Introduction
In an increasingly digital landscape, the security of applications has never been more critical. As cyber threats evolve, organizations must adopt robust strategies to identify and mitigate vulnerabilities before they can be exploited.
App vulnerability scanners emerge as essential allies in this endeavor, automating the detection of security weaknesses and streamlining the remediation process. By integrating these tools into the software development lifecycle, organizations can ensure that security is woven into the fabric of their development practices.
The growing reliance on solutions like Kodezi CLI not only enhances code quality but also accelerates the identification and resolution of vulnerabilities, allowing teams to focus on innovation while maintaining a strong security posture.
This article delves into the pivotal role of app vulnerability scanners, the common threats they detect, and best practices for their implementation, highlighting the transformative impact these tools can have on application security.
Defining App Vulnerability Scanners: An Overview
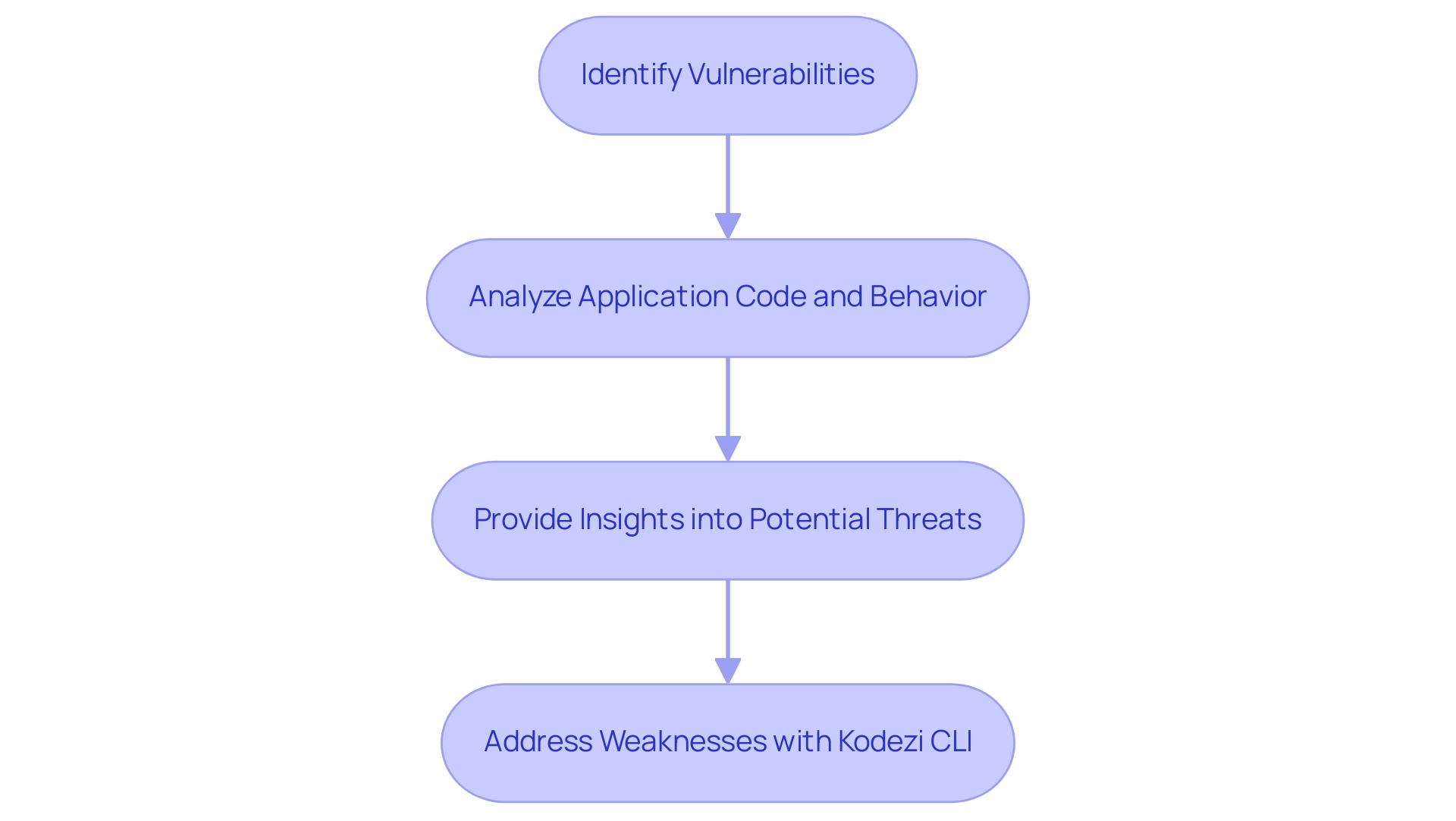
A software flaw detector acts as an essential resource in recognizing weaknesses within programs. These specialized app vulnerability scanners automate the identification of vulnerabilities, such as SQL injection flaws, cross-site scripting (XSS), and insecure configurations. By meticulously analyzing application code and behavior, these tools provide essential insights into potential threats that malicious actors could exploit.
In conjunction, Kodezi CLI improves this process through automated code debugging, quickly identifying and resolving codebase issues to ensure adherence to best practices and coding standards. Kodezi CLI also enhances code formatting and adds exception handling, addressing performance bottlenecks to optimize overall code quality. The global Vulnerability Scanning market, valued at $X billion in 2020, underscores the growing recognition of the importance of these tools in cybersecurity.
The effectiveness of the app vulnerability scanner lies in its ability to streamline the assessment process, enabling organizations to proactively address weaknesses before they can be exploited in a real-world context. As Eoin Keary aptly points out, 'As a society, we need to focus on what matters and execute more efficiently. In cybersecurity, context is king, given the endgame is to prevent and detect breaches.'
This year's report emphasizes the necessity of addressing the 'right issues' more quickly and reducing our window of exposure through tools like Kodezi CLI, which enhances code quality and automates testing. Furthermore, the case study on the Malicious File Upload issue, identified as the third most common high/critical severity flaw in 2023, highlights the urgency of timely remediation, with an average remediation time of 117 man-days. This demonstrates the significant effect of weaknesses and the essential function that app vulnerability scanners, along with automated solutions such as Kodezi, fulfill in enhancing application protection.
Try out Kodezi CLI to experience its capabilities firsthand.
The Critical Role of App Vulnerability Scanners in Security
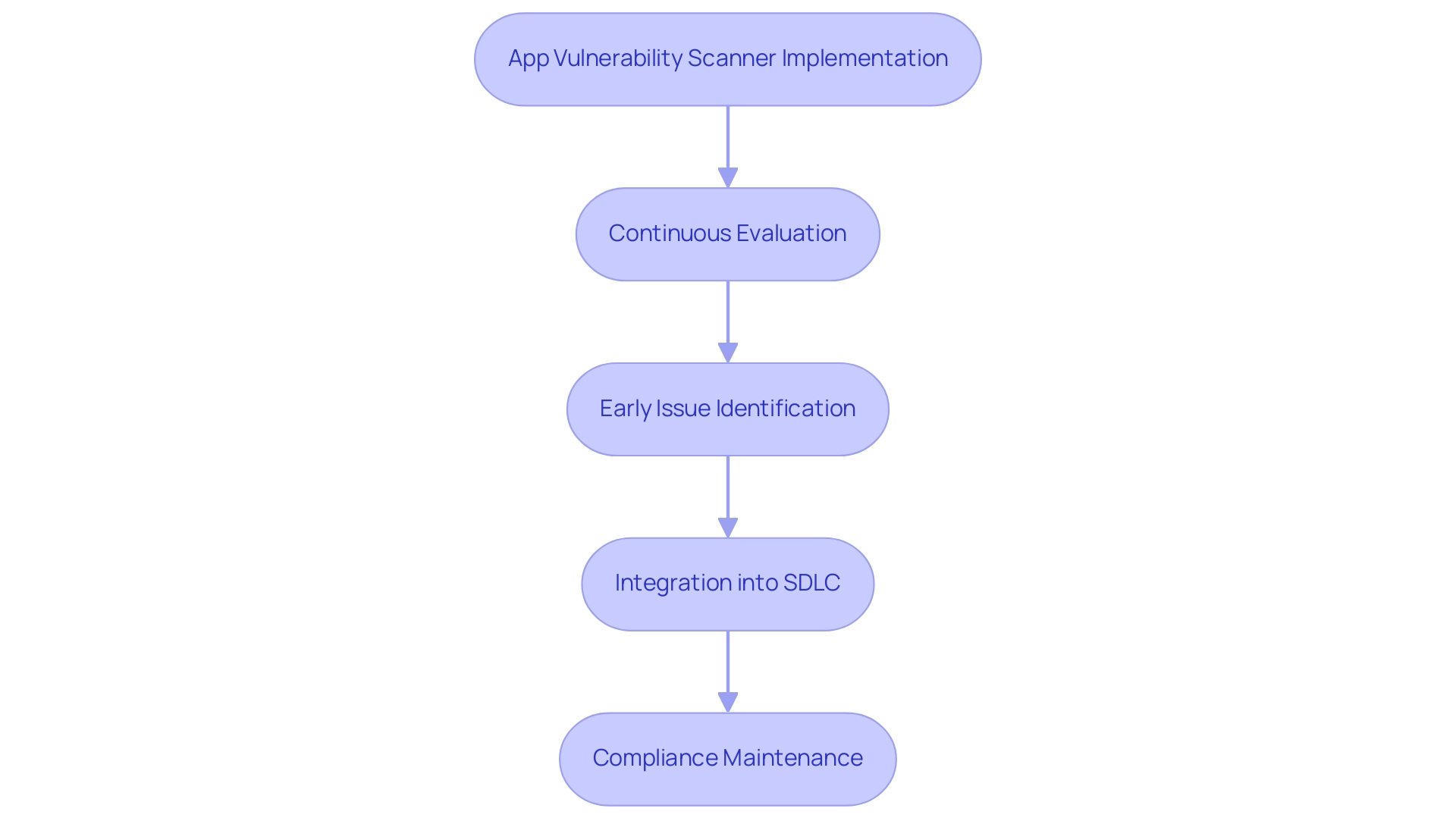
App vulnerability scanners play a crucial role in the protection environment by offering organizations the capability to identify and address weaknesses effectively. They facilitate continuous evaluations, enabling teams to identify issues early in the development cycle, which is essential for agile development practices. By incorporating these devices into the software development lifecycle (SDLC), organizations can guarantee that protection is a key element of their development process, rather than a secondary consideration.
Additionally, an app vulnerability scanner helps maintain compliance with industry regulations and standards through regular scanning, thereby reducing the risk of costly breaches and enhancing the organization's reputation in the market.
Common Vulnerabilities Detected by App Vulnerability Scanners
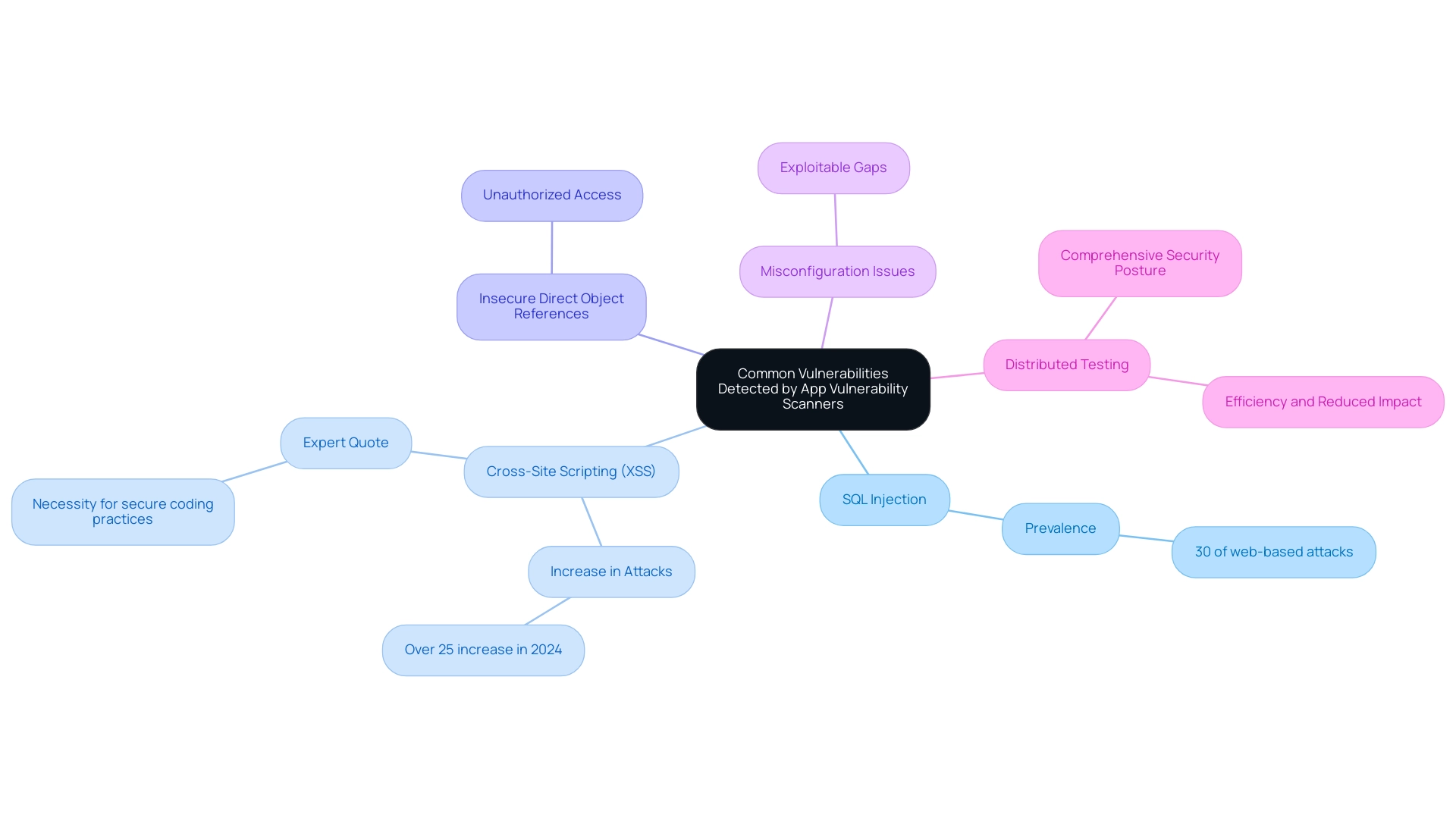
App security scanners excel at detecting a variety of common weaknesses that can significantly undermine software safety. Key vulnerabilities include:
- SQL Injection: This attack vector allows malicious SQL statements to be inserted into input fields, leading to unauthorized access and potential database compromise. Recent statistics suggest that SQL injection remains a prevalent threat, with studies revealing that it represented about 30% of all web-based attacks in 2024. This underscores the need for robust defenses.
- Cross-Site Scripting (XSS): This flaw allows attackers to inject harmful scripts into web pages, affecting users who engage with those pages. In 2024 alone, XSS attacks have been reported at alarming rates, with an increase of over 25% compared to the previous year, emphasizing the critical nature of addressing this issue. An expert in application protection noted, "The rise in XSS attacks highlights the necessity for developers to prioritize secure coding practices and utilize an app vulnerability scanner to mitigate risks."
- Insecure Direct Object References: This issue exposes internal implementation objects, permitting unauthorized access and manipulation by malicious actors.
- Misconfiguration Issues: Often arising from default settings or incomplete setups, this flaw creates exploitable gaps in protective protocols.
By actively recognizing and tackling these weaknesses, organizations can utilize an app vulnerability scanner to establish preventive actions that secure software and protect confidential information. The distributed testing method, which utilizes multiple tools across various locations, enhances efficiency while ensuring a comprehensive view of the security landscape. As demonstrated in a recent case study on distributed testing, this method reduces effects on target systems and uncovers weaknesses that may otherwise stay concealed under particular operational conditions, ultimately resulting in a more secure software environment.
Best Practices for Implementing App Vulnerability Scanners
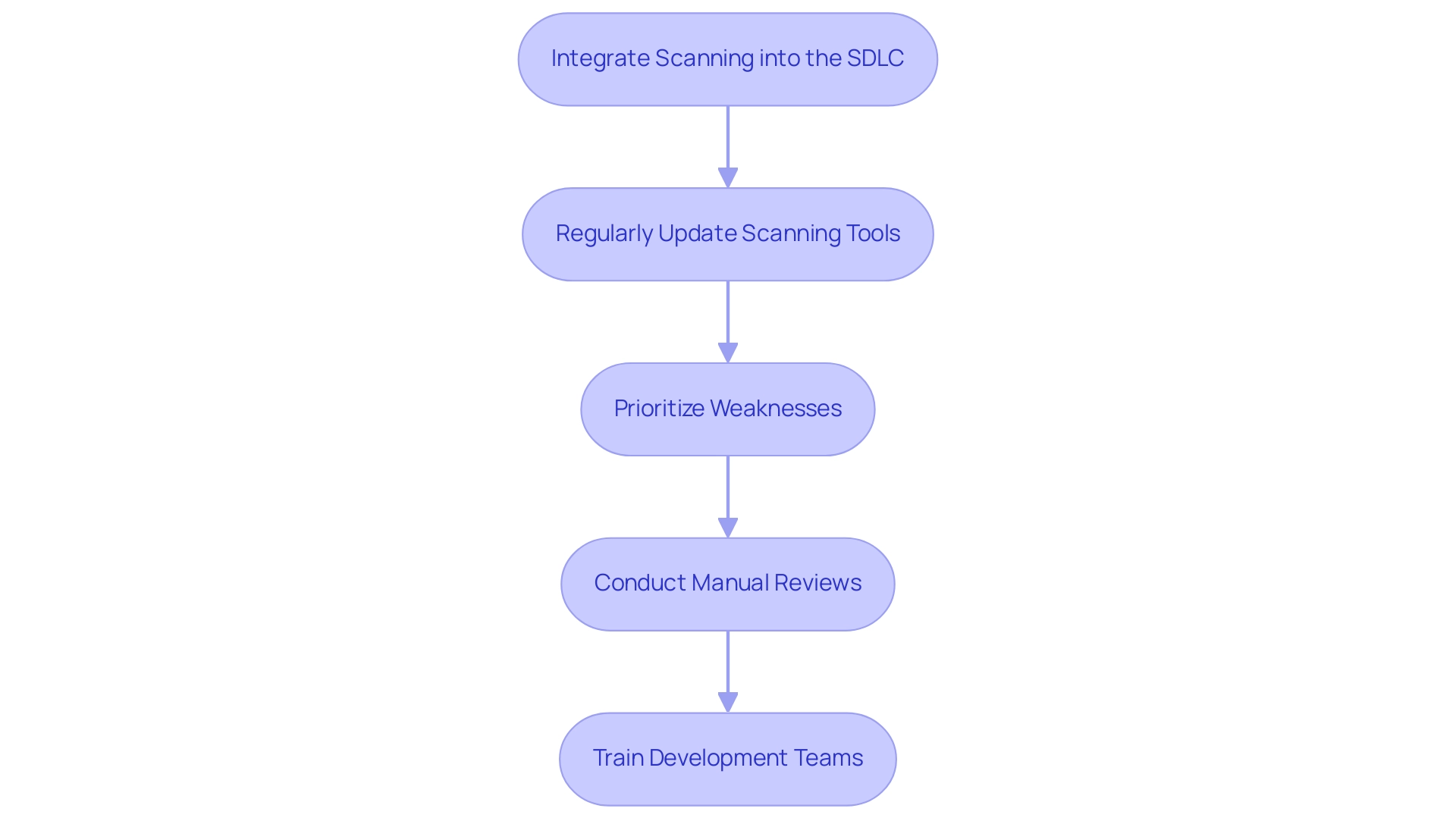
To enhance the effectiveness of application vulnerability scanners, organizations should adopt the following best practices:
- Integrate Scanning into the SDLC: Embed security scanning at every stage of the software development lifecycle, from initial design through to deployment. As Mark McMurtrey from the University of Central Arkansas observes, "The SDLC is a theory that has widespread application in practice," stressing that protection must be a fundamental aspect of development rather than an afterthought.
- Regularly Update Scanning Tools: Consistently update scanning tools to ensure they can detect the latest weaknesses and threats. For example, at General Hospital, software upgrades occur every six weeks, emphasizing the importance of regular updates for maintaining a strong defense posture.
- Prioritize Weaknesses: Acknowledge that not all weaknesses pose the same risk; prioritize remediation according to both severity and potential impact to effectively allocate resources and mitigate risks.
- Conduct Manual Reviews: While automated scans are efficient, supplementing them with manual code evaluations can identify complex weaknesses that tools may overlook, providing a more thorough assessment of safety.
- Train Development Teams: Equip developers with knowledge about safety best practices and how to interpret scanner results. This training promotes a culture of awareness and enables teams to proactively address vulnerabilities. The insights gained from the SAD Course case study illustrate how practical exercises can enhance understanding of software acquisition and protection practices, reinforcing the importance of such training.
By implementing these best practices, organizations can significantly bolster their application security using an app vulnerability scanner, ensuring a proactive stance against potential threats.
Conclusion
App vulnerability scanners are indispensable tools in the modern cybersecurity landscape, enabling organizations to proactively identify and remediate vulnerabilities before they can be exploited. By automating the detection of common threats such as SQL injection, cross-site scripting, and insecure configurations, these scanners streamline the security assessment process and integrate security into the software development lifecycle. The integration of solutions like Kodezi CLI further enhances this capability, allowing teams to focus on innovation while maintaining robust security practices.
The importance of adopting best practices in utilizing app vulnerability scanners cannot be overstated. Regular updates, prioritization of vulnerabilities, and embedding security measures throughout the development process are vital strategies that enhance the effectiveness of these tools. Supplementing automated scans with manual reviews and training development teams fosters a culture of security awareness, empowering organizations to tackle vulnerabilities head-on.
In conclusion, embracing app vulnerability scanners and related tools is not just a defensive measure; it is a strategic advantage in safeguarding applications against evolving cyber threats. By prioritizing application security, organizations can not only protect sensitive data but also enhance their reputation and operational efficiency in an increasingly digital world. The time to act is now—invest in these essential tools and practices to fortify application security and drive innovation confidently.
Frequently Asked Questions
What is the purpose of a software flaw detector?
A software flaw detector helps identify weaknesses within programs by automating the detection of vulnerabilities such as SQL injection flaws, cross-site scripting (XSS), and insecure configurations.
How does Kodezi CLI enhance the vulnerability scanning process?
Kodezi CLI improves the process by automating code debugging, quickly identifying and resolving codebase issues, ensuring adherence to best practices, enhancing code formatting, and adding exception handling to optimize overall code quality.
Why is the app vulnerability scanner important in cybersecurity?
App vulnerability scanners streamline the assessment process, enabling organizations to proactively address weaknesses before they can be exploited, thus preventing and detecting breaches effectively.
What are some common vulnerabilities detected by app vulnerability scanners?
Common vulnerabilities include SQL injection, cross-site scripting (XSS), insecure direct object references, and misconfiguration issues.
How can organizations maintain compliance and enhance their reputation using app vulnerability scanners?
By regularly scanning for vulnerabilities, organizations can maintain compliance with industry regulations and standards, reducing the risk of costly breaches and enhancing their reputation in the market.
What are some best practices for enhancing the effectiveness of application vulnerability scanners?
Best practices include integrating scanning into the software development lifecycle (SDLC), regularly updating scanning tools, prioritizing weaknesses, conducting manual reviews, and training development teams on security best practices.
What is the significance of addressing vulnerabilities like SQL injection and XSS?
SQL injection and XSS are prevalent threats that can lead to unauthorized access and compromise of sensitive data, making it essential for developers to prioritize secure coding practices and utilize vulnerability scanners to mitigate risks.
What does the report emphasize regarding the urgency of vulnerability remediation?
The report highlights the necessity of timely remediation of vulnerabilities, such as the Malicious File Upload issue, which has significant average remediation times, underscoring the critical role of app vulnerability scanners in enhancing application protection.




