and compliance issues, underlining the importance of a proactive approach in safeguarding applications against cyber threats.
Introduction
In an age where cyber threats loom larger than ever, the integrity of software applications is paramount. Secure code analysis emerges as a vital practice, empowering developers to uncover vulnerabilities before they can be exploited.
By systematically scrutinizing code, organizations can not only enhance their security posture but also improve overall code quality and maintainability. The integration of automated tools, such as Kodezi, streamlines the process, allowing teams to focus on high-risk areas while minimizing human error.
As cyberattacks become increasingly sophisticated, adopting a proactive approach to secure coding is not just beneficial; it is essential for safeguarding sensitive data and maintaining compliance in a rapidly evolving digital landscape.
With the stakes so high, understanding the importance of secure code analysis and best practices is crucial for any organization aiming to thrive in today’s tech-driven world.
Understanding Secure Code Analysis: Importance and Benefits
Secure code analysis is an essential practice for detecting and addressing security vulnerabilities within software applications. By methodically reviewing and scrutinizing programs, developers can identify weaknesses that could expose applications to cyber threats. Automated debugging plays a crucial role here, enabling instant identification and resolution of issues in the codebase while providing detailed insights into fixes.
This process involves:
- Improving formatting
- Adding exception handling
- Addressing performance bottlenecks
These actions significantly contribute to overall quality and maintainability. The benefits of reliable program analysis are significant: it not only strengthens the protective stance of software but also improves overall quality and maintainability. Additionally, incorporating reliable program analysis into the development lifecycle can result in substantial cost reductions by identifying issues early, thus reducing the risk of costly breaches and compliance fines in the future.
Research indicates that organizations prioritizing safe coding practices experience notably fewer security breaches, highlighting the profound benefits of a proactive strategy. With 43% of cyberattacks aimed at small businesses—yet only 14% feeling sufficiently ready—implementing secure code analysis is not just advantageous but essential for protecting against potential threats. Particularly concerning is the 8% rise in critical weaknesses among applications processing payment card data, underscoring the importance of secure coding.
A case study titled 'Enterprise Cybersecurity Statistics' reveals that cybercriminals can penetrate 93% of company networks, emphasizing the vulnerabilities faced by small and medium-sized enterprises (SMEs). As emphasized in the most recent Internet Crime Report, BEC (Business Email Compromise) attacks resulted in an astonishing $2.9 billion in losses in 2023, underscoring the essential requirement for strong protective measures in software development.
Optimal techniques for application protection involve:
- Performing regular assessments
- Keeping informed about the latest trends and threats
- Adopting a reliable development lifecycle
- Educating developers in safe coding practices
- Utilizing automated tools for testing
For example, automated debugging can not only detect weaknesses but also improve performance by simplifying execution paths, ultimately enhancing quality and adherence to best practices.
Best Practices for Conducting Effective Secure Code Reviews
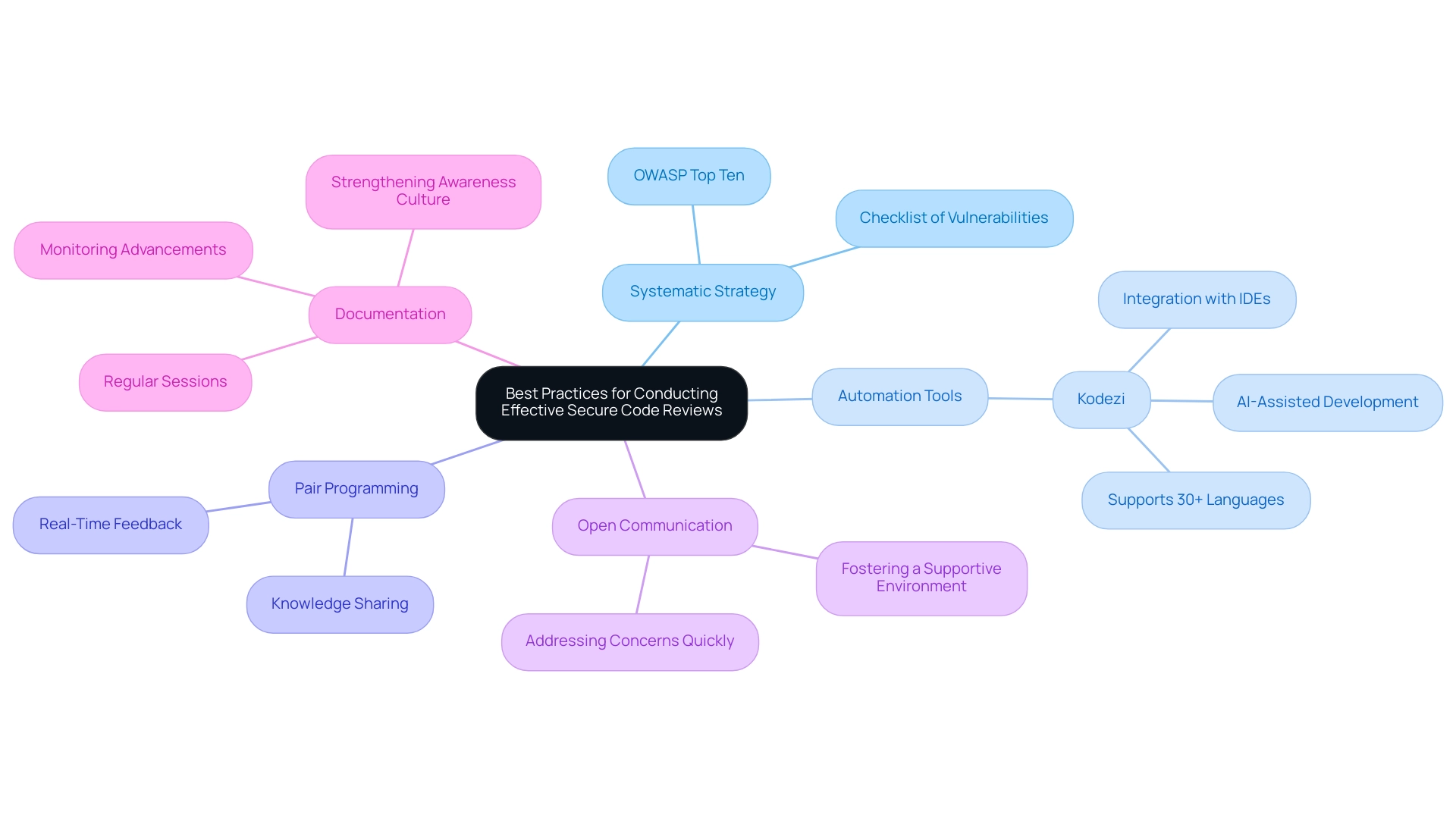
To execute effective secure code analysis in 2024, developers must implement a systematic strategy that prioritizes safety at every stage of the software development lifecycle. A foundational step is to utilize a detailed checklist of prevalent vulnerabilities, prominently featuring the OWASP Top Ten, which is invaluable in guiding teams through common pitfalls while ensuring comprehensive coverage of critical vulnerabilities relevant to their application domain. With fines for breaches of EU privacy law spiking sevenfold to $1.2 billion, the financial implications of insufficient protective measures cannot be overlooked.
Automation tools like Kodezi can significantly enhance this process by streamlining repetitive tasks, analyzing bugs, and allowing developers to concentrate on high-risk areas that demand human oversight and expertise. Kodezi’s AI-assisted development tool functions as an autocorrect for programming, automatically resolving issues and generating comments, which further contributes to improving safety practices. Kodezi supports over 30 programming languages and is presently compatible with Visual Studio Code (Vscode), with intentions to support additional IDEs in the future.
Pair programming stands out as a best practice, fostering real-time feedback and enhancing knowledge sharing among team members, which can lead to more robust protection outcomes. As mentioned by Braz and Bacchelli, reviewers must have a profound comprehension of protective knowledge, emphasizing the proficiency required in secure code analysis. Regularly scheduled secure code analysis sessions are essential to reinforce safety as a primary focus, rather than treating it as an afterthought.
Furthermore, encouraging open communication within the team creates an atmosphere favorable for quickly addressing concerns. Documenting findings and resolutions is similarly essential, as it not only monitors advancements over time but also strengthens a culture of awareness among developers. Considering that 74% of professionals believe legacy application protection tools expose them to supply chain risks, transitioning to modern, comprehensive testing capabilities, such as those provided by Kodezi, is essential.
Kodezi provides both free and paid plans based on usage, and your information and data are safeguarded, guaranteeing that privacy is essential. By following these best practices and utilizing the latest tools, organizations can greatly improve their protection stance and lessen weaknesses effectively.
Essential Tools for Secure Code Analysis: SAST, DAST, and More
Developers now have access to a robust array of tools designed for secure code analysis, which is crucial for maintaining application integrity. Static Application Security Testing (SAST) tools, like Checkmarx, examine source code for weaknesses prior to execution, enabling early identification of flaws. In contrast, Dynamic Application Security Testing (DAST) tools, like OWASP ZAP, evaluate applications in their runtime environment, effectively identifying issues that may only manifest during execution.
Furthermore, Software Composition Analysis (SCA) tools, exemplified by WhiteSource, manage open-source software components to ensure that known weaknesses are promptly addressed. Incorporating a mix of these tools is essential for a thorough protection strategy. By incorporating SAST, DAST, and SCA tools into the development pipeline, organizations can automate secure code analysis to identify and correct vulnerabilities, significantly improving overall code protection.
This proactive approach not only mitigates risks but also streamlines compliance with industry standards, ultimately safeguarding organizational assets. Considering the rising threats, with a reported 41% increase in ransomware-related breaches that require 49 days longer to handle than usual, it is essential to implement strong protective measures. Moreover, the integration of AI in safeguarding can lead to significant financial benefits, saving organizations up to $3.81 million per breach.
Real-world weaknesses, such as those highlighted in the SISA case study on common application security issues, further emphasize the necessity of employing SAST, DAST, and SCA tools to effectively combat threats like SQL injection attacks and broken authentication mechanisms.
Integrating Secure Code Analysis into the Software Development Lifecycle
To effectively embed secure code analysis into the Software Development Lifecycle (SDLC), a security-first approach must be embraced by developers from the outset. This begins with threat modeling, which is crucial for identifying potential risks and vulnerabilities tailored to the specific application. During the development phase, incorporating secure code analysis into continuous integration/continuous deployment (CI/CD) practices is essential; this should integrate automated testing of vulnerabilities into the build process, ensuring that protective measures are consistently applied.
Regular reviews and updates of protection requirements throughout the application’s evolution are vital to adapt to new challenges. After deployment, conducting routine audits and penetration testing helps to identify and mitigate any newly introduced vulnerabilities. By prioritizing protection as a core component of the SDLC, organizations can drastically reduce the risk of breaches and cultivate a culture of vigilance.
As Jeff Smith, Lead Technical Writer, notes,
Learning these technologies and helping other people do the same is his passion.
This dedication to education and proactive measures corresponds with the industry trend, where a Forrester report indicates that 26% of global IT and digital professionals consider risk and governance as their main challenges in adopting agile and DevOps methodologies in 2023. Furthermore, the integration of AI/ML and automation in DevSecOps practices is on the rise, with 75% of teams either using or planning to use these technologies for test/code review, an increase from 41% in 2021.
Adopting these practices not only improves safety but also optimizes the overall development process, as demonstrated by the case study titled 'Automation and AI in DevSecOps,' which highlights the increasing adoption of these technologies.
Fostering a Culture of Security: Training and Awareness for Developers
Creating a strong culture of protection within development teams requires ongoing training and awareness initiatives. Research indicates that a significant 70% of organizations recognize the importance of secure code analysis and secure coding practices, reflecting a pivotal shift in cybersecurity responsibilities that extends beyond IT departments. To strengthen this culture, regular workshops and training sessions should be established, concentrating on essential topics such as:
- Threat modeling
- Vulnerability assessment
- The effective use of protective tools
Developers can greatly benefit from participating in conferences and webinars, which serve as valuable platforms for expanding their knowledge. Moreover, utilizing gamification techniques—such as capture-the-flag challenges—can transform learning about protection into an engaging and memorable experience, making the training more relatable and enjoyable for developers. Easy access to the latest resources and documentation regarding safe coding standards is vital for keeping teams informed and prepared.
By highlighting continuous training on safety, organizations enable their developers to take an active part in building a more secure software development lifecycle that incorporates secure code analysis. As noted by an expert from PCI Energy Solutions,
I’ll be sharing my expertise on this topic at SecureWorld Boston 2025, offering actionable insights to help organizations build a security-first culture.
The effect of such training programs is substantial; companies that participate in awareness training observe a remarkable 70% decrease in incidents.
This underscores the critical importance of fostering a culture of security in tech teams, highlighting that regular training initiatives not only improve knowledge but also lead to tangible reductions in vulnerabilities.
Conclusion
Embracing secure code analysis is a crucial strategy for organizations seeking to fortify their software against the ever-evolving landscape of cyber threats. By systematically reviewing code and utilizing automated tools, developers can proactively identify and address vulnerabilities before they become critical issues. This practice not only enhances security but also boosts overall code quality and maintainability, leading to significant cost savings by preventing potential breaches and compliance penalties.
Integrating secure coding practices into the software development lifecycle is essential for cultivating a robust security posture. By adopting a security-first approach from the outset, engaging in regular training, and leveraging advanced tools like Kodezi for automated debugging and real-time feedback, teams can effectively mitigate risks. The importance of fostering a culture of security cannot be overstated; ongoing education and awareness initiatives empower developers to take ownership of security responsibilities, thereby creating a more resilient software environment.
As organizations increasingly prioritize secure coding practices, the benefits extend beyond mere compliance. They pave the way for enhanced trust with customers and stakeholders, ultimately contributing to the long-term success of the business. In a world where cyberattacks are on the rise, investing in secure code analysis and best practices is not just a choice; it is a necessity for safeguarding sensitive data and maintaining a competitive edge in the digital landscape.
Frequently Asked Questions
What is secure code analysis and why is it important?
Secure code analysis is a practice for detecting and addressing security vulnerabilities within software applications. It is important because it helps identify weaknesses that could expose applications to cyber threats, ultimately strengthening software protection and improving overall quality and maintainability.
What are the key actions involved in secure code analysis?
Key actions in secure code analysis include improving formatting, adding exception handling, and addressing performance bottlenecks.
How does secure code analysis contribute to cost savings?
By identifying issues early in the development lifecycle, secure code analysis can reduce the risk of costly breaches and compliance fines, leading to substantial cost savings.
What statistics highlight the need for secure coding practices?
Research shows that organizations prioritizing safe coding practices experience notably fewer security breaches. Additionally, 43% of cyberattacks target small businesses, with only 14% feeling sufficiently prepared. There is also an 8% rise in critical weaknesses among applications processing payment card data.
What are some optimal techniques for application protection?
Optimal techniques include performing regular assessments, staying informed about the latest trends and threats, adopting a reliable development lifecycle, educating developers in safe coding practices, and utilizing automated tools for testing.
How can automation tools like Kodezi enhance secure code analysis?
Automation tools like Kodezi streamline repetitive tasks, analyze bugs, and allow developers to focus on high-risk areas. Kodezi also functions as an autocorrect for programming, automatically resolving issues and generating comments.
What role does pair programming play in secure code analysis?
Pair programming fosters real-time feedback and enhances knowledge sharing among team members, which can lead to more robust protective outcomes in secure code analysis.
Why is documentation important in secure code analysis?
Documenting findings and resolutions is essential for monitoring advancements over time and strengthening a culture of awareness among developers regarding security practices.
What are the available plans for using Kodezi?
Kodezi offers both free and paid plans based on usage, ensuring that user information and data are safeguarded to protect privacy.
What is the significance of transitioning from legacy application protection tools?
Transitioning to modern, comprehensive testing capabilities is essential, especially since 74% of professionals believe legacy tools expose them to supply chain risks. Using updated tools like Kodezi can greatly improve protection and reduce vulnerabilities.




